pfSense Login Emails
-
@newUser2pfSense said in pfSense Login Emails:
does pfSense have a way of emailing you when someone either logs in via the Web GUI, SSH
This mans that that user should be on the 'LAN' from where pfSense GUI login access is allowed.
And uses an IP from which that login is allowed.
These two reasons already make it necessary that the user has physical access to pfSense.Also : pfSense isn't a multi user environment. Most pfSense setups are managed by one, two, and rarely admins. The will use a the very secret pfSense admin password : (here is mine : MdtApi+46700) and have their decvice attached to the pfSense LAN and have an IP between 192.168.1.10 and 192.168.1.30. (starting from 31 and they will use an IP from the DHCP pool : not allowed).
Btw : Login from OpenVPN over the OpenVPN tunnel is also allowed for me. The hacker should have my cert of course.SSH : no password login should be possible. Password login is possible in the beginning, and the very first admin task should be : generate keys, and switch to :
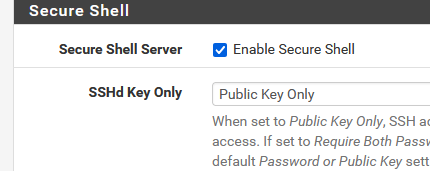
and done.
That's for the "why would you need a mail" part.
Now for the good news : I'm pretty sure this question was already asked, so a solution was already mentioned.
You still have to find it.
It's probably an "add one line this 'this' file" and you have your mail.
If the find button isn't your friend, post back here, and I ask him ^^ -
I try to assume a bad actor is always in my network, vs. assuming my network is secure. A network is too complex to know with any certainty that only authorized people are in it. The insider threat is the hardest to mitigate effectively.
A login attempt email would be useful for trying to catch instances of attempted hacks.
I don’t have a redmine account to comment on the request and I really don’t want to create another account, but I support the request, fwiw.
-
@Mission-Ghost I always suspect bad actor(s) are in my network poking around. Many a moon ago, I was away from home on vacay and I was able to login to my pfSense box's Web GUI using my dynamic DNS. I don't know if anyone can do that any longer or not as I haven't tried. Agreed, any login attempt by any method pfSense supports would be most helpful; who wouldn't want to know that their pfSense was logged into! Just a thought. Thanks for supporting. I appreciate it.
-
@newUser2pfSense said in pfSense Login Emails:
Many a moon ago, I was away from home on vacay and I was able to login to my pfSense box's Web GUI using my dynamic DNS. I don't know if anyone can do that any longer or not as I haven't tried
What do you mean you don't know ?
Imho, that's a massive security thread, and "you don't know" ? Euh ...@newUser2pfSense said in pfSense Login Emails:
I always suspect bad actor(s) are in my network poking around
With an open WAN GUI pfSEnse access, your 'network' was enlarged by the entire Internet.
I agree with you : no doubt about it, there are some bad actors out there (on the Internet).
So : undo this access (please) !!
Remember : by default, there are no WAN firewall rules so no WAN GUI access.
You made that access possible. Just undo it.If you need to access the pfSense GUI from the Internet, use a VPN.
About the log attempts : when the admin logs in, a System log is added :
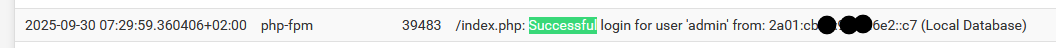
These logs, the System, and others, is the most important info (for me) on pfSense, way beyond what the GUI dashboard can show me. So these logs, I send them to a (LAN based) remote syslog server, if something goes wrong with my pfSense, I have access to the 'what happened' info, even if the pfSense drive was wiped.
This syslog server has some nice tricks, like highlighting the very common messages, the less common ones, and the ones I never want to see ^^ So I could decide to tell the syslog collector to notify me if it detects strange messages, like multiple failed login attempts.Anyway ....
I know I've posted the 'solution' somewhere in the past here on this forum.
But I couldn't find it.So, as usual, as the GUI is a 'web server', I drilled down from index.php to the place where the message "Successful login for user" is logged : it was in /etc/inc/auth.inc.
Open that file, around line 2263 (pfSense 25.07.01).
Find :.... $_SESSION['REMOTE_ADDR'] = $_SERVER['REMOTE_ADDR']; phpsession_end(true); log_auth(sprintf(gettext("Successful login for user '%1\$s' from: %2\$s"), $_POST['usernamefld'], get_user_remote_address() . get_user_remote_authsource())); if (isset($_POST['postafterlogin'])) { return true; } else { if (empty($page)) { $page = "/"; ...Add this single line :
notify_all_remote(sprintf(gettext("Successful login for user '%1\$s' from: %2\$s"), $_POST['usernamefld'], get_user_remote_address() . get_user_remote_authsource()));so now you have :
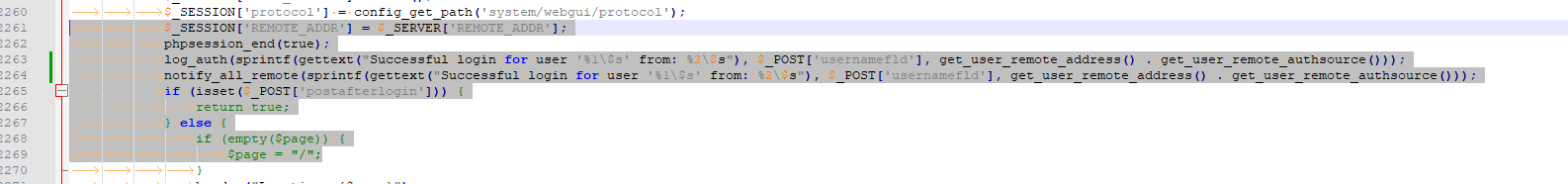
Save & enjoy !
WARNING :
Editing these files is easy. It really looks like open source after all : I can see them, edit them, etc.
: I can see them, edit them, etc.
Keep in mind : This is a "what I would do" solution. Maybe not the best solution. I'm not aware of any side effects, although I gave it some thoughts, as I don't want to post pure BS here on the forum.
The function notify_all_remote() (see /etc/inc/notices.inc, at the bottom, uses all activated notify channels like Telegram, Slack, email, etc that you've activated) sends a notification (a simple text string) if you've activated at least one of them.edit :
Found something :
Login pfSense and you see the log line, and you received the notification.
Cool.
Logout.
Login again and now you see this log line :
so : no mail (notification), as the content of the mail was identical as the last mail as I logged in from the device LAN device, and good practice is not to send identical subsequent mails (mail server don't like this, as it is a sort of spamming).
I'm working on a solution : making the notifications string different by prepending a time stamp. -
@Gertjan Ok. I created an IP firewall alias and called it pfSense Web GUI. I then created a WAN firewall rule to block all IPv4/6 and any protocols, from anywhere, to the pfSense Web GUI alias and dragged it up near the top of the WAN rules and saved. I took my phone off Wi-Fi and tested with 3 different browsers to my dynamic dns and I couldn't get to the pfSense Web GUI. This seems to have worked. Is this what you mean?
I don't have a syslog server and have never configured one before. I'll look into it.
I'll wait on your time stamp solution to add to the /etc/inc/auth.inc file. This would be fantastic.
Thanks for taking time for this.
-
All incoming connections on the WAN would be blocked by default so you shouldn't need a block rule there. Just make sure any allow rules you may have added are not passing more than you think.
But, yes, the pfSense webgui should never be exposed to external IPs on WAN.
-
@stephenw10 Interestingly, I've never had any rule on the WAN that would have allowed access to the pfSense Web GUI. It's been so many years ago now, I think I had a VPN on pfSense, likely OpenVPN at the time, where I was able to get to the Web GUI using my dynamic dns [scratching my head]. My memory of that is foggy at best.
-
Well if you were coming in over OpenVPN that's OK. That's the recommended way to access it externally if you have to.
-
@newUser2pfSense said in pfSense Login Emails:
I'll wait on your time stamp solution to add to the /etc/inc/auth.inc file. This would be fantastic.
notify_all_remote(sprintf(gettext("Successful login for user '%1\$s' from: %2\$s at: %3\$s"), $_POST['usernamefld'], get_user_remote_address() . get_user_remote_authsource(), date('m/d/Y h:i:s a', time()))); -
@Gertjan Thanks for this. It worked in 2.8.1 CE. I appreciate it.