Looking for few pointers getting Suricata on PFSense to talk to my Security Onion box.
-
Hello, how would I go about sending my Suricata data into S.O.? I DID open the syslog firewall port in S.O., as per the S.O. web site, and locked it down to only allow the router's IP with a net mask of /32. However, I am kind of lost on the PFSense side.
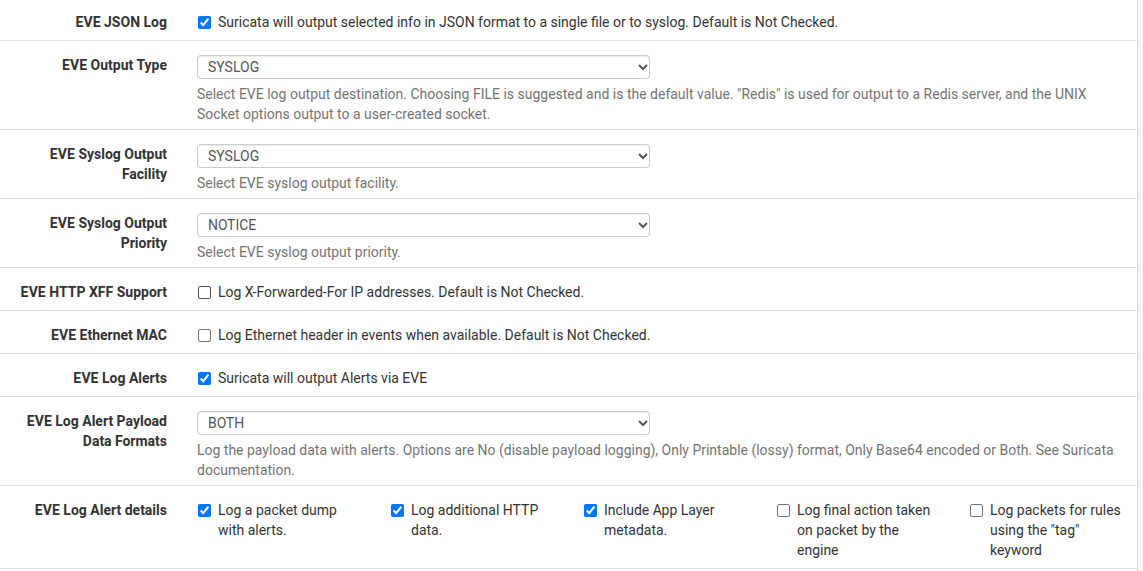
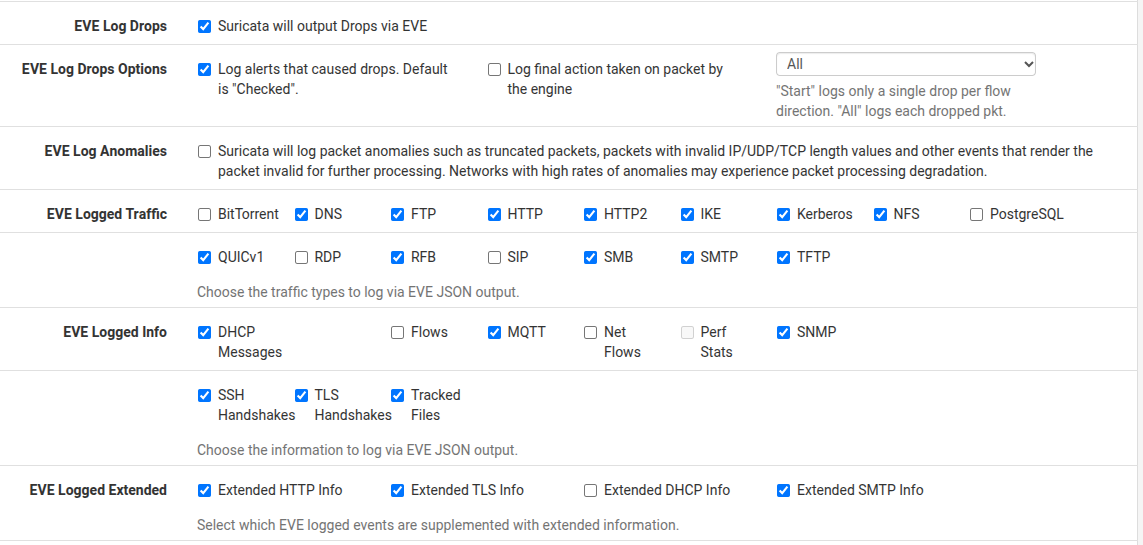
-
Forgot a few screenshots, and couldn't edit my original post:
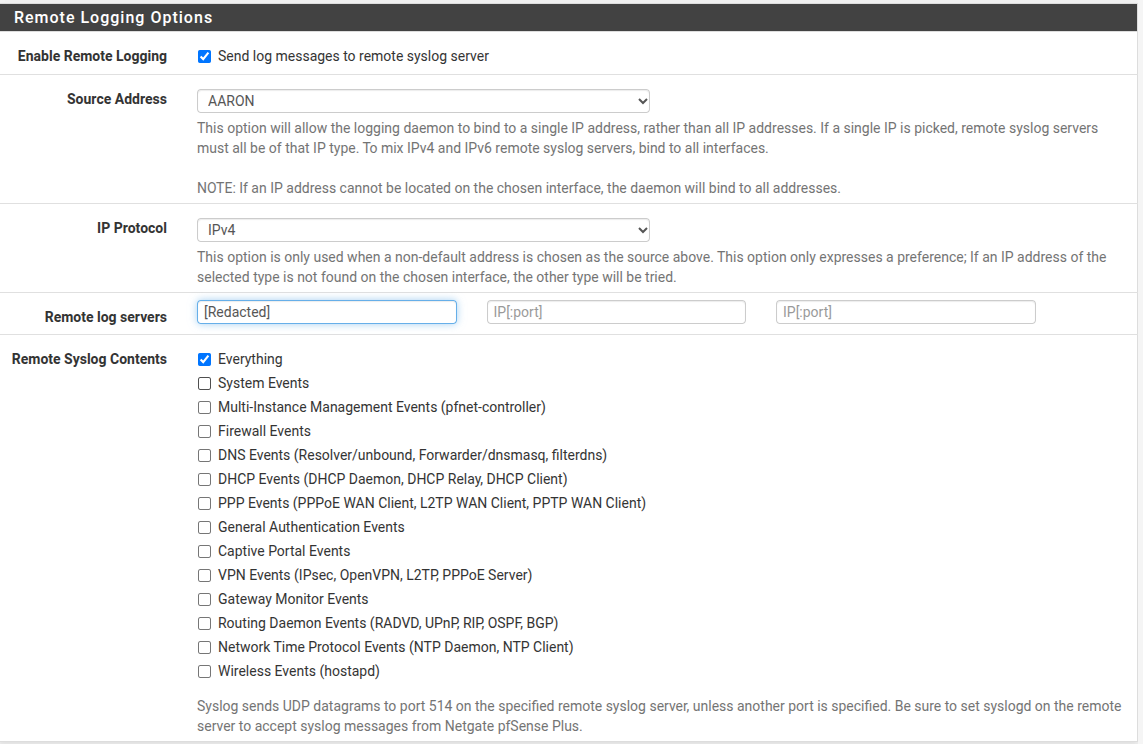
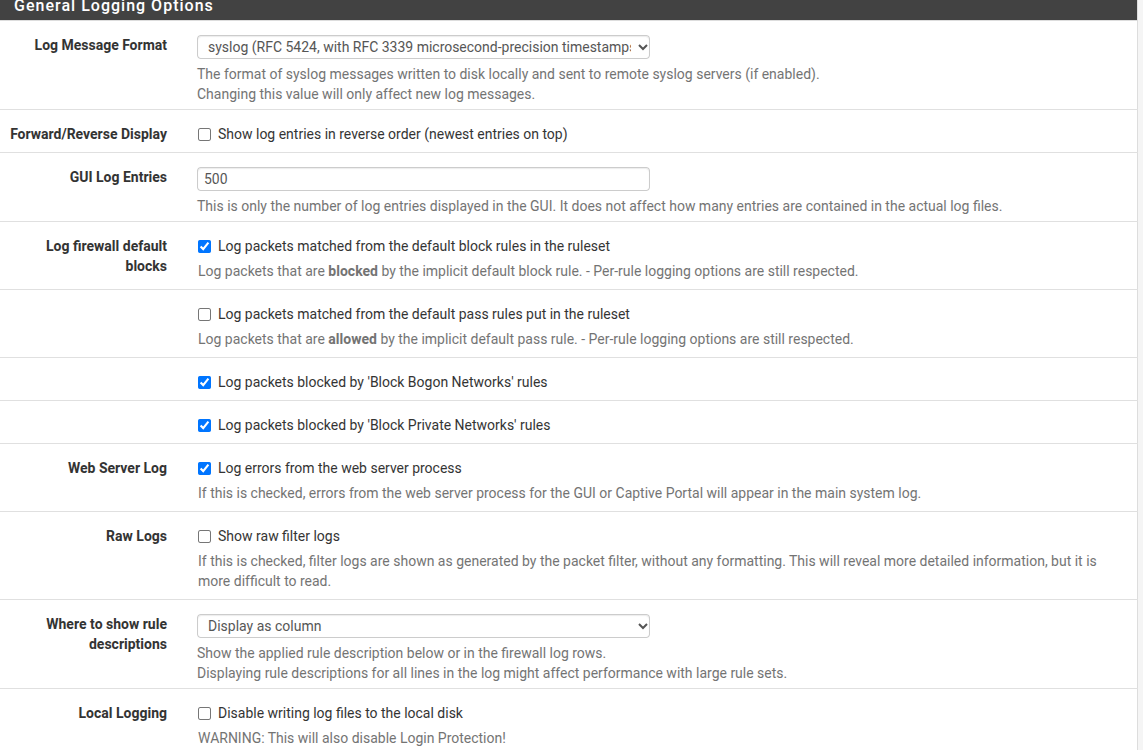
-
Your pfSense settings appear to be correct, but be aware that
syslogon FreeBSD can impose a size limit on each syslog record. I seem to recall it is 480 bytes. It's actually related to the maximum "safe size" of a UDP datagram when the MTU is not known. So, this means that potentially a large chunk of each EVE JSON record will be truncated when sent oversyslog.You will also need to be sure the Security Onion
syslogdaemon is configured to accept remote connections (including the port, which is normally 540) and that any firewall running on the Security Onion appliance has an appropriate pass rule enabled for the traffic.Better to install a third-party log scraper package and export the text EVE JSON log to your Security Onion box. Unfortunately, there is no natively available pfSense package for that. You will need to carefully cobble something together independently. A Graylog client is popular these days for such a task.
-
Ok, so I've been researching the topic. It seems SO has an integration for PFSense. However, the FreeBSD implementation of Syslog is not optimal for this purpose, as mentioned above.
Although I am comfortable with CLI Linux, I am effectively a Newbie with regard to BSDs.
My next question is: What would be the least invasive method as far as the PFSense Box to export just the Suricata logs? I believe I saw an option to log to a Unix Socket. Would that be helpful coupled with something like Netcat? I'm not necessarily looking for help with such a feat, just wondering if such would likely be fruitful, or am I just chasing the infamous wild goose?
-
@aaronouthier said in Looking for few pointers getting Suricata on PFSense to talk to my Security Onion box.:
Ok, so I've been researching the topic. It seems SO has an integration for PFSense. However, the FreeBSD implementation of Syslog is not optimal for this purpose, as mentioned above.
Although I am comfortable with CLI Linux, I am effectively a Newbie with regard to BSDs.
My next question is: What would be the least invasive method as far as the PFSense Box to export just the Suricata logs? I believe I saw an option to log to a Unix Socket. Would that be helpful coupled with something like Netcat? I'm not necessarily looking for help with such a feat, just wondering if such would likely be fruitful, or am I just chasing the infamous wild goose?
I recommend exporting the EVE JSON log as that will be the most comprehensive. To export to a UNIX socket, change the EVE OUTPUT TYPE setting to UNIX socket. You will need to manually create the socket and give it a name. It will be up to you then to "receive" the socket data stream and redirect it elsewhere (seems you want it remote for your case to Security Onion).