Block Traffic Between Subnets?
-
I would like to block traffic between subnets while having Internet access for all. I tried following this guide: Isolating Subnets in pfSense
Unfortunately, I am not able to access the Internet anymore.
I'm very new to pfSense and a lot of what I have been reading is going over my head.
-
Why would try to use such a shitty guide??
So lets call your "subnets" lan 1 and lan2? I assume you have 2 lan interfaces on pfsense right - or are these vlans using one physical interface?
So on lan1 or the default lan has a rule out of the box that is any any - this allows your lan clients to go wherever they want, internet, other segments connected to pfsense on OPT interfaces, etc.
When you create a new segment on a new inteface, OPT1 for example there are not default rules - nothing. If you want it to be the same as lan then you would create a new rule any any and everyone can talk to everyone.
Now if you rename your lan to lan1 and your opt1 to lan2 the rules are this simple
If you do not want lan1 to talk to lan2, simple rule change on that any any rule by default change it to dest ! Lan2
On lan2 make dest ! lan1
This rule mean NOT lan1 or NOT lan2 as your destination - so they can go to the internet, but they can not go to your other lan segment.
See attached pictures
1st pic is default lan rule rule that allows any any
2nd pic is rule create on your 2nd segment just like default any any. - everyone can now to talk to everyone even internet.3rd pic is how you edit the rule - dest ! (not) and the other lan
4th is showing rule for lan1 that can NOT go to lan2
5th is showing rule for lan2 that can NOT got to lan 1Ther you go your segments can not not talk to each other. If you want to allow specifics things to talk between then you would create the specific allow rule you want above the NOT rule.





-
Agreed, that guide is horrible. It seems to exhibit some pretty fundamental lack of understanding throughout.
The OP wasn't to know that though.Steve
-
johnpoz - Thank you very much for making it very easy to understand :)
I'm using a quad-port Intel nic in a spare computer (no VMs).
It took a few minutes but I have it working now after following your post.
When I had your 2nd pic rule (LAN2 … any) with the 5th pic rule (LAN2 net ... ! Lan1 net) together, nothing was blocked even when changing the order. Once I removed the Lan2 ... any rule, there is Internet access.
-
Agreed, that guide is horrible. It seems to exhibit some pretty fundamental lack of understanding throughout.
The OP wasn't to know that though.I don't know this comment he makes at the bottom kind of tells me its gibberish ;)
"It could very well be that my approach is STILL all wrong. Maybe it is catastrophically wrong! I feel stupid even posting this on the Internet,"
"When I had your 2nd pic rule (LAN2 … any) with the 5th pic rule (LAN2 net ... ! Lan1 net) together"
What rules did you have together - there should not be any rules together on your interfaces in this simple setup. Only when you were going to make exceptions to this rule would you put rules above it. Rules are parsed top down when looking at interfaces in pfsense.
-
Ha! Yes.
I meant the OP of this thread but I guess there were warnings. ;)
To be fair to the poster of that blog it's not written as a guide, more as a log of what didn't work for their own benefit.Steve
-
After implementing these rules, I haven't touched the pfSense except to backup the configuration & update the release. I discovered this problem when I had Windows laptop set for Obtain an IP address automatically and had the static IP set in Alternate Configuration instead of Use the following IP Address.
I'm running 2.3.2 (latest version) and the Windows DHCP Server (LAN) is handing out IP addresses for devices on other subnets (OPT1 & OPT2). It is not an option to turn off the Windows DHCP Server because it breaks the server.
If you look closely at the image, you will see that Laptop 1 is connected to WAP-1 (Laptop 2 … WAP-2) but is getting an IP address for the LAN. No DHCP Server is running on OPT1 & OPT2 because static IP addresses are given.
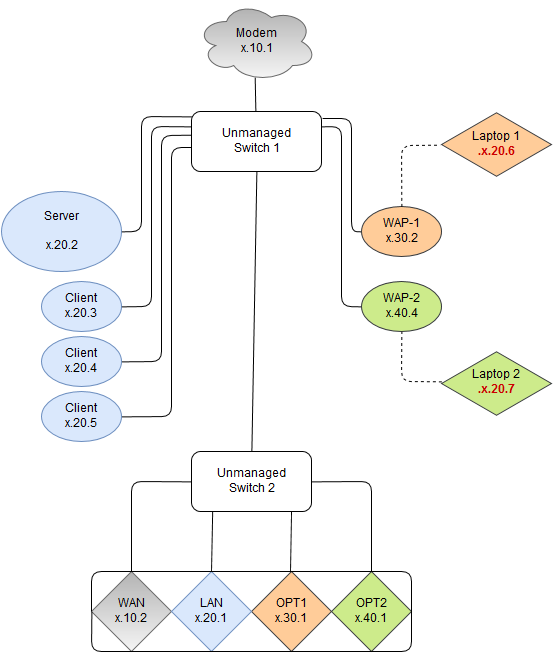
When I plug the WAPs directly into pfSense, the laptops were unable to get an IP address automatically and used the alternate configurations.
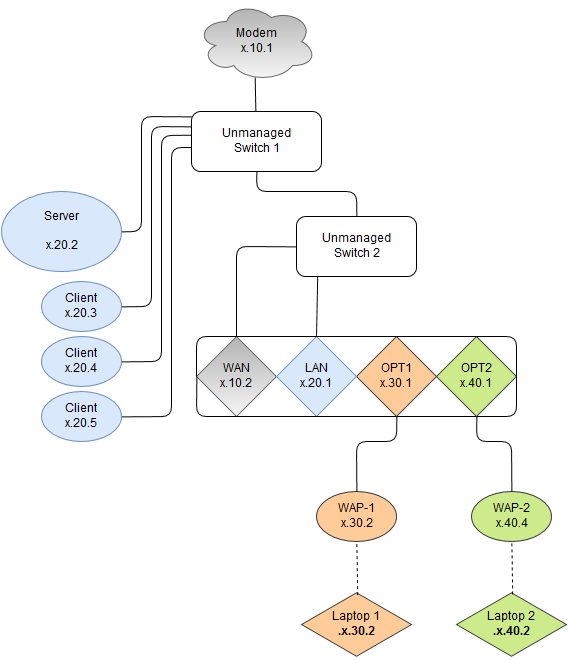
Due to the location of pfSense, I have to run it from an unmanaged switch to another unmanaged switch. Moving things or running more cable is not an option so I need to have this fixed through the rules.

-
WTF?! If all you have are dumb switches, then pfSense is supposed to be connected directly to your modem. Everything else goes behind it, through the switches (one switch per interface required).
-
WTF?! If all you have are dumb switches, then pfSense is supposed to be connected directly to your modem. Everything else goes behind it, through the switches (one switch per interface required).
The modem was placed in an area which only allowed enough space for an unmanaged switch and all the cables were run to that location long before my time. If I was able to have modem –> pfsense --> switch per interface, I would be doing it that way but that is not possible.
-
You cannot do that. You need to separate all your LAN segments into VLANs using managed dot1q-capable gear.
You do not need to pull more cable. VLAN tagging allows you to run multiple, isolated layer 2 networks on one cable. You do need proper, managed switches however.
-
So why are you just coming back to this thread from 2014?? And where exactly is pfsense in those drawings?
But as stated your running multiple layer 3 over the same layer 2 - this is BORKED!!! You need vlan capable switches to have more than 1 network on the same switch and be isolated.
-
Um, yeah you need VLANs if you can't physically moved the different bits of equipment.
Potentially your WAPs might be able to tag traffic directly and your unmanaged switches might pass that tagged traffic which would allow you to isolate that traffic to pfSense. But that still leaves WAN and LAN in the same layer 2 which is all wrong!
Steve