PORT FORWARDING NOT WORKING AFTER UPGRADE TO BETA 25.03
-
Hi,
I upgraded our Netgate 7100 to Pfsense Beta 25.03. However, port forwarding stopped working. Any idea how to resolve this.
Sam
-
The good news : nothing changed, so there shouldn't be any issues.
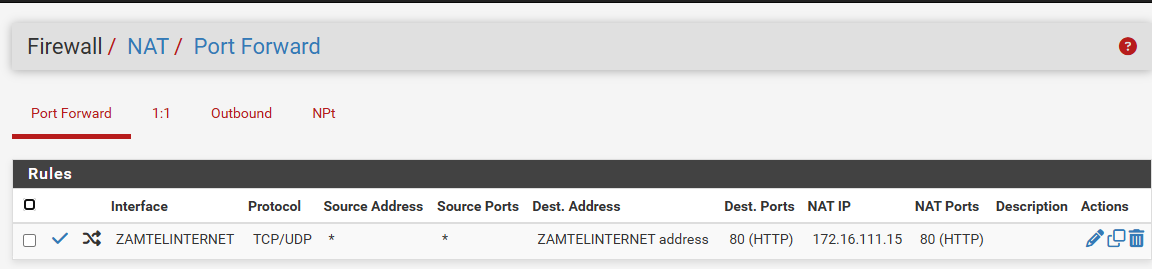
For example, I've several NAT rules in place, I use the latest 25.03 Beta version "25.03.b.20250515.1415".Best guess : check if traffic reaches your WAN ?
Use the packet capture ( Diagnostics > Packet Capture ), select the WAN, specify the correct "destination port" and NAT protocol, UDP or TCP and start the capture.
Now you can see if traffic that was natted before, even reaches pfSense.Another check : the device you NAT to (some device on a LAN ?) still use the same IPv4 ?
-
@Gertjan Hi, Thank you so much for your feedback.
I have done that and these are the results.
14:39:02.026573 IP 45.215.255.224.40542 > 172.16.111.15.80: tcp 0
14:39:07.897087 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0
14:39:08.916557 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0
14:39:09.926632 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0
14:39:10.926291 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0 -
As I don't know who 45.215.255.224 is, neither 172.16.111.15 i'll have to presume a lot.
I see a destination port 80 : that's an old web or 'http' server.
If - you tell me - 172.16.111.15 is your pfSense WAN, and 45.215.255.224 is the device with a web browser, then you've shown that the intended web traffic arrives at your pfSense WAN interface.Now : can show your NAT rule (and the auto created WAN firewall rule) ?
edit :
I've just installed the latest 5.03 beta, "25.03.b.20250610.1659", and it works well. -
Thanx once more,
45.215.255.224 is the device outside the network tring to access 172.16.111.15 which is the web server inside the betwork.
-
-
@samweli said in PORT FORWARDING NOT WORKING AFTER UPGRADE TO BETA 25.03:
172.16.111.15
Oops.
172.16.x.y is RFC1918.Knowing that you can not find RFC1918 out there on the internet.
RFC1918can't be routed on the Internet.
That means that if an RFC1918 IP like 192.168.1.1 or your 172.16.111.15 passes trough any router out there, that ones that are part of the 'Internet', it's dropped right away.This makes me wonder :
14:39:02.026573 IP 45.215.255.224.40542 > 172.16.111.15.80: tcp 0 14:39:07.897087 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0 14:39:08.916557 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0 14:39:09.926632 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0 14:39:10.926291 IP 45.215.255.224.29311 > 172.16.111.15.80: tcp 0How did you obtain these results ?
I presume now that 172.16.111.x is your pfSense LAN network, and not your WAN.
Or is 172.16.111.15 your pfSense WAN IP and you have a router in front of your pfSense ? In that case, it would be ok.edit :
Noop.
so 172.16.111.15 is your pfSense LAN ? ! -
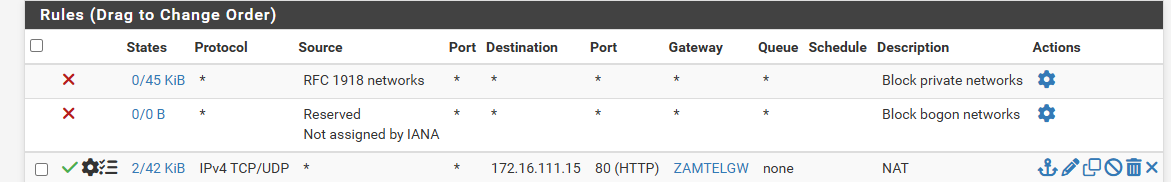
@Gertjan You are right. 172.16.111.15 is a LAN host on 172.16.0.0/16 network on the LAN side. The WAN IP is sitting on the ZAMTELINTERNET interface
-
So traffic should come in into the WAN IP, with as destination the WAN IP.
Your packet capture, you were using the WAN interface, right ? an not LAN ?From there on, the WAN IPv4 and the destination port = 80, matches with a WAN firewall rule, the firewall rule that belongs to the NAT rule. If the two match,n then the traffic is mapped to the LAN network, the IP 172.16.111.15. same port.
Btw : Web server traffic is TCP only.
This :
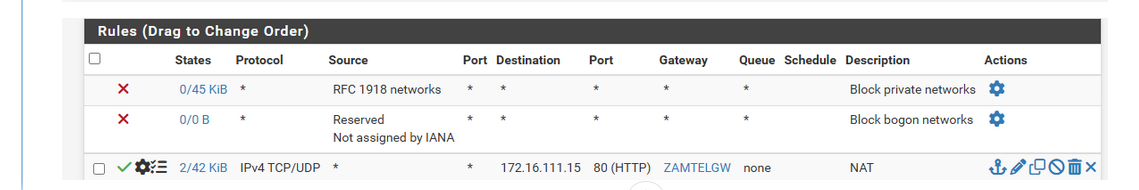
You've set a gateway ?
Please read [Port Forwarding](https://docs.netgate.com/pfsense/en/latest/nat/port-forwards.html¶ one more time. -
@Gertjan said in PORT FORWARDING NOT WORKING AFTER UPGRADE TO BETA 25.03:
Btw : Web server traffic is TCP only.
Normally I would agree with you - but there is quic now, and it is possible to run http and https over UDP.
But highly unlikely in the case of someone running something behind pfsense.
-
@johnpoz said in PORT FORWARDING NOT WORKING AFTER UPGRADE TO BETA 25.03:
but there is quic now, and it is possible to run http and https over UDP
So, first : Normally I would agree with you

But if some one would set up an apache2 or nginx on its LAN using https, quic then this person can't have problems with ancient stuff like "natting" a port.
Right ?
( I do have this feeling that the pfSense documentation isn't always clear about things. That's why I love the - old, true, but still very valid - Youtube videos on the Netgate channel )Port natting (= patting), on my ISP router, pfSense, or a high end Cisco or any other TPlink /DLink wallmart device out there : it's all the same ...
Anyway, very soon we can ditch IPv4 and Natting and things become easy for everybody ....

-
@Gertjan said in PORT FORWARDING NOT WORKING AFTER UPGRADE TO BETA 25.03:
Anyway, very soon we can ditch IPv4 and Natting and things become easy for everybody
Yeah soon ;) they have been saying that for 20+ years already.. Soon ;)