PC Engines apu2 experiences
-
It should be no problem at 20Mbps.

2.5 is still a way out.Steve
-
and who knows, maybe by the time 2.5 comes along, they will have backed off this pointless aes-ni requirement and won't force retirement of working hardware.
-
While I wish they didn't implement it to be mandatory until the next major revision (and maybe 2.5 is a major revision, idk), I really don't see much of a problem. They gave us something like 2 years notice and 2.4 will be supported for at least a year after 2.5 is released which is likely still some months away as FreeBSD12 isn't even out yet. By that time most of us will have more old equipment that supports aes-ni laying around. For my company it means having to spend about another $1,500 in hardware to replace 6 more devices with APU2s but that's a small price compared to purchasing the alternatives.
I do feel bad for people who paid money for devices specifically for pfSense, like the APU1 series, only to find it will be retired 3 years later but the 2.4 line will still work in the them without issue forever. You still get 5 years of supported service life out of the equipment. The other big name firewalls we use are SonicWall and they don't offer anything beyond the 5 year mark, either.
I don't know what precipitated the requirement but I appreciate the big heads up. I hope it's for more than VPN traffic and it is somehow used foundationally to further enhance security. I also hope it clears up the confusion as to what the aes-ni settings should be to get the best performance out of our boxes. I guess we'll see once it launches.
-
@stewart said in PC Engines apu2 experiences:
While I wish they didn't implement it to be mandatory until the next major revision (and maybe 2.5 is a major revision, idk), I really don't see much of a problem. They gave us something like 2 years notice and 2.4 will be supported for at least a year after 2.5 is released which is likely still some months away as FreeBSD12 isn't even out yet. By that time most of us will have more old equipment that supports aes-ni laying around. For my company it means having to spend about another $1,500 in hardware to replace 6 more devices with APU2s but that's a small price compared to purchasing the alternatives.
That would all be reasonable--if there were a compelling reason to force the obsolescence. Since there isn't, it's just obnoxious.
I don't know what precipitated the requirement but I appreciate the big heads up.
As far as I can tell, poking the china box vendors in the eye was what precipitated the requirement.
I hope it's for more than VPN traffic and it is somehow used foundationally to further enhance security. I also hope it clears up the confusion as to what the aes-ni settings should be to get the best performance out of our boxes. I guess we'll see once it launches.
You leave the settings alone; the confusion is mostly people who don't know what they're doing repeating things they've read on reddit that were written by other people who don't know what they're doing. I would not be at all surprised if there are people pushing "tricks" to "speed up" crypto by doing idiotic things to override the defaults long after 2.5 is released.
-
@vamike said in PC Engines apu2 experiences:
You leave the settings alone; the confusion is mostly people who don't know what they're doing repeating things they've read on reddit that were written by other people who don't know what they're doing. I would not be at all surprised if there are people pushing "tricks" to "speed up" crypto by doing idiotic things to override the defaults long after 2.5 is released.
Maybe that's the way it is now but it's hasn't always been clear. At one time there was a lot of discussion as to what to set where as the results were all over the place depending on the hardware you had. Right now, do you select hardware or software decryption? Or none at all? It all depends on your hardware and which encrypting you are doing.
-
@stewart said in PC Engines apu2 experiences:
@vamike said in PC Engines apu2 experiences:
You leave the settings alone; the confusion is mostly people who don't know what they're doing repeating things they've read on reddit that were written by other people who don't know what they're doing. I would not be at all surprised if there are people pushing "tricks" to "speed up" crypto by doing idiotic things to override the defaults long after 2.5 is released.
Maybe that's the way it is now but it's hasn't always been clear. At one time there was a lot of discussion as to what to set where as the results were all over the place depending on the hardware you had. Right now, do you select hardware or software decryption? Or none at all? It all depends on your hardware and which encrypting you are doing.
It's been pretty clear except for people posting misunderstood and misleading openssl benchmark results and shooting themselves in the foot. The discussions mostly revolved around fanciful numbers in which screwing up the config would magically make a system do crypto even faster than it could access memory. Just leave it alone has been the correct action for a long time.
-
Mmm, that sslspeed thread was.... um...wild!
The default settings should work well for most. Some tuning can help. The asynchronous-crypto setting in 2.4.4 can dramatically increase ipsec throughput in some situations but can also break it in some edge cases so it not enabled by default in CE.
Steve
-
PC Engines / 3mdeb have released a new legacy coreboot BIOS v4.0.23.
Interestingly the release notes (https://pcengines.github.io/#lr-15) note that ECC is enabled with this release.
So on my test APU2 apu2c4 I've updated the BIOS from v4.0.7 to v4.0.23. All working well although only storage in use is a 32GB mSATA card.
Unfortunately command
dmidecode -t 17(this should dump memory config) does not work with coreboot - so it is not easy to verify to determine if ECC is actually working. Just have to wait for some cosmic rays or something ... -
@dugeem Thanks for sharing the result, I just upgraded from v4.0.18 to v4.0.23, all went well (for now ;) )
-
PC Engines / 3mdeb have released another new legacy coreboot BIOS v4.0.24.
The release notes (https://pcengines.github.io/#lr-16) note that CPB is now enabled with this release. CPB = Core Performance Boost ... the AMD equivalent of Intel Turbo Boost.
On my test pfSense system (2.4.4-RELEASE-p2) I'm seeing a useful 5-10% improvement in single core task performance.
Example using openssl:
openssl speed -elapsed -evp aes-128-gcm ... type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes aes-128-gcm 52651.25k 134318.72k 296380.07k 408489.98k 482383.19kPowerD is enabled in adaptive mode. No significant change in CPU temperature was observed.
/boot/loader.conf.local
#hw.acpi.cpu.cx_lowest=C2
hw.igb.rx_process_limit=-1Kudos to PC Engines & 3mdeb for these continuing BIOS improvements.
Edit: the hints hint.p4tcc.0.disabled & hint.acpi_throttle.0.disabled in loader.conf.local are no longer required as they are now defaults in /boot/device.hints
Edit2: hw.acpi.cpu.cx_lowest=C2 does not apply from loader.conf.local -
I am on Bios v4.0.24 also.
edit: noticed that CPU temperature dropped. Normally it was around 54c now it's around 47c.
-
i must upgrade my APU, but i would like to know why we can not use Mainline releases...
-
@keen said in PC Engines apu2 experiences:
i must upgrade my APU, but i would like to know why we can not use Mainline releases...
I use mainline, no problems here.
I’m on 4.9.0.2 currently.
-
Please read this
http://www.pcengines.info/forums/?page=post&id=6D2EEC40-5928-463B-8BAE-7C74A46B2060&fid=DF5ACB70-99C4-4C61-AFA6-4C0E0DB05B2ACheers Qinn
https://pcengines.github.io/#mr-19
-
@veldkornet said in PC Engines apu2 experiences:
@keen said in PC Engines apu2 experiences:
i must upgrade my APU, but i would like to know why we can not use Mainline releases...
I use mainline, no problems here.
I’m on 4.9.0.2 currently.
@veldkornet Do you use mSATA disk?
-
@qinn Yes, I have a Samsung SSD 850 EVO mSATA 250GB.
-
@veldkornet Thanks and good to know as the table on site mentioned, not tested.

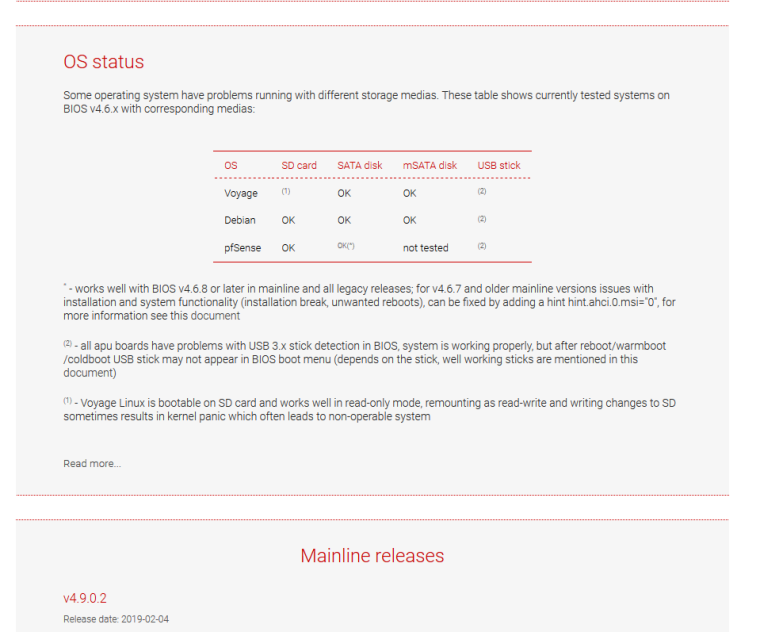
-
For another quick comparison I updated my test APU2C4 to mainline v4.9.0.2. Quick & dirty performance testing showed gain for light loads was similar to legacy v4.0.24 (at least within a few percent).
I also compared full multi core performance on both versions and had similar results (again within a few percent).
@Qinn FYI I'm also running mSata SSDs in both my test and live systems.
-
@dugeem said in PC Engines apu2 experiences:
For another quick comparison I updated my test APU2C4 to mainline v4.9.0.2. Quick & dirty performance testing showed gain for light loads was similar to legacy v4.0.24 (at least within a few percent).
I also compared full multi core performance on both versions and had similar results (again within a few percent).
@Qinn FYI I'm also running mSata SSDs in both my test and live systems.
Thanks for confirming. Btw how do you install the bios, I boot into a USB stick with has tinycore and then flashrom?
-
@qinn SSH into it and install flashrom. No need to boot from USB etc.
pkg install flashrom
Upload the firmware to /tmp with scp and run:
flashrom -w /tmp/apu2_v4.9.0.2.rom -p internal:boardmismatch=forceShutdown pfSense, pull the power for 10 seconds, then boot up.