DNS Issues After Upgrading to 25.07
-
About the (restarts) :
Check with the system log what happened, why unbound was told to restart.
A very common reason is : an interface used by unbound was taken down for a moment.
If possible, stop this from happening.About the dig : dig bypasses the resolver (unbound), it does all the work 'itself'.
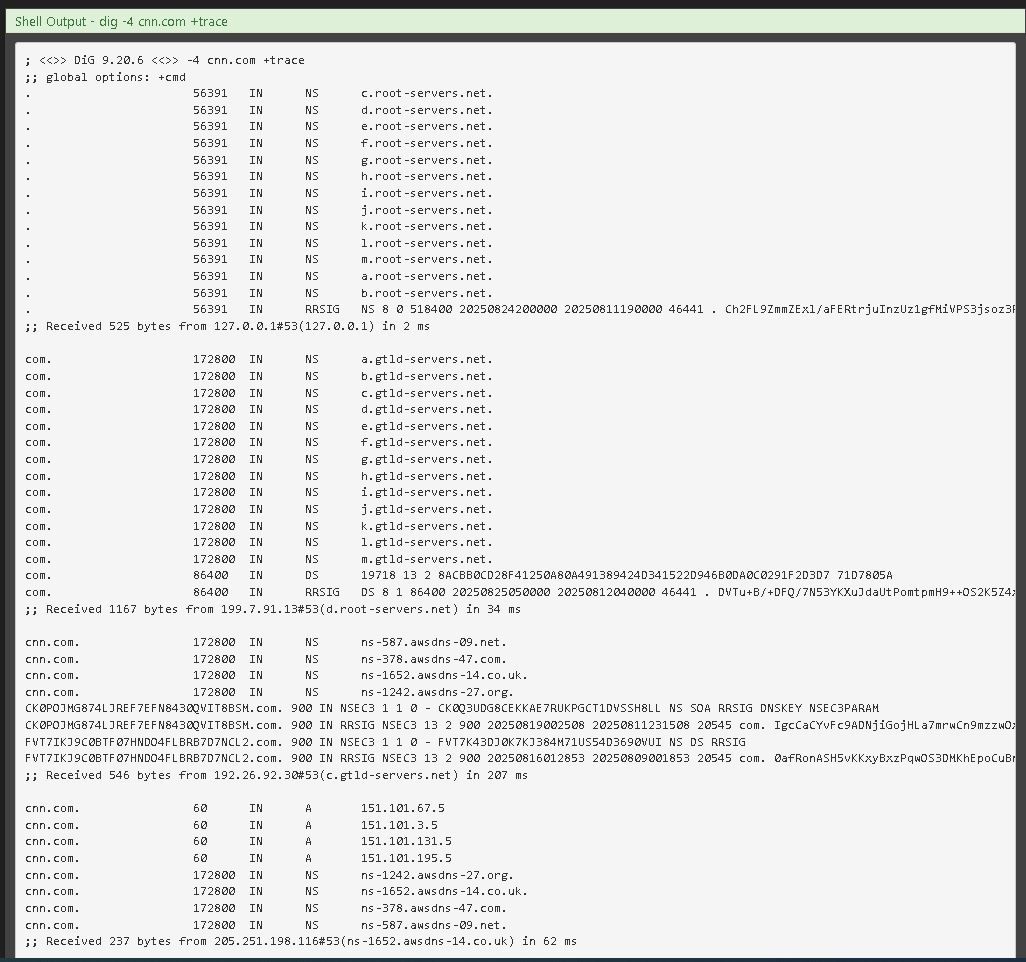
As it get back DNS records with IPv6 addresses, it will use these to 'check' them. Because your don't have Ipv6 support, these will fail.A cleaner result can be obtained by specifying dig to use IPv4 only :
dig -4 cnn.com +traceBut dig isn't the resolver.
There are special options for unbound that you can specify here :
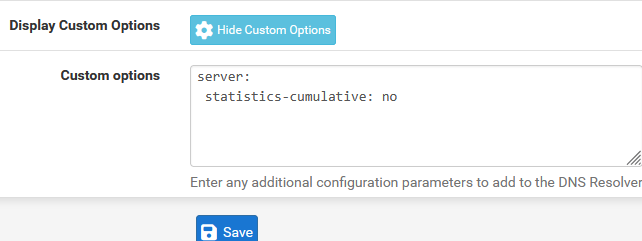
so you can inform unbound not to use Ipv6 (just to be sure).
-
-
-
Thank you for your assistance. I will continue to monitor the system status.
-
Been seeing a similar issue after upgrading to 25.07. Internal resolver just stops working completely at random and can't recover on its own. Never had issues with this on 24.11, and no package changes or settings changes. Restarting unbound doesn't even fix it most of the time; I have to resort to allowing DNS to fall back to remote servers to get it working again. Nothing interesting in the logs other than failed DNS resolutions and an occasional restart message. Even trying to ping google.com from the UI fails until I've toggled the DNS fallback behavior (which shouldn't be a thing given that my DNS setup is effectively a mirror of https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html). In my case DHCP is disabled and pfBlocker is in Python mode so no DHCP issues should be at play here. Sounds like there's a nasty bug floating around but not really sure where to look in logs and filing a bug with no supporting information other than 'it's not working' doesn't seem productive. In the meantime, I'm just glad I no longer use pfSense for my DNS because it's unreliable after this upgrade.
-
@freph533 said in DNS Issues After Upgrading to 25.07:
In my case DHCP is disabled
So all your LAN devices have a static IP, network, gateway and DNS set.
DNS points to where - what IP ?If 'unbound' (the resolver) had a problem, this forum would 'explode' right now with hundreds of thousands complaining about DNS not working - you agree ?
Your pfSense resolver setup is not default, as you 1) forward, and 2) over TLS.
If you go back to default resolver mode, your issue is gone ?
You forward (over TLS) to where ?
Still, if unbound couldn't forward over TLS to, for example 1.1.1.1, then the https://github.com/NLnetLabs/unbound/issues would mention this.The bad and good news rule probably apply : it's your setup/connection/ISP ...
I've tested this https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html many times, (but not yet with the latest 25.07.1).@freph533 said in DNS Issues After Upgrading to 25.07:
Even trying to ping google.com from the UI
If DNS is down, google.com won't get resolved, and ping can't work. Ping needs an IP, not a host name.
If you were using an IP, ping would work, right ?@freph533 said in DNS Issues After Upgrading to 25.07:
and pfBlocker
I have to ask / check : pfBlockng isn't blocking the DNS server you forward to, right ?
-
@Gertjan said in DNS Issues After Upgrading to 25.07:
So all your LAN devices have a static IP, network, gateway and DNS set.
DNS points to where - what IP ?All of my clients point to an external DHCP/DNS server since I decided to decouple it from pfSense in case I ever wanted to switch to another firewall/router solution.
If 'unbound' (the resolver) had a problem, this forum would 'explode' right now with hundreds of thousands complaining about DNS not working - you agree ?
I agree - but there's a nonzero amount of reports of this issue. The hard part is correlating exactly what's scenarios cause it. I imagine pfBlocker and DNS over TLS usage is widespread enough that if it were linked solely to those common items it would be a much more reported issue, however that's not the case.
Your pfSense resolver setup is not default, as you 1) forward, and 2) over TLS.
It's not default, but it's a documented configuration published by Netgate themselves that should still be functional after an upgrade where it was previously working just fine on 24.11.
If you go back to default resolver mode, your issue is gone ?
Haven't tested disabling forwarding (DNS Query Forwarding under DNS Resolver) when this issue happens. I can try it and get back to you when it occurs again.
You forward (over TLS) to where ?
To Cloudflare. As I said, it's effectively a mirror of the DNS over TLS docs - Cloudflare IPv4/IPv6 and all.
Still, if unbound couldn't forward over TLS to, for example 1.1.1.1, then the https://github.com/NLnetLabs/unbound/issues would mention this.
I never said it had issues forwarding. It's the internal resolution that pfSense uses to resolve things for itself that fails. Toggling DNS Resolution Behavior to use remote for fallback instead of ignore remote gets it out of whatever weird state it's in when it breaks, and I can change it back to ignore remote servers (which is the desired setting and what's suggested to use in the DNS over TLS docs.
The bad and good news rule probably apply : it's your setup/connection/ISP ...
I've tested this https://docs.netgate.com/pfsense/en/latest/recipes/dns-over-tls.html many times, (but not yet with the latest 25.07.1).This isn't related to ISP - this is an issue that explicitly started happening after the update. My other recursive DNS server that hits roots works just fine. And as mentioned it works fine for a while after it's been restarted/DNS behavior toggled. It's still working just fine after I restarted it last night. That's the problem - this happens seemingly at random.
If DNS is down, google.com won't get resolved, and ping can't work. Ping needs an IP, not a host name.
If you were using an IP, ping would work, right ?Yep - IP (and IP communications) continue to work just fine. It's pfSense's own resolution that breaks (and breaks domain resolution of aliases along with it which is problematic).
I have to ask / check : pfBlockng isn't blocking the DNS server you forward to, right ?
No.
One thing I noticed was that ntopng was taking up quite a lot of resources compared to normal so I disabled it and cleared out all of its data. I'll be interested to see if the issue with the resolver resurfaces again now that it's disabled.
-
Update from my side: issue hasn't appeared again since disabling ntopng, so seems that was the culprit (or one of them, anyway).
-
Hopefully this isn't an ongoing bug because it's pretty crippling.
-
@xana I am having the same exact issue. It will just suddenly stop working, the service is running but failing to respond.
I have disabled DNSSEC and do not have ntop installed.
The only way to restore service is to restart the unbound service.
I am using encrypted DNS but that is the only difference from standard setup, I followed the pfsense docs closely when setting it up. Was not a problem until this version, but there are things in this version I need elsewhere so I cannot go back.