How to connect to XGS-PON controller
-
I have an XGS-PON plugged into port IX1 on my 7100. I need to connect to the controller at address 192.168.11.1. I cannot figure out how to do this because that port is my WAN port and it has a WAN address.
Is there a way to route 192.168.11.0/24 traffic to the WAN VLAN and hit a device hidden there?
Could I bridge with another port without affecting performance? Only management traffic would cross the bridge. -
@AndyRH what you want is: Netgate doc: Accessing a CPE/Modem from Inside the Firewall
-
@patient0 Those instructions will not work because the physical interface is the WAN. Are there similar instructions for this situation?
-
@AndyRH said in How to connect to XGS-PON controller:
Those instructions will not work because the physical interface is the WAN
Is WAN no on a VLAN? If WAN is on a VLAN the instructions still apply, you choose the VLAN parent interface.
If not then the question would be does the XGS-GON even listen to 192.168.11.1?
-
@patient0 WAN is not a VLAN. The XGS-PON does listen on 192.168.11.1.
I am not sure how it will react if I place the WAN in a VLAN. Moving the WAN to a VLAN or bridging to an unused port will likely be what I try this weekend unless there is a better idea.At least I cannot lock myself out again messing with the WAN.

-
@AndyRH what I meant: does your ISP require you to set a VLAN to get WAN connection. Because you wrote:
Is there a way to route 192.168.11.0/24 traffic to the WAN VLAN and hit a device hidden there?
If there is no VLAN, you can try setting a virtual IP (Firewall / Virtual IPs) on the WAN interface. Not sure if you would need a static route to it or not, I'm out of my depth here, that be like having two subnets on the same ethernet cable/broadcast domain, without VLAN or anything. On LAN that does work :)
-
You can still add a VIP onto the WAN in the 192.168.11.1 subnet and pfSense will use it to try to reach the modem/module.
Make sure the VIP has the full subnet set (not /32) since it will be only IP in the subnet on the interface.
-
@patient0 The ISP is ATT and the XGS-PON emulates the ATT router. On my side there is no requirement for a VLAN. pfSense simply sees a 10Gb SFP and gets the public address. The controller is on my side of the SFP and answers on 192.168.11.1. To monitor the device I need to connect to this address which is what has started this interesting problem.
The original plan was to place it in my switch, but because of the heatsink and the slightly recessed ports on my switch made me place it directly into the 7100. On the switch it would be easy, just add a spare port to the VLAN and I am in. Right now I am thinking a bridge might be an easy solution. Right now I am collecting ideas to try Saturday when I will have time to mess with it again. -
@stephenw10 said in How to connect to XGS-PON controller:
You can still add a VIP onto the WAN in the 192.168.11.1
I tried several times with no luck. Do I need to add a route?
-
Nope not if it's in the subnet. It should just ARP for it and see it as locally connected.
Can you ping 192.168.11.1 from the VIP in pfSense via DIag > Ping?
Do you see an entry for it in the ARP table?
-
@stephenw10 said in How to connect to XGS-PON controller:
Can you ping 192.168.11.1 from the VIP in pfSense via DIag > Ping?
Dumb ass moment, I did not try from there. It does ping from pfSense. It does not ping or connect from my PC.
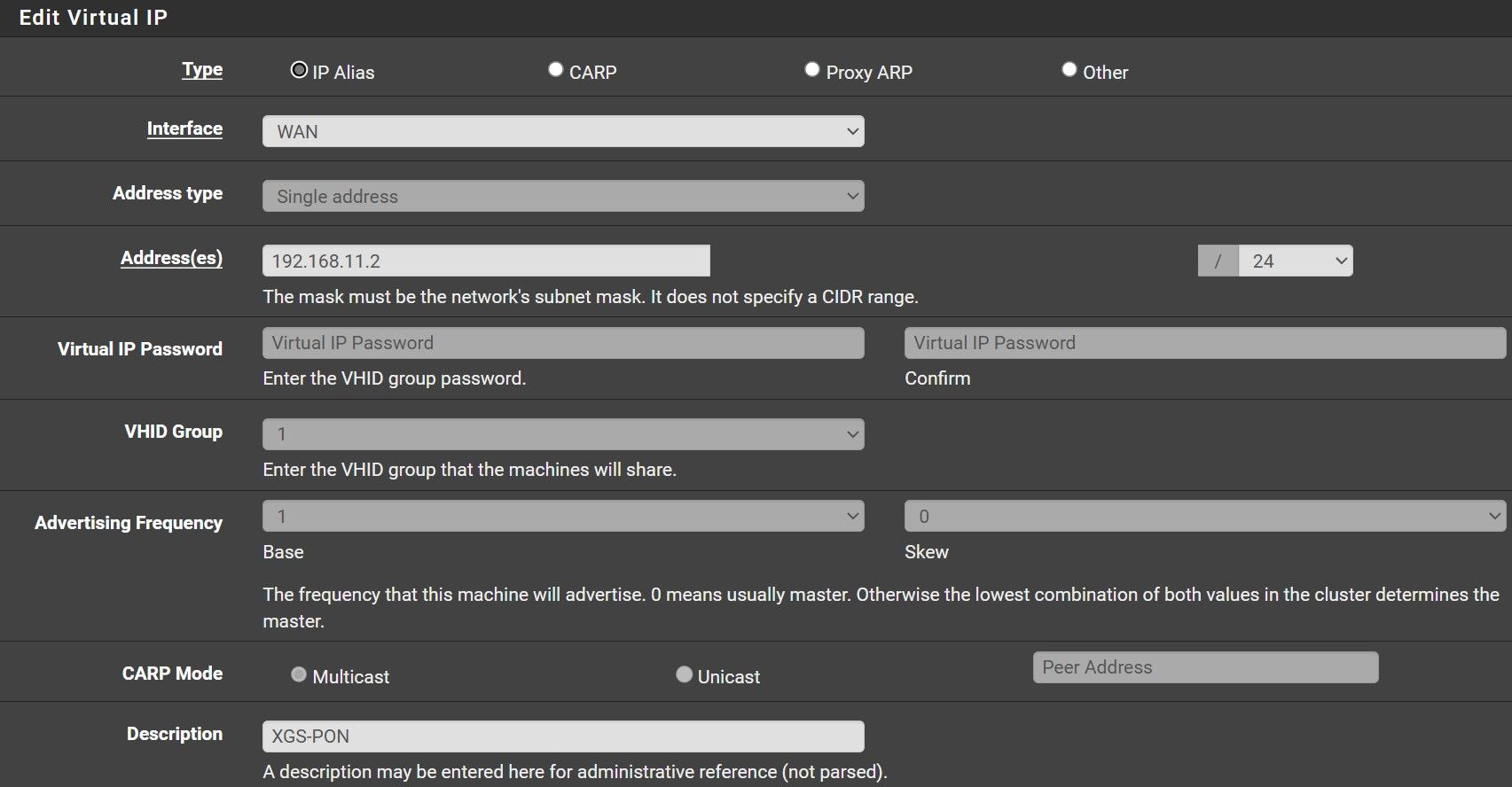
-
Ok cool. Then you probably need an outbound NAT rule on WAN to translate traffic from your LAN subnet to 192.168.11.0/24 to the VIP address.
The XPON module has no rout5e back to your LAN otherwise.
-
@stephenw10 You have found my weakness... routing.
I tried several things. This is the current outbound NAT rule and I must not understand something.

-
That rule needs to be on the WAN. It has to translate the traffic as it leaves the WAN.
-
@stephenw10 Not my day, something is blocking pings... Tried SSH and it connected.
For future generations this is the outbound NAT rule.
VLAN42 is where my PC sits.
Thank you for the help. Easier than I thought it would be.
-
 A AndyRH referenced this topic on
A AndyRH referenced this topic on
-
B BennySoh referenced this topic on