Simple port forward error default deny rule ipv4
-
Hello all
I have setup a simple port forward rule which is not working and showing the error "Default deny rule IPv4 (1000000103)". Any advise would be geatly appreciated as I have spent nearly 2 days reading and researching with no solution yet.
-
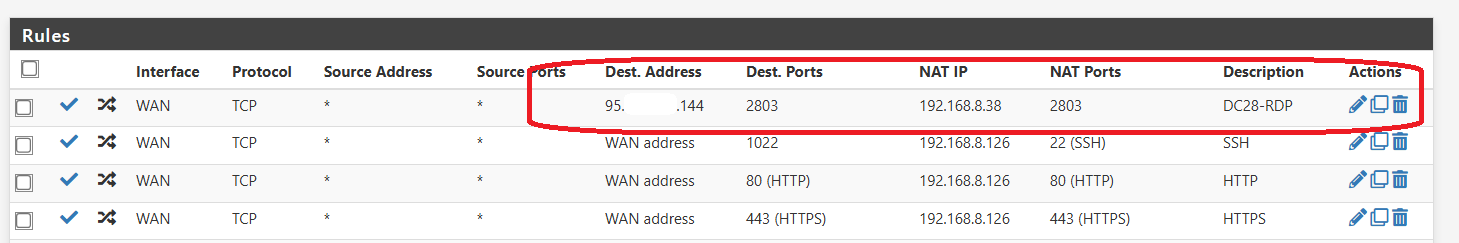
Destination is a Windows machine running RDP on custom port 2803
-
- This has been tested and is working both from a local IP and directly from the internet (if I assign the public IP to it for testing)
-
pfsense is a dedicated hardware running the latest version
-
The rule is anyone connecting to the specied VIP on port 2803, forward it to the local IP (192.168.8.38) of windows machine on port 2803
-
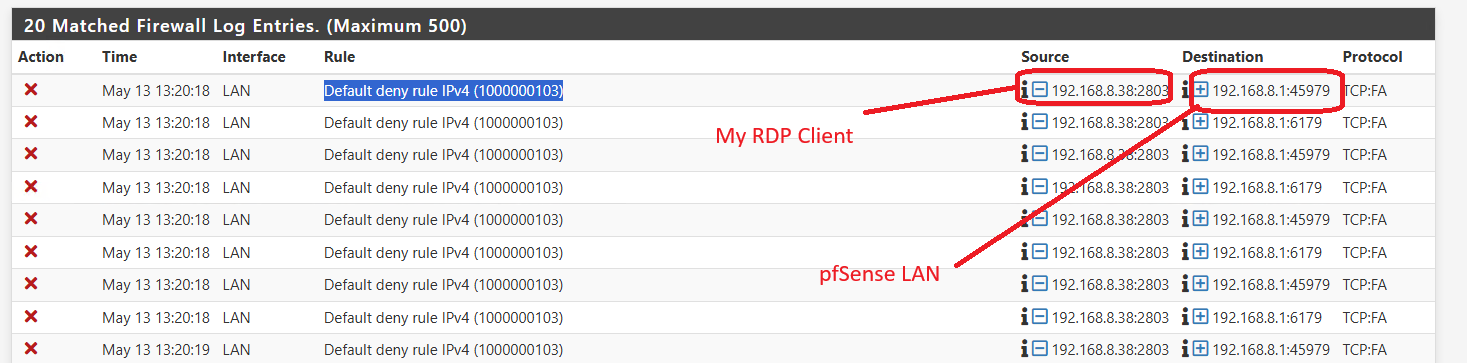
Looking at the firewall logs, I can see RDP traffic coming from my laptop on the internet and being forwarded to the RDP client successfully
-
- However, the logs also show that the return packets from RDP client to pfSense are being blocked on the LAN interface (Default deny rule IPv4 (1000000103)
-
I have setup the NAT with reflection (Pure NAT)
-
- pfSense created the corresponding WAN rule for it too
-
I have used the "Test port" tool to ensure pfSense can see the RDP client on port 2803
-
Both devices definitely can see and ping each other on the LAN
-
I have attached screenshots of the config and firewall log
I am at a loss and not sure whereelse to look or how to troubleshoot further.
Best wishes


-
-
@TheCalvinator those are all fin,ack - ie that rdp box sending back to the pfsense IP, which unless your doing source natting shouldn't be happening. Even if was going to send FA it should be to the IP of the device wanting to connect.. Something on the internet I take it since your port forwarding stuff that hits your wan.
That return traffic should of really been to your 209.x address. Unless you source natted it, ie outbound nat on your lan so the rdp traffic sent to 2803 looked like it came from pfsense IP on your lan I assume (that 192.168.8.1 address)
But either way, your port forward works and the rdp box on 192.168.8.38 sent back a FA..
I would guess those are just multiple FA being sent, even after pfsense closed the state. Or you have asymmetrical traffic flow - but if that was the cause you really should of seen SA (syn,ack) being blocked because lack of state.
If pfsense has no state open to allow the traffic, then yes it would be blocked by the default deny.. Or if there was a state but the device continues to see traffic after the state was closed then yeah that traffic would be closed.
A FA is that 192.168.8.38 saying I am done with this conversation. So its not pfsense causing a problem with your port forward.
-
@johnpoz Hello John
Thank you for your reply. I agree that it was strange seeing the packet had pfsense as its destination as opposed to my 209.X IP address.
I have not setup asymmetric traffic flow nor source NAT, but how do I check if it is there? Anything else I can check?
Best wishes
-
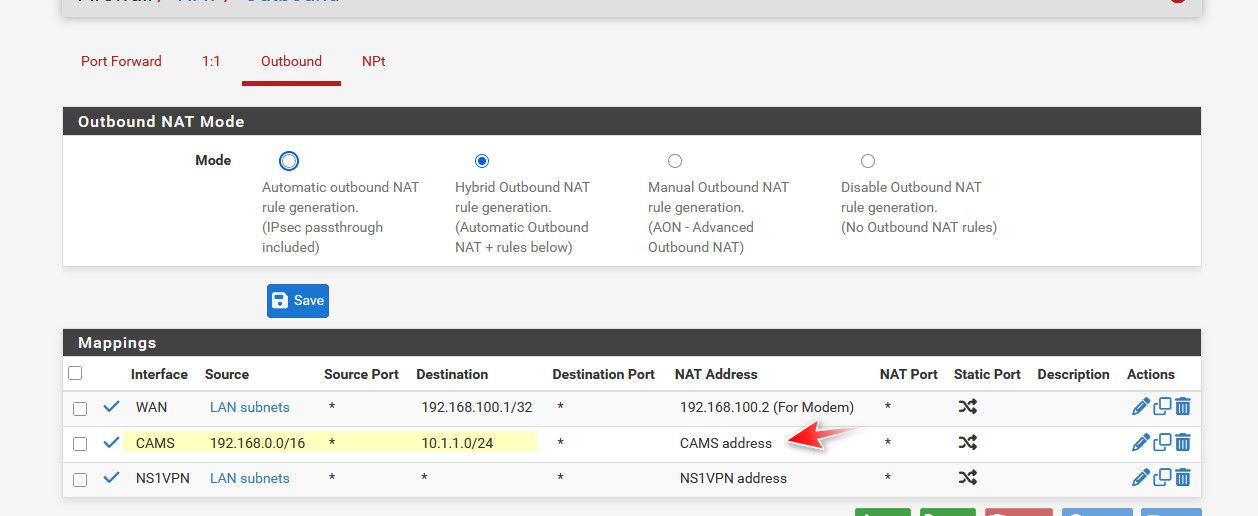
@TheCalvinator what do you have in your outbound nat - do you have something setup for outbound on your lan interface? That would nat your traffic so it looks like it came from pfsense IP on that interface.
You might even want that so you don't have to alter firewall rules on the box your rdping too.. It would think the client is on its local 192.168.8 network.
example: here I nat traffic going to my cams network (10.1.1/24) so it looks like it comes from pfsense IP on that cams network.. The cameras on that network use the nvr as their gateway, no pfsense - so if I didn't source nat the traffic they wouldn't send the traffic back to pfsense, they would send it to their gateway. Which wouldn't work.
-
Hello John
I hope you are well. The problem was an incorrect source NAT setup by a colleague and is now resolved. Thank you for your great help and guidance

Best wishes
-
@TheCalvinator glad to hear finally sorted. Thanks.