Static Routes not working
-
Hello Team,
I'm not sure whether it is an configuration problem or a bug. Currently I'm running 2.0.1-RELEASE (amd64)
Here a short overview how our network looks like.
Internal Net 192.168.0.0/16 -> pfsense (192.168.0.254|172.24.2.1) -> DMZ 172.24.2.0/26 -> External Firewall (172.24.2.62) -> Router -> Internet
This is working fine. There is an additional VPN Router in the DMZ with the IP 172.24.2.20 which has an established connection to one of our customers.
The destination network behind this router is 10.236.18.112/29, so I created the 172.24.2.20 as a gateway and created a static route under system -> routing
Screenshot: http://awesomescreenshot.com/0af6tsx82
If I'm trying to communicate with the VPN, I can see the request on our external firewall, which is the default gateway. That shouldn't be the case if the static route would work. Is there anything todo in addition, that this will work?
Log from our external firewall.
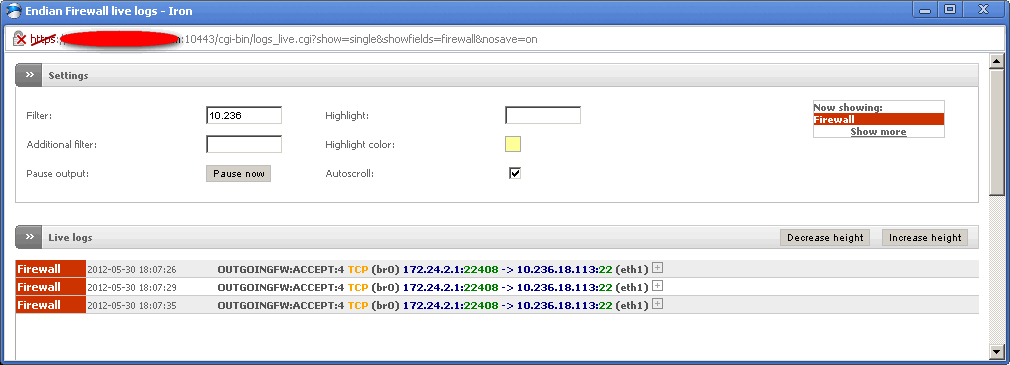
-
Your attempt to connect to host 10.236.18.113 from the internal network is being passed by a firewall rule on pfsense's internal network interface. Can you identify this rule and determine whether it has a gateway defined?
-
Your attempt to connect to host 10.236.18.113 from the internal network is being passed by a firewall rule on pfsense's internal network interface. Can you identify this rule and determine whether it has a gateway defined?
It has no gateway defined, even if I configure there the gateway in explicit it doesn't change the behaviour.
-
Does anyone have an idea why it's not working?
There must be something wrong with the routing if there are two gateways within the same zone:
Internet:
Destination Gateway Flags Refs Use Netif Expire
default 172.24.2.62 UGS 0 1940326 em1
8.8.8.8 172.24.2.62 UGHS 0 15387 em1
10.0.0.0/8 172.24.2.20 UGS 0 352985 em1
127.0.0.1 link#8 UH 0 217 lo0
[snip][2.0.1-RELEASE][DGI@janus.debln01.loc]/home/DGI(11): traceroute 10.46.0.5
traceroute to 10.46.10.5 (10.46.0.5), 64 hops max, 52 byte packets
1 cerberus.dmz.debln01.loc (172.24.2.62) 0.397 ms 0.240 ms 0.214 ms
2 ae0-17.frankfurt-1.celox.net (212.60.225.129) 1.724 ms 1.469 ms 1.960 ms
3 bras2.ber.qsc.de (92.197.130.22) 7.110 ms 7.486 ms 7.969 ms
4 core1.ber.qsc.de (87.234.13.141) 55.821 ms !N 40.591 ms !N 32.144 ms !N
[2.0.1-RELEASE][DGI@janus.debln01.loc]/home/DGI(12):
[snip]If I change the route from 172.24.2.20 into the other zone which is 192.168.0.0/16 it's working
Internet:
Destination Gateway Flags Refs Use Netif Expire
default 172.24.2.62 UGS 0 1981180 em1
8.8.8.8 172.24.2.62 UGHS 0 15844 em1
10.0.0.0/8 192.168.0.1 UGS 0 353213 em0
127.0.0.1 link#8 UH 0 225 lo0[2.0.1-RELEASE][DGI@janus.debln01.loc]/home/DGI(17): traceroute 10.46.10.5
traceroute to 10.46.10.5 (10.46.10.5), 64 hops max, 52 byte packets
1 zeus (192.168.0.1) 0.397 ms 0.317 ms 0.212 ms
2 pcdgi (192.168.10.53) 0.852 ms * 1.098 ms
3 10.46.10.5 (10.46.10.5) 0.906 ms 1.264 ms 0.616 ms
[2.0.1-RELEASE][DGI@janus.debln01.loc]/home/DGI(18): -
I have to agree that result is unexpected, and pfsense appears to be ignoring your static route, unless you have snipped some redundant route from the routing table that you posted.
-
Everything that passes out of a WAN interface (any interface with a gateway selected) gets routed to the WAN's gateway by default by the pass out rule, so if you have a static route on an interface with a gateway that goes somewhere other than the gateway on that interface, you need a floating rule to bypass said policy routing. Pass out on WAN from the appropriate source to the destination of the static route with no gateway selected with quick chosen.
-
@cmb:
Everything that passes out of a WAN interface (any interface with a gateway selected) gets routed to the WAN's gateway by default by the pass out rule, so if you have a static route on an interface with a gateway that goes somewhere other than the gateway on that interface, you need a floating rule to bypass said policy routing. Pass out on WAN from the appropriate source to the destination of the static route with no gateway selected with quick chosen.
Thanks, that did the trick :D