Only reverse lookups for localdomain from client, external domains work (i.e. google.com)
-
Settings:
pfSense 2.8.0 - LAN IP address 192.168.1.254General Setup -> DNS -> 192.168.1.1 (main DNS server)
General Setup -> DNS Server Override -> Deactivated
General Setup -> DNS Resolution Behavior -> Use remote DNS, ignore local DNSDNS Forwarder -> Enabled
Problem:
Clients can only do reverse lookups for localdomain. But for external domains both forward and reverse lookups work.Testing DNS from the pfSense itself (Diagnostics -> DNS lookup) works for localdomain and external domains likewise. It shows the configured DNS server 192.168.1.1 as the source for the replies.
nslookup Example
> server 192.168.1.254 Default server: 192.168.1.254 Address: 192.168.1.254#53 > hostname.localdomain Server: 192.168.1.254 Address: 192.168.1.254#53 *** Can't find hostname.localdomain: No answer > 192.168.1.50 50.1.168.192.in-addr.arpa name = hostname.localdomain. Authoritative answers can be found from: > google.com Server: 192.168.1.254 Address: 192.168.1.254#53 Non-authoritative answer: Name: google.com Address: 142.250.185.174 Name: google.com Address: 2a00:1450:4001:811::200e > -
@AWeidner said in Only reverse lookups for localdomain from client, external domains work (i.e. google.com):
nslookup Example
> > server 192.168.1.254 > Default server: 192.168.1.254 > Address: 192.168.1.254#53 > > hostname.localdomain > Server: 192.168.1.254 > Address: 192.168.1.254#53 > > *** Can't find hostname.localdomain: No answerI don't think, that there is much pfSense can do to make your DNS server giving a correct response.
pfSense just runs a DNS forwarder, forwarding any DNS request to your server.Obviously it doesn't know the host name.
-
@AWeidner if your fowarding - be it a local name server or one out on the internet. Anything that returns rfc1918 would be a rebind.
You would need to turn off rebind protection for that specific .localdomain, or turn it off completely
https://docs.netgate.com/pfsense/en/latest/services/dns/rebinding.html
but if you have a client directly asking your name server 192.168.1.1 and you do not get an answer - then yeah something wrong with that NS.
But you state that diag dns lookup works - which would be a direct query from pfsense to your ns so that wouldn't be rebind.
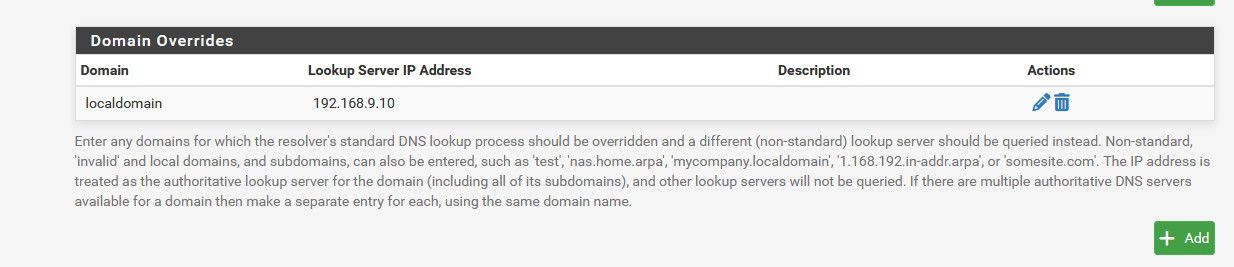
edit: here I setup local dns for .localdomain. And told pfsense to forward to it 192.168.9.10 to resolve localdomain
See it resolves something that is not rfc1918
> nonrfc1918.localdomain Server: sg4860.home.arpa Address: 192.168.9.253 Non-authoritative answer: Name: nonrfc1918.localdomain Address: 1.2.3.4but if I ask it for something that would return rfc1918 it would be rebind.. But when you setup a manual forward for the domain like I did it adds that to the conf
cat /var/unbound/unbound.con
# DNS Rebinding # For DNS Rebinding prevention private-address: 127.0.0.0/8 private-address: 10.0.0.0/8 private-address: ::ffff:a00:0/104 private-address: 172.16.0.0/12 private-address: ::ffff:ac10:0/108 private-address: 169.254.0.0/16 private-address: ::ffff:a9fe:0/112 private-address: 192.168.0.0/16 private-address: ::ffff:c0a8:0/112 private-address: fd00::/8 private-address: fe80::/10 # Set private domains in case authoritative name server returns a Private IP address private-domain: "localdomain" domain-insecure: "localdomain"But if your forwarding everything - it wouldn't so you would have to manually add it to your custom options. Or just manually setup a dns override for your domain and then it would auto add
-
@johnpoz
Thank you for the extensive summary. I was able to get it to work with the examples provided in the linked section of the documentation.rebind-domain-ok=/example.com/ rebind-domain-ok=/dnsbl.example/Using nslookup to directly query the server (192.168.1.1) pfSense forwards to, works. Forward and reverse lookups are resolved.
It just seems counterintuitive to me, that i have to add settings if all i want is to forward all DNS requests coming into pfSense and maybe (as a bonus) cache the results.
-
@AWeidner its just pfsense trying to proect you against a rebind. When you foward to something that is normal some external public NS - which normally should not be returning rfc1918.
You might want to read some of the history of rebind attacks. And why this good protection to have in place.