Watchguard XTM 5 Series
-
-
@mr-john-0
After several hour I think I it is still loud maybe because I’m using INTEL Quad Core Q6600, seems like I will need to consider replacing all 4 fans. The only quite fan I know is Noctua A4x20 PWN (4 Pins) dimension 40x40x20mm it is very expensive so if anyone have any better choice please note that I’m open for suggestion.
-
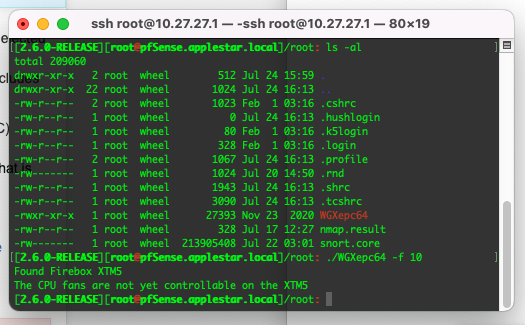
The 2 CPU fans on the XTM5 are in fact controllable just not (yet) by WGXepc directly. See: https://forum.netgate.com/post/1039661
However even if you turn them down they will always be quite loud with a high power CPU in a very high ambient like that.
Steve
-
Thank u Steve but those script seems to be too complicated for me to understand how to apply them. I have decided purchase 4 of Noctua NF A4x20 PWM 4 Pins fans. Hope it would help reducing the noisy fan from XTM5 unit
-
It seems that the newer images will no longer write on these boxes.. has anyone successfully written a 2.6 or 2.7 image to one? Mine just hangs.
I have 2.7 snaps on it now but had to load an earlier image back when I loaded it and did upgrades to be able to test on 2.7 Now it will not update to the later snaps and I want to try to re-load from scratch.
-
Running on mine but I also upgraded to it.
It fails to boot the installer from USB? Or fails to boot the installed image?
What install options did you use?
Steve
-
If I install the USB stick in one of the front ports it will ignore it even though I have the boot options in BIOS set to look at USB first.
If I pull the SATA to the hard drive the unit will go through BIOS then the countdown or press escape to boot now option.. The one beep and stops.
I have an older 2.4.5 image I am going to try right now. I believe that worked last time I did this.
-
@stephenw10 said in Watchguard XTM 5 Series:
It fails to boot the installer from USB? Or fails to boot the installed image?
Steve
It fails to boot from USB and I used no options.
I think the answer is in the BIOS but for now I got it to update after a couple of days of fooling around with it.
2.7.0-DEVELOPMENT (amd64)
built on Thu Sep 22 18:30:19 UTC 2022
FreeBSD 14.0-CURRENT -
@chpalmer I just got this box back out as I had been using a Meraki from work that still had life left on its license. Downloaded the latest OPNsense and pfSense and was able to install one to each of the hard drives in the box. After I get home from the wife's lunch break today I'll blow them both away and reinstall pfSense using the 2nd drive for squid caching.
Only trouble I had was I tried making the freebsd-boot partition larger, but both would not boot if I made them 1024K instead of 512K.
-
By latest do you mean a 2.7 snapshot or 2.6? Or Plus maybe?
-
@stephenw10 pfSense-CE-memstick-serial-2.6.0-RELEASE-amd64.img.gz was the file I downloaded and put on my USB drive.
-
I know I previously used WGXepc64 on this box in the past, but after installing to this hard drive, I tried downloading WGXepc64 to /root. I did a chmod 755 to make it executable. But when running it, I get a "Syntax error: redirection unexpected (expecting word)" when trying to do any of the commands.
-
@mcdonnjd said in Watchguard XTM 5 Series:
I know I previously used WGXepc64
Did you grab this version- https://github.com/stephenw10/WGXepc/raw/master/WGXepc64
And on 2.6??
-
@chpalmer I did. But I also screwed up when adding the 2nd drive to the box. Box would fail to boot. Since I hadn't gotten very far in setting up pfSense, I decided to just wipe it and start over, and create the partition during install. After redoing the basic setup, I re-downloaded it and now it is working. I'm not sure why.
Maybe it was a bad download the first time, I didn't get much of a chance to dig into it. But it's nice to have a green armed LED again. Need to eventually get around to remembering how I customized the BIOS image so that I can change the bootup option to say pfSense V2.6 (or maybe get ahead of it and change it to 2.7 despite being on 2.6) instead of 2.2. But that's minor and only seen during boot.
-
@t-rexky said in Watchguard XTM 5 Series:
I made some additional BIOS tweaks and I think I am now done. One thing I was still unable to get working is the password protection of the BIOS - no matter what I tried the unit always bypasses the password check when entering BIOS setup. It has been this way ever since I unlocked it. Here is the list of changes:
ACPI_AML version 0x03: Introduced independent BIOS minor version codes for ACPI_AML revisions BIOS branch x.x.An for E3400 CPU, where n is the ACPI_AML revision BIOS branch x.x.Bn for Q9505S CPU, where n is the ACPI_AML revision Changed 'Sign On Message' to include 'Unlocked v1.9.A3 / E3400 PT'. Changed 'Sign On Message' to include 'Unlocked v1.9.B3 / Q9505S PT'. XTM515-BIOS1.3-UNLOCKED1.9: Modified BIOS Strings from 'Fan confiruration' to 'Fan configuration' Modified DVMT BIOS String "This setting is only available for WinXp." to "This setting is only for WindowsXP." & introduced line breaks. Changed Failsafe and Optimal IDE mode to AHCI (00 -> 02) Changed Failsafe and Optimal 'Remote Access Term Type' to VT100 (00 -> 01) Changed Failsafe and Optimal 'Always CF Card Boot' to Disable Changed 'Sign On Message' to include 'Unlocked v1.9 PT'. XTM515-BIOS1.3-UNLOCKED1.8b: Corrected all ACPI_AML iasl Warnings based on "Internet wisdom" Corrected all applicable ACPI_AML iasl Remarks, 17 benign Remarks remain Introduced all eight P-states in ACPI_AML for E3400 CPU Corrected P-sate power consumption values based on XTM5 power measurements Changed 'Sign On Message' to include 'Unlocked v1.8b PT / E3400'. Changed 'Sign On Message' to include 'Unlocked v1.8b PT / Q9505S'. XTM515-BIOS1.3-UNLOCKED1.8a: Implemented P-state dependencies _PSD in ACPI_AML. Changed 'Sign On Message' to include 'Unlocked v1.8a PT / E3400'. Changed 'Sign On Message' to include 'Unlocked v1.8a PT / Q9505S'. XTM515-BIOS1.3-UNLOCKED1.8: Changed 'Sign On Message' to include 'Unlocked v1.8 PT / E3400'. Corrected ACPI version help string line breaks in "Enabled RSDP pointers to 64-bit [...]". XTM515-BIOS1.3-UNLOCKED1.7: Changed 'Sign On Message' to include 'Unlocked v1.7 PT / E3400'. Modified LCD boot string from "WG BIOS 1.3" to "Firewall UTM" in module 1B (Single Link Arch BIOS). XTM515-BIOS1.3-UNLOCKED1.6: Changed 'Sign On Message' to include 'Unlocked v1.6 E3400 PT'. Created two ROM branches, one for E3400 CPU and one for Q9505S CPU. XTM515-BIOS1.3-UNLOCKED1.5: Changed 'Sign On Message' to include 'Unlocked v1.5 PT'. Enabled 'PCIPnP' and 'Chipset' menus. Enabled 'CPU Configuration' submenu in 'Advanced' menu. Enabled 'ACPI Configuration' submenu in 'Advanced' menu. XTM515-BIOS1.3-UNLOCKED1.4: Updated platform 11 CPUID 1067a microcode to version a0b. XTM515-BIOS1.3-UNLOCKED1.3: Disabled 'Lan ByPass Control' submenu in 'Advanced' menu. Modified BIOS Strings from 'Port0 AHCI Speed limit to' to 'Port0 AHCI Speed limit' for Port0 to Port3. XTM515-BIOS1.3-UNLOCKED1.2: Changed 'Aways CF Card Boot' to 'Show' in 'Advanced' menu. XTM515-BIOS1.3-UNLOCKED1.1: Unlocked the BIOS by changing 'User Access Level' to 03 in 'Security' menu.And those who are interested can download it from here:
https://www.dropbox.com/s/icnp3jloiw5rnyb/XTM515-BIOS-v1.9.zip?dl=0
As before, I included the factory and the modified ACPI tables in source format (.dsl) and compiled format (.aml).
DISCLAIMER: These work great for me, but please USE AT YOUR OWN RISK.
@t-rexky said in Watchguard XTM 5 Series:
Back once more with a little bit of the BIOS modifying information that I promised a while ago. Unfortunately I do not have the time to write elaborate instructions, but in any case there is a minimum amount of knowledge required in order to be successful, so just a few pointers should be enough.
Fundamentally, a few software tools and files are required that one can locate on the "net" with a little bit of effort. As always, be cautious about the source and do the required virus checks, etc., especially for items 1 and 2 below:
-
AmiBCP-3.51.zip
-
MMTool_322_1B_21Fix.zip
-
Intel IASL compiler tools for platform of your choice (I compiled it for my Mac) to modify the ACPI module
-
Any hex editor if you would like to change the string displayed on the LCD
-
Intel microcode update files for your CPU
The AmiBCP program is used to unlock the BIOS, modify the displayed menus, enable the red LED, change boot version string, change any other BIOS strings, etc.
The MMTool program is used to extract/insert/replace individual modules within the BIOS. For example, you can use it to replace the microcode for the specific platform and cpuid, or you can replace the ACPI_AML module with one that contains the Speedstep configuration specific to your CPU.
For a little bit more information I would refer you to the
realmreadme file in my unlocked BIOS archive that I posted a little bit ago. I tried to be a little bit more descriptive in it and indicate where the changes are being made. It should be a good starting point.Peter.
Has anyone tried to implement the above changes, specifically the one related to power consumption?
Peter talks about "readme" file as starting point, but i can't find it under the ZIP archive he posted... -
-
Enabling Speedstep?
I've done that by loading a separate DSDT file rather than adding it to the BIOS.
Steve
-
Hi @stephenw10
Sorry, i dont have experience neither with .rom configurations or DSDT files. I have E3400 cpu on 510 box btw. I do see that Peter has ACPI_AML_E3400_A3.aml file under 1.9 folder, which i believe i can load as separate DSDT file? If so, can you please point me to the instructions how to do so, or any information as starting point will be appreciated.
Would it also be correct to assume that Peter's unlocked BIOS version (xtm515-bios1.3-unlocked1.9.a3-e3400.rom) has SpeedStep enabled? How can i confirm that?
Thank you! -
Upload the aml file to, for example, /root.
Create the file /boot/loader.conf.local then add to it:
acpi_dsdt_load="YES" acpi_dsdt_name="/root/ACPI_AML_E3400_A3.aml"You need to actually enable speedstep in the BIOS as well as having an aml file the defines the steps. So that requires you flash one of the unlocked versions. If you use the one with the correct dsdt in it you obviously don't need the aml file.
When it's functioning you will see the est device attach at boot and after enabling powerd you will see the reported CPU frequency change on the dashboard or in the sysctl output.
Steve
-
Thank you for the info @stephenw10 !
Do you recommend using flashrom?
And, just theoretically, if i brick my system, how do i restore the previous ROM, assuming i have the backup? I guess the question is how do i connect to the bricked system shell to run flashrom? -
You can write the ROM directly to the chip using the SPI header. You need some sort of flashing tool to do that but it can be as simple as 4 resistors and a parallel port:
https://forum.netgate.com/post/336712Pretty sure I don't have anything with a parallel port any longer!
You can get a USB flash tool relatively easily if you need it.Steve
-
 S stephenw10 referenced this topic on
S stephenw10 referenced this topic on