pfblocker not working
-
We've recently setup pfBlockerNG on a firewall of countries with traffic we're not expecting via a blacklist alias and blacklist rule:

(Setup using MaxMind's GeoIP service)
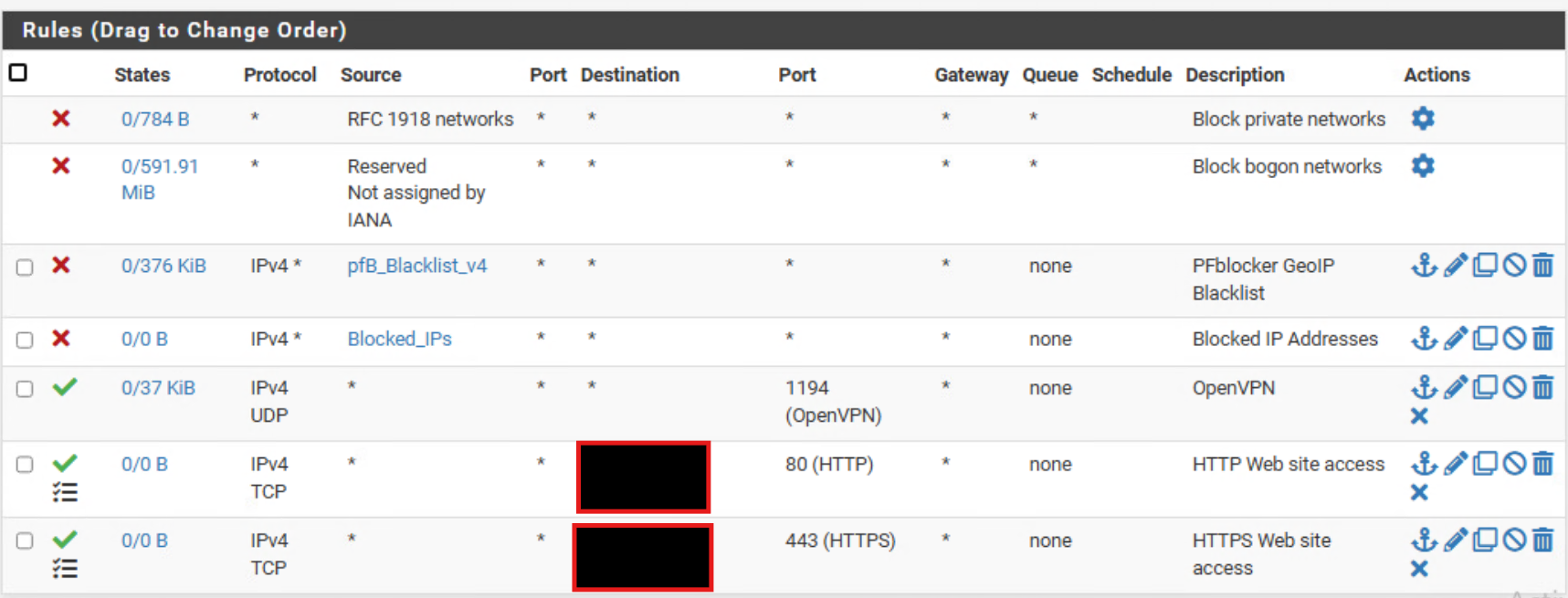
However we are still seeing traffic coming through from some countries that are in the rule:
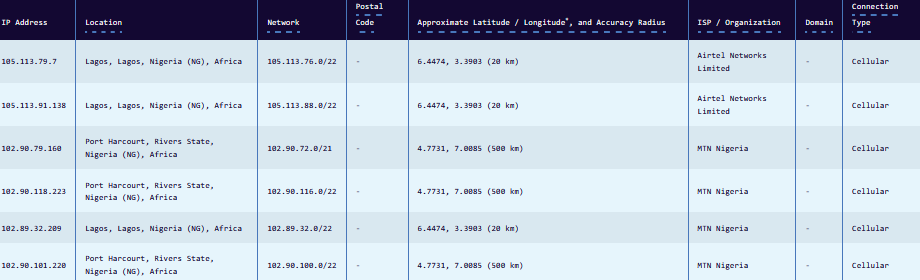
Pretty new to this so wanted to ask if there's anything to check that might catch me out?
Thanks!
-
Important info is missing.
The first image : the firewall rules : do we have to presume it is your WAN interface ? Another interface ?
Let's presume its WAN.When you hover the mouse over the third firewall rule, the one with the Source "pfB_Blacklistv4", do you see (the top of) a big list filled with IPs ?
If so, and all is well, this list should be the list with Geo IPs you want to block.If you want to check the "pfB_Blacklistv4" list yourself, you can (I think) find it in this folder : /var/db/pfblockerng/deny/ and then you can check if 102.90.101.220 (the 102.90.108.0/22 network) is in there.
This rule is actually blocking traffic : the "States" column mentions packets ... (hover the mouse over it).Btw : Don't try to block 'the entire Planet', as this would produce a list so big that it can't into the firewall's (the firewall kernel process) working memory anymore. Remember : there are a lot of IPs/networks. And we haven't talked about IPv6 yet.
Exemple : I created a list with all the IPs of my country, and used that list to allow incoming VPN connection only from my country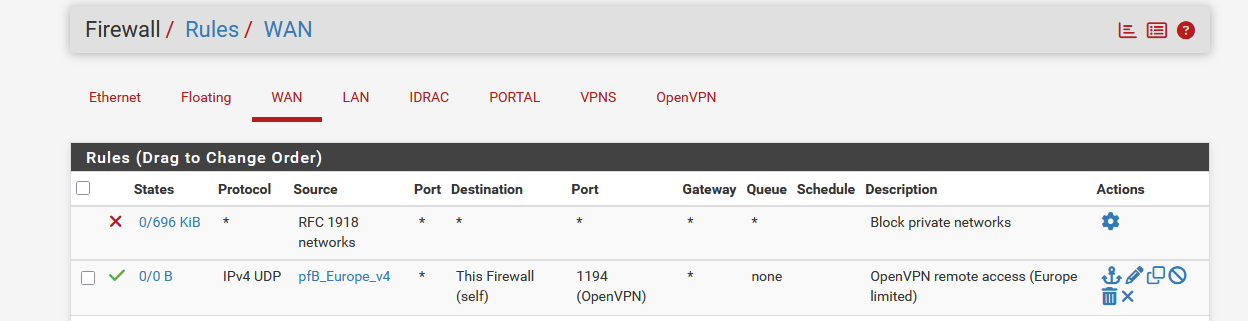
What about this solution : create a selection of IPs (countries) that are allowed to connect to your pfSense ?
And be ware : start blocking the "US" first, as that's the most dangerous country ^^If needed, visit : Diagnostics > States > Reset States and reset the current firewall states.
This one :
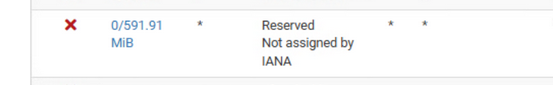
needs some thoughts.
500+ MBytes of incoming traffic using IPs that do not / can not exist ??
Call your ISP and ask them if all is well ? Your ISP shouldn't even route BS traffic to you ... -
Yes geoip blocking is never 100% accurate.
Check the alias table in Diag > Tables. Make sure it actually contains the subnets you're trying to block.
It's often better to pass traffic based on an alias rather than trying to block alias. But that really depends on what traffic you need to serve there.