PfSense to Cisco ISR IPSec VPN Issues
-
Hello,
Long time cisco user, just started playing around with pfSense.
So far, it doesn't appear that ipsec VPN functions as expected and was hoping for some help.
I'm following the guide here: https://doc.pfsense.org/index.php/IPsec_between_pfSense_and_Cisco_IOS
I've set up numerous Cisco to Sonicwall/Fortigate/etc. before and am surprised that pfsense is having such trouble with this simple task
Below is the debug output from pfsense
Dec 25 11:58:15 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4e0: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:15 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447910: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey X_SPDDUMP message
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey X_SPDDUMP message
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4c0: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447190: 10.20.30.0/24[0] 10.20.30.1/32[0] proto=any dir=in
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey X_SPDDUMP message
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4c0: 10.20.30.1/32[0] 10.20.30.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447190: 10.20.30.0/24[0] 10.20.30.1/32[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4c0: 10.20.30.1/32[0] 10.20.30.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447490: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey X_SPDDUMP message
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4c0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447190: 10.20.30.0/24[0] 10.20.30.1/32[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4c0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447490: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4c0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447790: 10.20.30.1/32[0] 10.20.30.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[1] recv()
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[2] recv()
Dec 25 11:58:16 racoon: DEBUG: reading config file /var/etc/ipsec/racoon.conf
Dec 25 11:58:16 racoon: DEBUG: hmac(modp1024)
Dec 25 11:58:16 racoon: DEBUG: no check of compression algorithm; not supported in sadb message.
Dec 25 11:58:16 racoon: DEBUG: getsainfo params: loc='10.20.30.0/24' rmt='192.168.10.0/24' peer='NULL' client='NULL' id=1
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey REGISTER message
Dec 25 11:58:16 racoon: INFO: unsupported PF_KEY message REGISTER
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey X_SPDADD message
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4d0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447190: 10.20.30.0/24[0] 10.20.30.1/32[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4d0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447490: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4d0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447790: 10.20.30.1/32[0] 10.20.30.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4d0: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447910: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: ERROR: such policy already exists. anyway replace it: 10.20.30.0/24[0] 192.168.10.0/24[0] proto=any dir=out
Dec 25 11:58:16 racoon: DEBUG: pk_recv: retry[0] recv()
Dec 25 11:58:16 racoon: DEBUG: got pfkey X_SPDADD message
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4d0: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447190: 10.20.30.0/24[0] 10.20.30.1/32[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: sub:0x7fffffffe4d0: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: DEBUG: db :0x801447490: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=in
Dec 25 11:58:16 racoon: [Unknown Gateway/Dynamic]: ERROR: such policy already exists. anyway replace it: 192.168.10.0/24[0] 10.20.30.0/24[0] proto=any dir=inNo logs on the cisco even with debug crypto ipsec/isakmp
Using the following settings in Pfsense 2.1
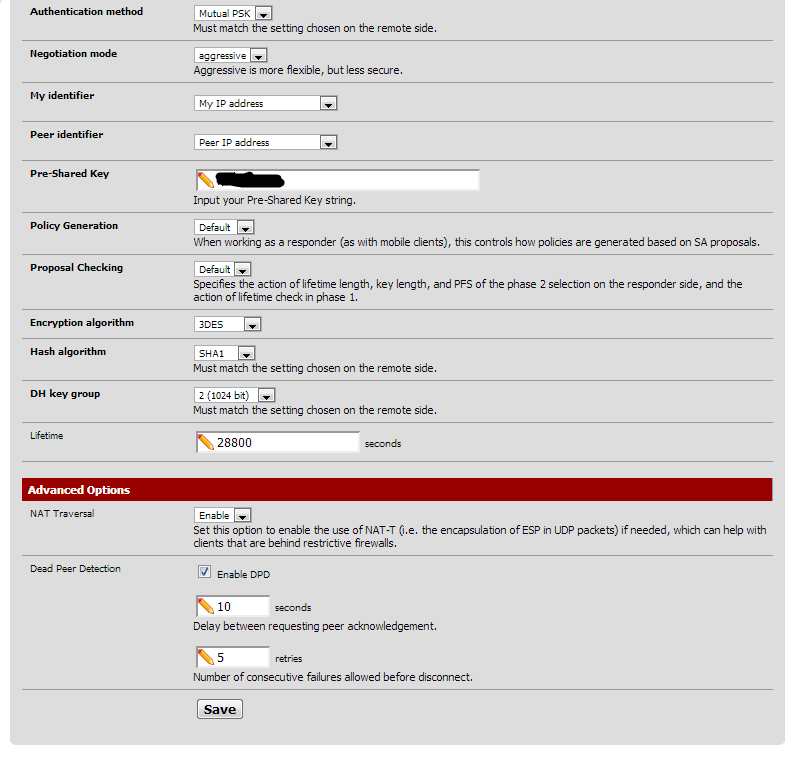
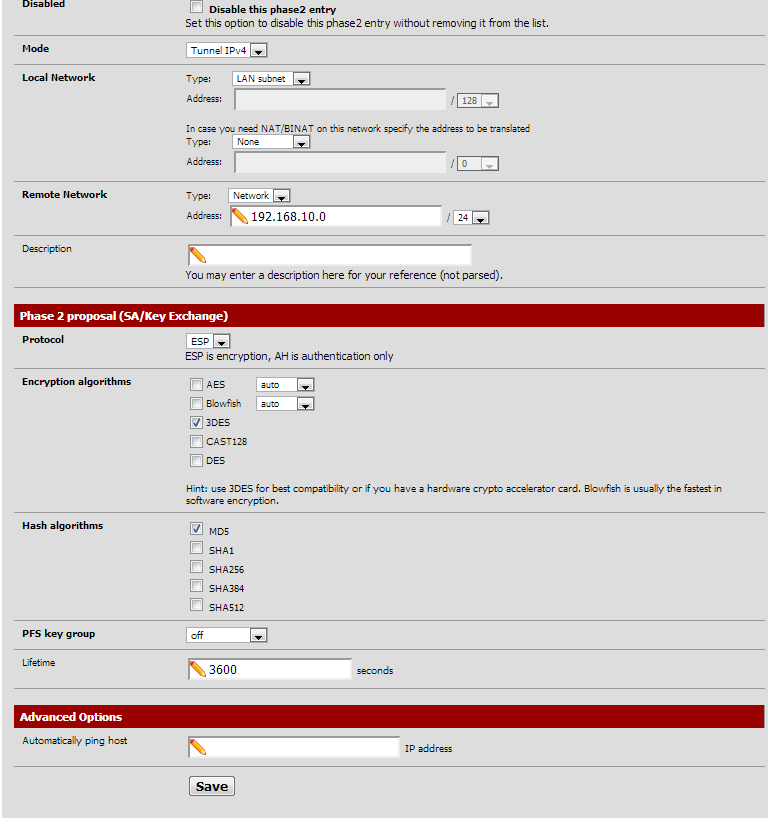
Phase1 and 2 match on the Cisco (3DES/SHA1/group 2 for phase 1, 3DES/MD5/no group for Phase 2)
(Also, as a side note, since I'm verified will I always have to type the captcha? The captchas on this site are terrible)
Thanks!
EDIT: Added the relevant parts of the cisco config as well
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
lifetime 28800crypto isakmp key PRESHAREDKEY address PFSENSEWANIP
crypto isakmp keepalive 3600 periodic
crypto ipsec transform-set VPNSET esp-3des esp-md5-hmac
crypto map IPSEC-MAP 10 ipsec-isakmp
set peer PFSENSEWANIP
set security-association lifetime seconds 28800
set transform-set VPNSET
match address TEST-VPN-ACLint WANINTERFACE
crypto map IPSEC-MAP! Have tried with and without this. Some site to site VPN seems to require this
ip route 10.20.30.0 255.255.255.0 PFSENSEWANIPip access-list extended TEST-VPN-ACL
permit ip 192.168.10.0 0.0.0.255 10.20.30.0 0.0.0.255
permit ip 10.20.30.0 0.0.0.255 192.168.10.0 0.0.0.255ip access-list extended NAT_ACL
deny ip 192.168.10.0 0.0.0.255 10.20.30.0 0.0.0.255
permit ip 192.168.10.0 0.0.0.255 any -
You haven't set the hash type in your crypto policy
-
If you're talking about the cisco config, SHA1 is the default and doesn't show up
-
After a few days trying this out, I think it's time to give up and try a different solution.
Was trying out pfsense for work, we are an MSP and were looking for some alternatives. While many of the other features may work great, ipsec is a must have and clearly isn't very mature.
What is more troubling is the many forum posts one finds with no replies in the ipsec category…
Thanks for the great project, look forward to seeing how it matures after a few years
-
Hello,
Have you already given up?
I've configured IPSec site-to-site VPNs between Cisco 1841 & 2801 routers, and between the Cisco 2801 router & a pfSense firewall.
Maybe we can try to find a solution, if you agree.Thanks.