Extreem low throughput
-
I have a problem with IPSEC.
I have configured a IPSEC tunnel with GRE (I need to do some special routing, so I need GRE)
Everything works, but I get very low throughput on the IPSEC/GRE tunnel, both ends are connected direct with a gigabit connection.
When I copy a large file over the network, I get only 4mbit with spices to 20mbit but a very unstable throughput at the same time I have a ping running from another machine and it's going from steady 1ms to jumpy 4 to 20ms.
Logfiles of IPSEC/Racoon say nothing special, just that the tunnel is setup rightSep 8 07:58:41 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.17[500]->172.16.8.22[500] spi=109112871(0x680ee27) Sep 8 07:58:41 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=127719491(0x79cd843) Sep 8 07:58:41 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=160971926(0x9983c96) Sep 8 07:58:43 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP 172.16.8.38[500]->172.16.8.33[500] spi=146599732(0x8bcef34) Sep 8 07:58:43 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.33[500]->172.16.8.38[500] spi=228854563(0xda40b23) Sep 8 07:58:43 racoon: [IPSEC FW2]: INFO: respond new phase 2 negotiation: 172.16.8.38[500]<=>172.16.8.33[500] Sep 8 07:58:43 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=15753609(0xf06189) Sep 8 07:58:43 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=164379843(0x9cc3cc3) Sep 8 08:46:42 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP 172.16.8.22[500]->172.16.8.17[500] spi=160971926(0x9983c96) Sep 8 08:46:42 racoon: [IPSEC FW1]: INFO: initiate new phase 2 negotiation: 172.16.8.22[500]<=>172.16.8.17[500] Sep 8 08:46:42 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.17[500]->172.16.8.22[500] spi=127719491(0x79cd843) Sep 8 08:46:42 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=42417108(0x2873bd4) Sep 8 08:46:42 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=117860727(0x7066977) Sep 8 08:46:44 racoon: [IPSEC FW2]: INFO: respond new phase 2 negotiation: 172.16.8.38[500]<=>172.16.8.33[500] Sep 8 08:46:44 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=162027152(0x9a85690) Sep 8 08:46:44 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=2195156(0x217ed4) Sep 8 08:46:44 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP 172.16.8.38[500]->172.16.8.33[500] spi=164379843(0x9cc3cc3) Sep 8 08:46:44 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.33[500]->172.16.8.38[500] spi=15753609(0xf06189) Sep 8 09:34:43 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP 172.16.8.22[500]->172.16.8.17[500] spi=117860727(0x7066977) Sep 8 09:34:43 racoon: [IPSEC FW1]: INFO: initiate new phase 2 negotiation: 172.16.8.22[500]<=>172.16.8.17[500] Sep 8 09:34:43 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.17[500]->172.16.8.22[500] spi=42417108(0x2873bd4) Sep 8 09:34:43 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=205171083(0xc3aa98b) Sep 8 09:34:43 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=63644472(0x3cb2338) Sep 8 09:34:45 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP 172.16.8.38[500]->172.16.8.33[500] spi=2195156(0x217ed4) Sep 8 09:34:45 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.33[500]->172.16.8.38[500] spi=162027152(0x9a85690) Sep 8 09:34:45 racoon: [IPSEC FW2]: INFO: respond new phase 2 negotiation: 172.16.8.38[500]<=>172.16.8.33[500] Sep 8 09:34:45 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=55345065(0x34c7fa9) Sep 8 09:34:45 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=107959198(0x66f539e) Sep 8 10:21:15 racoon: [IPSEC FW1]: INFO: renegotiating phase1 to 172.16.8.17 due to active phase2 Sep 8 10:21:15 racoon: [IPSEC FW1]: INFO: respond new phase 1 negotiation: 172.16.8.22[500]<=>172.16.8.17[500] Sep 8 10:21:15 racoon: INFO: begin Aggressive mode. Sep 8 10:21:15 racoon: INFO: received broken Microsoft ID: FRAGMENTATION Sep 8 10:21:15 racoon: INFO: received Vendor ID: DPD Sep 8 10:21:15 racoon: [IPSEC FW1]: INFO: ISAKMP-SA established 172.16.8.22[500]-172.16.8.17[500] spi:25c84f02badbf0b0:d128d5730e184f7c Sep 8 10:21:16 racoon: [IPSEC FW2]: INFO: renegotiating phase1 to 172.16.8.33 due to active phase2 Sep 8 10:21:16 racoon: [IPSEC FW2]: INFO: respond new phase 1 negotiation: 172.16.8.38[500]<=>172.16.8.33[500] Sep 8 10:21:16 racoon: INFO: begin Aggressive mode. Sep 8 10:21:16 racoon: INFO: received broken Microsoft ID: FRAGMENTATION Sep 8 10:21:16 racoon: INFO: received Vendor ID: DPD Sep 8 10:21:16 racoon: [IPSEC FW2]: INFO: ISAKMP-SA established 172.16.8.38[500]-172.16.8.33[500] spi:a9767b2315e70da1:b16ecafbf951e190 Sep 8 10:22:44 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP 172.16.8.22[500]->172.16.8.17[500] spi=63644472(0x3cb2338) Sep 8 10:22:44 racoon: [IPSEC FW1]: INFO: initiate new phase 2 negotiation: 172.16.8.22[500]<=>172.16.8.17[500] Sep 8 10:22:44 racoon: [IPSEC FW1]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.17[500]->172.16.8.22[500] spi=205171083(0xc3aa98b) Sep 8 10:22:44 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=64373214(0x3d641de) Sep 8 10:22:44 racoon: [IPSEC FW1]: INFO: IPsec-SA established: ESP 172.16.8.22[500]->172.16.8.17[500] spi=30180720(0x1cc8570) Sep 8 10:22:46 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP 172.16.8.38[500]->172.16.8.33[500] spi=107959198(0x66f539e) Sep 8 10:22:46 racoon: [IPSEC FW2]: INFO: IPsec-SA expired: ESP/Transport 172.16.8.33[500]->172.16.8.38[500] spi=55345065(0x34c7fa9) Sep 8 10:22:46 racoon: [IPSEC FW2]: INFO: respond new phase 2 negotiation: 172.16.8.38[500]<=>172.16.8.33[500] Sep 8 10:22:46 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=5852710(0x594e26) Sep 8 10:22:46 racoon: [IPSEC FW2]: INFO: IPsec-SA established: ESP 172.16.8.38[500]->172.16.8.33[500] spi=155524182(0x9451c56)The MSS clamping is set to 1360
MTU size is set to 1412
I have played with both settings, but no improvement.drawing:
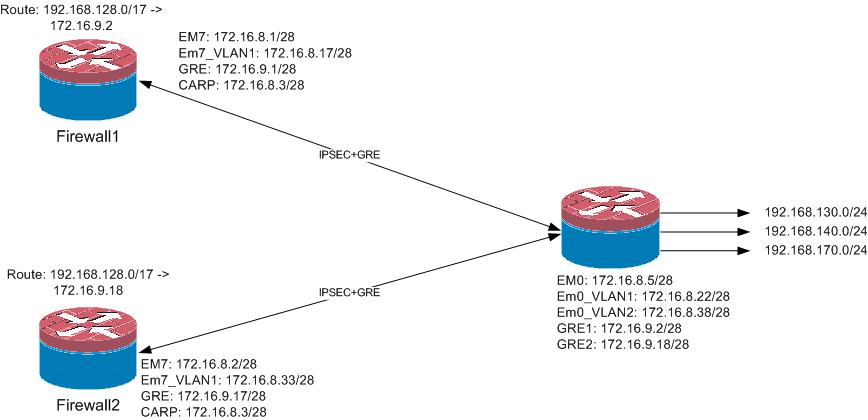
What's not in the drawing, the GRE tunnel runs over the VLANS.
from the 3rd firewall there are 2 ipsec tunnels, routing is policy based and the redundancy is done by a gateway failover (gw1: 172.16.9.1, gw2: 172.16.9.17)My first setup was ipsec to the 172.16.8.3 CARP adress, but that didn't work very well IPSEC and CARP.
Somebody knows what's wrong in here?