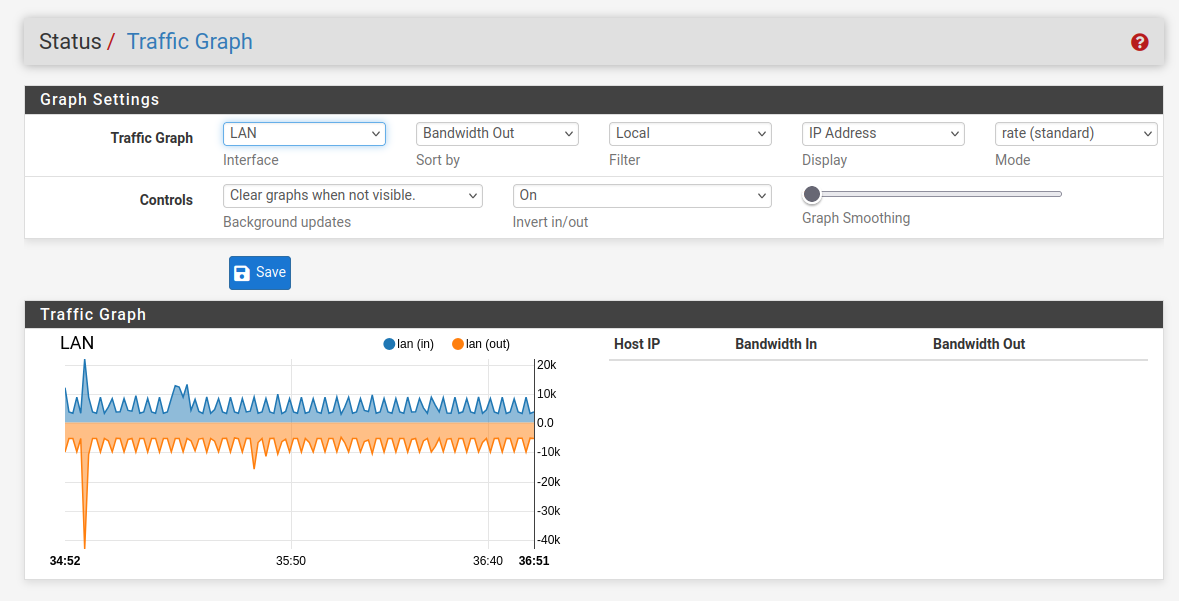
Normal traffic graph in "idle"?
-
Ask pfSense what it is ?
Select LAN, ask for "Full" (details) :
and hit the start button at the bottom of the page.
What was it ?
-
@Gertjan I see a lot of stuff but I can't really identify what it is.
I see netgate forum but also an IP from Google that according to Alienvault belongs to Certificate Subject detectportal.firefox.com and some STP and LLDP coming from my Qnap Switch. And a TCP retransmission. OTX alienvault shows a high AV detection ratio? It's whitelisted but also malicious apparently. Is that cause for concern?
I also see some 34.x.x.x adresses
How can I make sense of that capture?Unrelated I had some weird IPs from my Windows computer connecting to some random network from svchost.exe but the service was LanmanServer which is sus. I am on high alert since then.
-
What is the source of that traffic on the LAN? The pcap should show you that. Or you could check the states in Diag > States.
It's a very small amount of traffic though.
-
@stephenw10 It says mostly Application Data and the source is either my laptop or the IPs from Google etc. There is no directionality. Its a back and forth.
-
@rasputinthegreatest said in Normal traffic graph in "idle"?:
There is no directionality. Its a back and forth.
Yes, that's how traffic works. But unless you have port forwards setup or an entirely routed network then Google cannot open a connection to your LAN. It can only reply to connections your LAN side clients have opened to it. So your laptop is talking to Google.
-
@stephenw10 It looks like my laptop initiates it. I use Firefox. It seems to do a lot of talking if I look up the IPs. Like detectportal or push.services.mozilla.com and 93.243.107.34.bc.googleusercontent.com
-
Yup. All normal and expected.
-
@stephenw10 What I wonder though. I am having a double nat situation. So if I says Source and Destination in Wireshark is that actually flipped in that case? So I should see the source as the destination because behind it the actual ISP router sits?
-
Also what does [TCP Dup ACK 46#1] mean
-
@rasputinthegreatest said in Normal traffic graph in "idle"?:
It says mostly Application Data and the source is either my laptop or the IPs from Google etc. There is no directionality. Its a back and forth.
A Windows OS ? You ever heard about telemetry data ? The keylogger you installed on your PC ?

@rasputinthegreatest said in Normal traffic graph in "idle"?:
I see a lot of stuff but I can't really identify what it is.
As a router pfSense admin, it's your job to know what this 'thing' actually does.
You actually stared doing so :
@rasputinthegreatest said in Normal traffic graph in "idle"?:I see netgate forum
Normal. While you are capturing you'll see traffic from your PC going to the Netgate's IP, port 443. That your browser or a javascript in your browser chatting with that web server.
@rasputinthegreatest said in Normal traffic graph in "idle"?:
to Alienvault
What is that ?
@rasputinthegreatest said in Normal traffic graph in "idle"?:
detectportal.firefox.com
That's your browser doing auto-captive-portal detection. This is port destination 80 TCP traffic, right ?
@rasputinthegreatest said in Normal traffic graph in "idle"?:
some STP and LLDP
and you can also so DHCP, ARP, NTP, DNS requests and many more.
@rasputinthegreatest said in Normal traffic graph in "idle"?:
I also see some 34.x.x.x adresses
Nearly anything from 1.1.1.1 to 254.254.254.254.254 is possible.
Wait until you see IPv6 traffic, the one that is replacing IPv4 right now.@rasputinthegreatest said in Normal traffic graph in "idle"?:
How can I make sense of that capture?
As said above, 'IP' traffic is a very recent invention. Not that hard to understand. But it does take time to look for examples and finding out what is used when etc etc.
You were actually using all this stuff all the time. It's always a good thing to find out how things work.Btw : your "less then 10 Kbit" LAN traffic, that's more the usual back ground noise.
You LAN initiated traffic can go to the outside (== the Internet) but nothing can come in if that traffic was non-invited = not requested for by some device on your LAN.
With the packet capture you can discover what devices communicate to where and what. You'll find out that the actual data = payload is often TLS encrypted, but at least you know who is going where.@rasputinthegreatest said in Normal traffic graph in "idle"?:
Also what does [TCP Dup ACK 46#1] mean
Euh ... you've missed the original goal of Google ?!
Here is my version : Also what does TCP Dup ACK 46#1 mean ?
Most stuff can be found by copy past Google click read done.
More then often, as the question was already asked a couple of xxxxx times, you'll find answers right away. -
@rasputinthegreatest said in Normal traffic graph in "idle"?:
I am having a double nat situation. So if I says Source and Destination in Wireshark is that actually flipped in that case?
No. The source and destination are stll the same.
If you pcap on WAN you will see the traffic outside the NAT of pfSense so you only ever see the pfSense WAN IP as the local address.
If you pcap on LAN you will see the internal client IPs that are sending and receiving.
-
@Gertjan said in Normal traffic graph in "idle"?:
A Windows OS ? You ever heard about telemetry data ? The keylogger you installed on your PC
It's Ubuntu though ;)
@Gertjan said in Normal traffic graph in "idle"?:
What is that ?
A website to check what is behind an IP. For example:
https://otx.alienvault.com/indicator/ip/34.149.144.89@Gertjan said in Normal traffic graph in "idle"?:
That's your browser doing auto-captive-portal detection. This is port destination 80 TCP traffic, right ?
Yep port 80 traffic
@Gertjan said in Normal traffic graph in "idle"?:
You were actually using all this stuff all the time. It's always a good thing to find out how things work.
I am still trying to figure things out. I haven't gotten into the packet capture part yet. Only superficially by checking Snort captures. I also googled what TCP Dup ACK is but I don't know if it is something to worry about or a normal occurance. The last couple of days I saw 3 out of 5 Windows computers make outgoing connections to malicious IPs that are flagged on otx.alienvault and it makes me worried. Even on a fresh Windows install I had this happen by a service that should only communicate on LAN (Windows LanmanServer). I just blocked the whole IP range to be safe. It was also blocked by Snort with "ET INFO Packed Executable Download", Misc activity 3. I hope it's just a false positive.
@stephenw10 said in Normal traffic graph in "idle"?:
No. The source and destination are stll the same.
Ok great. Thank you :)