@techpro2004 said in ssh wan block bug:
How do I figure out where the filter logs are from.
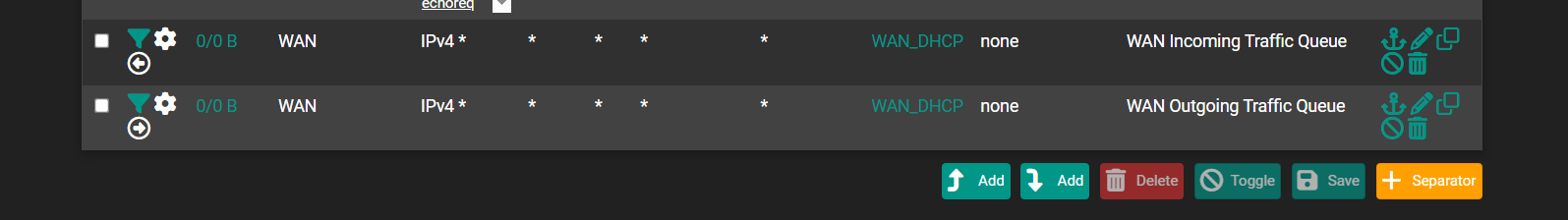
What do you mean its right there in the log who is sending the traffic.. For starters I would remove the bridge.. then you can filter on your interfaces where noise is coming in easier to not log it.
May 13 14:00:00 pfSense filterlog[7432]: 2,,,1000000101,ix0,match,block,in,4,0x0,,128,46560,0,none,17,udp,256,169.254.14.211,192.168.1.27,1900,60690,236
This is just pure noise.. You got something with APIPA address, ie didn't get a dhcp address? Sending SSDP to 192.168.1.27..
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,48715,0,DF,17,udp,863,192.168.1.4,239.255.255.251,37810,37810,843
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,34515,0,DF,17,udp,691,192.168.1.14,239.255.255.251,37810,37810,671
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,64642,0,DF,17,udp,691,192.168.1.16,239.255.255.251,37810,37810,671
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,9381,0,DF,17,udp,690,192.168.1.12,239.255.255.251,37810,37810,670
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,49402,0,DF,17,udp,691,192.168.1.18,239.255.255.251,37810,37810,671
May 13 14:00:00 pfSense filterlog[7432]: 4,,,1000000103,bridge0,match,block,in,4,0x0,,1,20481,0,DF,17,udp,818,192.168.1.6,239.255.255.251,37810,37810,798
Also pure noise.. Multicast Discovery of DNS Services is that multicast address - why would you need that noise logged or going over you wireguard connection?
 3
0 Votes7 Posts642 Views
3
0 Votes7 Posts642 Views