VLAN assignment to LAN and Ubiquiti switch
-
Dear Forum,
I had to change an old switch from D-Link. I could not log in and see the current configuration. The new switch is an Ubiquiti USW Pro Max 48 PoE.
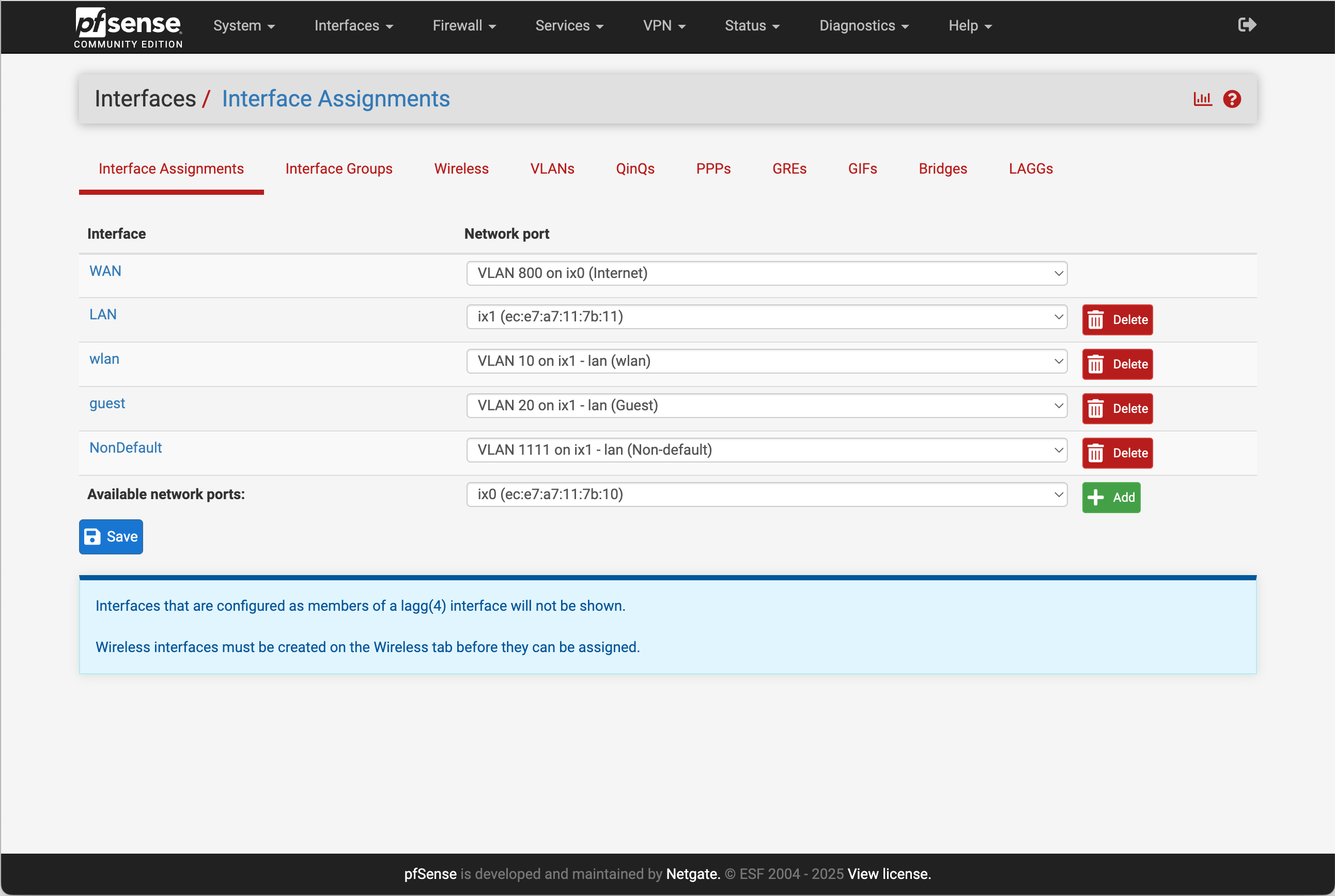
Originally, pfSense was configured with VLANs for
LAN
andWAN(ix1.100andx0.800) and it has been working like that for years.I can get it to work with the
WANinterface set toix0.800as shown.I can't make it work with the
LANinterface set toix1.100. No traffic passesix1.100(tcpdump). I have tried to setting port 4 to eithernative VLAN 1ornative VLAN 100to no avail.If I use the
LANinterface without any VLAN configuration and connect all the "access ports" tonative VLAN 1it is working well. When I look at the GUI for the controller, port 4 (in this case) is marked as "uplink".There are two reasons I want to make this work. First, we are advised not to use the default
VLAN 1in the documentation. Second, I really should be able to configure VLANS in this particular switch like I can in another switch.I am not by any means an expert, so I will appreciate any help.
PS
The other configured VLANs are not important in this context. But both theGuestand thewlandoes actually work as intended.Regards,
Jon Theil Nielsen

-
@jontheil said in VLAN assignment to LAN and Ubiquiti switch:
I can't make it work with the LAN interface set to ix1.100. No traffic passes ix1.100 (tcpdump)
- How to you connect to the pfSense, using WLAN, GUEST or the console - to verify that the LAN => ix1.100 assignment was successful?
- When you set LAN to ix1.100, where do you run
tcpdump, on the pfSense itself? Have you set one of the USW ports as access port for VLAN 100 for easy testing?
-
- I use to the console physically cotcnnected to pfSense with a keyboard and monitor
- So when I check with
tcpdump -i ix1.100I am directly connected to pfSense - I also tested with simple
pingfrom a labtop connected to eitherVLAN 1orVLAN 100
The only thing I see with
tcpdumpis a lot ofARPreqests forDHCPclients. -
@jontheil said in VLAN assignment to LAN and Ubiquiti switch:
The only thing I see with tcpdump is a lot of ARP reqests for DHCP clients.
That is indeed confusing since it a) worked with the D-Link switch and b) should really work, after all VLAN100 is just another VLAN.
Can you post a screenshot of the LAN interface when configured for VLAN100 and one of the working VLAN interface config and VLANs config? (Temporary allow access to the pfSense GUI from the
guestorwlanVLAN).I have tried to setting port 4 to either native VLAN 1 or native VLAN 100 to no avail.
I read that again and setting it to native VLAN100 on port 4 is never going to work, just leave it on native VLAN1.
Setting it to native VLAN100 means setting the port 4 as an access port. All traffic entering untagged (from pfSense) will be tagged with VLAN100. But setting LAN to VLAN100 leaves pfSense traffic tagged with VLAN100.
I also tested with simple ping from a labtop connected to either VLAN 1 or VLAN 10
Can you set port 4 to
native VLAN1and the port you connect your laptop to tonative VLAN100and try again? -
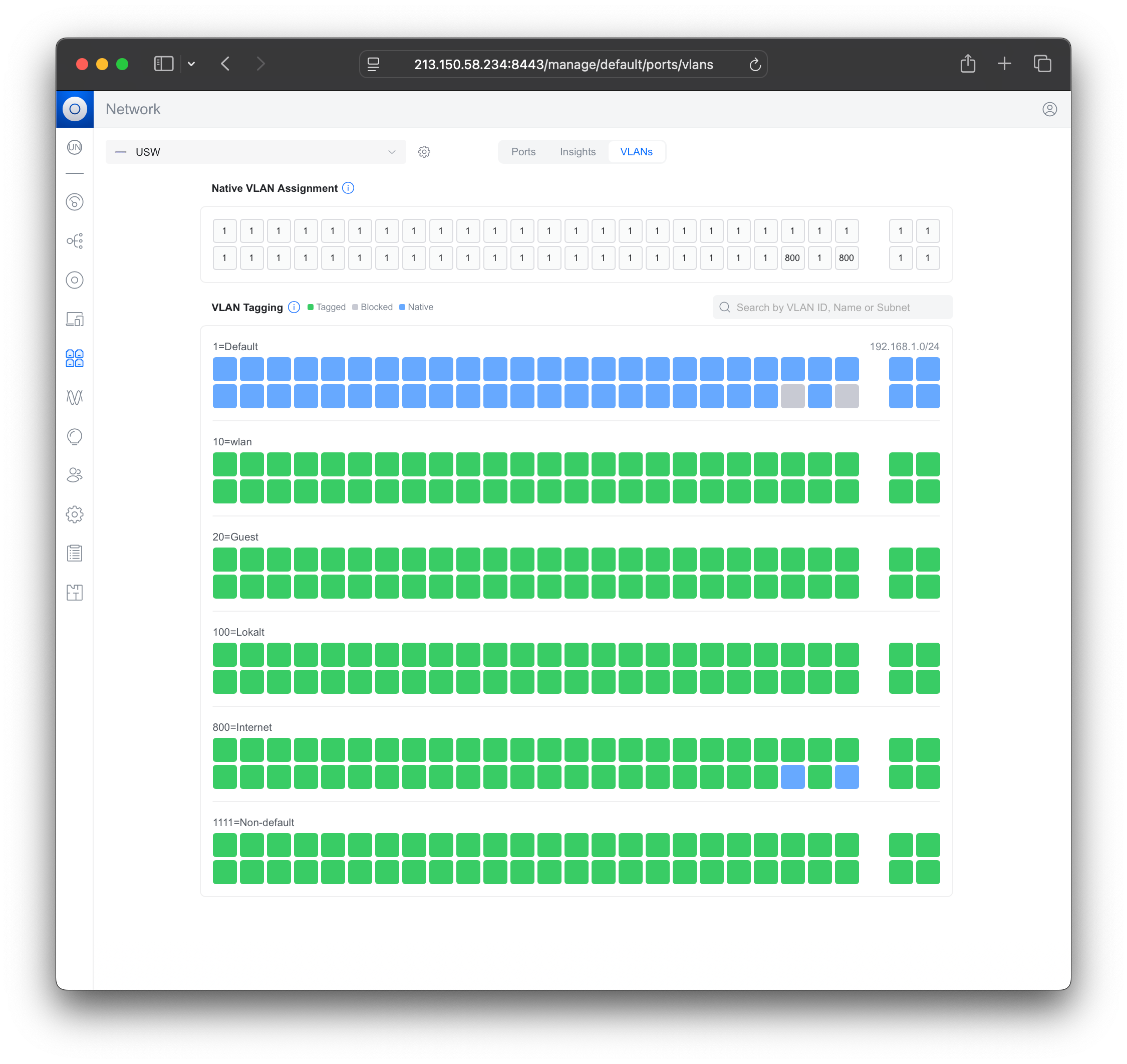
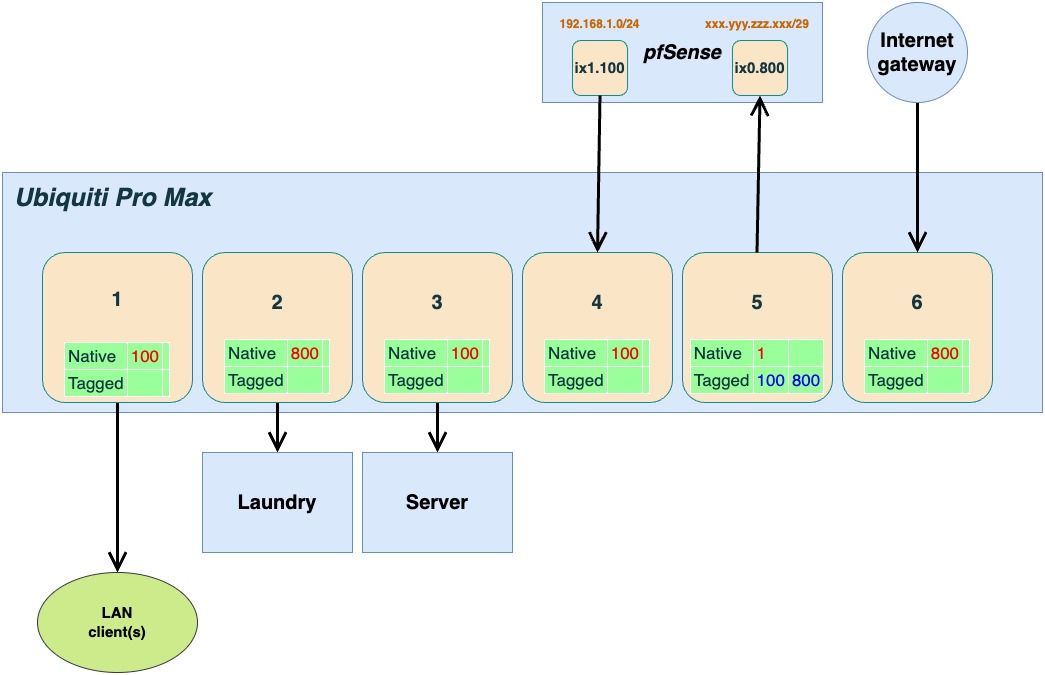
@jontheil The VLAN mapping in the Port manager view of the Unifi switch look pretty much like you describe. But, VLAN 1 is not tagged on ports 4 and 6 (or are they 44 and 48 perhaps?)
VLAN 1 is grey on those ports which would make sense since you changed them to 800 native.I'm trying to understand the reasoning behind your VLAN 800? Since it's set as untagged (native) towards the ISP I'm guessing it's not a requirement on their part?
But then, why would you want to have VLAN 800 available anywhere else on the switch? And why have any of the other VLAN's exposed towards the gateway?
What is Laundry, which you also have set as untagged 800? Are you running some IDS/IPS tool?
Then when it comes to VLAN 100, as I mentioned, you have that exposed on the internet.
Now, what switches or devices do you have connected that are expected to be on VLAN 100? Unless they also are VLAN aware, they will not pick up any traffic on that VLAN. You need to set any ports towards VLAN 100 clients to Untagged, and then it should work... -
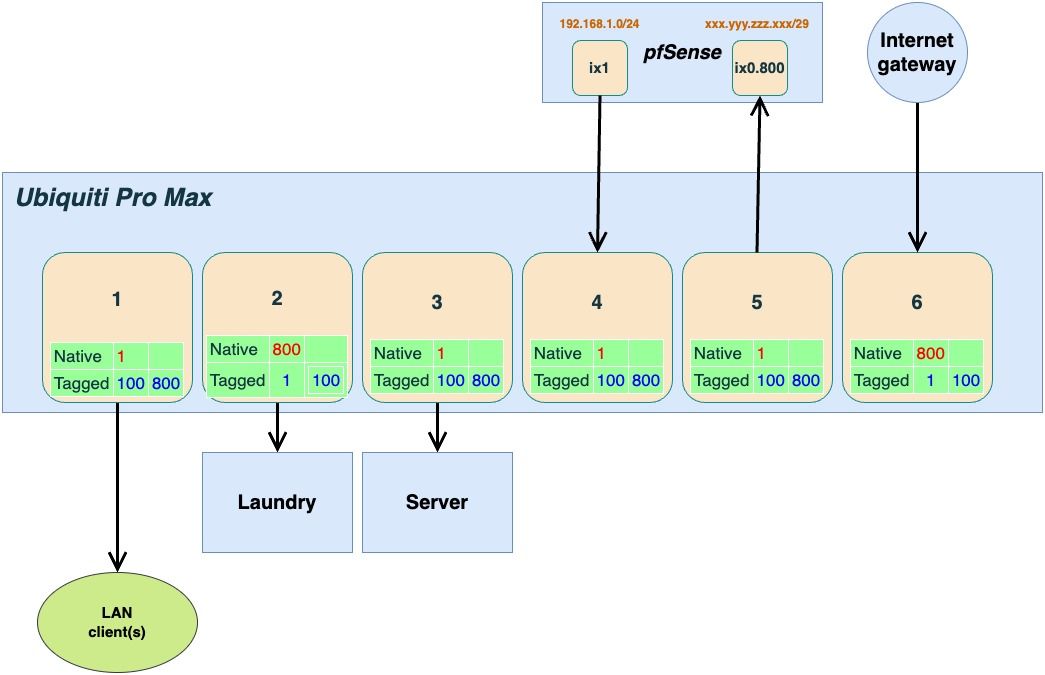
The reasoning is to pass Internet traffic directly to and from the laundry. There is a separate router in there with its own /29 address. Maybe it could be done in another way, but this configuration used to work with the D-Link switch.
Obviously, I have a hard time understanding VLANs per se, even worse with different terminology for different brands.
None of the clients are expected to be VLAN aware.
The point of avoiding the "default"
VLAN 1, as I understand it, is partly to increase security. So I should only allow traffic onVLAN 100(natively) for the clients (in Ubiquiti lingo "Block All)?My challenge is that I try to make the trasition at night and I need to be able to get back to the working setup quickly. So I keep
VLAN 1alive to be able to do any changes in the Ubiquiti Controller which lives on the connected server.I pretty sure I haven't got all your points. But I will add a new version of my schematic representation. I will really appreciate if you can comment on it.
Regards, Jon
-
@jontheil Ok so if you have two IP's and two separate routers/firewalls, then I would probably do it a little bit differently.
I have a similar setup where I get two IP's from my ISP and have a second firewall I am using for testing purposes mainly. For that I initially used a similar setup where I was using VLANs on one of my internal switches to separate out the ports on the WAN side.That didn't feel 100% secure so I now have a separate switch only for the WAN side. Perhaps you could consider repurposing the DLink switch and use that only for the WAN connections? It doesn't matter that you can't access the management interface.
Otherwise I would "split" the Ubiquity switch into two separate parts.
The way to do that would be to create a WAN side where you set up three ports to be VLAN 800 only. No other VLAN's should be present on these three ports. Depending on how you continue with pfsense you need that port to be either Tagged or Untagged (Native).
When you set up a VLAN like that, you do it internally to the switch, as a way to splitting it up into "a switch within the switch". In this case, none of the connected devices (firewalls in this case) need to use VLANs at all. And most importantly, the VLAN 800 should NOT be anywhere other than on the WAN side. And none of the LAN side VLAN's should be on the WAN side (remove 100 Tagged from port 5 in your picture).
Remember that the VLAN setup is the only separation between your LAN and WAN side here, since the switch is connected to both. It might be possible to add port isolation as an added security layer, but I'm not sure how that is done on Unifi.
To make life a bit simpler, I would have just used the parent interface ix0 on pfsense for WAN and not do VLAN at all on that. But if changing that creates too much of a hassle, you can probably keep VLAN 800 as is. But in that case it will expect to see tagged traffic so you need to keep that port on the switch as tagged. But as mentioned, remove any other VLAN's from it. In the Unifi Controller Port Manager you select None as the Native VLAN and then choose 800 as Tagged.
I'm not sure a simple change from VLAN 1 to 100 across the board accomplishes that much from a security standpoint. If that is your concern I'd look at segmenting traffic using a more elaborate scheme. And I'd let pfsense manage the different network segments.
Say for example you want to have the Server(s) separated from the LAN and manage the access to them from pfsense (using firewall rules). Then you could have VLAN 100 native as you have it set up now, and add VLAN 200 as your Server VLAN. In that case port 3 would change to Native 200 and you add 200 as Tagged on port 4 and set up rules in pfsense to allow or block access to VLAN 200 from VLAN 100.
Later you could add a Guest network and perhaps an IoT network if the need arises.Anyway, the way you have now changed the picture where port 1 and 3 (LAN and Server) are VLAN 100 Native should work. However, looking at your Interface Assignments, you also have VLAN 10, 20 and NonDefault (1111) ??
I'm guessing this 1111 is your intended 100?? If so you need to adjust accordingly. Also the switch port connected to pfsense need to have all those VLAN's as Tagged (not Native), since pfsense will expect tagged traffic to arrive with those VLAN ID's.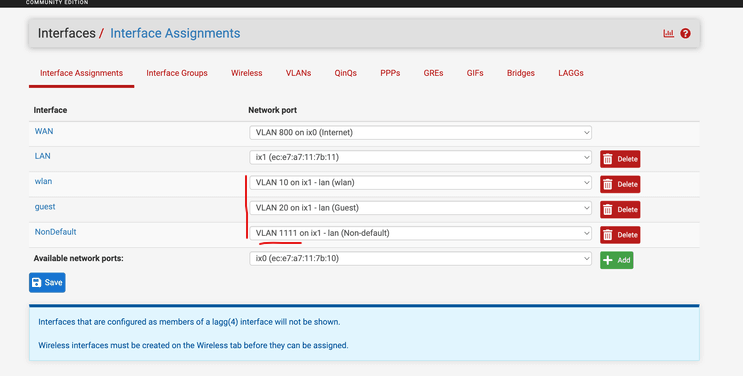
-
@Gblenn
I am greatful for your very thorough explanation. Later on I will give it another go according to your suggestions.Just at note on the
VLAN 1111. It was just a silly experiment to get rid ofVLAN 1as the default. I read in the Ubiquiti VLAN docuentation that a VLAN should exist in the third-party gateway before they are configured in the controller. Since this VLAN was just a "dead end" in pfSense, I never used it.
VLAN 10andVLAN20are configured in the WiFi settings of the controller and work as intended for WiFi clients connected through Unifi access points. -
@Gblenn
I would have followed up earlier but have been busy with both the network and other stuff.
I still appreciate your advice. And I have been reading more about the concept of VLANs.
The old D-Link is still in the rack and I use it for a "backup" so I can go back to this if the Unifi switch does not work.
Theres is another problem that I haven't been able to solve.
The Unifi controller holds all the configured wired and wireless networks even if I use hardware reset on the switch. But no matter what I do, the switch appears to be offline after a few moments.
And even if it still handles the traffic according to the configuration, it is offline in the sense that I can't ping it or log in withssh.
When I use the old switch and just connect the new one through a single cable, the switch can be adopted and configured.
I have read a lot of post about similar issues at the Ubiquiti Forum. Some suggests to manually change theinform hostlike thisset-inform http://ip-of-controller:8080/inform. This seems not to change anything.
Other suggestions are to add an43 optionto the DHCP server (pfSense) or make a host override at the same place.
Do you have any suggestions?