Portforwarding problems with port 53
-
Hi
First message and a problem.
I´ve been having some problems with pfsense and port-forwarding on port 53 to one of my dns servers on LAN interface.
On pfsense version 2.1 everything worked until november. And then it stopped. So I decided to wait for the next release and do a clean/new install.
did that so the version is now 2.2 x64. I have contacted my ISP and they are not blocking port 53.
I have set i three port-forwarding rules see attachment.
The icmp and 3389 rule working perfect. And the 3389 was just for testing. but the port 53/dns rule is not working at all.
DNS Forwarder and DNS Resolver is disabled. The NAT method is pure nat.
The DNS Server is working and responds on port 53.
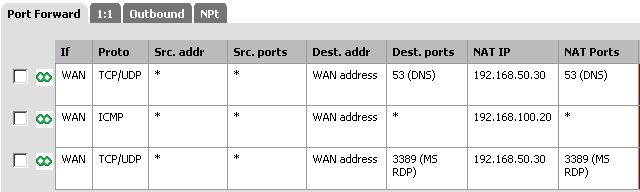
I have worked through the port-forwarding troubleshooting.
I have run out of ides almost. Where is the config file for port-forwarding located?
Anyone any ideas?
/nmd
-
What does the nat reflection method have to do with this?? So your testing from inside your network to your public IP?
Did you have someone test from actual outside? if you followed the troubleshooting guide, did you see packets on your wan? Are they forwarded on your lan to your dns box? Simple packet captures shows us this.
What is your dns server? Ah clearly windows if you stated rdp worked to the same box. What is the settings on the windows firewall? You allowing for queries from other than your local network?
-
I have tested from the outside and it did not forward. So then i tested from the inside and it worked!
Yes it´s a windows server. And It has not been changed since a year back.
Yes port 53 is open and working and queris from other network is allowed.
Will post loggs later of firewall
-
well lets see the packet captures.. Either the packets are there and didn't get forwarded, or they are not there. Not sure why those were not posted from the get go since you say you walked through the troubleshooting guide
step 5 would give you the definitive source of the problem.
-
didn't have any log with me at the time.
but I have just made a portscan on port 53 on my ip from ipfingerprints.com.
–---------------------------------------
LOG Packet Capture19:51:26.680499 00:0c:29:97:c8:25 > 00:1b:0d:ee:98:c0, ethertype IPv4 (0x0800),
length 95: (tos 0x0, ttl 127, id 1833, offset 0, flags [none], proto UDP (17),
length 81)
..*.71.31741 > 195.54.122.200.53: [udp sum ok] 14198+% [1au] A?e9476.ksd.akamaiedge.net. ar: . OPT UDPsize=4000 OK (53)
19:51:26.762633 00:1b:0d:ee:98:c0 > 00:0c:29:97:c8:25, ethertype IPv4 (0x0800),length 111: (tos 0x0, ttl 58, id 59601, offset 0, flags [none], proto UDP (17),
length 97)
195.54.122.200.53 > ..*.71.31741: [udp sum ok] 14198 q: A?e9476.ksd.akamaiedge.net. 1/0/1 e9476.ksd.akamaiedge.net. A 69.192.64.38 ar: .
OPT UDPsize=4096 OK (69)
-
dude what part do you not understand about sniffing on the wan and the lan and doing a query to your nameserver??
What is your public IP? PM it to me.. And I will see if it answers on 53.
-
So that IP answers ping, but no dns - not udp or tcp, don't even get a syn,ack if try tcp.
So either the traffic is not even getting to you for dns, or your forwards are wrong..
If you sniff on your wan I can send queries that you would see, and then on your lan you should see pfsense send on the traffic and your box respond. This is really click click sort of stuff. I can pm my IP to you so you know what IP to be looking for as you can see in the bottom pics starts with 24.13
So look, click click port forward tcp/udp 53 to my box running bind. Now it has NO ACLs to allow queries from the public net, but you see that it answers with REFUSED. So connectivity is there.
then the next too are sniffs on the wan interface showing my remote box doing a query and getting an answer. And If I snff on the lan you see the remote being sent on to my private IP 192.168.1.7 and it answering.



