IPv6 ICMP rule review
-
I have this rule set up (I can't remember where I read it or the context as its been years since I added it in!) and I need it validated here.
In my WAN and other VLANS I have this firewall rule set up (see screenshot):
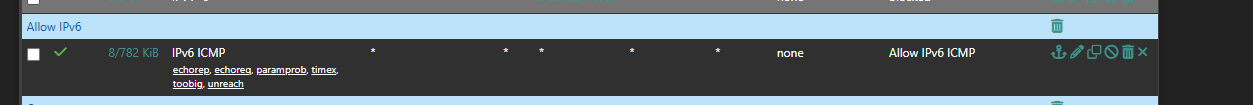
IPv6 ICMP (echorep, echoreq, paramprob, timex, toobig, unreach) allow all
Is is really required for WAN and all VLANs?
-
Simple answer : not at all.
When you installed pfSense, that rule wasn't there, yet it routed traffic (TCP, UDP, ICMP, etc) just fine.When initially installed you found yourself with just one LAN. VLAN's are just special kind of LANs.
When you created other LANs, alos called OPTx, you could have copied over the original LAN firewall rule over to this new LAN (or VLAN), change LAN_Subnets for OPT1_Subnets (as the source) and the new OPTx interface would have worked just fine.Your ICMP IPv6 rule make me think you want to have more control over you traffic, so you've created pass and /or other block rules, and for some reason you've add this ICLMP IPv6 pass rule.
I've the same rule btw on my WAN (!) :
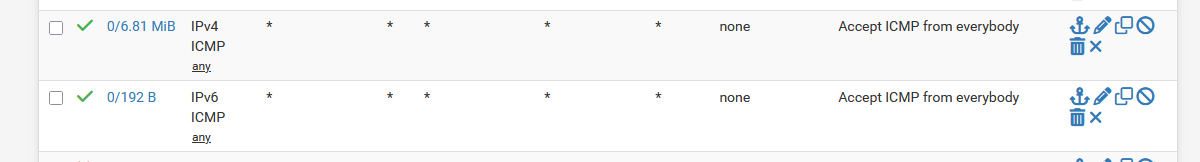
Btw : I don't care if some remote device can 'ping' me, or not ^^
For IPv6, ICMP(v6) is important, and not to be compared as what is ICMPv4 for IPv4.
Read of couple of these : does IPv6 need ICMP ? and you'll get the picture.So :
For your WAN : it might be needed.
For your LANs : If you don't use a general pass rule anymore, it might be needed.
'might' because it depends on your needs. -
Unlike IPv4, IPv6 uses ICMP a lot. So, be careful on blocking any of it. I allow all ICMP on both.
-
-
@alnico pfsense already have ipv6 rules on it to allow ipv6 to work. They are just hidden.
look in /tmp/rules.debug
# IPv6 ICMP is not auxiliary, it is required for operation # See man icmp6(4) # 1 unreach Destination unreachable # 2 toobig Packet too big # 128 echoreq Echo service request # 129 echorep Echo service reply # 133 routersol Router solicitation # 134 routeradv Router advertisement # 135 neighbrsol Neighbor solicitation # 136 neighbradv Neighbor advertisement pass quick inet6 proto ipv6-icmp from any to any icmp6-type {1,2,135,136} ridentifier 1000000107 keep state # Allow only bare essential icmpv6 packets (NS, NA, and RA, echoreq, echorep) pass out quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {129,133,134,135,136} ridentifier 1000000108 keep state pass out quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {129,133,134,135,136} ridentifier 1000000109 keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to fe80::/10 icmp6-type {128,133,134,135,136} ridentifier 1000000110 keep state pass in quick inet6 proto ipv6-icmp from ff02::/16 to fe80::/10 icmp6-type {128,133,134,135,136} ridentifier 1000000111 keep state pass in quick inet6 proto ipv6-icmp from fe80::/10 to ff02::/16 icmp6-type {128,133,134,135,136} ridentifier 1000000112 keep state pass in quick inet6 proto ipv6-icmp from :: to ff02::/16 icmp6-type {128,133,134,135,136} ridentifier 1000000113 keep stateBut simple enough to test - just disable the rule, give it a few days - do you notice any problems? What is not working? If you have no issues you can delete the rule. As I said there are hidden rules that allow for the min required for IPv6 to work.
What you will notice that is not in the main rule is 128,129 echoreq and echorep - ie ping. So if you want to allow for that via non link-local you would want to add those.
-
@alnico notably for WAN, do you want/need the Internet to be able to ping you?
-
@SteveITS Not really.
But I want to connect to my home VPN via IPv6 on OpenVPN and Wireguard
-
@alnico FWIW you don't need pinging for that.
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/firewall-rules.html
https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/rules.html -
@SteveITS Thanks, I will remove those rules.