IPv6 firewall rules with logging disabled still generating logs
-
Description:
I'm running pfSense 2.8.0-RELEASE and experiencing an issue where IPv6 traffic continues to be logged despite having explicit Block rules with logging disabled.
Here is my config:
- Both LAN and WAN interfaces have IPv6 Block rules configured
- Action: Block
- Address Family: IPv6
- Protocol: Any
- Source: Any (LAN subnets for LAN rule)
- Destination: Any
- Log: UNCHECKED (logging explicitly disabled)
- Rules are positioned at the top of their respective interface rule lists (but for LAN, there is an ipv4 rule which always put this on position 2, not counting the anti-lockout rule, see picture below and for WAN, there is at the top the rules for private network and bogon networks which are not "surpassable")
Issue:
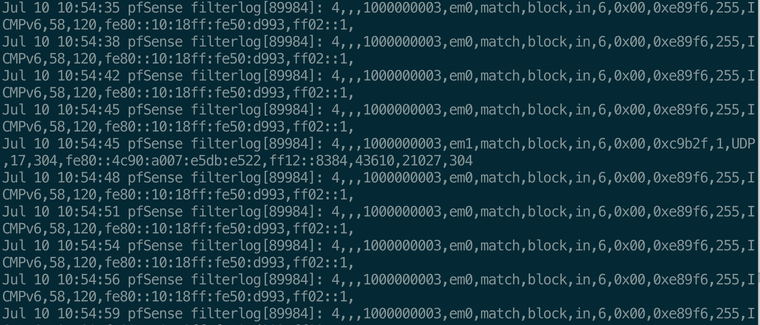
Despite these rules, IPv6 traffic continues to appear in /var/log/filter.log (picture below)What I've tried:
- Verified rules are properly configured (Block + Log unchecked)
- Placed IPv6 block rules at top of interface rule lists (with exceptions mentionned supra)
- Applied changes and restarted pfSense
- Removed IPv6 gateways
- No floating rules interfering
- Rules show as active and correctly configured in WebGUI
Question:
Are there system-level IPv6 logging rules that override custom interface rules? How can I completely disable IPv6 logging when I have explicit Block rules with logging disabled? For the time being, I don't use IPv6 at allAny insight would be appreciated.
Plicplic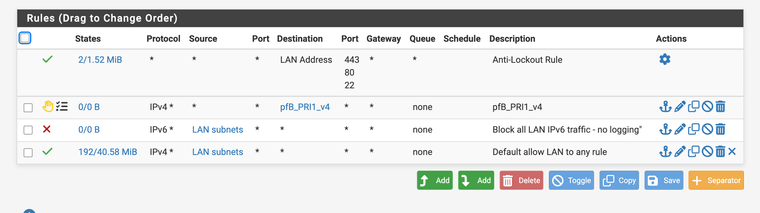
-
The traffic you see logged is sourced from some clients link-local address which is not in the LAN subnet. So your rule doesn't match it.
Try changing the rule to any source.
-
I will try that right now, thanks Stephen!
-
Follow-up: Even after changing Source to "Any" and disabling all IPv6 services, the issue persists.
Additional steps taken:
- Changed LAN rule Source from "LAN subnets" to "Any"
- Disabled DHCP6 on WAN interface (set to None)
- Disabled IPv6 Track Interface on LAN (set to None)
- Rebooted pfSense completely
Current status:
IPv6 traffic continues to be logged on both interfaces despite Block rules with logging explicitly disabled:Here, some examples:
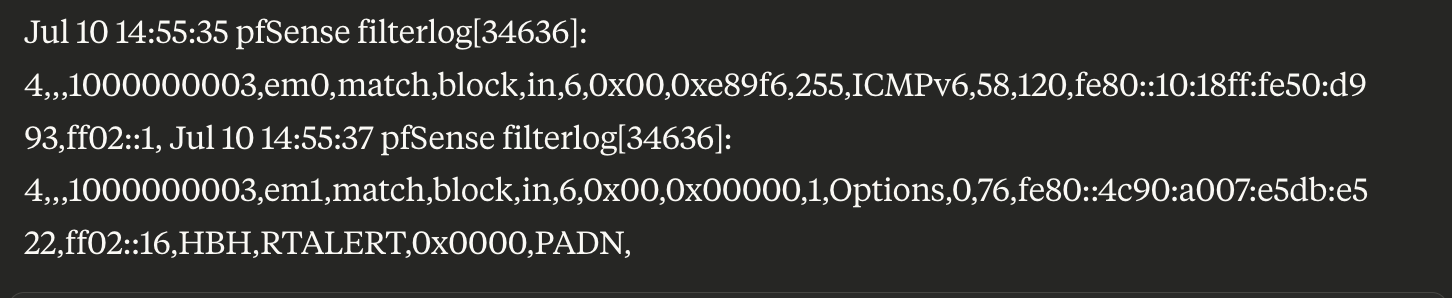
Both WAN and LAN rules are configured as:
- Action: Block
- Address Family: IPv6
- Protocol: Any
- Source: Any
- Destination: Any
- Log: UNCHECKED
Question: Is there a system-level IPv6 logging mechanism in pfSense that overrides custom firewall rules? The traffic is being blocked correctly but continues to generate logs despite logging being disabled in the rules.
Additional guidance would be appreciated!
-
You can see that it's matching the default IPv6 block rule there. Which implies it's not matching your custom rule. It's much easier to see that in the gui log.
Which interface is WAN there?
The second log looks like it has IP Options so you would need a rule with that set to match it.
-
You're right - here's the GUI log analysis:
All entries show my custom rules "Block all IPv6 (1000000003/4)" - NOT default rules.And em0 is the Wan interface.
Main issue: My IPv6 Block rules have "Log: UNCHECKED" but continue logging anyway.
IP Options question: Should I configure specific IP Options settings for IPv6 rules? Currently using Protocol: Any with default options.
This looks like IPv6 logging ignores the disable setting in 2.8.0.
-
You will need block rules for both to match traffic with and without IP Options for that I believe.
How does that actually appear in the GUI though? If it's matching the rule I'd expect it not to log. Though there have been some changes to the behaviour of IP Options in pf.
-
After extensive testing, I suspect this is a possible pfSense bug and not a configuration issue. But of course, I'm no specialist and will comply with any further test You could propose!
Complete test sequence performed:
- Initial setup: IPv6 Block rules on both WAN and LAN interfaces with "Log: UNCHECKED"
- Applied stephenw10's suggestion: Changed LAN rule Source from "LAN subnets" to "Any"
- Created separate IP Options rules: Added distinct rules for traffic with and without IP Options as recommended
- Tested pfBlockerNG theory: pfBlockerNG automatically repositioned itself above our rules after cron updates
- Final isolation test: Completely disabled pfBlockerNG service to eliminate any interference
Results:
Throughout ALL tests, IPv6 traffic continues logging with identical behavior:
- Same rule IDs (1000000003/1000000004) matching in GUI logs
- Same traffic patterns (ICMPv6 Neighbor Discovery, mDNS on port 5353)
- Same logging frequency on both em0 (WAN) and em1 (LAN) interfaces
Current status with pfBlockerNG disabled:
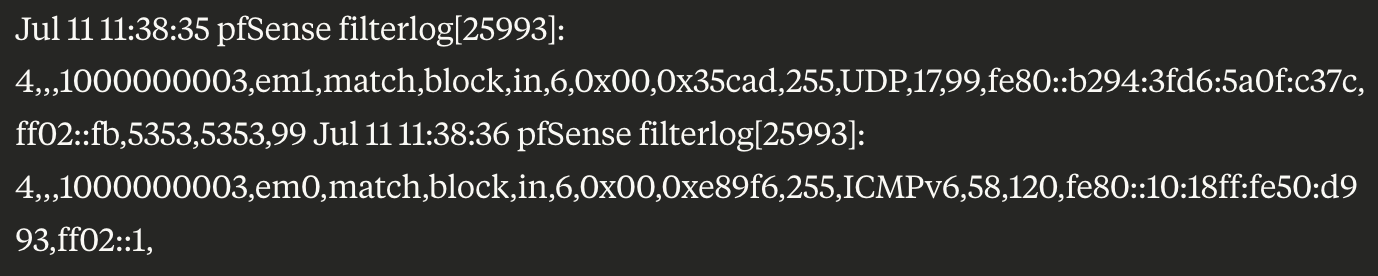
Conclusion:
IPv6 Block rules ignore the "Log packets that are handled by this rule" UNCHECKED setting. The rules correctly match and block traffic but continue generating logs despite logging being explicitly disabled.
Configuration is correct, pfBlockerNG is not the cause, and the issue persists across multiple rule variations and system restarts.
Is this a known issue with IPv6 logging in pfSense 2.8.0?
-
It's probably this: https://redmine.pfsense.org/issues/16068
But I can't see from the raw log output if you are seeing it on traffic with IP Options. It looks like you haven't. And it's UDP and ICMP which normally wouldn't so that's confusing.
Try this. Go to Status > Filter Reload and reload the ruleset. Make sure it's actually loading without errors.
Then at the CLI run:
pfctl -vsrCheck the actual running rules for 1000000003/4.
-
-
Filter reload shows no error while reloading.
-
pfctl -vsr | grep -A 5 -B 5 "1000000003"
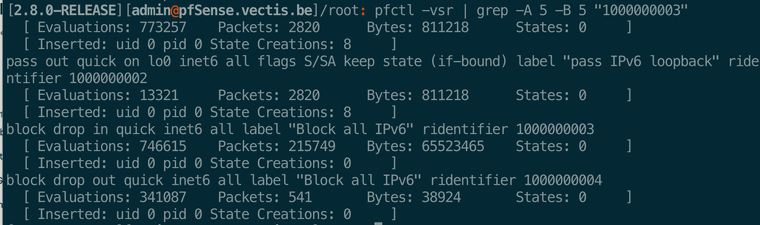
Log is unchecked in every rule for Wan and LAN in the firewall rules
- I found this in Status --> System.logs --> Settings (and changed some checks)
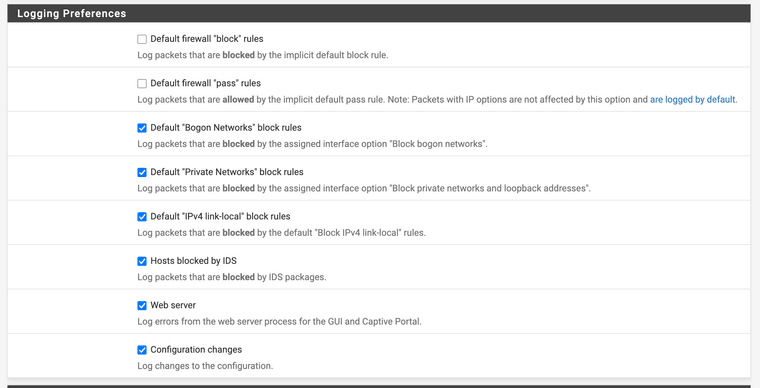
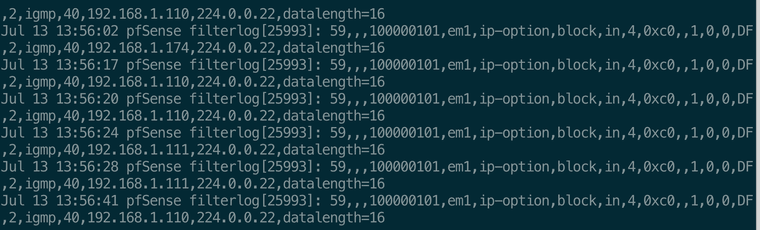
And now filter.log is only populated with ipv4
-
-
@plicplic yeah when you block all IPv6 it creates those hidden block all IPv6 rules. And yeah most likely going to create a lot of noise in the logs.
Those blocks your still seeing to to 224.0.0.22 are multicast with ip-option set but not allowed - you could change your rules to either create one that blocks but doesn't log, or your allow rule to allow ip-option being set
-
Yup, what I missed here is that whilst it's not hitting the default block rule it's in fact also not hitting your custom rules. It's actually the hidden block all v6 rules that are added when you unset 'allow IPv6'.