Issue with local Ubuntu VPN behind PFsense
-
This post is deleted! -
You VPN Server you want to use is the one running on pfSense ?
Or a VPN server on your LAN ?@alexanderjh said in Issue with local Ubuntu VPN behind PFsense:
any hits for UDP on my WAN for 1701/4500/500
pfSense can't handle traffic it doesn't receive ^^
When you connect to your ISP WAN IP, your ISP router has to 'port forward' (NAT) this traffic to the pfSense WAN IP (192.168.1.x) on the correct port. Nothing arrives on pfSense, so check the NAT rules on your ISP router.Example :
I use the pfSense VPN server.
It listens on the pfSense WAN interface, port 1194, UDP.
So I created this pfSense WAN firewall rule :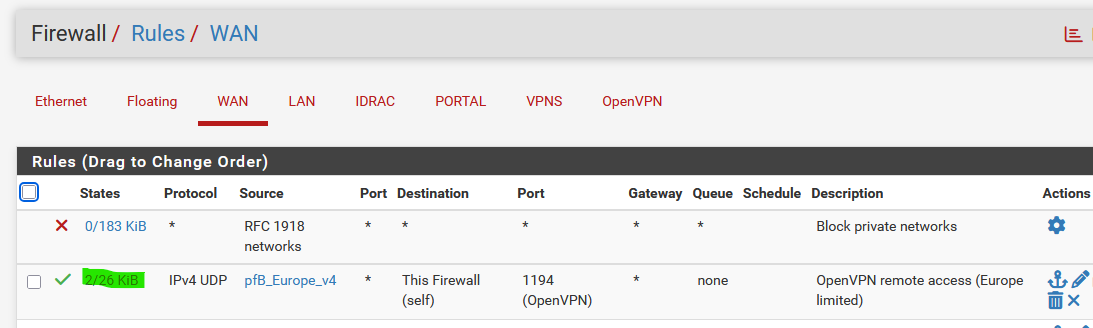
the rule matches traffic, see the green marked indication.
I have, like you, an upstream ISP router, so I has to NAT on this router port 1194 UDP to the WAN IP of pfSense.
Be ware : I only needed this "pass" firewall rule, which is not part of a NAT rule, as the destination of the VPN traffic is my pfSense, not some device on my LAN.
If my VPN server was on the LAN, I had to create a 'VPN server' NAT rule, which will redirect (on pfSense) the incoming WAN VPN traffic to this LAN device. -
Thanks for reply.
The VPN i have issue with is a separate instance, behind PFsense that worked before PFsense. This means i know my ISP allows port forwarding, i simply changed the IP from my VPN in the PF rules to the PFsenseIP (as my VPN was now behind PFsenseo on a new IP).
As stated - Port forwards are set (192.168.1.2) <- WAN IP of my PFSENSE.
I also added 192.168.1.2 as DMZ on my ISP router!Then i have a NAT setup listening for, the HTTPS/HTTP forwarding is working for web traffix to the web server on the same VPN instance.
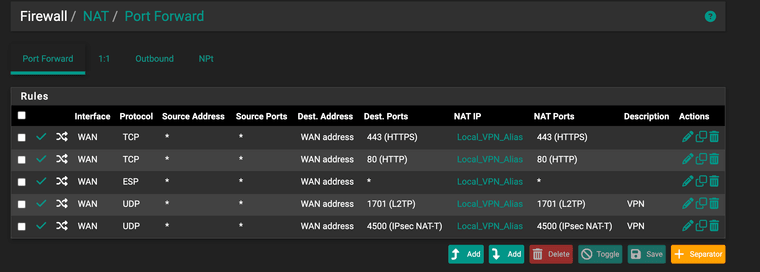
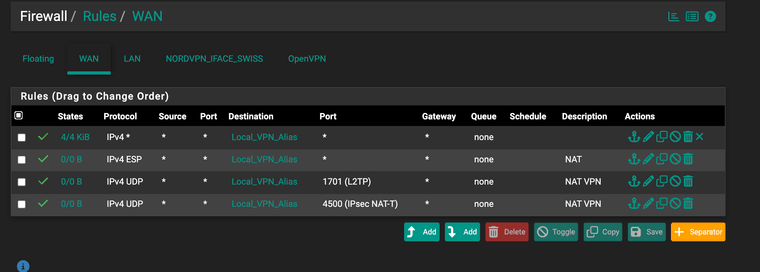
I have also a VPN CLIENT on the PFsense box that is routing specific MAC client to Swiss break out. i mention this as i just want to be sure it is not a cause of any issues.
-
This :
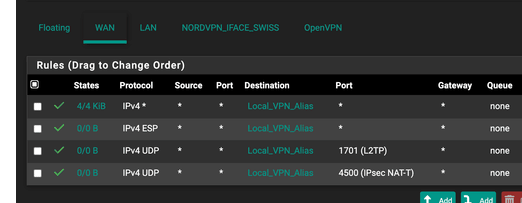
the first firewall rule, the one that says : 4/4KiB, that is a firewall rule not being part of a NAT rule ? Right ?
Something tells me that that rule 'gobs' all incoming IPv4 and sends it to ... black hole ?Your IPv4 ESP doesn't mention a port ... maybe ESP doesn't needs port (like ICMP) - I can't tell.
-
ah yes i move this one top or bottom , just trying to "catch everything" as you say but it didn't work i should delete it.
-
This post is deleted! -
@alexanderjh said in Issue with local Ubuntu VPN behind PFsense:
I also enabled NAT reflection on the rule
Normally not needed.
Use 'http://the-host-name-on-your-lan' and you can connect to that host. This traffic will not even been seen or reach pfSense as it is LAN (device) to LAN (device) traffic.@alexanderjh said in Issue with local Ubuntu VPN behind PFsense:
also connect to the VPN (for test) on the LAN
Same thing, that's (pfSEnse) LAN (device) to (pfSense) LAN (device) traffic and never passes trough (reaches) pfSense.
-
thanks and yes appreciate that on LAN its simple bnut also a good test to prove that my VPN server didn't randomly break :)
I really struggle to see where issue is. Other option is to. move my VPN outside of the PFsense and back onto the "WAN" IP range but then this will be annoying as i want to access the "LAN" network when connected to that VPN. I don't see why its being so dificult!
-
@alexanderjh said in Issue with local Ubuntu VPN behind PFsense:
on LAN its simple bnut also a good test to prove that my VPN server didn't randomly break
Be aware : most server device, like a Windows PC with RDP activated will only accept connections from the local LAN, so the 192.168.0.x network.
That is, the RDP service will accept connections from everywhere but the windows firewall will block all non-local attemps.
Whne you set up 'any' server device, like a web server on some LAN device, check if the firewall of this devices accepts connection from 'every where' and not only LAN.
That said, this isn't probably your issue. -
@alexanderjh said in Issue with local Ubuntu VPN behind PFsense:
I really struggle to see where issue is.
The very first thing I test when dealing with NAT rules : I set them up, then de de-activate the wifi on my phone, and connect to the "ISP WAN IP" using a browser, VPN client or RDP tool and check here :
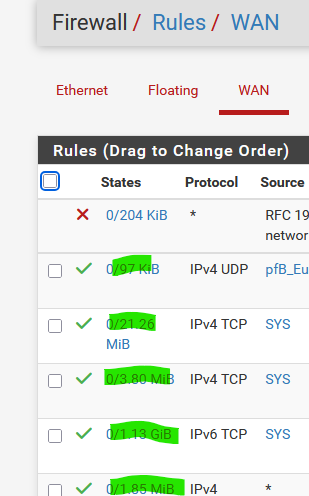
where I can see the firewall rule in question receives traffic = the counters start to raise = the rule is actually used.
If these stay 0/0 then you have a solid proof that your traffic isn't reaching the pfSense WAN interface. -
@Gertjan Yeah this is really tricky with UDP.
I can see the HTTP and HTTPS traffic hitting the WAN, being passed to the LAN and then serving the webpages internally and externally. I set up the same rules except of course UDP and 4500/500 for the VPN and NOTHING... really frustrating!
UDP port checker online says they are open..... Hmm i guess no easy answer and i just need to keep playing around!
(for what its worth, my VPN Ubuntu box does not see any attempts on its UFW logs or strong swan, other then when internally connected or serving web pages that is working...
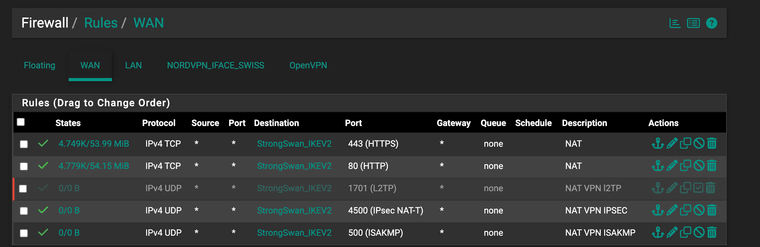
-
This post is deleted! -
@alexanderjh said in Issue with local Ubuntu VPN behind PFsense:
this is really tricky with UDP.
The thing is, I use the pfSense Openvn server, that uses the default UDP and default 1194 port.
I don't know anything about "IPSEC" and "strongwan".
What protocol number it is, if it uses ports, etcKeep mind that your issue isn't pfSense related right now.
Here : proof :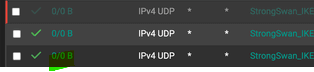
your VPN traffic never even reaches the pfSense WAN port. It can't redirect what it didn't receive ^^
That said (example) : if IPSEC is using IPv4 and UDP, and port '45000' as a destination.Your rules do work fine for traffic with destination port 80 and 443, TCP, IPv4 - the web server traffic.