Can pfSense's DHCP server update Microsoft DNS?
-
Inside pfSense under the DHCP Server options, it looks like it's able to send a dynamic DNS update to a DNS server.
It has the following options (in pfSense's DHCP server):
Enable registration of DHCP client names in DNS. Enter the dynamic DNS domain which will be used to register client names in the DNS server. Enter the primary domain name server IP address for the dynamic domain name. Enter the dynamic DNS domain key name which will be used to register client names in the DNS server. Enter the dynamic DNS domain key secret which will be used to register client names in the DNS server.Can anybody point me in the right direction on how to get this working so pfSense's DHCP registers the hostnames in a Microsoft DNS server?
-
At a loss to why you would want to do this? Why not just have AD dhcp be your dhcp server if your using AD for your dns, etc. Seems like your over complicating it.
-
Well, I have a dedicated router (physical hardware) but my domain controller is on a virtual machine on different hardware.
Because this is on a home network, if my domain controller (or virtual server) is down, I'd still like internet access to be available to my other devices. (i.e. iPad, etc)
-
what does that have to do with registering dhcp in AD?
If your AD vm goes down, and your pointing to it for dns your still going to be down.
You have your clients pointing to dns both at your AD and pfsense. Members of AD should ONLY Point to AD for dns, you can not split dns that do not have all the same information or you going to have problems.
If your worried about your AD vm crashing and not having internet.. Why not just setup dhcp on pfsense only when that happens, takes what 5 seconds to enable. So you set it up, and if your VM crashes you enable it.. Have your clients renew dhcp and big bang zoom your on the internet again.
How do you have your client setup now, pointing to both pfsense and your AD for dns? This is borked setup.. AD members should only point to AD DNS, this AD dns can then forward for external lookups or direct to roots. Having a client point to say pfsense at 192.168.1.1 and AD dns at 192.168.1.2 is not good configuration. Unless you had full sync of all dns records for your AD, etc. And since unbound or dnsmasq can not do that - are you running bind on pfsense?
-
OK - I'm still learning all of this, so I do appreciate your help.
My plan was to use pfSense for DHCP and Windows for DNS. pfSense's DHCP would hand out the Windows DNS as primary DNS, and Google DNS (8.8.8.8) for secondary DNS. This way if the domain controller was offline, clients could still obtain an IP address and resolve DNS queries.
Because this is only for a home network/lab, it's important to me to "decouple" the domain controller as much as possible from internet access.
I understand what you're saying about being able to toggle pfSense DHCP on and off, but I'm really hoping for something more automatic.
Here's a scenario I'm thinking about:
At my house, the power goes out and all servers are offline. The power comes back online and the router and cable modem work fine. However, my virtual server cannot start due to a hardware failure, etc. If I'm relying on my virtual server (domain controller) for everything, then nothing at my house will be working until I get home to fix it.
This type of scenario doesn't make sense in a full production environment, but I'm looking to use this for different purposes. (also, before anybody asks, I have a full MSDN membership allowing licenses for Microsoft products for development/education purposes)
I really, really do appreciate your help!
-
"Windows DNS as primary DNS, and Google DNS (8.8.8.8) for secondary DNS."
That is not how you would do it.. if your machines are members of your AD.. then the ONLY dns they should point to should be to your AD DNS.. google at 8.8.8.8 has no clue to anything to do with your AD.
Be it your setting up AD in production, home lab whatever.. if a box is a member of AD then the only dns it should point to is AD DNS - period!!! Now you can have more than 1 dns server listed if they are both your AD dns.. What your going to do is borked from the get go.
If you want your machines to join your AD, then they should point to your AD for dns, and dhcp for that matter makes it easy for your AD to keep track of its members and when their IPs change, etc.. Now you setup your AD dns to forward to 8.8.8.8 if you want or have it look up from roots, or forward to pfsense.. But having 2 different dns servers 1 public and one AD on a client that is joined to AD is not good setup.
If you want to run AD and are worried about hardware failure, then you should have 2 DCs etc.. To be honest I see no reason to run AD in the home, other than play and test - and you can do that with a vms, etc..
To be honest who is to say that pfsense doesn't have a hardware failure, and now nothing works til you get home anyway. I run pfsense in VM, I have a domain as well - but my actual machines and laptops are not joined to it because there is no real use of that sort of setup in a home. I have other vms joined to the domain for when I have to test something or want to play with something, lab it etc..
I have had power outages in my home - but then again I have my esxi box on a UPS, and also have my modem and switch and since my AP are poe - even when there is a power outage my internet works for 20 to 30 minutes before everything starts shutting down ;)
So get UPS or 2 if your worried about power outages ;)
-
Yeah, I think that AD might be overkill but my goal was to be able to synchronize UIDs and GIDs across my different VM servers.
Here's a list of my machines:
Windows PC (gaming, physical machine)
MacBook (physical machine)
Router (pfSense, physical machine)
ESXi (physical machine)On my ESXi box, I have lots of virtual machines:
File Server (VT-d passthrough of HBA cards and 16x HDDs, shares using NFS and SMB)
Media Server (Plex, AirVideo, etc)
Download Server (Nzbget, etc)
Web Server (Nginx)
Build Server (OSX project building)I thought that Active Directory might be nice to synchronize my username/password across all machines but should be looking at something else maybe?
Should I maybe look into FreeIPA or something even simpler?
-
what user names are you going to sync? How are you going to sync say username on pfsense to your AD? Might be simpler to just setup a radius or ldap server and use that login to your different devices. Freeipa might be a solution for you sure.
I do believe freeipa can have window machines auth with use of ksetup on the windows machine. You could use pGina on your windows machine as well to point to different auth methods vs just local accounts so you could use something that all your devices support.
Not sure about esxi, while it does support AD login I do believe you need the non free license to do that, since you would have to use vserver vs just the client to manage your host.
-
@sofakng said in Can pfSense's DHCP server update Microsoft DNS?:
Inside pfSense under the DHCP Server options, it looks like it's able to send a dynamic DNS update to a DNS server.
It has the following options (in pfSense's DHCP server):
Enable registration of DHCP client names in DNS. Enter the dynamic DNS domain which will be used to register client names in the DNS server. Enter the primary domain name server IP address for the dynamic domain name. Enter the dynamic DNS domain key name which will be used to register client names in the DNS server. Enter the dynamic DNS domain key secret which will be used to register client names in the DNS server.Can anybody point me in the right direction on how to get this working so pfSense's DHCP registers the hostnames in a Microsoft DNS server?
I'd like to know the exact answers to these questions, and I hate that this thread goes off topic about a whole different way of solving the problem instead of at a bare minimum, answering the question.
There are reasons to want to have external DCHP servers (e.g. you have many networks distributed across the country, and not all of them are Microsoft networks, and some of them have local DHCP servers, but you still want all of that feeding back into your centralized MS AD DS and DNS.
Anyway, this time, somebody please answer the question instead of trying to talk me out of what I'm doing. Which key(s) are supposed to be used in this scenario? The KSK? The ZSK? Some other key(s)? Thanks in advance for any help!
-
The answer is NO.. Is that direct enough for you..
-
@johnpoz It's a pretty dickish way to say it, but yes, it's the answer you should have posted 5 years ago if that's indeed the case.
The rest of the internet is not clear about this. Microsoft DNS supports
RFC 2136, and even supports unsecure updates, so it should be possible. It seemsdhcpdwon't even try if the update is not secure? This is also unclear from the documentation, but may be the case. -
Your clients will update the SOA of the domain.. Have them do that..
-
@johnpoz Though, you STILL didn't answer the actual other question about "which keys are supposed to be used in this approach" I'll answer that here for future people on the internet, since this forum is supposed to be useful and provide answers:
This page answers the question of where the key comes from (e.g. on
Linuxwithbind9) and how to generate it and apply it:
https://archyslife.blogspot.com/2018/02/dynamic-dns-with-bind-and-isc-dhcp.htmlAnd this page answers the question w.r.t.
PowerDNS:
https://doc.powerdns.com/authoritative/dnsupdate.htmlEven if Microsoft DNS doesn't support the secure key, it should still support insecure updates, so I'm going to keep trying to understand what is needed to make
dhcpdandMicrosoft DNScommunicate in that scenario. Unfortunately here be dragons because it seems either not documented or nearly impossible to find with a google/duckduckgo search. -
@johnpoz Linux clients don't do that by default. I presume you suggest that I should join all of my Linux clients to the domain? But that's part of the thing - I don't want to join hundreds of Linux servers to the AD DS domain (first and foremost because it's a pain to do, and not easily scalable, and second because it involves installing a lot of extra software [samba, kerberos, etc.] on the linux machines which I don't really want them to have). I just want DNS to know about them, but for them to stay otherwise in a separate Linux universe.
See the issue? It should be solvable via
RFC 2136via aDHCP server- but it does not seem documented how (unless you're using anMicrosoft DNSserver, and then it is documented how - at this link: https://ephemeralelectrons.wordpress.com/2017/07/19/dynamic-registration-of-dns-for-linux-devices-in-an-active-directory-environment-with-windows-dns-server/). -
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-name-resolution-ddns
@layla This article from Azure documents how to do secure updates with
bind9andMS DNSusing the linux version ofnsupdate(the using-gwith the keys mentioned above forbind9and-kwithkerberosforMS DNS(though again, this goes back to basically enrolling into the domain for theMS DNScase.)It also talks about insecure updates from
linuxdirectly withnsupdateduringifup/ifdownvia scripting. This could sort of work, but it's so much less elegant to modify hundreds of linux machines (particularly where they need to be changed in different ways because e.g.Ubuntu 18.04 LTSdoes things differently thanUbuntu 20.04 LTS, etc.)...So again, if
nsupdatecan do it (insecurely), why can'tdhcpd? It sure seems like it should be possible. But does seem not documented... :/ -
This tutorial seems like pretty much what you're looking for with an external DNS server being told about DHCP lease IPs + names - https://freeipa-users.redhat.narkive.com/xJVbXRdO/pfsense-dhcp-to-ipa-s-bind-dynamic-updates-success.
-
@layla I know this is old, but could you come up with a solution. I made some research here, hoping one could configure Windows DNS server to accept unsecure update from just one source. That would help a little, as long as pfSense could send unsecure updates on behalf of the clients (I'm not sure it can). Anyway, it seems we can't limit that in Windows.
On the other hand, it would be interesting if we could configure those DNS Domain Key and DNS Domain Key Secret on Windows DNS Server. It seems it is a no go, also, right?
-
I just saw the new KEA DHCP server implementation doesn't even have the DNS update feature. The KEA has a separate daemon for that, the DHCP-DDNS server. I'm not sure if it is available for pfSense (the package list is not being updated on my systems right now). I know it can do unsecure updates.
-
The "25.07.1" (and probably 2.8.1) Kea can do 'DDNS' just fine. Everything is already there, it's just not yet made avaible in the pfSense GUI.
You want to read this : ISC DHCP Dynamic DNS feature and Kea DHCP where I demonstrated a IPv6 DDNS update. I was updating against a "bind9 domain name server".
It worked pretty well, although I was only updating IPv6 IPs, as updating IPv4 RFC1918 (!) IPs into the domain name server doesn't make any sense ^^
Just remember : if you reboot your pfSense you have to start the kea-ddns process manually. The config files aren't touched by pfSense.edit : instead of editing 'system files' as suggested in the thread mentioned, you can now use :
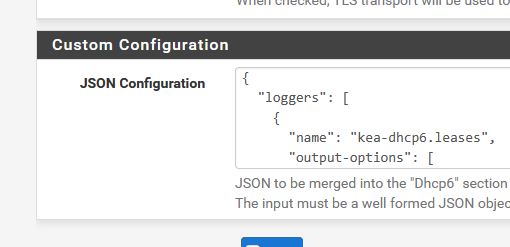
to add the needed dhcp(v6) extra config settings.
-
@Gertjan Thank you. I see KEA is in implementing process yet. I miss the custom DHCP options that would be very helpful. I could do it hard-coded in the config generation script, but I'm sure it will be available in GUI soon enough.
On the DDNS, I actually was looking for Windows AD DNS update, but it seems it lacks of a way to set custom authentication keys or ACLs to permit specific non secure updates, and I cannot change it to accept insecure updates globally, of course. So I'll keep the DDNS on hold for now.