Confused about DNS setup
-
@tinfoilmatt said in Confused about DNS setup:
@g289519 What you're doing at the request of the auditors here is a setup that nobody is going to have in the real world: pfSense configured as a recursive LAN resolver with its system DNS intentionally left empty.
I understand, we wont leave it that way permanently. I just need to show I have control over the DNS server by being able to remove it. Its just one of many steps. I didn't write the procedures. Eventually it will have some server address there. Appreciate the feedback thanks.
-
@g289519 No I'm with you, man. You've personally piqued my interest with this for my own setups. I'd fail pfSense if I was the auditors over this, too. I get that leaving system DNS blank is just the test. So you need to figure out how to block
localhost-generated lookups from leaving the WAN interface!Does that DNS answer offer any clues about where it's coming from? It's possible ISP is simply redirecting 53/853 traffic wherever (after sniffing the lookups of course, lol).
-
Pinging @stephenw10—is there any way to place a deny rule above the default 'let out from itself' rules?
-
@g289519 said in Confused about DNS setup:
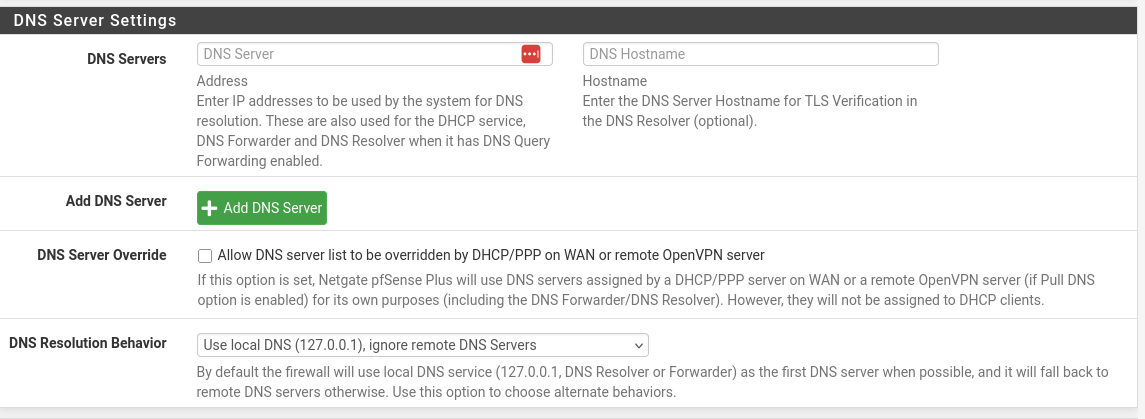
I have been tasked with ensuring our firewall uses a specific DNS server and only that server. Under the General settings tab, I specified the desired IP and hostname for TLS resolver, and everything appeared to work OK.
IMHO, you missed a step.
First, you have to indicate a DNS server you want to use : example :
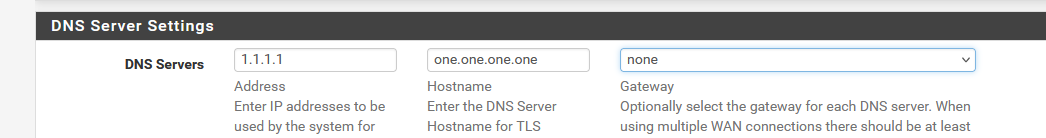
or, if you have a local, on pfSense's LAN or nearby, on it's WAN :
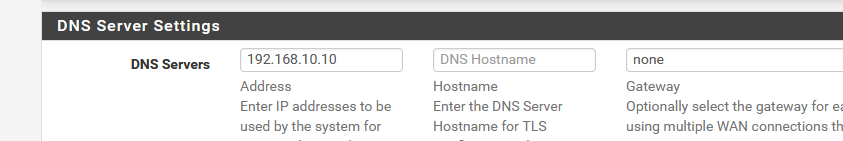
This could be a pi hole, a Windows DNS server or a local company DNS server : a DNS server that is under local or your control.
Then, instruct the resolver to forward to this IP :
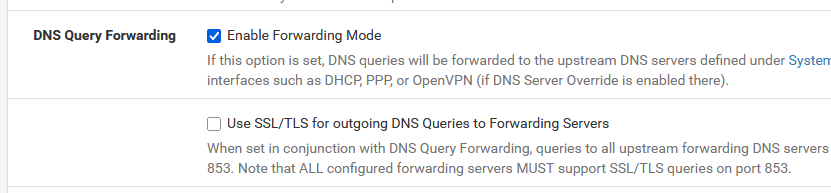
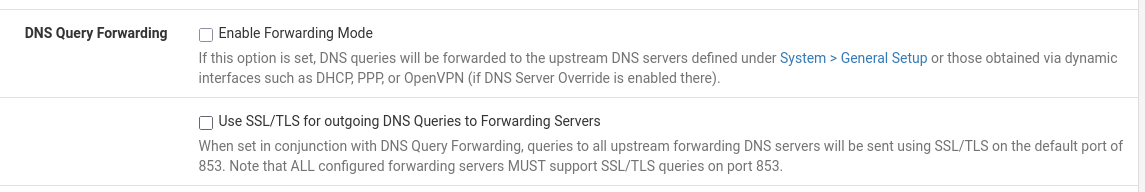
If this DNS server, like 1.1.1.1, supports TLS you can also enable TLS Forwarding (the second check box).
To make sure all LAN devices use no use your defined DNS server, block all DNS traffic = port 53, UDP and TCP, for IPv4 and IPv6, and only allow LAN devices to contact pfSense (using port 53, UDP and TCP, for IPv4 and IPv6).
If needed, create also a pass rule to allow port 853 TCP to pfSense and afterwards a block rue for 853 TCP, any destination.
And check :
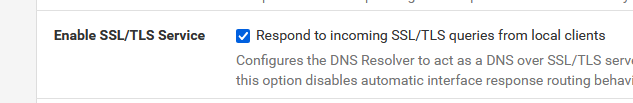
From now on, your LAN devices can only ask pfSense for DNS info, and pfSense, the resolver which now has become a 'dumb' forwarder, will forward the request to the IP you specified. It won't go anywhere else.
If the path to 1.1.1.1 is broken (blocked, shut down, whatever) then your pfSense (and LAN) DNS will fail. -
@Gertjan said in Confused about DNS setup:
First, you have to indicate a DNS server you want to use
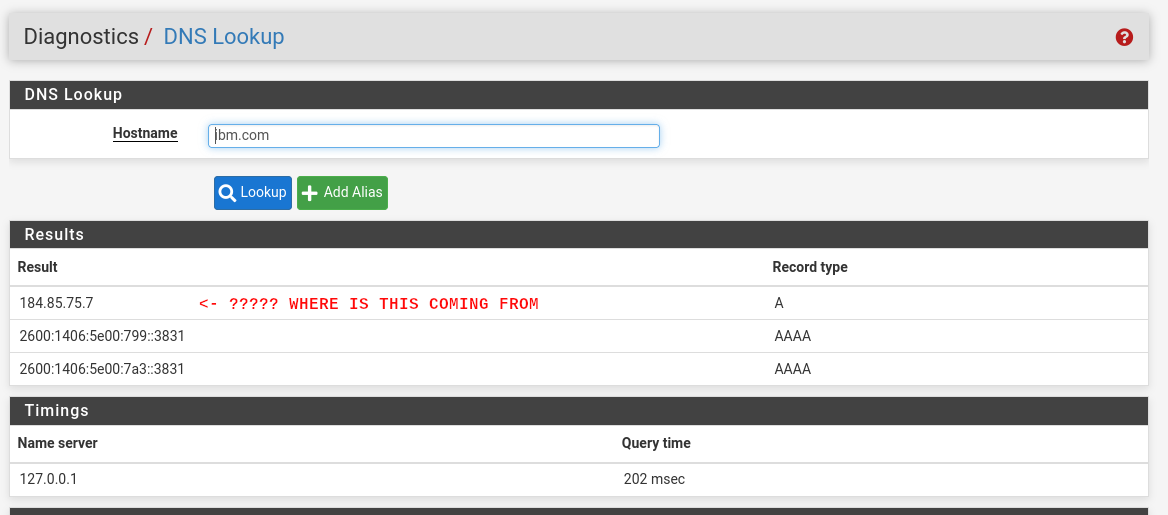
OP needs to intentionally leave DNS Servers configuration blank in order to prove to corporate auditors that DNS resolution using the DNS Lookup tool then fails—but he's still getting an answer after doing that!
-
Ah ....
Putting the resolver in forwarding mode without any DNS servers listed on the General will fail :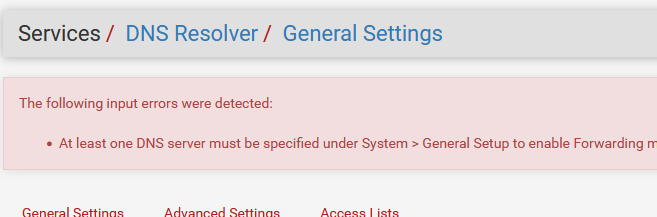
so exit forwarding mode.
The resolver will then resolve as that is its job.
Stopping it then seems the only good solution (with the LAN(s) firewall rules mentioned earlier).
Leaving unbound (the resolver) running while blocking its outgoing traffic over WAN is ... strange/counter productive.What seems to works : set up a forwarding IP on the General settings page as shown above.
Now, the resolver can be put in forwarding mode without complaints.
Back again tho the general settings page, remove the DNS IP listens and save that page.
After the save, I checked, the resolver was still running.
But :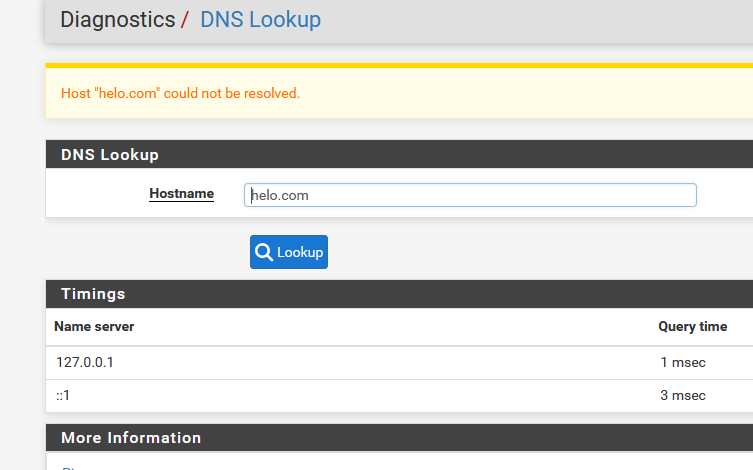
and on my PC :
C:\Users\Gauche>nslookup google.com Serveur : pfSense.bhf.tld Address: 2a01:cb19:dead:beef:92ec:77ff:fe29:392c *** pfSense.bhf.tld ne parvient pas à trouver google.com : Server failedThis seems to look ok - I managed to break DNS.
-
@Gertjan said in Confused about DNS setup:
What seems to works : set up a forwarding IP on the General settings page as shown above.
The auditors may or may not allow a configuration change like this, since it's essentially a 'workaround' to pass the already-defined test—that being, DNS must fail when pfSense's configured system DNS is left blank. But that's all some good DNS Resolver behavior testing regardless.
I think I agree that if OP must continue using DNS Resolver/unbound, then more is needed to pass this test, likely (and most minimally) a firewall rule blocking
localhostlookups from egressing WAN outbound.
@g289519 How many interfaces are selected under
Services / DNS Resolver / General Settings / Outgoing Network Interfaces? Note thatLocalhostcan be unselected. Actually, that could be a potential fix here...
-
@Gertjan said in Confused about DNS setup:
This seems to look ok - I managed to break DNS.
By the way, when I read this...

-
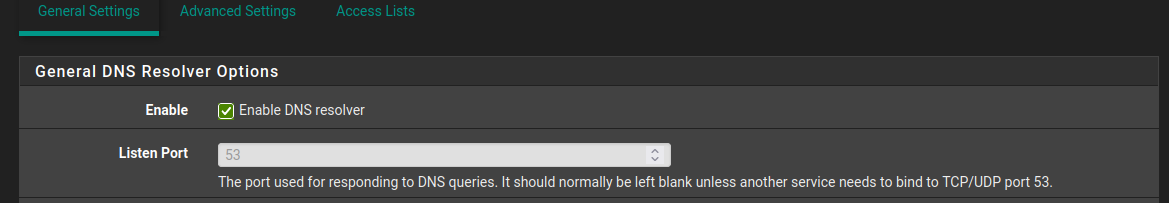
I have no way to test this. But what if you put PF Sense into fowarding mode and then turn off Resolver???
-
@Gertjan That works perfectly thank you so much! Enabling DNS Query Forwarding seems to be the correct setting for us.
I think what was throwing us off was the wording "or those obtained by dynamic interfaces such as DHCP". Obviously we can't have that. However the qualification "if DNS server override is enabled there", which it is not, so that just didn't apply.
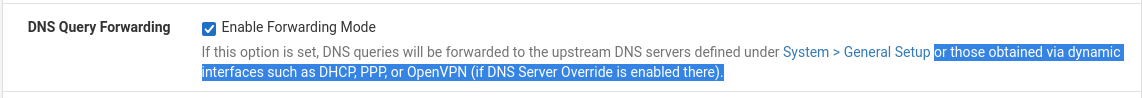
Now if I have a DNS address specified it works, and if that server is unreachable for any reason it doesn't. That is what I want.
Again thank you so much. I can now move on to step 2 +++ ;) We will take further steps to deal with DoT and DoH as you and others have mentioned.