Squid and c-icap does not work PFsense 2.3
-
Hi everyone, i need help here with squid.
everything was working fine with squid and HAVP
Since i upgrade to 2.3 squid and C-iCAP doesnt work.I don't know what i've done wrong but if i tick "Allow Users on Interface " in squid config then i cant access any thing, although squid and everything is running.
I tried to download test virus http://www.eicar.org/download/eicar.com.txt but it wont work as it was on HAVP in older version.
Also none of the ads blocked with squidgards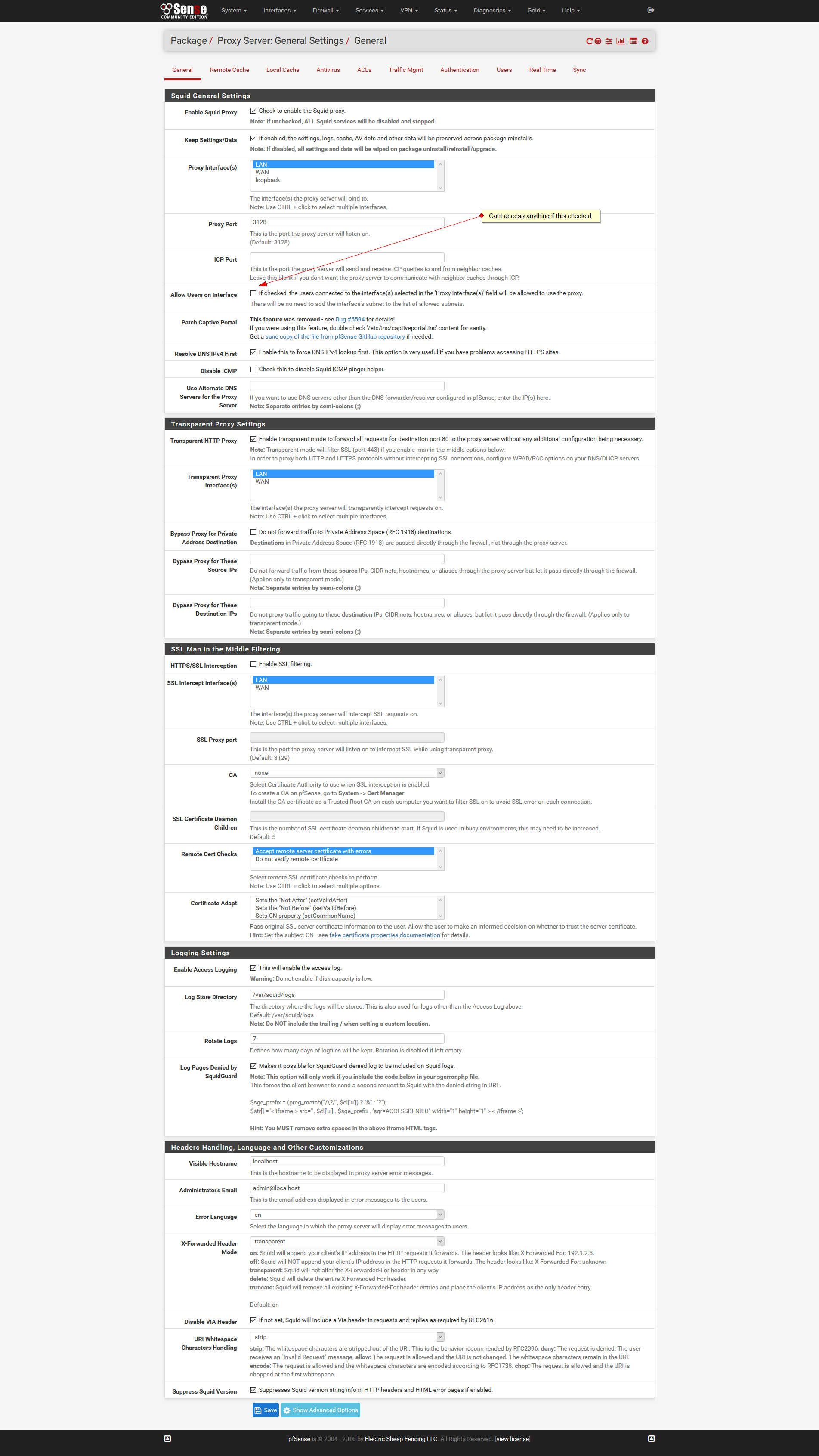
Please check my screen shots and give me your advice.
http://easycaptures.com/fs/uploaded/932/7681022914.png
http://easycaptures.com/fs/uploaded/932/0913961144.png
http://easycaptures.com/fs/uploaded/932/8972112036.png
http://easycaptures.com/fs/uploaded/932/8827296471.png
Thanks everyone -
Hi,
same here.
I use squid in transparent mode. everything with default settings, but I can download the Eicar test file over HTTP.
Seems that this is not working correctly.
squid.conf
This file is automatically generated by pfSense
Do not edit manually !
http_port 192.168.5.1:3128
http_port 192.168.7.1:3128
http_port 127.0.0.1:3128 intercept
icp_port 0
dns_v4_first on
pid_filename /var/run/squid/squid.pid
cache_effective_user squid
cache_effective_group proxy
error_default_language de
icon_directory /usr/local/etc/squid/icons
visible_hostname tohil1.pfsensefirewall.local
cache_mgr angelo@tohil.net
access_log /var/squid/logs/access.log
cache_log /var/squid/logs/cache.log
cache_store_log none
netdb_filename /var/squid/logs/netdb.state
pinger_enable off
pinger_program /usr/local/libexec/squid/pingerlogfile_rotate 1
debug_options rotate=1
shutdown_lifetime 3 secondsAllow local network(s) on interface(s)
acl localnet src 192.168.5.0/24 192.168.7.0/24
forwarded_for on
uri_whitespace stripacl dynamic urlpath_regex cgi-bin ?
cache deny dynamiccache_mem 64 MB
maximum_object_size_in_memory 256 KB
memory_replacement_policy heap GDSF
cache_replacement_policy heap LFUDA
minimum_object_size 0 KB
maximum_object_size 4 MB
cache_dir ufs /var/squid/cache 100 16 256
offline_mode off
cache_swap_low 90
cache_swap_high 95
cache allow allAdd any of your own refresh_pattern entries above these.
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|?) 0 0% 0
refresh_pattern . 0 20% 4320#Remote proxies
Setup some default acls
From 3.2 further configuration cleanups have been done to make things easier and safer. The manager, localhost, and to_localhost ACL definitions are now built-in.
acl localhost src 127.0.0.1/32
acl allsrc src all
acl safeports port 21 70 80 210 280 443 488 563 591 631 777 901 10443 3128 3129 1025-65535
acl sslports port 443 563 10443From 3.2 further configuration cleanups have been done to make things easier and safer. The manager, localhost, and to_localhost ACL definitions are now built-in.
#acl manager proto cache_object
acl purge method PURGE
acl connect method CONNECTDefine protocols used for redirects
acl HTTP proto HTTP
acl HTTPS proto HTTPS
http_access allow manager localhosthttp_access deny manager
http_access allow purge localhost
http_access deny purge
http_access deny !safeports
http_access deny CONNECT !sslportsAlways allow localhost connections
From 3.2 further configuration cleanups have been done to make things easier and safer.
The manager, localhost, and to_localhost ACL definitions are now built-in.
http_access allow localhost
request_body_max_size 0 KB
delay_pools 1
delay_class 1 2
delay_parameters 1 -1/-1 -1/-1
delay_initial_bucket_level 100
delay_access 1 allow allsrcReverse Proxy settings
Custom options before auth
Setup allowed ACLs
Allow local network(s) on interface(s)
http_access allow localnet
Default block all to be sure
http_access deny allsrc
icap_enable on
icap_send_client_ip on
icap_send_client_username off
icap_client_username_encode off
icap_client_username_header X-Authenticated-User
icap_preview_enable on
icap_preview_size 1024icap_service service_avi_req reqmod_precache icap://127.0.0.1:1344/squid_clamav bypass=off
adaptation_access service_avi_req allow all
icap_service service_avi_resp respmod_precache icap://127.0.0.1:1344/squid_clamav bypass=on
adaptation_access service_avi_resp allow allclamd.conf
#This file was automatically generated by pfSense WebGUI configuration
Please read the clamd.conf(5) manual before editing this file.
Uncomment this option to enable logging.
LogFile must be writable for the user running daemon.
A full path is required.
Default: disabled
LogFile /var/log/clamav/clamd.log
By default the log file is locked for writing - the lock protects against
running clamd multiple times (if want to run another clamd, please
copy the configuration file, change the LogFile variable, and run
the daemon with –config-file option).
This option disables log file locking.
Default: no
#LogFileUnlock yes
Maximum size of the log file.
Value of 0 disables the limit.
You may use 'M' or 'm' for megabytes (1M = 1m = 1048576 bytes)
and 'K' or 'k' for kilobytes (1K = 1k = 1024 bytes). To specify the size
in bytes just don't use modifiers. If LogFileMaxSize is enabled, log
rotation (the LogRotate option) will always be enabled.
Default: 1M
#LogFileMaxSize 2M
Log time with each message.
Default: no
#LogTime yes
Also log clean files. Useful in debugging but drastically increases the
log size.
Default: no
#LogClean yes
Use system logger (can work together with LogFile).
Default: no
#LogSyslog yes
Specify the type of syslog messages - please refer to 'man syslog'
for facility names.
Default: LOG_LOCAL6
#LogFacility LOG_MAIL
Enable verbose logging.
Default: no
#LogVerbose yes
Enable log rotation. Always enabled when LogFileMaxSize is enabled.
Default: no
#LogRotate yes
Log additional information about the infected file, such as its
size and hash, together with the virus name.
#ExtendedDetectionInfo yes
This option allows you to save a process identifier of the listening
daemon (main thread).
Default: disabled
PidFile /var/run/clamav/clamd.pid
Optional path to the global temporary directory.
Default: system specific (usually /tmp or /var/tmp).
#TemporaryDirectory /var/tmp
Path to the database directory.
Default: hardcoded (depends on installation options)
DatabaseDirectory /var/db/clamav
Only load the official signatures published by the ClamAV project.
Default: no
#OfficialDatabaseOnly no
The daemon can work in local mode, network mode or both.
Due to security reasons we recommend the local mode.
Path to a local socket file the daemon will listen on.
Default: disabled (must be specified by a user)
LocalSocket /var/run/clamav/clamd.sock
Sets the group ownership on the unix socket.
Default: disabled (the primary group of the user running clamd)
#LocalSocketGroup virusgroup
Sets the permissions on the unix socket to the specified mode.
Default: disabled (socket is world accessible)
#LocalSocketMode 660
Remove stale socket after unclean shutdown.
Default: yes
FixStaleSocket yes
TCP port address.
Default: no
#TCPSocket 3310
TCP address.
By default we bind to INADDR_ANY, probably not wise.
Enable the following to provide some degree of protection
from the outside world. This option can be specified multiple
times if you want to listen on multiple IPs. IPv6 is now supported.
Default: no
#TCPAddr 127.0.0.1
Maximum length the queue of pending connections may grow to.
Default: 200
#MaxConnectionQueueLength 30
Clamd uses FTP-like protocol to receive data from remote clients.
If you are using clamav-milter to balance load between remote clamd daemons
on firewall servers you may need to tune the options below.
Close the connection when the data size limit is exceeded.
The value should match your MTA's limit for a maximum attachment size.
Default: 25M
#StreamMaxLength 10M
Limit port range.
Default: 1024
#StreamMinPort 30000
Default: 2048
#StreamMaxPort 32000
Maximum number of threads running at the same time.
Default: 10
#MaxThreads 20
Waiting for data from a client socket will timeout after this time (seconds).
Default: 120
#ReadTimeout 300
This option specifies the time (in seconds) after which clamd should
timeout if a client doesn't provide any initial command after connecting.
Default: 5
#CommandReadTimeout 5
This option specifies how long to wait (in miliseconds) if the send buffer is full.
Keep this value low to prevent clamd hanging
Default: 500
#SendBufTimeout 200
Maximum number of queued items (including those being processed by MaxThreads threads)
It is recommended to have this value at least twice MaxThreads if possible.
WARNING: you shouldn't increase this too much to avoid running out of file descriptors,
the following condition should hold:
MaxThreads*MaxRecursion + (MaxQueue - MaxThreads) + 6< RLIMIT_NOFILE (usual max is 1024)
Default: 100
#MaxQueue 200
Waiting for a new job will timeout after this time (seconds).
Default: 30
#IdleTimeout 60
Don't scan files and directories matching regex
This directive can be used multiple times
Default: scan all
#ExcludePath ^/proc/
#ExcludePath ^/sys/Maximum depth directories are scanned at.
Default: 15
#MaxDirectoryRecursion 20
Follow directory symlinks.
Default: no
#FollowDirectorySymlinks yes
Follow regular file symlinks.
Default: no
#FollowFileSymlinks yes
Scan files and directories on other filesystems.
Default: yes
#CrossFilesystems yes
Perform a database check.
Default: 600 (10 min)
#SelfCheck 600
Execute a command when virus is found. In the command string %v will
be replaced with the virus name.
Default: no
#VirusEvent /usr/local/bin/send_sms 123456789 "VIRUS ALERT: %v"
Run as another user (clamd must be started by root for this option to work)
Default: don't drop privileges
User clamav
Initialize supplementary group access (clamd must be started by root).
Default: no
AllowSupplementaryGroups yes
Stop daemon when libclamav reports out of memory condition.
#ExitOnOOM yes
Don't fork into background.
Default: no
#Foreground yes
Enable debug messages in libclamav.
Default: no
#Debug yes
Do not remove temporary files (for debug purposes).
Default: no
#LeaveTemporaryFiles yes
Permit use of the ALLMATCHSCAN command. If set to no, clamd will reject
any ALLMATCHSCAN command as invalid.
Default: yes
#AllowAllMatchScan no
Detect Possibly Unwanted Applications.
Default: no
#DetectPUA yes
Exclude a specific PUA category. This directive can be used multiple times.
See https://github.com/vrtadmin/clamav-faq/blob/master/faq/faq-pua.md for
the complete list of PUA categories.
Default: Load all categories (if DetectPUA is activated)
#ExcludePUA NetTool
#ExcludePUA PWToolOnly include a specific PUA category. This directive can be used multiple
times.
Default: Load all categories (if DetectPUA is activated)
#IncludePUA Spy
#IncludePUA Scanner
#IncludePUA RATIn some cases (eg. complex malware, exploits in graphic files, and others),
ClamAV uses special algorithms to provide accurate detection. This option
controls the algorithmic detection.
Default: yes
#AlgorithmicDetection yes
This option causes memory or nested map scans to dump the content to disk.
If you turn on this option, more data is written to disk and is available
when the LeaveTemporaryFiles option is enabled.
#ForceToDisk yes
This option allows you to disable the caching feature of the engine. By
default, the engine will store an MD5 in a cache of any files that are
not flagged as virus or that hit limits checks. Disabling the cache will
have a negative performance impact on large scans.
Default: no
#DisableCache yes
Executable files
PE stands for Portable Executable - it's an executable file format used
in all 32 and 64-bit versions of Windows operating systems. This option allows
ClamAV to perform a deeper analysis of executable files and it's also
required for decompression of popular executable packers such as UPX, FSG,
and Petite. If you turn off this option, the original files will still be
scanned, but without additional processing.
Default: yes
#ScanPE yes
Certain PE files contain an authenticode signature. By default, we check
the signature chain in the PE file against a database of trusted and
revoked certificates if the file being scanned is marked as a virus.
If any certificate in the chain validates against any trusted root, but
does not match any revoked certificate, the file is marked as whitelisted.
If the file does match a revoked certificate, the file is marked as virus.
The following setting completely turns off authenticode verification.
Default: no
#DisableCertCheck yes
Executable and Linking Format is a standard format for UN*X executables.
This option allows you to control the scanning of ELF files.
If you turn off this option, the original files will still be scanned, but
without additional processing.
Default: yes
#ScanELF yes
With this option clamav will try to detect broken executables (both PE and
ELF) and mark them as Broken.Executable.
Default: no
#DetectBrokenExecutables yes
Documents
This option enables scanning of OLE2 files, such as Microsoft Office
documents and .msi files.
If you turn off this option, the original files will still be scanned, but
without additional processing.
Default: yes
#ScanOLE2 yes
With this option enabled OLE2 files with VBA macros, which were not
detected by signatures will be marked as "Heuristics.OLE2.ContainsMacros".
Default: no
#OLE2BlockMacros no
This option enables scanning within PDF files.
If you turn off this option, the original files will still be scanned, but
without decoding and additional processing.
Default: yes
#ScanPDF yes
This option enables scanning within SWF files.
If you turn off this option, the original files will still be scanned, but
without decoding and additional processing.
Default: yes
#ScanSWF yes
This option enables scanning xml-based document files supported by libclamav.
If you turn off this option, the original files will still be scanned, but
without additional processing.
Default: yes
#ScanXMLDOCS yes
This option enables scanning of HWP3 files.
If you turn off this option, the original files will still be scanned, but
without additional processing.
Default: yes
#ScanHWP3 yes
Mail files
Enable internal e-mail scanner.
If you turn off this option, the original files will still be scanned, but
without parsing individual messages/attachments.
Default: yes
ScanMail yes
Scan RFC1341 messages split over many emails.
You will need to periodically clean up $TemporaryDirectory/clamav-partial directory.
WARNING: This option may open your system to a DoS attack.
Never use it on loaded servers.
Default: no
#ScanPartialMessages yes
With this option enabled ClamAV will try to detect phishing attempts by using
signatures.
Default: yes
#PhishingSignatures yes
Scan URLs found in mails for phishing attempts using heuristics.
Default: yes
#PhishingScanURLs yes
Always block SSL mismatches in URLs, even if the URL isn't in the database.
This can lead to false positives.
Default: no
#PhishingAlwaysBlockSSLMismatch no
Always block cloaked URLs, even if URL isn't in database.
This can lead to false positives.
Default: no
#PhishingAlwaysBlockCloak no
Detect partition intersections in raw disk images using heuristics.
Default: no
#PartitionIntersection no
Allow heuristic match to take precedence.
When enabled, if a heuristic scan (such as phishingScan) detects
a possible virus/phish it will stop scan immediately. Recommended, saves CPU
scan-time.
When disabled, virus/phish detected by heuristic scans will be reported only at
the end of a scan. If an archive contains both a heuristically detected
virus/phish, and a real malware, the real malware will be reported
Keep this disabled if you intend to handle ".Heuristics." viruses
differently from "real" malware.
If a non-heuristically-detected virus (signature-based) is found first,
the scan is interrupted immediately, regardless of this config option.
Default: no
#HeuristicScanPrecedence yes
Data Loss Prevention (DLP)
Enable the DLP module
Default: No
#StructuredDataDetection yes
This option sets the lowest number of Credit Card numbers found in a file
to generate a detect.
Default: 3
#StructuredMinCreditCardCount 5
This option sets the lowest number of Social Security Numbers found
in a file to generate a detect.
Default: 3
#StructuredMinSSNCount 5
With this option enabled the DLP module will search for valid
SSNs formatted as xxx-yy-zzzz
Default: yes
#StructuredSSNFormatNormal yes
With this option enabled the DLP module will search for valid
SSNs formatted as xxxyyzzzz
Default: no
#StructuredSSNFormatStripped yes
HTML
Perform HTML normalisation and decryption of MS Script Encoder code.
Default: yes
If you turn off this option, the original files will still be scanned, but
without additional processing.
#ScanHTML yes
Archives
ClamAV can scan within archives and compressed files.
If you turn off this option, the original files will still be scanned, but
without unpacking and additional processing.
Default: yes
#ScanArchive yes
Mark encrypted archives as viruses (Encrypted.Zip, Encrypted.RAR).
Default: no
#ArchiveBlockEncrypted no
Limits
The options below protect your system against Denial of Service attacks
using archive bombs.
This option sets the maximum amount of data to be scanned for each input file.
Archives and other containers are recursively extracted and scanned up to this
value.
Value of 0 disables the limit
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 100M
#MaxScanSize 150M
Files larger than this limit won't be scanned. Affects the input file itself
as well as files contained inside it (when the input file is an archive, a
document or some other kind of container).
Value of 0 disables the limit.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 25M
#MaxFileSize 30M
Nested archives are scanned recursively, e.g. if a Zip archive contains a RAR
file, all files within it will also be scanned. This options specifies how
deeply the process should be continued.
Note: setting this limit too high may result in severe damage to the system.
Default: 16
#MaxRecursion 10
Number of files to be scanned within an archive, a document, or any other
container file.
Value of 0 disables the limit.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 10000
#MaxFiles 15000
Maximum size of a file to check for embedded PE. Files larger than this value
will skip the additional analysis step.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 10M
#MaxEmbeddedPE 10M
Maximum size of a HTML file to normalize. HTML files larger than this value
will not be normalized or scanned.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 10M
#MaxHTMLNormalize 10M
Maximum size of a normalized HTML file to scan. HTML files larger than this
value after normalization will not be scanned.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 2M
#MaxHTMLNoTags 2M
Maximum size of a script file to normalize. Script content larger than this
value will not be normalized or scanned.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 5M
#MaxScriptNormalize 5M
Maximum size of a ZIP file to reanalyze type recognition. ZIP files larger
than this value will skip the step to potentially reanalyze as PE.
Note: disabling this limit or setting it too high may result in severe damage
to the system.
Default: 1M
#MaxZipTypeRcg 1M
This option sets the maximum number of partitions of a raw disk image to be scanned.
Raw disk images with more partitions than this value will have up to the value number
partitions scanned. Negative values are not allowed.
Note: setting this limit too high may result in severe damage or impact performance.
Default: 50
#MaxPartitions 128
This option sets the maximum number of icons within a PE to be scanned.
PE files with more icons than this value will have up to the value number icons scanned.
Negative values are not allowed.
WARNING: setting this limit too high may result in severe damage or impact performance.
Default: 100
#MaxIconsPE 200
This option sets the maximum recursive calls for HWP3 parsing during scanning.
HWP3 files using more than this limit will be terminated and alert the user.
Scans will be unable to scan any HWP3 attachments if the recursive limit is reached.
Negative values are not allowed.
WARNING: setting this limit too high may result in severe damage or impact performance.
Default: 16
#MaxRecHWP3 16
This option sets the maximum calls to the PCRE match function during an instance of regex matching.
Instances using more than this limit will be terminated and alert the user but the scan will continue.
For more information on match_limit, see the PCRE documentation.
Negative values are not allowed.
WARNING: setting this limit too high may severely impact performance.
Default: 10000
#PCREMatchLimit 20000
This option sets the maximum recursive calls to the PCRE match function during an instance of regex matching.
Instances using more than this limit will be terminated and alert the user but the scan will continue.
For more information on match_limit_recursion, see the PCRE documentation.
Negative values are not allowed and values > PCREMatchLimit are superfluous.
WARNING: setting this limit too high may severely impact performance.
Default: 5000
#PCRERecMatchLimit 10000
This option sets the maximum filesize for which PCRE subsigs will be executed.
Files exceeding this limit will not have PCRE subsigs executed unless a subsig is encompassed to a smaller buffer.
Negative values are not allowed.
Setting this value to zero disables the limit.
WARNING: setting this limit too high or disabling it may severely impact performance.
Default: 25M
#PCREMaxFileSize 100M
On-access Scan Settings
Enable on-access scanning. Currently, this is supported via fanotify.
Clamuko/Dazuko support has been deprecated.
Default: no
#ScanOnAccess yes
Set the mount point to be scanned. The mount point specified, or the mount point
containing the specified directory will be watched. If any directories are specified,
this option will preempt the DDD system. This will notify only. It can be used multiple times.
(On-access scan only)
Default: disabled
#OnAccessMountPath /
#OnAccessMountPath /home/userDon't scan files larger than OnAccessMaxFileSize
Value of 0 disables the limit.
Default: 5M
#OnAccessMaxFileSize 10M
Set the include paths (all files inside them will be scanned). You can have
multiple OnAccessIncludePath directives but each directory must be added
in a separate line. (On-access scan only)
Default: disabled
#OnAccessIncludePath /home
#OnAccessIncludePath /studentsSet the exclude paths. All subdirectories are also excluded.
(On-access scan only)
Default: disabled
#OnAccessExcludePath /home/bofh
With this option you can whitelist specific UIDs. Processes with these UIDs
will be able to access all files.
This option can be used multiple times (one per line).
Default: disabled
#OnAccessExcludeUID 0
Toggles dynamic directory determination. Allows for recursively watching include paths.
(On-access scan only)
Default: no
#OnAccessDisableDDD yes
Modifies fanotify blocking behaviour when handling permission events.
If off, fanotify will only notify if the file scanned is a virus,
and not perform any blocking.
(On-access scan only)
Default: no
#OnAccessPrevention yes
Toggles extra scanning and notifications when a file or directory is created or moved.
Requires the DDD system to kick-off extra scans.
(On-access scan only)
Default: no
#OnAccessExtraScanning yes
Bytecode
With this option enabled ClamAV will load bytecode from the database.
It is highly recommended you keep this option on, otherwise you'll miss detections for many new viruses.
Default: yes
#Bytecode yes
Set bytecode security level.
Possible values:
# None - no security at all, meant for debugging. DO NOT USE THIS ON PRODUCTION SYSTEMS
# This value is only available if clamav was built with --enable-debug!
# TrustSigned - trust bytecode loaded from signed .c[lv]d files,
# insert runtime safety checks for bytecode loaded from other sources
# Paranoid - don't trust any bytecode, insert runtime checks for allRecommended: TrustSigned, because bytecode in .cvd files already has these checks
Note that by default only signed bytecode is loaded, currently you can only
load unsigned bytecode in –enable-debug mode.
Default: TrustSigned
#BytecodeSecurity TrustSigned
Set bytecode timeout in miliseconds.
Default: 5000
BytecodeTimeout 1000
Statistics gathering and submitting
Enable statistical reporting.
Default: no
#StatsEnabled yes
Disable submission of individual PE sections for files flagged as malware.
Default: no
#StatsPEDisabled yes
HostID in the form of an UUID to use when submitting statistical information.
Default: auto
#StatsHostID auto
Time in seconds to wait for the stats server to come back with a response
Default: 10
#StatsTimeout 10