Identify modified system files
-
I vaguely recall reading about a command that would generate a list of modified system files - ie, .inc or .sh files that have been edited.
Anyone recall what that command is?
-
I do recall there was a file somewhere that contained the hash for (nearly) every file that was put in place by the installer process.
Not the log files, neither the config files, and everything stored in the /var/ folder.@GPz1100 said in Identify modified system files:
Anyone recall what that command is?
Not actually a command. It's a question
 , to be asked to the guy who admin's the system.
, to be asked to the guy who admin's the system.
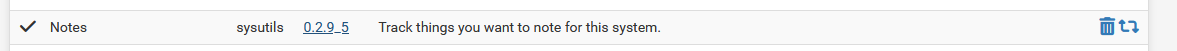
If some one starts to edit/modify 'system' files, then he surely knows what he was doing .... right ?Suggestion : Use this package for the notes.
More serious : look at the date time stamp of a file. If it's later as the date when pfSense was installed, it was probably modified. This could be an update/upgrade, or even a patch from the system patcher package, so info can be obtained from there.
And don't forget this : the source is there, so you can compare this source with what you have.
Btw : pfSense is an 'OS' and needs to be installed, true.
But it isn't like installing new Microsoft OS or something big like that. It's just a 10 minutes job (max).
You don't need to mirror the entire pfSense disk for backup purposes. Keep the installer (or before : ISO) up to date on an USB key, and make sure that the pfSense config is backed up very regularly. I've scripted a pfSense config file backup to a local NAS. You can also use the Netgate's "Auto Config Backup" method as a backup of your backup. -
@Gertjan It was an executable that when ran returned which system files were modified/altered or did not match some master hash table.
I generally do try to document well, but this would be another check.
For example, the gateway alarm script was changed to deal with att nuances (outage every 2 weeks). I vaguely recall changing some .inc files too for other reasons.
-
After digging some more through my notes, I found the command.
pkg-static check -s -aIt returned several modified files on my install. Some that I modified manually, other I suspect were modified by "patches". I will need to go through each (there's about a dozen) to see which changes I made.
Prepping to upgrade soon and don't want to waste time hunting for tweaks made.
-
@GPz1100 said in Identify modified system files:
pkg-static check -s -a

When I disregard all the /usr/local/share/ .... files, and several /man/ files, I did get a list that looks like correct : core files :
pfSense-25.07.1: checksum mismatch for /etc/bogons
pfSense-25.07.1: checksum mismatch for /etc/bogonsv6
pfSense-25.07.1: checksum mismatch for /etc/inc/auth.inc
pfSense-25.07.1: checksum mismatch for /etc/inc/system.inc
pfSense-25.07.1: checksum mismatch for /etc/inc/util.inc
pfSense-25.07.1: checksum mismatch for /etc/pfSense-rc
pfSense-25.07.1: checksum mismatch for /usr/local/captiveportal/index.php
pfSense-25.07.1: checksum mismatch for /usr/local/pfSense/include/www/bandwidth_by_ip.inc
pfSense-25.07.1: checksum mismatch for /usr/local/www/services_dhcp_relay.php
pfSense-25.07.1: checksum mismatch for /usr/local/www/widgets/javascript/thermal_sensors.js
pfSense-25.07.1: checksum mismatch for /usr/local/www/widgets/widgets/traffic_graphs.widget.phpbogons, bogonsv6 pfSense-rc is not me.
Two or 3 others are probably modified by the system patches, so these don't count neither.
The others : I plea guilty.pfSense-pkg-pfBlockerNG-devel-3.2.10: checksum mismatch for /usr/local/pkg/pfblockerng/pfblockerng.inc
That's a patch that I found 'somewhere'.
-
Note, when I do modify anything, I always save a backup with a .orig extension. Just need to do a diff between the two to see the actual changes.