Port Forwarding - Step-by-Step - Demystified - pfSense 2 [SOLVED]
-
It took me a week of coasting pfSense forum posts, cookbooks and complaints about the difficulties, to figure out how simple it is to forward ports on this distro. The superiority and functionality of pfsense makes it easy to get lost when starting.
Get Ready Summary for Basic Forwarding:
-
pfSense requires NAT and Rule for basic port forwarding.
-
Create aliases for destination devices.
-
Create aliases for non-standard destination ports.
-
Create NAT:RULE in one step.
My setup was for SIP (VOIP), but I’ve stripped this down to any single or block or port(s) to a single machine on an internal network.
PFSENSE NAT-RULE CREATION
pfSense employs a two-step construct, port forwards are ‘allowed’ by RULES and ‘defined’ by NAT. This can be done in one step once your aliases are created. This is a sticking point.
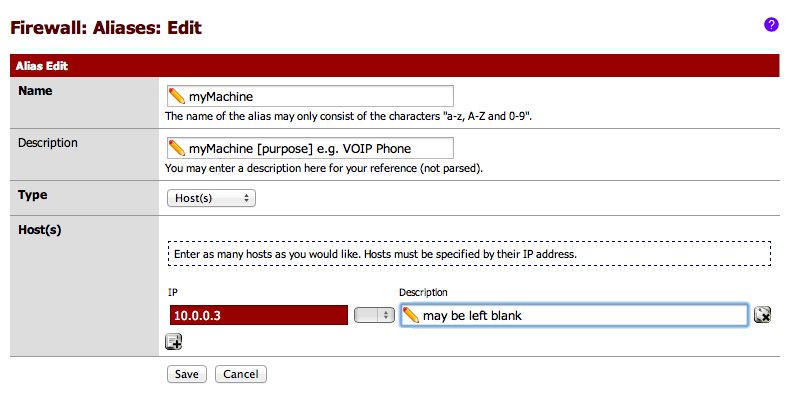
**ALIASES FOR DESTINATION DEVICE(S) (HOST(S)) *** Go to Firewall…Aliases from the main screen of pfSense 2.
-
Click the plus
 icon.
icon. -
Name your host (no spaces or symbols aside from underscore).
-
Description doesn’t matter, may be left blank, is not parsed.
-
Type: Host — we’re only doing one.
-
Click the plus
 icon under the Hosts, IP section.
icon under the Hosts, IP section. -
IP Address must match IP address of host on your network, if you’re using DHCP, check under Status…DHCP Leases to find the IP Address and make its address static.
-
Click ‘Save’ and then ‘Apply’ on the next screen.

ALIASES FOR NON-STANDARD PORTS
-
Go to Firewall…Aliases from the main screen of pfSense 2.
-
Click the plus
 icon.
icon. -
Name your port(s) alias (no spaces or symbols aside from underscore).
-
Description doesn’t matter, may be left blank, is not parsed.
-
Type: Port(s)
-
Click the plus
 icon under the Port(s) section.
icon under the Port(s) section. -
As an example, I want to forward port 2345 and ports 3580 through 3589 from the Wide Area Network (WAN) to one host on my Local Area Network (LAN).
-
First, I enter 2345 and press the plus
 icon.
icon. -
Enter 3580:3589 and press the Save
 button and then Apply button.
button and then Apply button.


CREATE NAT:RULE IN ONE STEP
-
Go to Firewall…NAT.
-
Click the Plus icon
 on the bottom-right.
on the bottom-right. -
Destination type, as far as I can tell, will ususally be any.
-
Enter your port(s) alias name in Destination Port Range.
-
Enter your Host alias name in Redirect Target IP.
-
See my example below, and make sure that Add associated filter rule is selected at the bottom before pressing Save and then Apply on the next screen.

That should do it. I’ll keep my eyes on this page for a while and invite criticism.Kirk****
-
-
Your FREAKING over complicating it with Aliases!!
Two weeks?? Really?? Nice run through and all - but come on??
How was this information not enough
http://doc.pfsense.org/index.php/How_can_I_forward_ports_with_pfSense%3FTo be honest the form in gui is pretty straight forward, just fumbling around the menu on pfsense and seeing the nat item and then forward should be pretty clear ;) You sure and the hell do not need to make aliases for forwarding to work.
-
With an alias you can port forward multiple ports instead of one.
And rules are easier to read -
NO rules are NOT easier to read - your telling me that myports tells you what ports are being used? Or that mymachine shows you what IP that is?
Sure if you need to GROUP a lot of ports together then an alias is a way to do that. But it sure and the hell is not easier to read the rules with them. And more often then not its going to be extra step and work, and extra place to make a mistake that a user that had to read a picture guide to figure out how to port forward is going to not be able to find.
-
Rules are easier to read with aliases, if you use desciptive alias names. And ofcourse if you do portforward with several ports those are definitely better than several portforwarding rules.
IM(NOT SO HUMBLE)O opinion is that aliases ease our lives, but it really depends how you use those.
No peas should be used on our nasal cavities
-
"Rules are easier to read with aliases"
Sure if I call the alias the port number and for the machine - then sure ;)
So extra step for NOTHING! How does creating a alias that is easy to read to something that if you just used the port and the IP you would know instantly what is going on.
As to grouping port. This can make for less rules in your listing sure, but only complicates looking at the list knowing what ports are being allowed/forwarded
2 rules here - which one is easy to see what is going on?

-
Both are understandable, but you didn't use descriptive name for that workstation, unless you know exactly what it is.
These things really are just how you prefer to adminster your firewall.I like that if have to allow ssh, http and https to server i do like to create only one rule what handles all of them, there is no point to click many times same kind of rule.
and example of my job. Our company had to move, because that building was going under destruction. And at our new place old isp couldn't supply internet again. We changed our isp also(I don't know why we don't have our own AS). Before moving we added to our remote access alias our new ip's and that was it. After we moved we just removed old ip's from those remote aliases. no hazzle and rulesets were untouched.
-
NO rules are NOT easier to read - your telling me that myports tells you what ports are being used? Or that mymachine shows you what IP that is?
Sure if you need to GROUP a lot of ports together then an alias is a way to do that. But it sure and the hell is not easier to read the rules with them. And more often then not its going to be extra step and work, and extra place to make a mistake that a user that had to read a picture guide to figure out how to port forward is going to not be able to find.
Johnpoz, darling, those alias names are 'placeholders' for a name that might be more descriptive to the person using the alias. I never said that aliases are necessary, I said that I did it that way, and no, the other port forwarding tutorials that I saw never made it clear that port forwards were a two-step process that was only made simple by starting with a NAT entry and ensuring that the paired RULE was automatically created.
I have been working with various firewall implementations for 15 years, this one's just a bit different. I'd limit criticism (which I did invite) to tutorials that do not, in fact, allow the user to complete their task or leave out vital steps as many of the pfSense port forwarding guides around the place do.
And yes, for my purpose I needed to group multiple discontinuous port ranges. I believe this is the way the developers of pfSense intend these features to be used. Why so hostile?
-
2.0.2 misses the redirect target port when doing GRE
-
Not wanting to be hostile - but your instructions IMHO are over complicating the process of simple forward.
Create aliases for destination devices.
Create aliases for non-standard destination ports.This is step 2 and 3 in your instructions. Now if your put say (optional) on the end statements and point out just using IP an ports it would be a great writeup. But your instructions make it seem like you have to create aliases, which is just not true and does not make it easier to read a list of rules.
When people post up rules that would show myworkstation or myports for help - this is useless to the person wanting to help. And no matter how descriptive you make the aliases, if does not work then its harder to verify that you did not make a mistake in the aliases.
Come on - you have been working with firewalls for 15 years, and it took you two weeks how to do a simple port forward.. You can not be serious!
I would say the one thing that throws new users to pfsense about forwards is that they create the forward and also need a firewall rule - this is different than most soho routers firmware. where you just create a forward, but the default is for pfsense to create and link the rule for you. Why people change this from the default is beyond me.. But you see it quite a bit. An other helpful hit would be just basic understanding –- 99 out of 100 times your source port is going to be ANY!!
-
Sorry for the bump but just wanted to say that I could not get port forwarding working at all…
Then I came across this post and it suddenly works! :)
I like the use of Aliases - similar idea to how checkpoint needs you to specify hosts.
-
Hello, I know this is marked as closed, but Im having trouble forwarding a port. Port 8081 to be exact. Here is my setup:
I am running VirtualBox with two guests. Guest one is pfsense with two nics (WAN and LAN). Guest two is Windows 2008.
pfsense WAN gets an IP from my HOST network, and pfsense LAN is set to a different network.
WAN = 192.168.1.35
LAN = 192.168.2.4The other Guest has an IP of 192.168.2.1 with a gateway of the pfsense LAN(192.168.2.4)
This allows my windows 2008 internet access from VirtualBox internal network.
I have apache installed on windows 2008 running on port 8081. If I change Windows2008 Nic type to Bridged Mode allowing it to be on the same network as my Host, I am able to connect to the apache server, so i know its running and works. With windows 2008 Back on VirtualBoxes internal network, I am trying to get port 8081 to be forwarded through but cannot.
Attached is a picture of my settings. Its not working, can someone help me with what I am doing wrong?
EDIT: I must have messed something up else where in the settings while playing with this. I reset to factory defaults, disabled the "Block Private networks" and its connecting just fine now.

