[SOLVED] No DNS Resolution for vlan
-
Hi everybody,
I have a very strange situation and I am sure that I missed just one click to complete my desired setting.
I have a pfsense (v 2.1.4), a zyxel switch (GS1910-24) and a tp-link access point (TL-WA801N).I have defined to SSIDs on the access point:
- home with vlan-id 1
- guests with vlan-id 200
If I connect to "home" I receive a correct IP from PFSense within the subnet 5.x, gateway 5.1 (=pfsense) and I can browse the internet
If I connect to "guests" I receive a correct IP from PFSense within the subnet 2.x, gateway 2.1 (=pfsense) and I can ping the pfsense from the client and pfsense can ping the client. I can access pages directly like: "http://5.35.240.23/" but www.google.de is not working.My questions:
- this sounds like a DNS Problem, right? Because I have internet access but only if I browse directly to an ip.
- Do you have any idea what I missed to make sure that PFSense works correctly as a DNS Server?
Hints:
- DNS Forwarder is activated
- there is an allow any rule for the vlan-id200 in pfsense
- I can ping www.google.de from PFSense webinterface with the source VLAN200
Thank you very much for your help.
Best regards
Christoph -
Hi everybody,
I found the solution!!! just for all the other who might face this problem. I had a allow any rule, but this rule was only for "tcp" Requests - and DNS requests are "udp".
As I said it was only one more click.Now I have 4 rules for my vlan200:
Allow TCP, port 80 to anything but LAN (= !LAN)
Allow TCP, port 443 to !LAN
Allow UDP, port 53 to 192.168.2.1 (Pfsense)
Block everything else.Best regards
Christoph -
Thanks bro i was getting the exact problem. Didn't realize the Allow Any rule was only for TCP. Thnx a bunch.
-
selbes Problem hier... meine Güte bin ich blöd, da hätte ich aber auch selber draufkommen können... vielen Dank Dir. Das wars bei mir
-
@christophdb said in [SOLVED] No DNS Resolution for vlan:
I had a allow any rule, but this rule was only for "tcp" Requests - and DNS requests are "udp".
You're still not there.
Handling TCP and UDP is ok, but there are more - like 50 or so ? - protocols.
The next best that you probably shouldn't block is ICMP. Better get used to include this one, because the day you'll adopts IPv6, ICMP becomes pretty mandatory.True : the other 47 are less known, less used.
But beware of the pitfall : in the future you install that new great app that does super things ..... and omg it doesn't work with pfSense ! .... because you took wrong decisions when "setting up your own firewall rules".I've solved the issue for myself with these selected two rules :
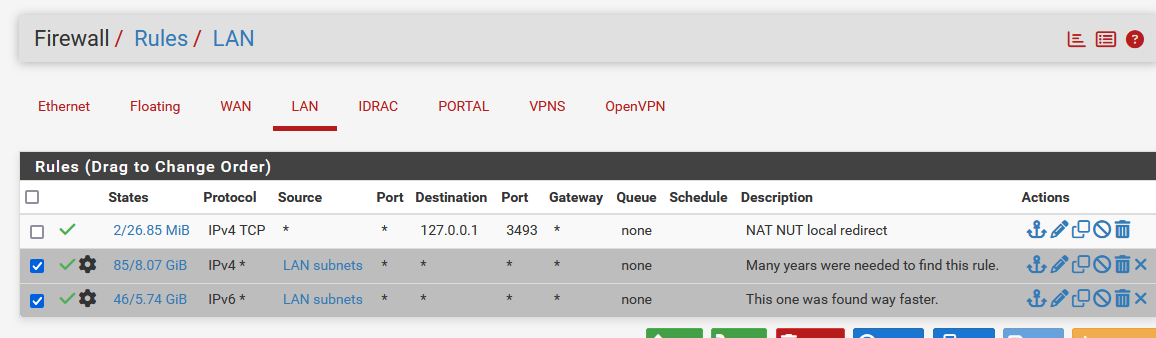
and I found out later that these two rules are the ones present on the LAN interface when you install pfSense from scratch.