curl certificate error
-
I'm running 24.11 and recently noticed plBlocker NG spitting out this error:
[ Myip_BL_v4 ] Downloading update [ 06/4/25 00:02:12 ] . cURL Error: 60 SSL certificate problem: unable to get local issuer certificate Retry [1] in 5 seconds... . cURL Error: 60 [ 06/4/25 00:02:17 ] SSL certificate problem: unable to get local issuer certificate Retry [2] in 5 seconds... . cURL Error: 60 [ 06/4/25 00:02:22 ] SSL certificate problem: unable to get local issuer certificate |Myip_BL_v4|https://www.myip.ms/files/blacklist/csf/latest_blacklist.txt| Retry [3] in 5 seconds... .. Unknown Failure Code [0]When I look at that URL in my browser, the cert looks fine. Running the curl command interactivelt from the pfsense console yields this error:
curl https://www.myip.ms/files/blacklist/csf/latest_blacklist.txt curl: (60) SSL certificate problem: unable to get local issuer certificate More details here: https://curl.se/docs/sslcerts.html curl failed to verify the legitimacy of the server and therefore could not establish a secure connection to it. To learn more about this situation and how to fix it, please visit the webpage mentioned above. -
@codechurn Their install is missing a cert. likely your browser has it from somewhere else.
https://www.ssllabs.com/ssltest/analyze.html?d=www.myip.ms&s=146.59.166.237&hideResults=on&latest
-
Thanks for the response!
Out of curiosity, how could I go about diagnosing this type of problem on the pfSense console in the future?
-
@codechurn I think the pfBlocker dashboard widget will show download errors? Other than that, not sure what to suggest.
The missing intermediate cert can be hard to spot. It just means the web server admin installed the cert for only their web server, pulled up the site in their browser, saw it worked, and walked away, not realizing it doesn't work in some cases, depending on whether the person visiting the site has downloaded that intermediate cert before.
-
@SteveITS
Yeah, I get how to spot the download failure, that's what got me to the console on pfSense :)I was curious if there was s strategy to spot the missing intermediate cert on pfSense, since clearly the cert must somehow be present on my client machine because I did not get a cert error when investigating the url.
Is there some way to validate/verify the cert chain of a site from the pfsense console?
-
@codechurn Not sure. The curl error is basically saying it, just not in detail. The question was why the cert is detected as invalid. ("curl failed to verify the legitimacy of the server")
-
@codechurn your best bet would prob be to run https://www.ssllabs.com/ssltest/
You can get more info from openssl s_client -connect fqdnorIP:443
But it can be a bit hard to interpret - with the ssl test above its clear what is not being sent
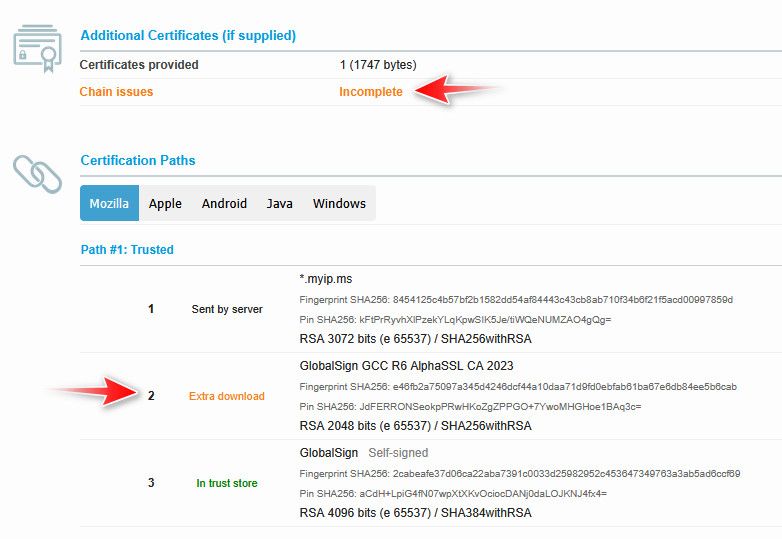
One fix is to add that missing ca to your authorities in cert manager. And have it add to trust store
But I think a piece that is missing in the info - maybe I just didn't see it, is you more than likely have to run
certctl rehash
after you add it - I did that and now your curl example that wasn't working is
[24.11-RELEASE][admin@sg4860.home.arpa]/tmp: curl https://myip.ms/files/blacklist/csf/latest_blacklist.txt # on Fri, 06 Jun 2025 15:00:40 +0000 Last 10days Blacklist IPs ############################################################################### # LIVE BLACKLIST IPv4/IPv6 ADDRESSES DATABASE # URL: https://myip.ms/browse/blacklist # Copyright 2025, Myip.ms # # File Format: ..IPAddress.. (compatible with cPanel, CSF Firewall) # # Notes for CSF Firewall: # Add/Replace Blacklist IPs to /etc/csf/csf.deny # DENY_IP_LIMIT - Maximum number of IP addresses that can be saved in /etc/csf/csf.deny file (default: 100) # To Increase Value - Go to WHM -> plugins -> configserver security & firewall -> Firewall configuration # (file: /etc/csf/csf.conf) -> and change the value to: DENY_IP_LIMIT = 0 (unlimited), after restart Firewall ############################################################################### # # Myip.ms Blacklist IPs in this List: 1,000 ip (27 May 2025 - 06 June 2025) # 27.124.71.194 3.138.195.54 185.177.72.104 119.59.99.39 103.133.143.229BTW - your url is a bit off, you have that www in there - that will cause you to just get a 301 (moved) and curl won't work.
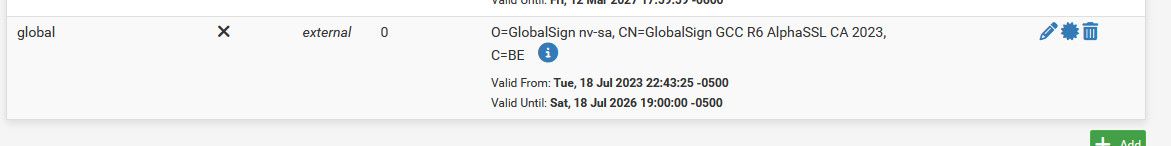
There is most likely a few ways to get the CA added to the trust store - but the cert manager gui is prob the easiest.. You can grab the missing one from firefox cert info..
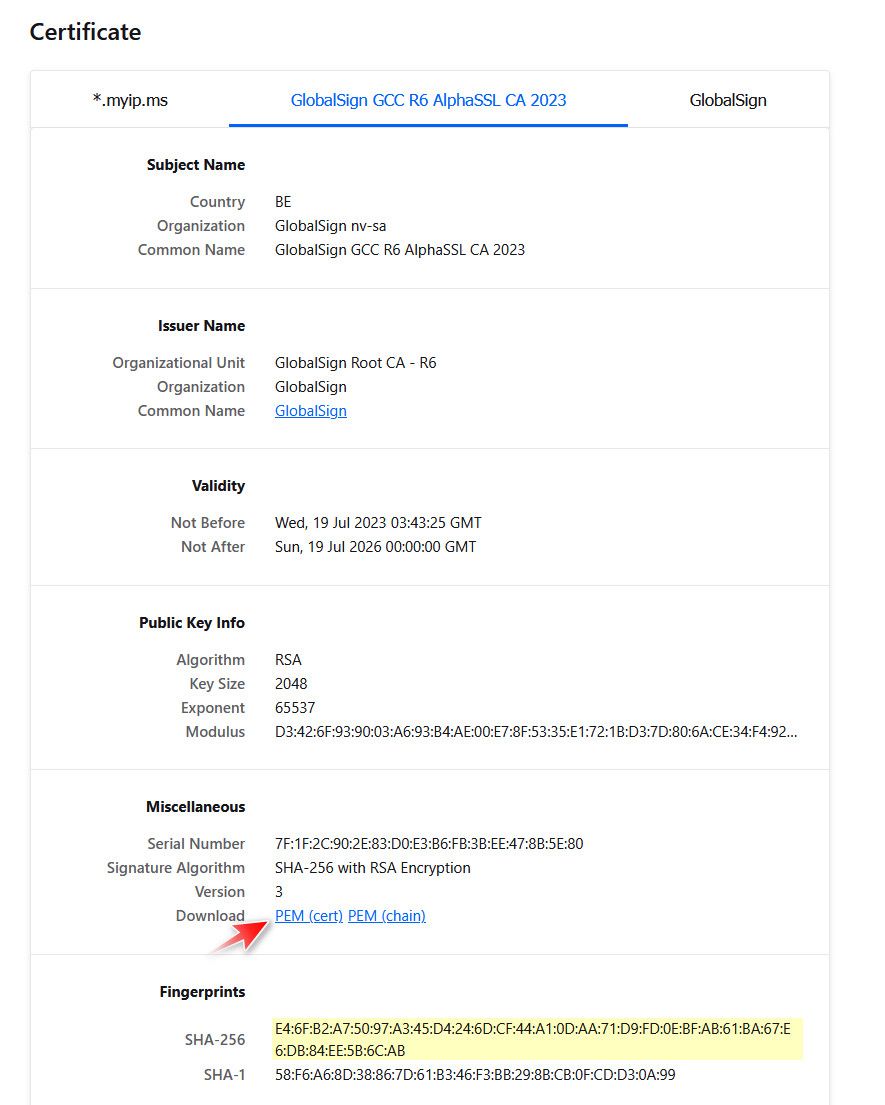
Notice the fingerprint matches the one that the ssl showed as having to be downloaded extra.
-
@johnpoz Thanks for this detail!
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
@johnpoz Can't install downloaded cert into Autorities in 25.3-BETA:
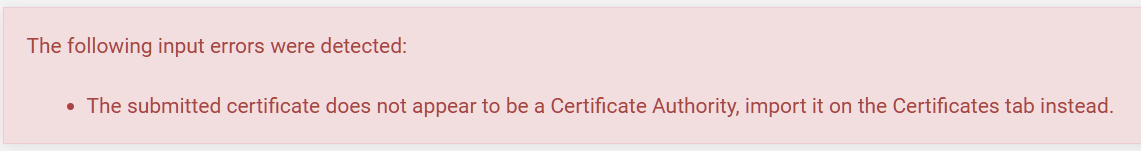
Event the Firefox cert info indicates that:
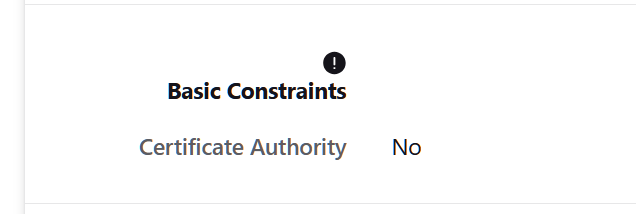
So how did you exactly managed to get it trusted?
-
@pfsjap you have to install the CA, clearly that cert your trying to install is not the CA cert.
You have to be on the CA page in firefox cert info to see the link - like in my screenshot.. Not on the cert page.
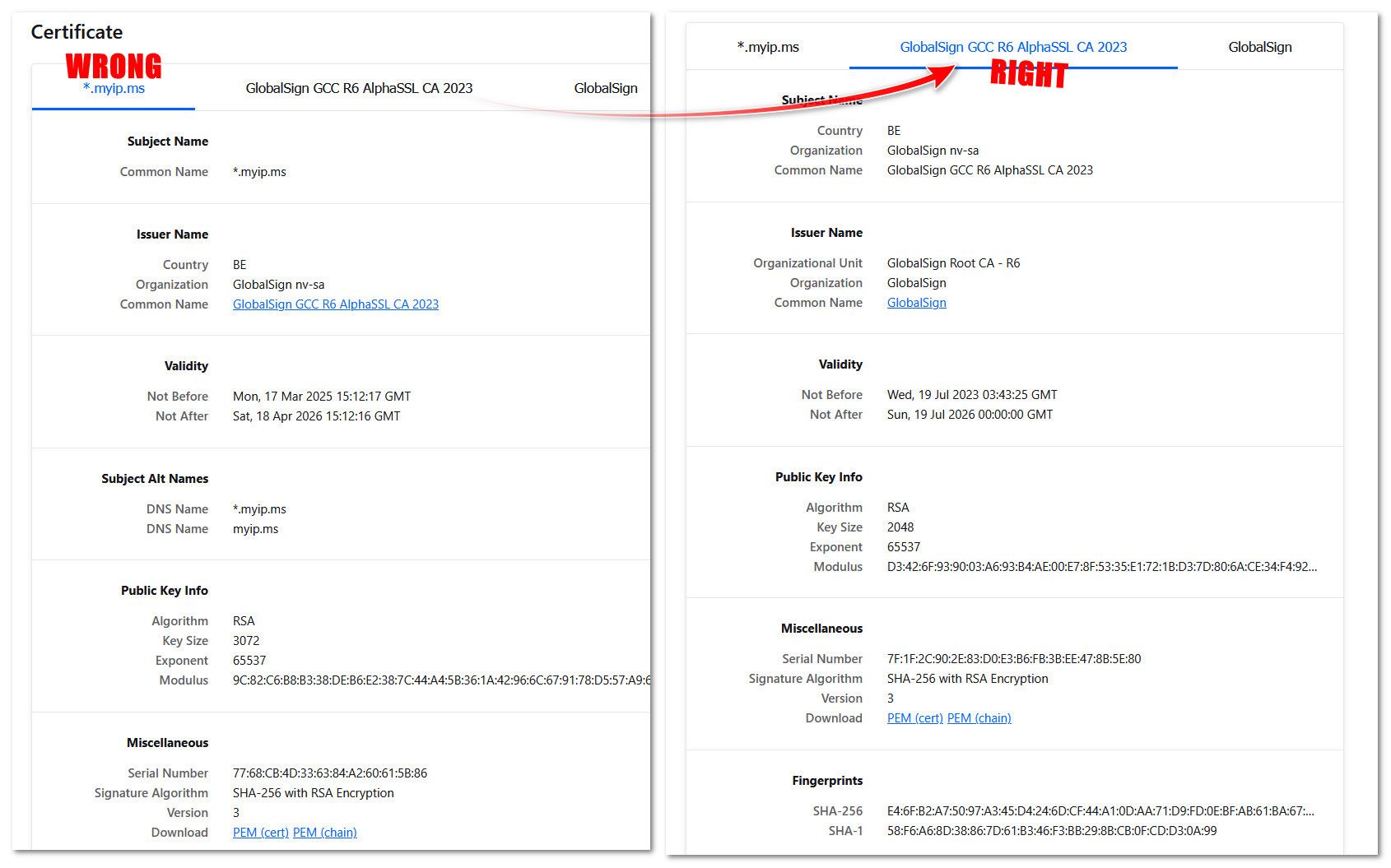
If you look above at my example - notice the fingerprint, as I pointed out is the same as what the ssl test site that told you was missing. And also notice it states it is a CA cert.
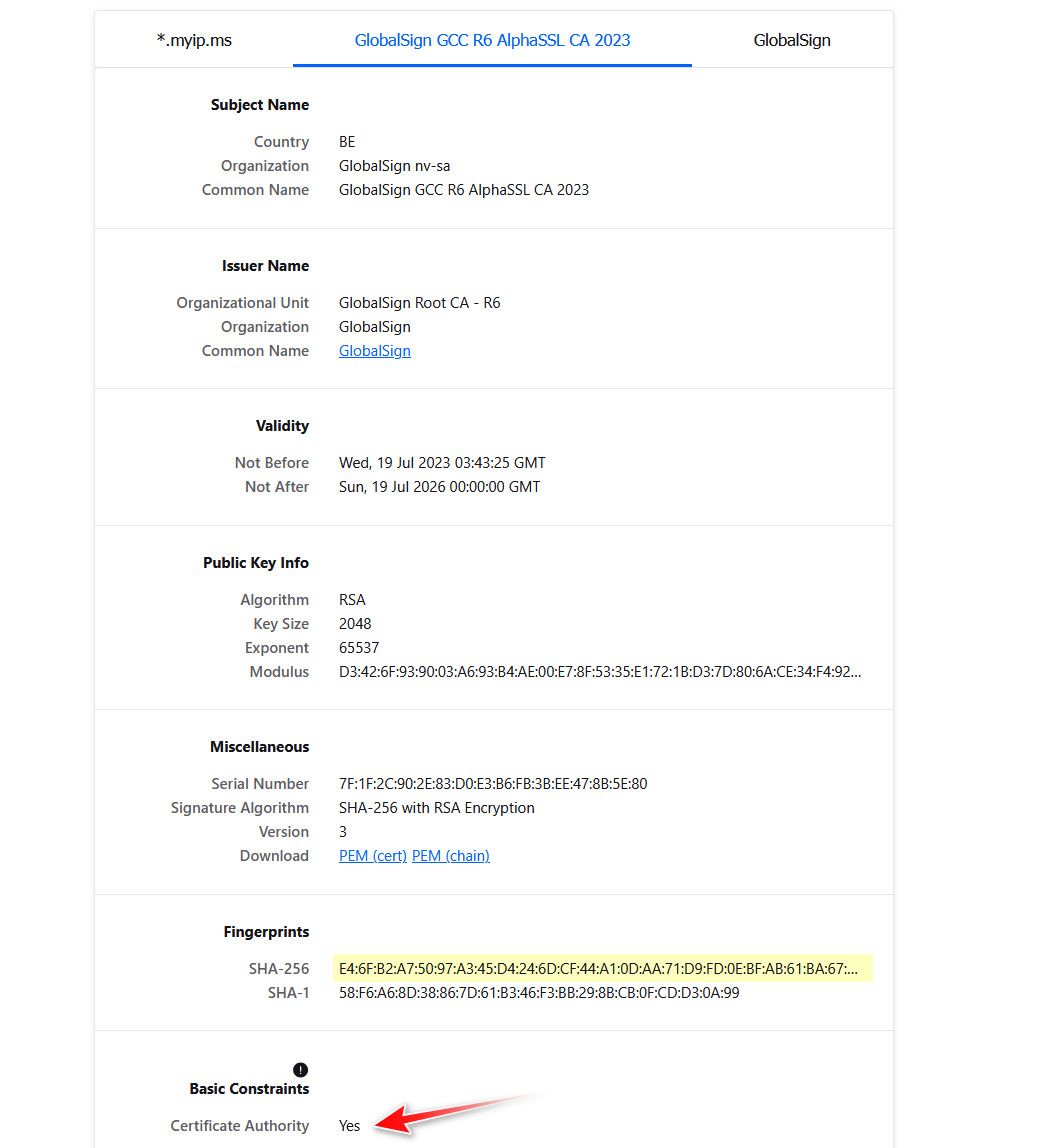
-
@johnpoz Yes, my bad, works now. Thanks!
-
@pfsjap glad you got it sorted.