[HOWTO] OPENVPN and traffic shaping GUIDE!
-
I have made Traffic Shaping work! Here is my Guide, I hope it helps others.
(This may need some tweaks for optimization, but this is working!)Assumptions:
- This guide traffic shapes WAN & OPENVPN traffic, but this guide can be used without an OPENVPN interface. Just follow the same guidlines
- The rules are applied from the perspective of the interface, not the standard traffic shaping rules like dd-wrt has. (see note 1 below)
Environment
PFSENSE: 2.0.3
WAN: PPPoE Single ADSL 3000/500 Mbs
LAN: Single private LAN (192.168.1.x /24)
OPENVPN Client: Enabled and Working• Keep in mind, the "WAN" in the diagram below is the same single PPPoE ADSL WAN link
• I do not need VOIP or PS3 traffic encrypted, so I created a rule to run it to the WAN interface directly.Client –> LAN –> WAN –> Internet (this is the path for VoIP and PS3)
|
–---> OPENVPN –> WAN –> Internet (this is the path for all other traffic)GOAL:
Prioritize traffic as follows- VOIP
- PS3
- Almost all remaining traffic
- Finally cloud Backup traffic
Step 1:
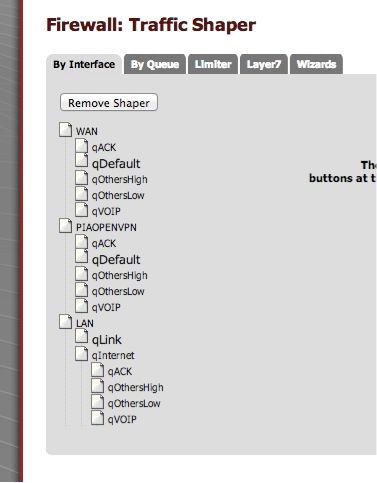
Here is how to accomplish this. Run the traffic shaper wizard. I choose 2 WAN interfaces. 1 for WAN and 1 for OPENVPN. Obviously, select one if you only have a WAN and no OPENVPN.Step 2:
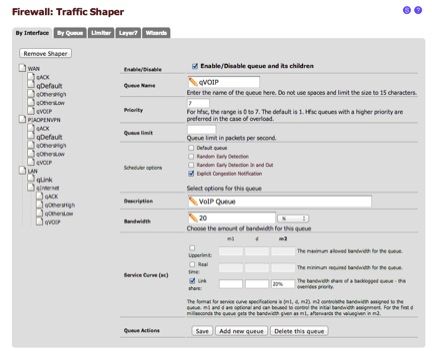
Open each one and make the section look something like this.Here are mine
Queue name/priority/linkshare%
qACK-6/20%
qDefault – 3/25% (checked as default also)
qOthersHigh – 4/15%
qOthersLow – 2/10%
qVOIP-7/20%Step 3:
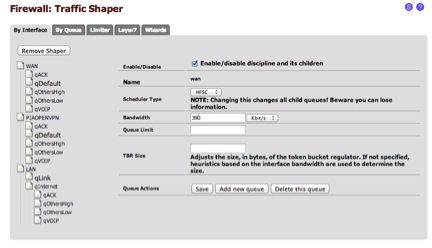
Ensure your bandwidth is setup correctly:
WAN and OPENVPN interface should have the same bandwidth settings. In my case, my 500 Mbps is actually 400Mbps (speedtest.net), so I choose 390 as my limit.Step 4:
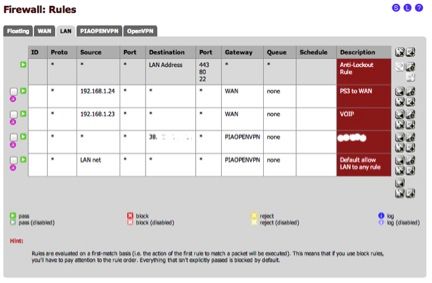
Now jump on over to Firewall rules. Go to LAN interface.
In my case, I added a 2 simple rules to send my LAN source IPs to the WAN directlyStep 5:
Add a rule for your cloud backup provider. Make sure you add it by destination IP or network to the OPENVPN interface.
Now add the default LAN path to the openVPN interface. Should look something like this when it is done.Step 6:
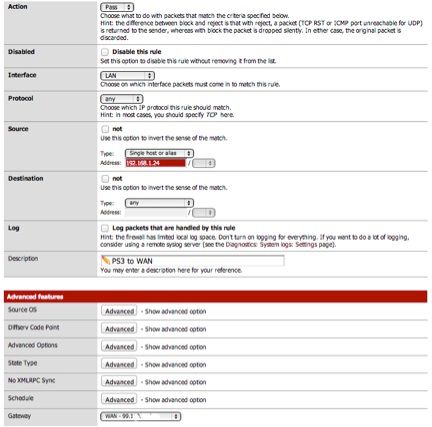
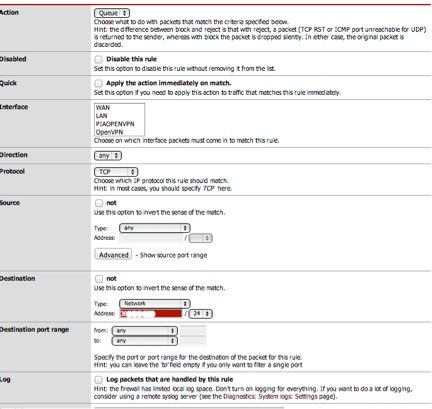
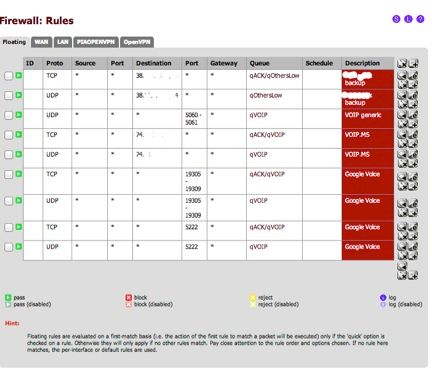
Now jump on over to the floating rules. Add them like this. Pay special attention to the Note #1 & #2 below. TCP with aQCK/Queue and UDP with just Queue. Now since this is bing applied to the WAN, local IP address will not work. So add the internet IPs of your destination or ports for your destination services.Put your bulk cloud back up servers to low queue
Put VOIP to the VOIP queue
Put PS3 traffic to High queueSpecial notes
- Actions should be queue
- Make sure there are NO interfaces are selected
- Directions ANY
- Protocol TCP or UDP, not both
- Destination is the internet IP, not your LAN addresses
- Select the queue
Step 7:
Now jump over to Diagnostics and States and reset the states. It takes about 2 minutes for the router to come back to life.
Results
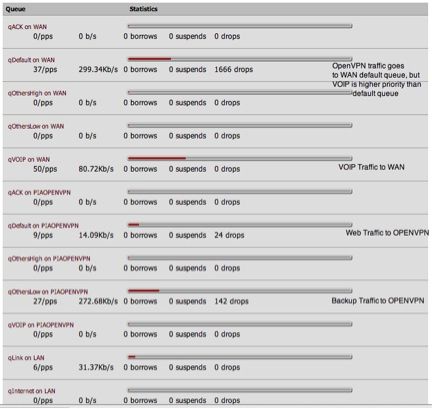
Cloud backup traffic and normal web traffic goes to the OPENVPN interface. Cloud traffic is low priority compared to the regular traffic.
All OPENVPN traffic dumps into the WAN qDefault queue.The VOIP and PS3 queues have a higher priority than the WAN qDefault, thus they take priority over all the other traffic.
Notes:
1) Rules must be from the perspective of the interface
In DD-WRT you could set a rule like this
VOIP LAN MAC address /IP address is priority Premium
PS3 LANMAC address /IP address is priority Express
All other LAN MAC address /IP address is priority Standard
P2P/Backup LANMAC address /IP address is priority BulkThis would make those internal devices priority on all WAN connections. SIMPLE!
This simplicity does not work with PFSENSE! This was a very frustrating part to learn. Since rules are from the perspective of the interface, the internal IP or MAC addresses of your LAN devices do not exist on the outside of your NATed WAN interface. Thus the rule will never get applied.
Your rules would need to look like this
WAN IP address (source IP or port) ⇒ Internet address (source IP or port)
Not like this
LAN IP address (source IP or port) ⇒ Internet address (source IP or port)2) Must have separate Floating rules for TCP and UDP traffic
So I learned that If you have a TCP/UDP rule that has a queue setup like qACK/qVoip and your traffic is UDP, all the VOIP traffic gets sent over the qACK queue. You don’t want this. So create 2 rules,
UDP floating rule with a queue like none/qVOIP
TCP floating rule with a queue like qACK/qVOIP
Do NOT create a rule like
TCP/UDP floating rule with a queue like qACK/qVOIP