External access to a internal web server (VPN site2site)
-
Hello
I am trying to access externally using Ubuntu C the web server on Ubuntu B that it is connected by VPN site to site with between pfsense client and pfsense server, but I can't access.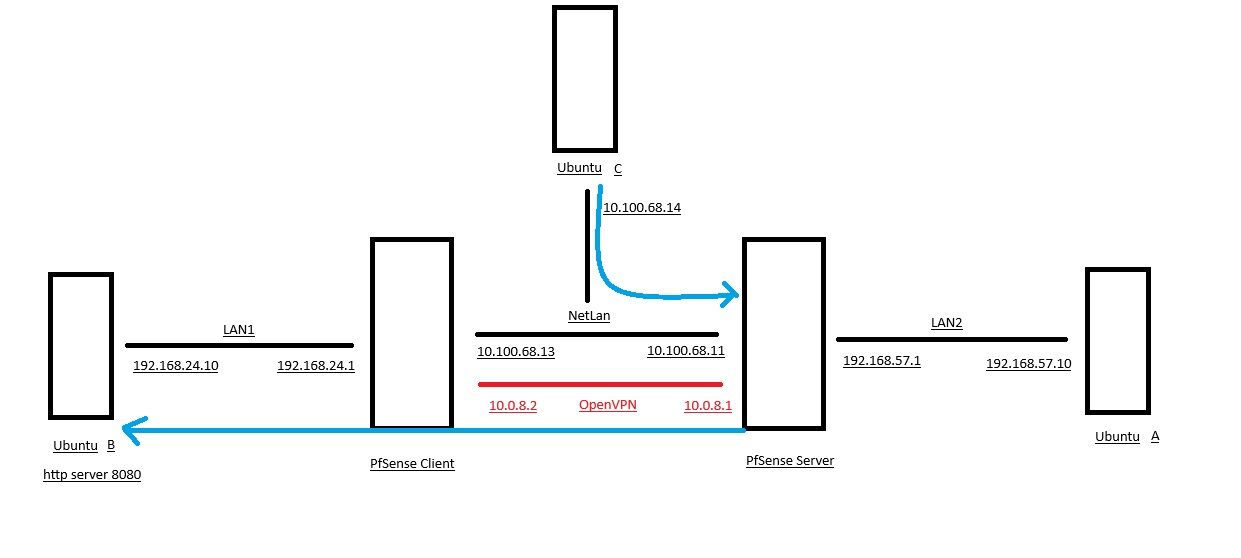
I am trying to do equal the blue line.
Why I need access by Pfsense server? Because it has a dedicaded IP. The pfsense client is a dynamic IP. So why don't you add a dedicaded IP to pfsense client? Because I need it like this.
This is a example on Virtual Box, but I will create this on real machine and VPS.
Today I can ping Ubuntu B on Ubuntu A and I can access the web server on Ubuntu A. But I can't do the same thing by Ubuntu C.
Has somebody some idea?
Thanks in advanced! -
@Wagner-0
Did you create a Client specific override in OpenVPN on the server?Did you add the subnet of Ubuntu C to the "remote networks" in the client config?
-
@viragomann, first of all, thanks for your help!
I did try to create a Client specific override in OpenVPN on the server, but it didn't work.
When you sayed to add the subnet of Ubuntu C to the "remote networks", you are saing on the Client specific override configurations in OpenVPN on the server, right?
I will post some printscreen of my configuration to try to help me.
Server OpenVPN configuration printscreen:
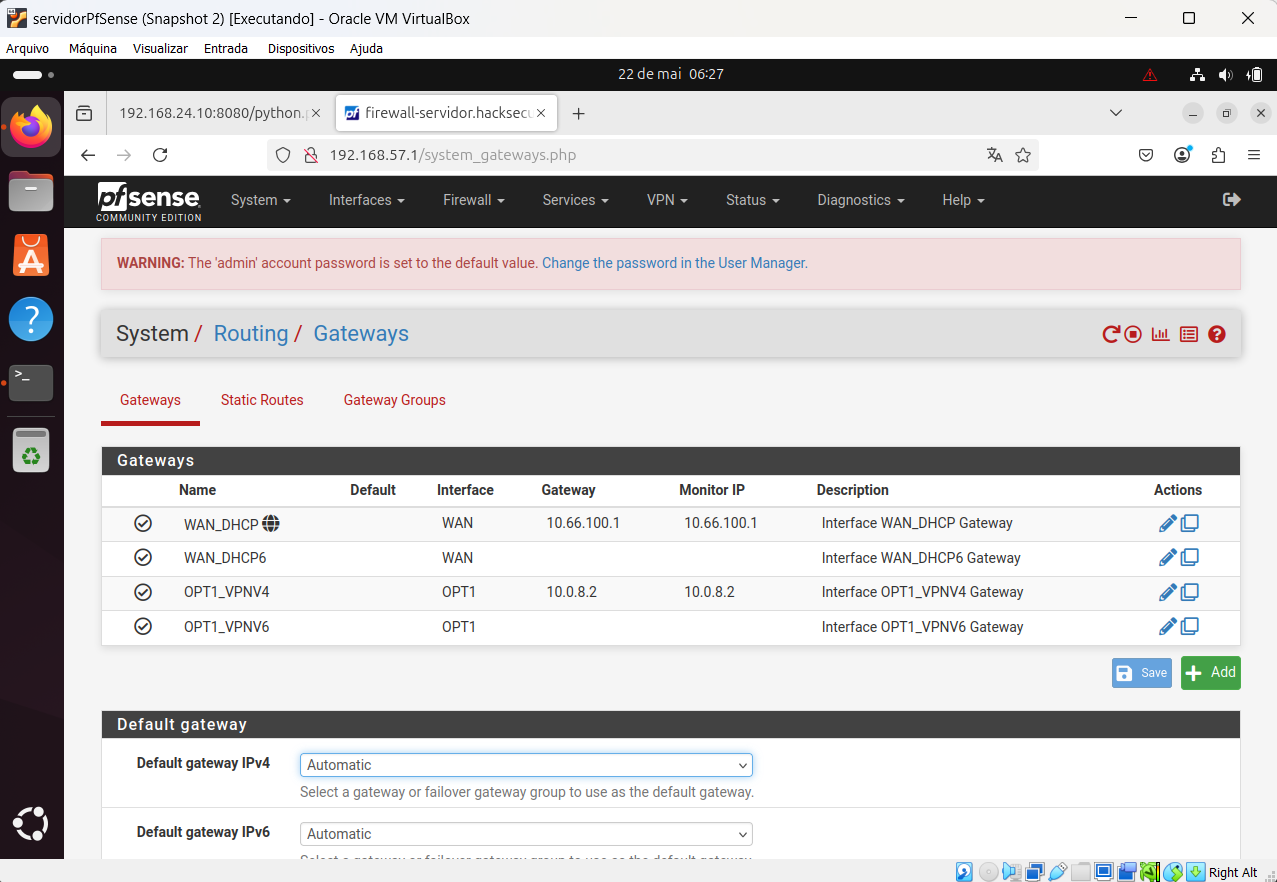

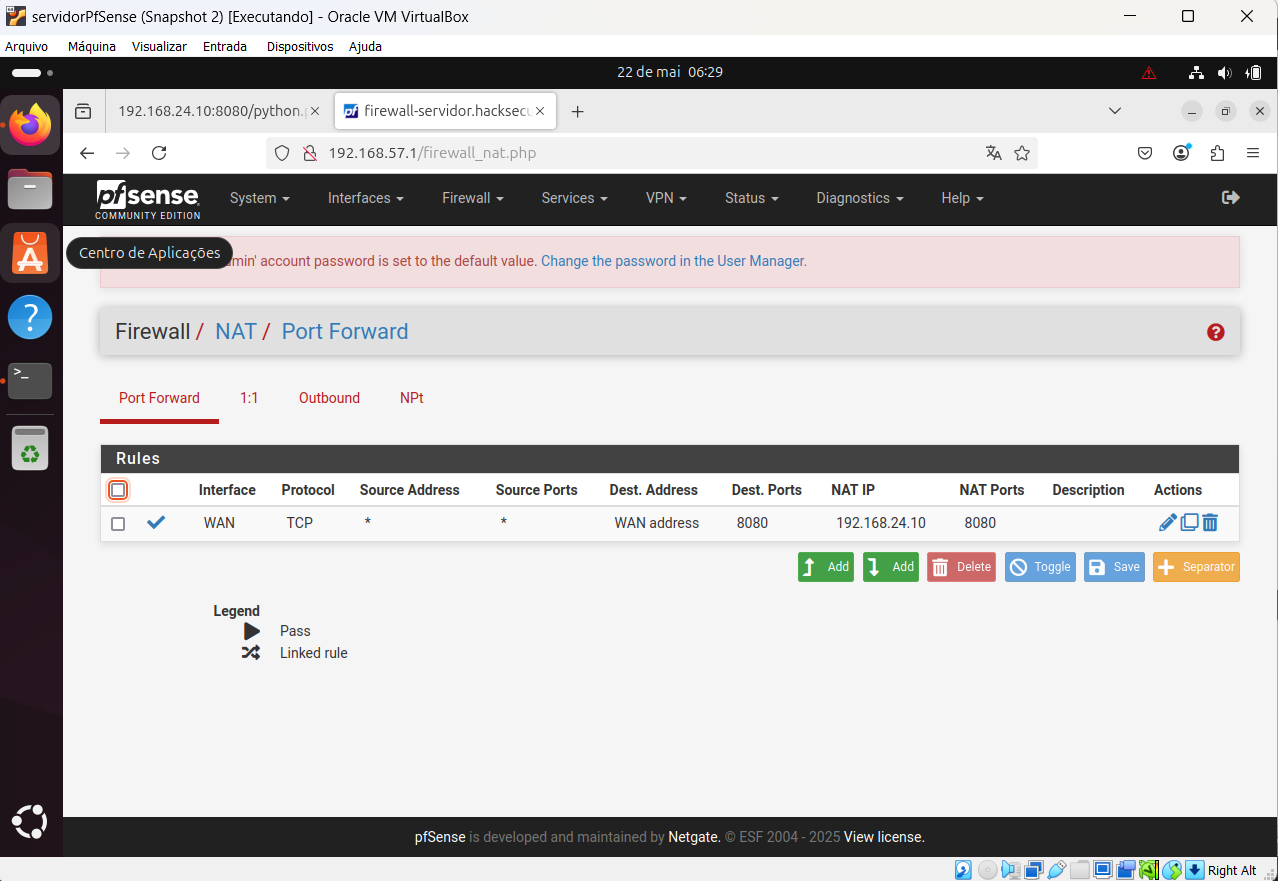


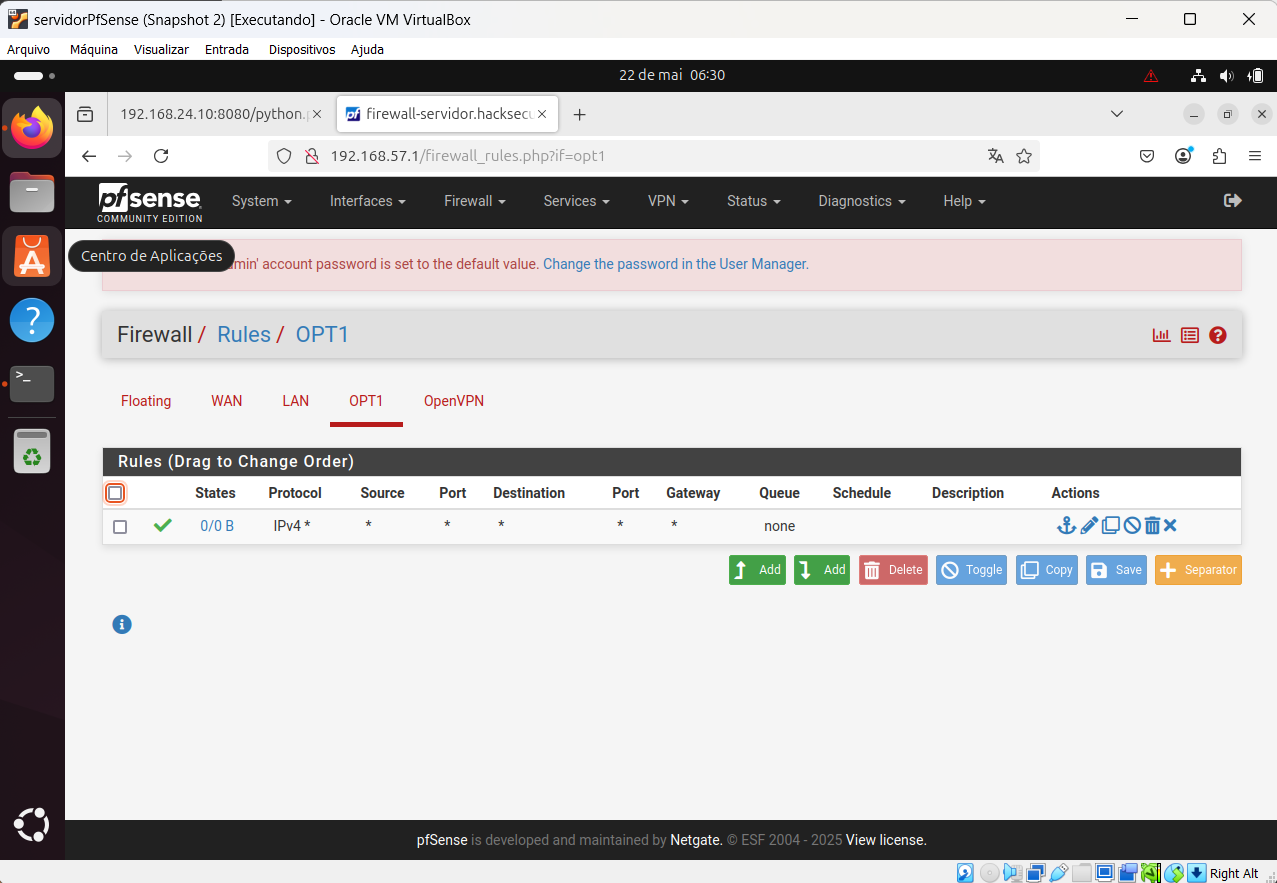
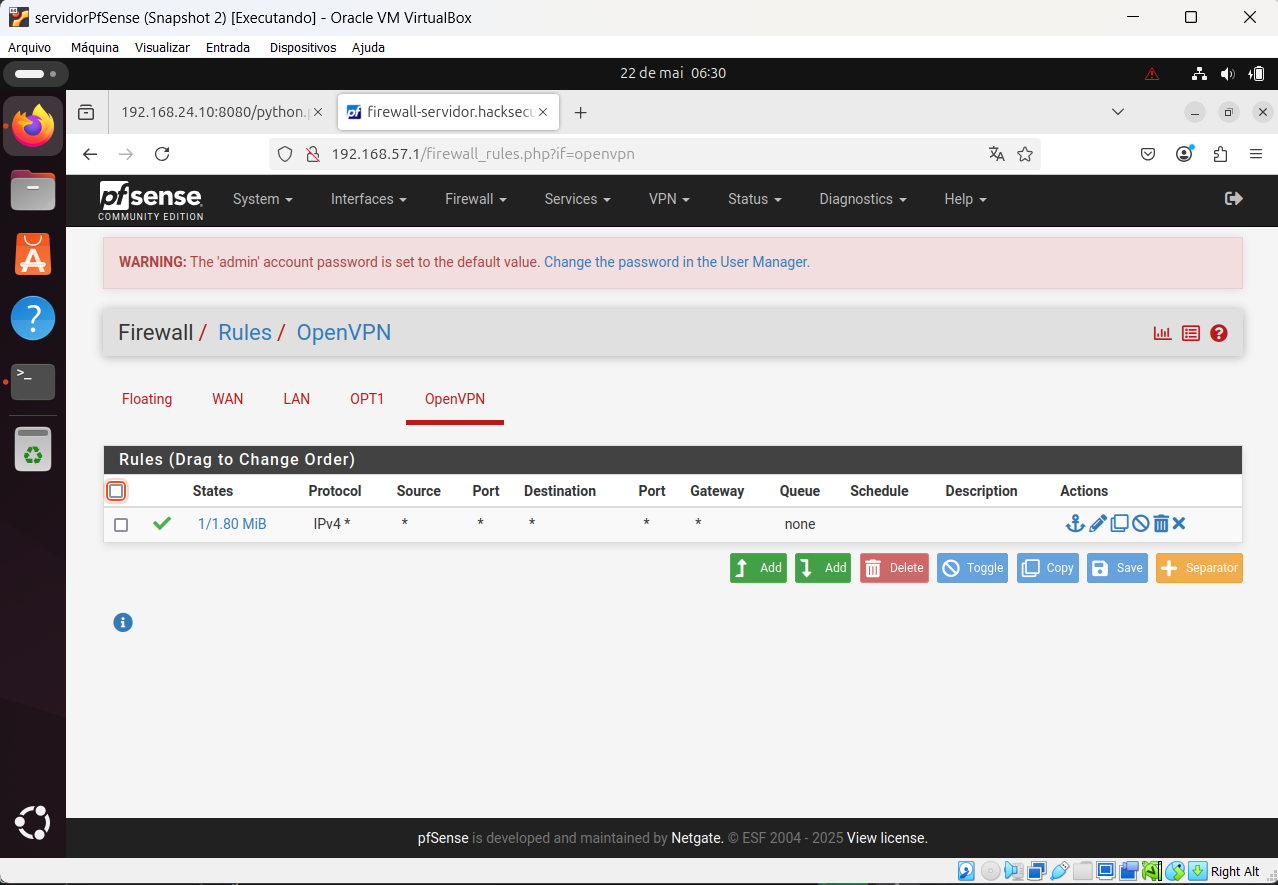

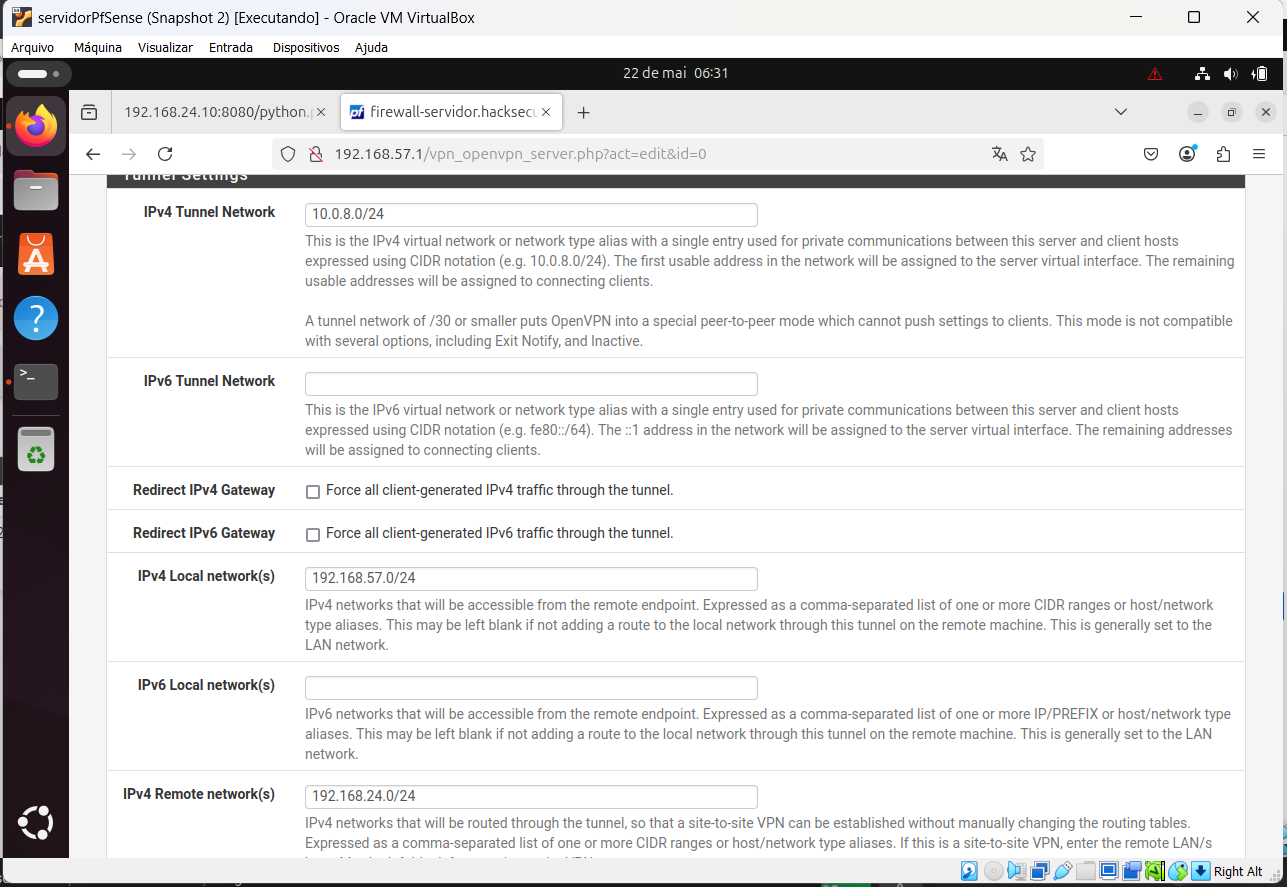
It is the configuration of Client specific override:
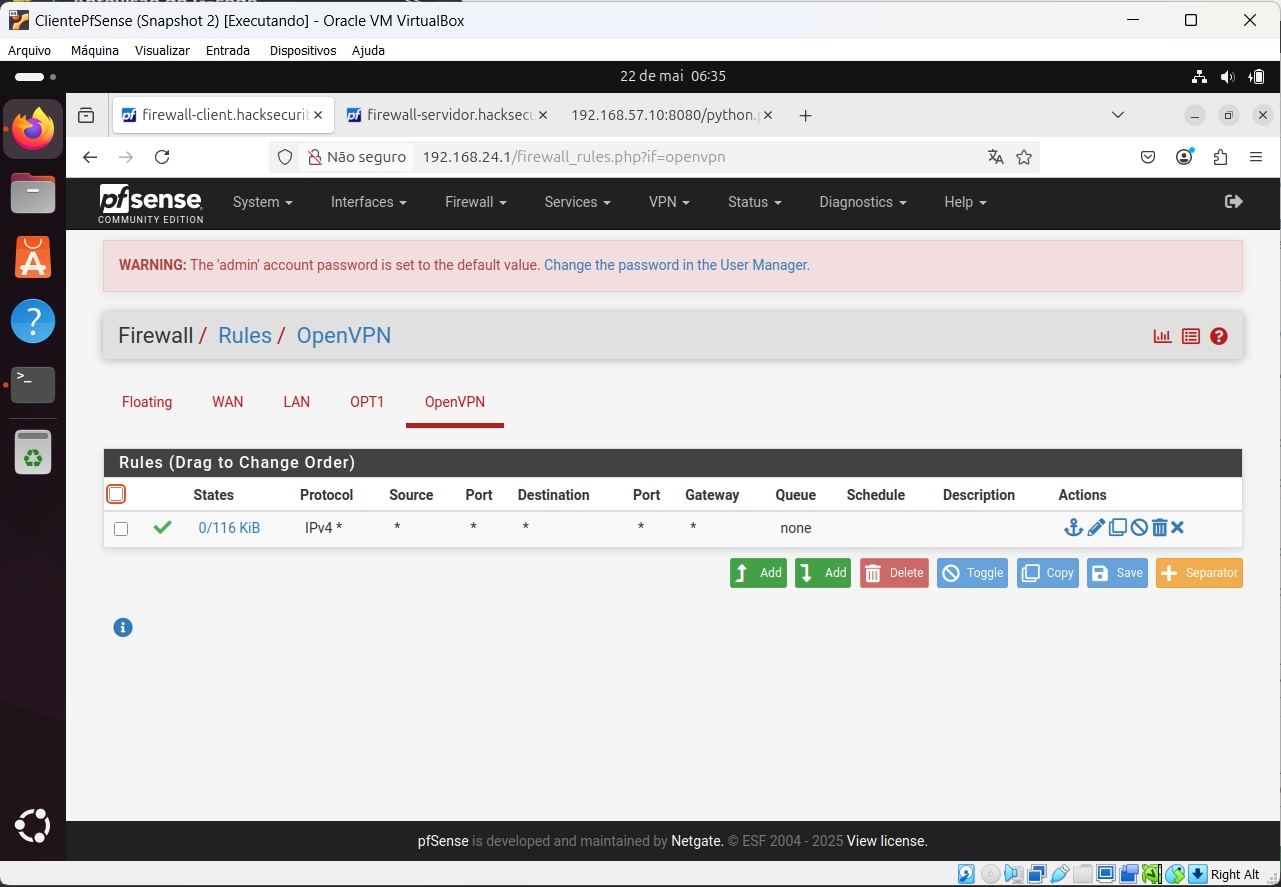
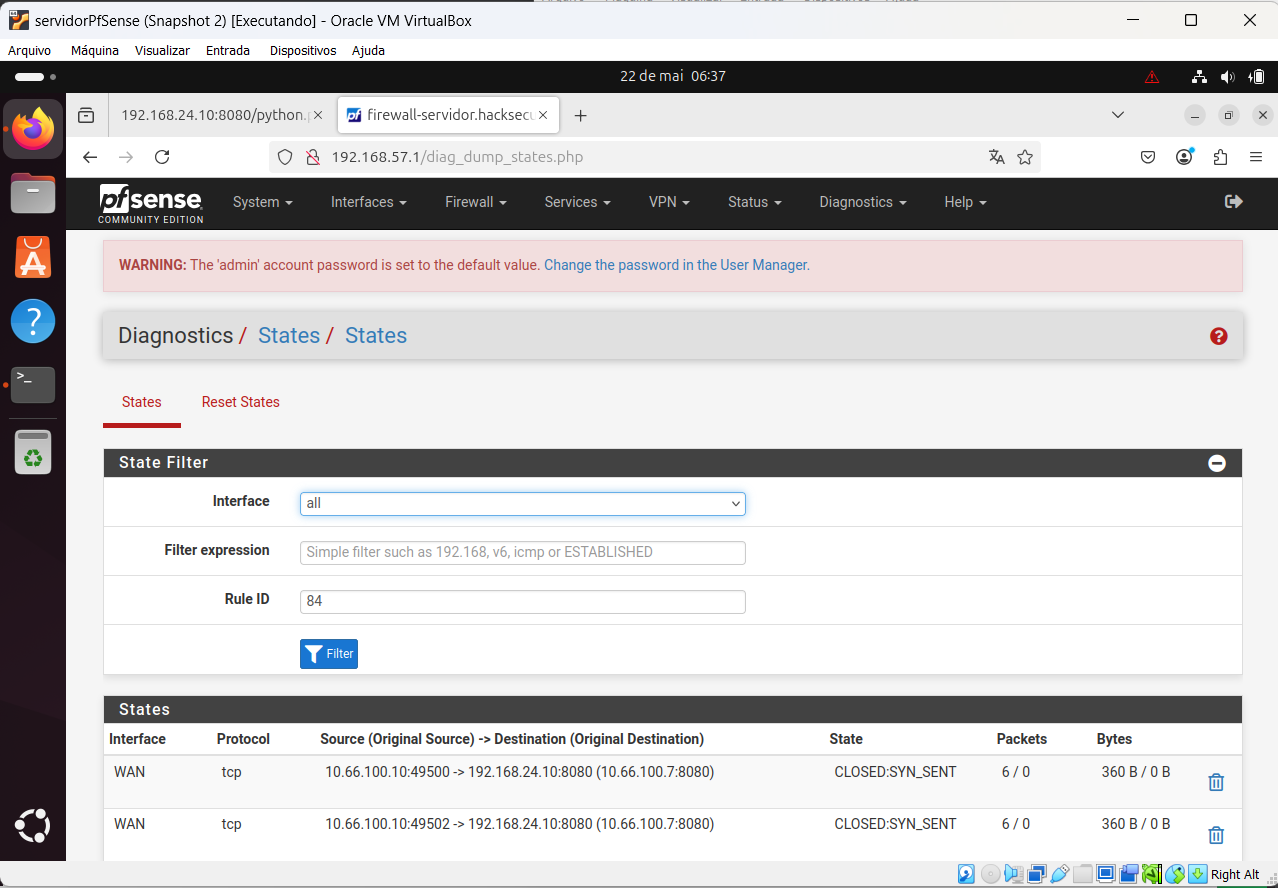
This is a firewall status when I try to connect with Ubuntu C (10.66.100.10)
-
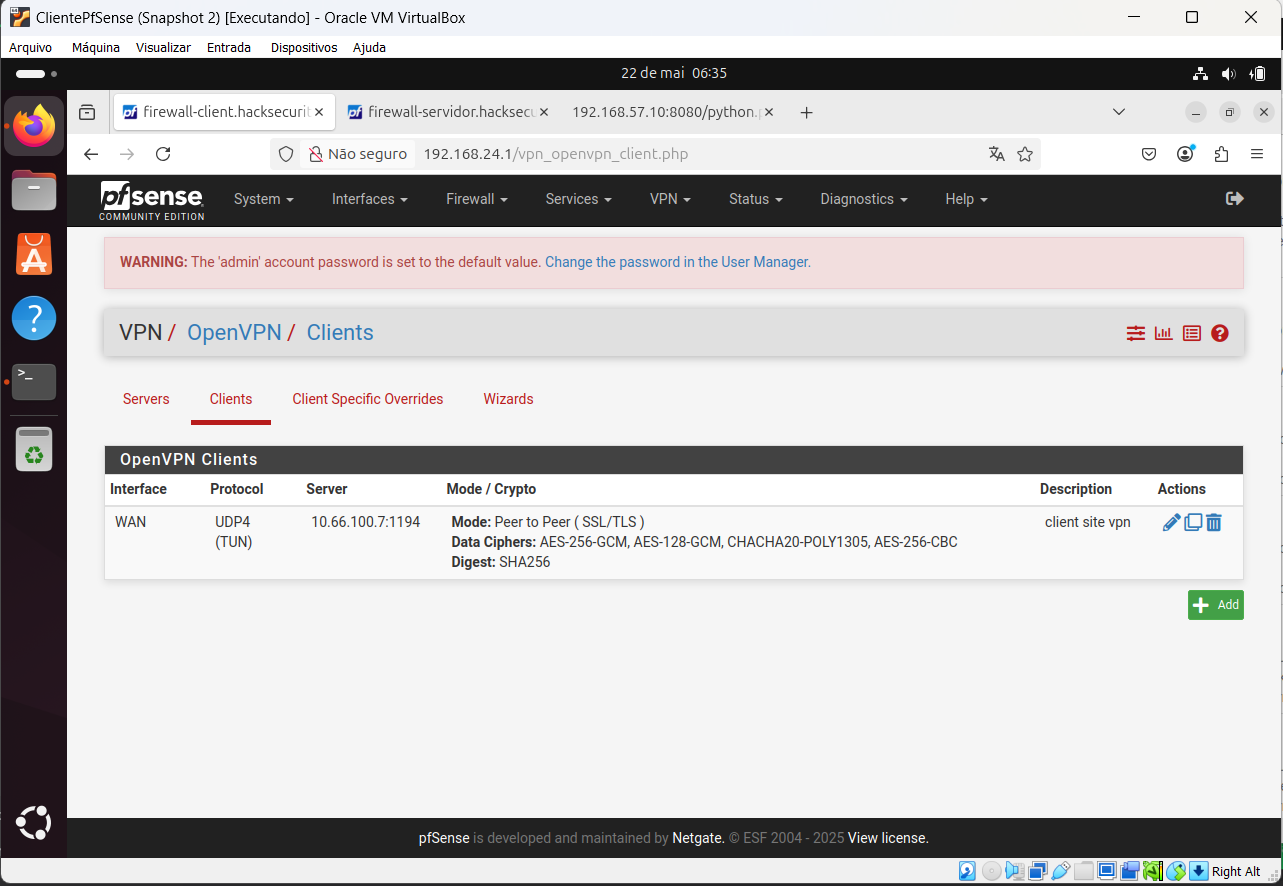
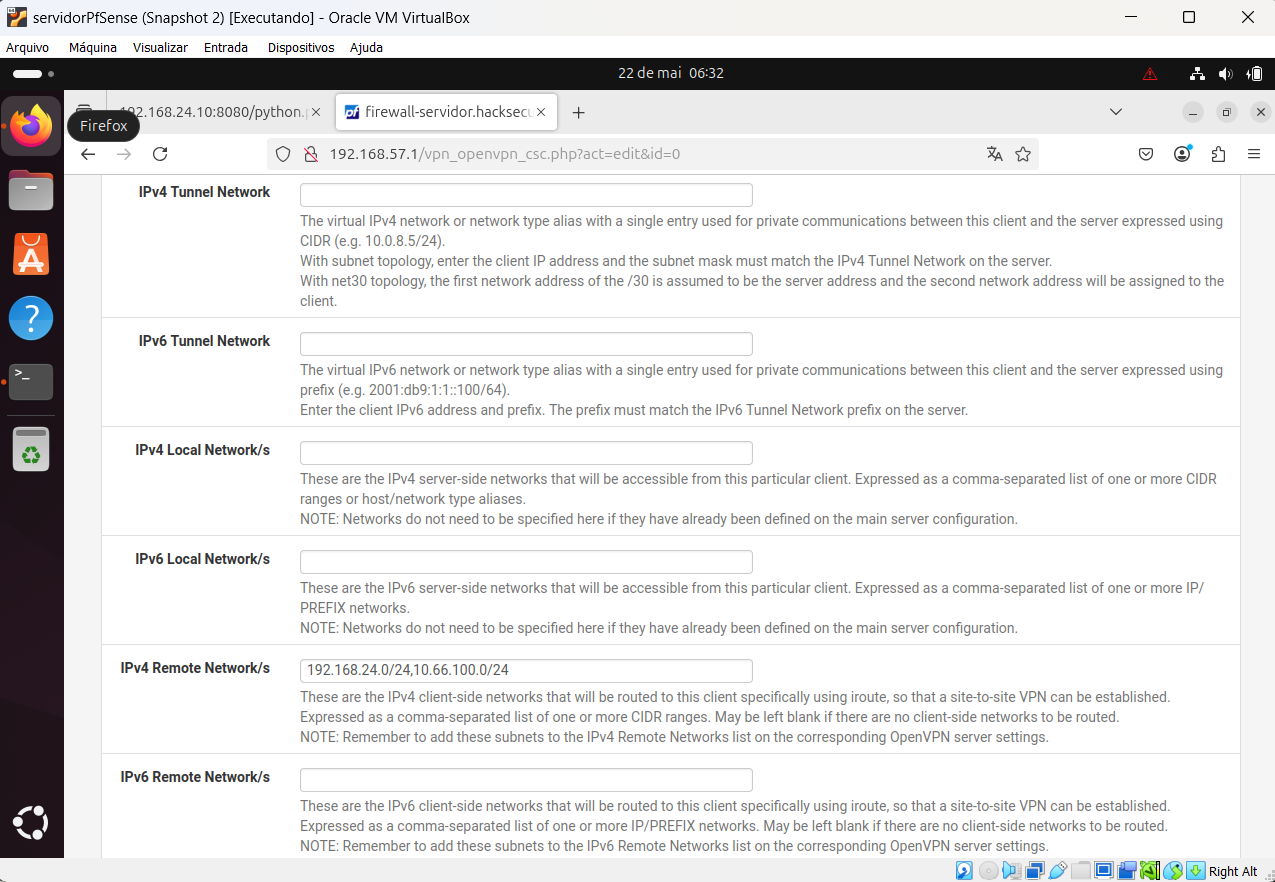
@viragomann, client OpenVPN configuration printscreen:
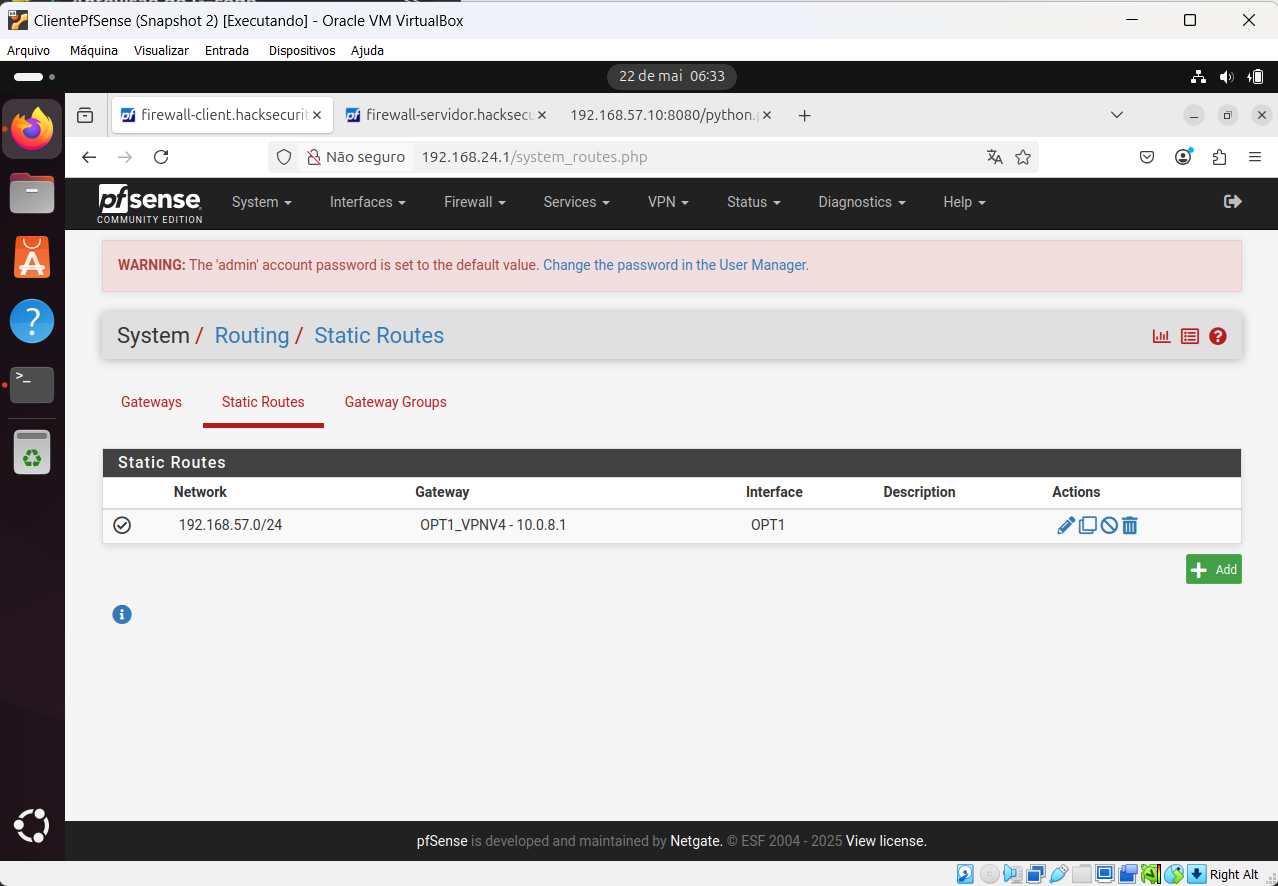
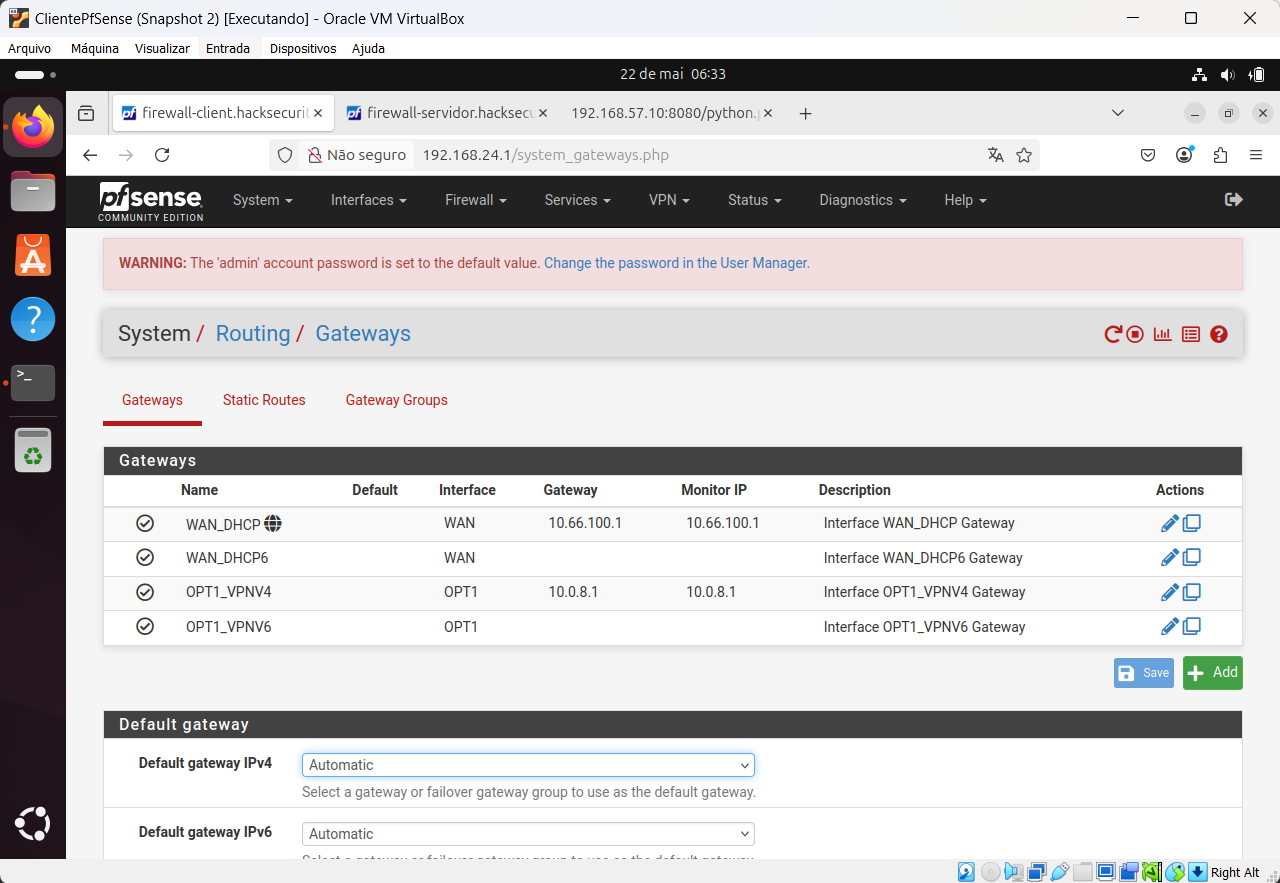
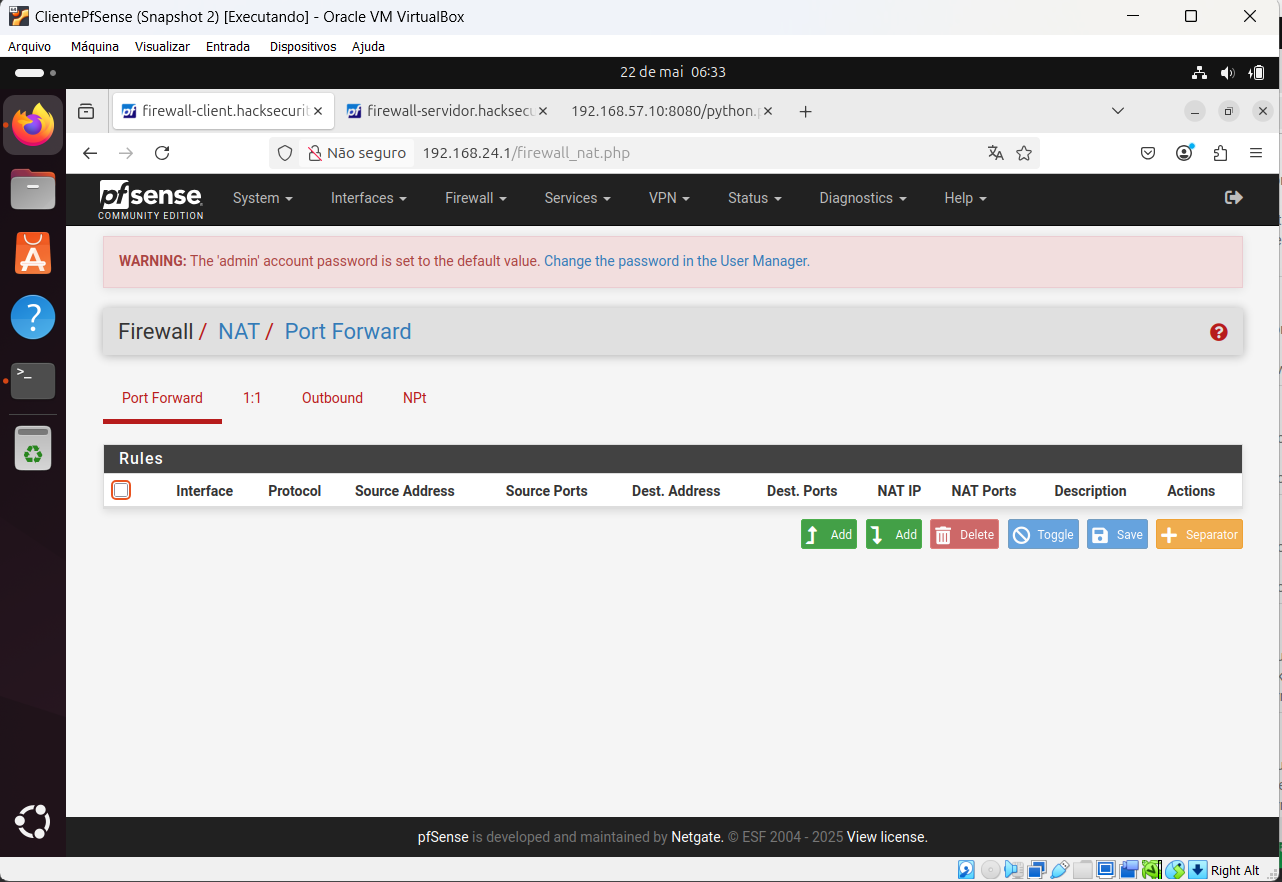
-
You might need an outbound NAT rule on the server side OpenVPN assigned interface for traffic coming from external addresses.
Without that replies from Ubuntu B may be leaving the client dircetly back to Ubuntu C since it's in the WAN subnet directly.
However, the reply-to tagging on the pass rule at the OpenVPN client should override it if you are passing traffic on the assigned interface. But it looks like you have pass all rules on the OpenVPN group interface also which do not get reply-to tags.
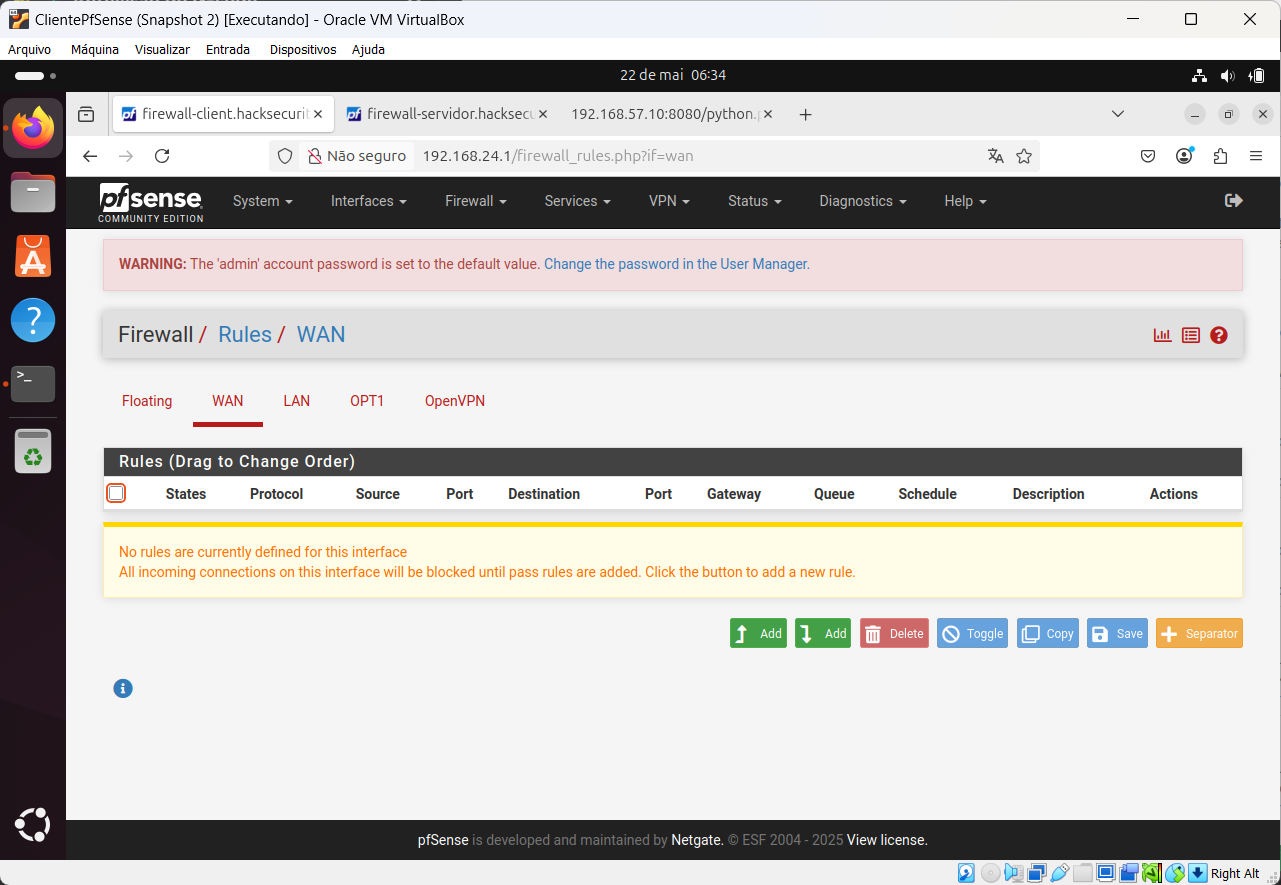
So first off disable or remove the pass rules on the OpenVPN interfaces in favour of the assigned ovpn interfaces which I assume is OPT1 at each end.
This should definitely be possible.
Check the states at both ends to see where traffic is going if it still fails.
-
-
Yeah assuming OPT1 is the assigned OpenVPN interface you must pass the traffic there and not on the OpenVPN group interface in order to get reply-to tagging on the states.
So add a pass rule on OPT1 and disable the rule on OpenVPN.
-
-
@stephenw10, thanks for your help!
I will check your recommendation when I arrive at my home.
Thanks again!
-
You still have the rules on the wrong tab at the client so reply-to will not be applied.
Edit: OK let us know if that helps.
-
@Wagner-0
I cannot give better suggestions than @stephenw10.
You need to enable the reply-to tagging on the client. This requires that the pass rule on the dedicated VPN interface has to be applied to the forwarded traffic.
However, rules on the OpenVPN tab (group) have precedence over member interface rules. That's why you have to remove these rules. -
@stephenw10, thank you very much for your help! It is working!
-
@viragomann, thank you very much for your help!