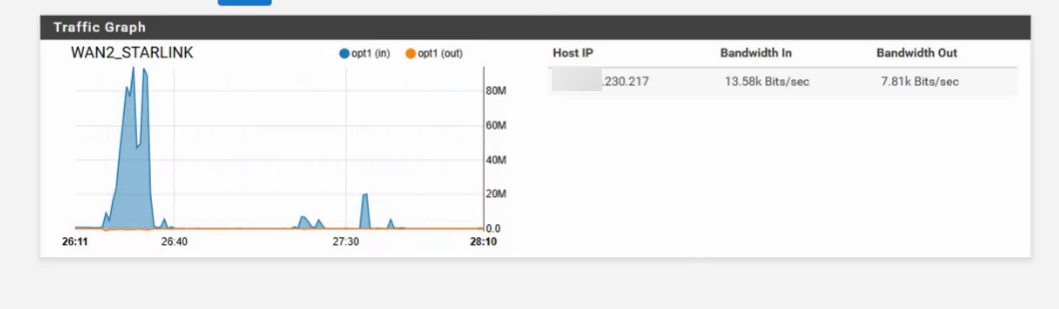
Traffic on Tier2 Gateway w/out Failover Event
-
Netgate 6100 running v25.07.1.
The problem was also happening on prior version.Gateway Group in Failover mode, Packet Loss or Latency.
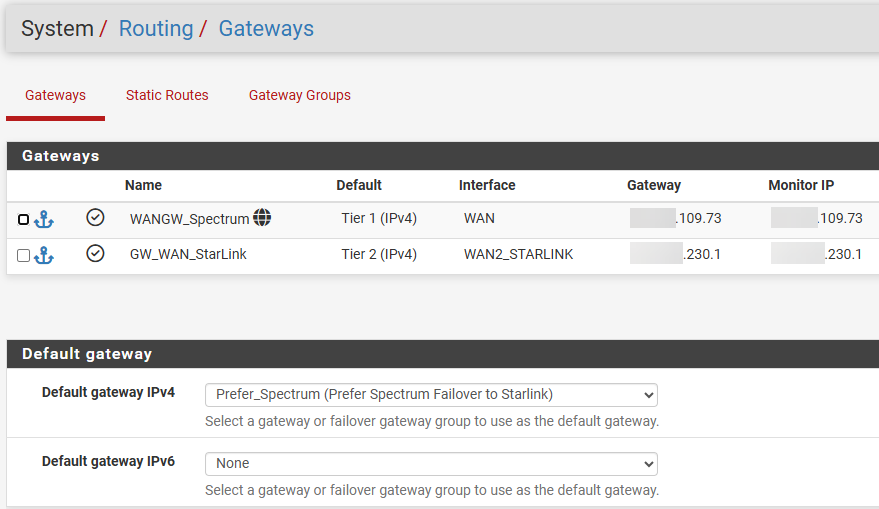
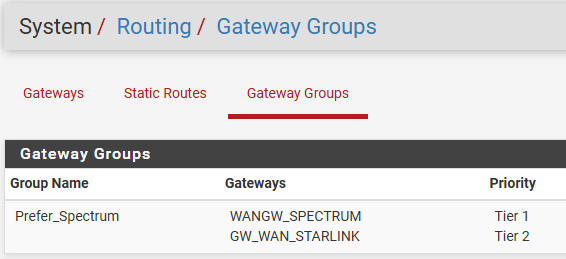
Starlink is Tier 2, primary ISP is Tier 1.
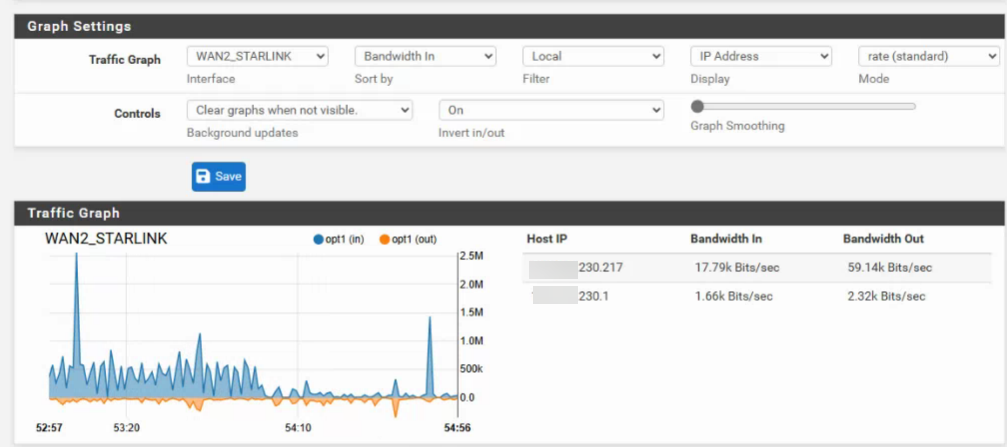
I am seeing significant traffic, 300k steady - 80Mbs burst, over Starlink without any failover events logged. I'm hitting our Starlink 50GB cap in 4-7 days.
There are no firewall rules that specify the Starlink GW. All fw rules either don't specify a gateway or specify the Tier 1 gateway.
Inbound WAN rules only allow traffic on the Tier1 interface so it should go out the same path it came in on.
Traffic monitor shows the gateway IP and the WAN2 interface as the source/destination.- How can I track down the source of the traffic?
- What could be causing traffic in the absence of a failover event?
- How can I prevent this?
Thank you for your help.
-
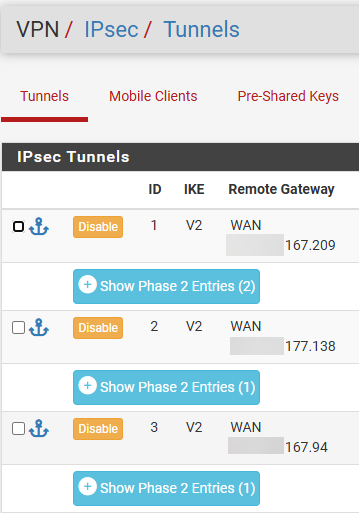
Also, there are 3 IPSEC tunnels on the WAN interface.
-
Tech support provided the help needed to get this resolved.
-
Set Kill State on Gateway Recovery. This setting is under Advanced-->Miscellaneous, not Gateway or Gateway Groups so it's easy to miss, as I did.
-
Use Diagnostics-->States to view what traffic was using the T2 Gateway (Starlink).
-
Set the Gateway Group as the specified Gateway on the firewall rules that were incorrectly using the T2 Gateway (Starlink).
-
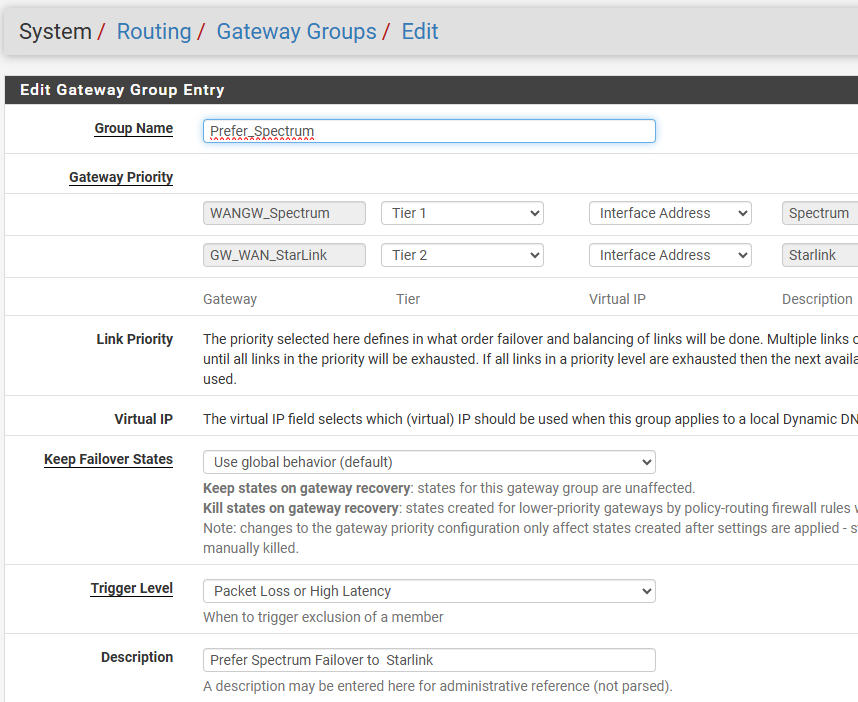
I believe setting the Gateway Group in the rule, vs relying on the Default Route = Gateway Group, was necessary because of this issue specific to Starlink:
Classless static routes received on DHCP WAN can override chosen default gateway
-
-
@pfnewb2016 said in Traffic on Tier2 Gateway w/out Failover Event:
Tech support provided the help needed to get this resolved.
-
Set Kill State on Gateway Recovery fnaf
This setting is under Advanced-->Miscellaneous, not Gateway or Gateway Groups so it's easy to miss, as I did. -
Use Diagnostics-->States to view what traffic was using the T2 Gateway (Starlink).
-
Set the Gateway Group as the specified Gateway on the firewall rules that were incorrectly using the T2 Gateway (Starlink).
-
I believe setting the Gateway Group in the rule, vs relying on the Default Route = Gateway Group, was necessary because of this issue specific to Starlink:
Classless static routes received on DHCP WAN can override chosen default gateway
Despite configuring a default route, your network traffic was incorrectly utilizing the T2 Gateway (Starlink), necessitating the explicit setting of the Gateway Group on firewall rules rather than relying on the default route. What is the specific issue with Starlink's behavior that makes it necessary to explicitly define the Gateway Group in firewall rules, rather than relying on the default route, to prevent incorrect traffic routing?
-