Snort block notifications script (third party script)
-
I ran across the site below that has a single PHP file that can be added to pfsense and set to run every every so often using cron. It will send alerts to the email address registered in the pfsense gui for notifications. It includes rwhois info and relevant snort alert logs to quickly deal with false positives. I am loving it so far.
https://rarforge.com/w/index.php/Pfsense
Hats off to whoever owns that site. I used crontab -e to create a cron entry as root instead of needing to install the cron gui management package which seems to have a beta status.
I made a few minor debugging changes to the script for when DEBUG variable is set but it is not needed as long as DEBUG is not set(by default it isn't). When DEBUG is set with the original script it doesn't return something in one of the functions which makes debugging pretty much useless.
-
I ran across the site below that has a single PHP file that can be added to pfsense and set to run every every so often using cron. It will send alerts to the email address registered in the pfsense gui for notifications. It includes rwhois info and relevant snort alert logs to quickly deal with false positives. I am loving it so far.
https://rarforge.com/w/index.php/Pfsense
Hats off to whoever owns that site. I used crontab -e to create a cron entry as root instead of needing to install the cron gui management package which seems to have a beta status.
I made a few minor debugging changes to the script for when DEBUG variable is set but it is not needed as long as DEBUG is not set(by default it isn't). When DEBUG is set with the original script it doesn't return something in one of the functions which makes debugging pretty much useless.
Glad you found the script useful. You are right about the debug being pretty much useless ( I guess I wasn't testing it script with DEBUG on). I updated the script on the wiki with the fix. It just needed - return array ($action,$body,$country,$netname,$inc_host); after the NotifyNewBlock function.
I'd like to add in some ignore options as I don't really care if it blocks china… but for now it's been doing it's job, just very chatty.
-
That is a good idea about ignoring some countries. That would reduce the background noise. The chances of a china network getting blocked that the users at a site that i setup need to actually access is pretty slim I would think.
I wonder if an inclusion or exclusion list would be bigger if the intent was to ignore alerts on ips in all countries except just a few (us, china, uk, etc). Pfblocker package already includes the lists I assume.
-
I forgot to mention that I set blocking on the snort instance on the Lan side. That keeps these alerts to a minimum.
-
quick and dirty - added two other features now. https://rarforge.com/w/index.php/Pfsense#snort_autoblock_notify.php
-
Exclude countries from notifications. $exclude_country = array('…');
-
Whois lookup will now check the parent block of an IP if it was reassigned/swip.
Example: IP: 76.28.152.x (comcast)
Before:
–---------------------- WHOIS -----------------------------
whois server: whois.arin.netComcast Cable Communications, Inc. WESTERN-1 (NET-76-16-0-0-1) 76.16.0.0 - 76.31.255.255
Comcast Cable Communications, Inc. WASHINGTON-20 (NET-76-28-128-0-1) 76.28.128.0 - 76.28.255.255
---------------------- END WHOIS ---------------------------Now:
–---------------------- WHOIS -----------------------------
whois server: whois.arin.netNetRange: 76.16.0.0 - 76.31.255.255
CIDR: 76.16.0.0/12
OriginAS:
NetName: WESTERN-1
NetHandle: NET-76-16-0-0-1
Parent: NET-76-0-0-0-0
NetType: Direct Allocation
Ref: http://whois.arin.net/rest/net/NET-76-16-0-0-1
Ref: http://whois.arin.net/rest/org/CMCS
OrgName: Comcast Cable Communications, Inc.
OrgId: CMCS
Address: 1800 Bishops Gate Blvd
City: Mt Laurel
StateProv: NJ
PostalCode: 08054
Country: US
Comcast Cable Communications, Inc. WESTERN-1 (NET-76-16-0-0-1) 76.16.0.0 - 76.31.255.255
Comcast Cable Communications, Inc. WASHINGTON-20 (NET-76-28-128-0-1) 76.28.128.0 - 76.28.255.255
---------------------- END WHOIS --------------------------- -
-
I like those additions.
Btw… I recall seeing a commit that mentioned something about allowing different subjects for mail notifications. I will have to go over the commit history on 2.1 and see if I can find it (or just confirm i am imagining things ;)).
Update: I found the commit...
https://github.com/pfsense/pfsense/commit/185f24c35ecdcb728f506401eae9bcd2a4a9cf50 -
I finally looked at the code and I realized the comment above is not enough as you should send notifications through notify_via_smtp() and not send_smtp_message() for duplicate checking (spam protection, etc). Since notify_via_smtp() doesn't support subject changes it was easy to modified the code on a firewall to do so. I gave it a third parameter which lets you customize the last part of the notification. Instead of the subject being…
somefirewall.exampledomain.com - Notification
It can now show...
somefirewall.exampledomain.com - Snort Blocked Notification
The lines I changed in 2.1 are in /etc/inc/notices.inc
function notify_via_smtp($message, $force = false) {
function notify_via_smtp($message, $force = false, $subjectpostfix = "Notification") {send_smtp_message($message, "{$config['system']['hostname']}.{$config['system']['domain']} - Notification");
send_smtp_message($message, "{$config['system']['hostname']}.{$config['system']['domain']} - $subjectpostfix");I then modified the snortblock notification script to send the subject as the third parameter. I also set the second parameter which forces sending to 0 to make sure duplicate messages still get dropped in case the same message gets sent multiple times for some reason.
notify_via_smtp($notify);
notify_via_smtp($notify, 0, "Snort Blocked Notification");I can now more easily know which alert this is. I wish all the alerts from pfsense did this so that you know what kind of an alert you are getting (cluster changes, config error, etc).
-
This sounds like something I will be trying soon.
Is there a way to disable getting alerts from certain SIDs?
Like TOR, DROP, CINS, RBN, Scans, DNS Amplifications, Policy MSSQL and MYsql.
Will it ever be packaged in the pfSense Package Repo?
-
Hi Adam and rarforge,
Would one of you consider adding some programming to this code to skip emailing reports for certain Alert SIDs?
-
Is there still any access to this script?
-
This is what I use for suricata, you may be able to tweak it a bit:-
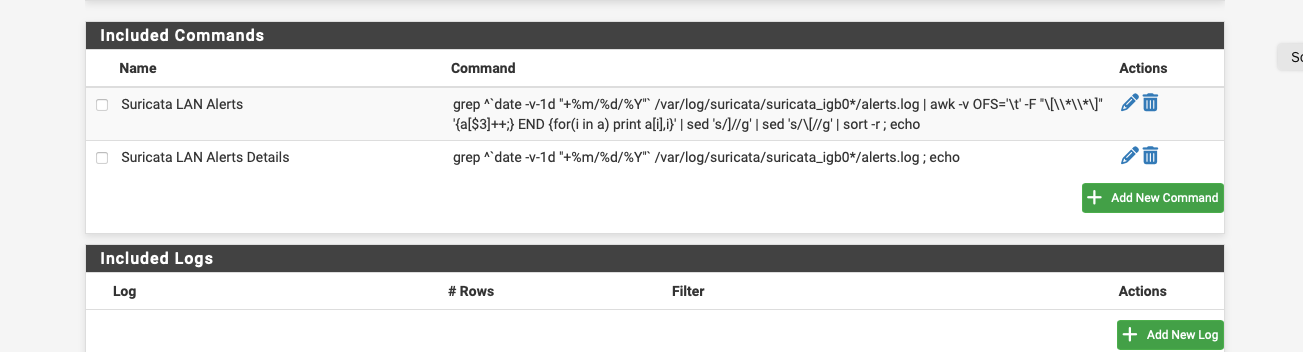
grep ^`date -v-1d "+%m/%d/%Y"` /var/log/suricata/suricata_igb0*/alerts.log | awk -v OFS='\t' -F "\[\\*\\*\]" '{a[$3]++;} END {for(i in a) print a[i],i}' | sed 's/]//g' | sed 's/\[//g' | sort -r ; echogrep ^`date -v-1d "+%m/%d/%Y"` /var/log/suricata/suricata_igb0*/alerts.log ; echo