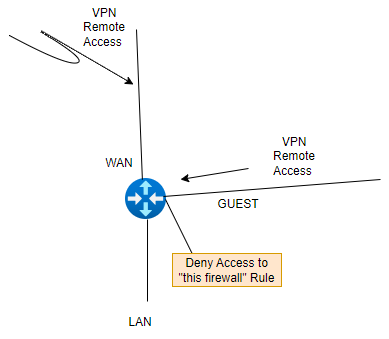
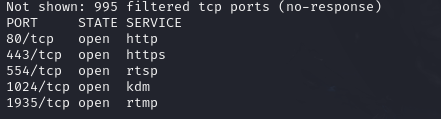
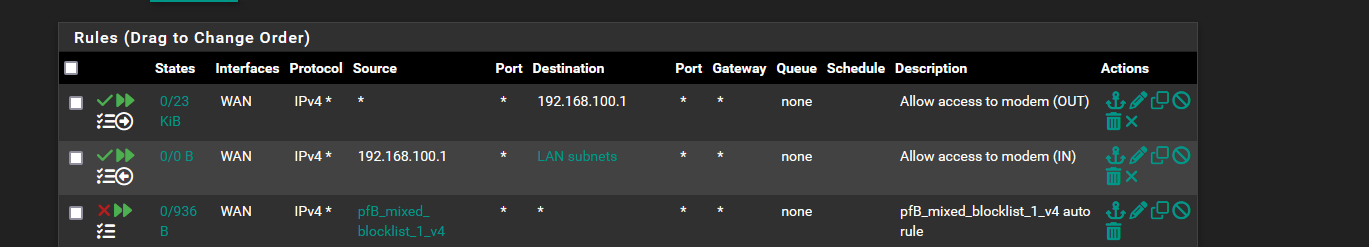
-
0 Votes4 Posts315 Views
-
0 Votes9 Posts893 Views
-
0 Votes8 Posts548 Views
-
0 Votes2 Posts199 Views
-
0 Votes7 Posts801 Views
-
0 Votes45 Posts5k Views
-
0 Votes4 Posts330 Views
-
0 Votes1 Posts224 Views
-
0 Votes11 Posts759 Views
-
0 Votes5 Posts399 Views
-
0 Votes9 Posts783 Views
-
0 Votes4 Posts428 Views
-
0 Votes18 Posts2k Views
-
0 Votes3 Posts474 Views
-
0 Votes4 Posts1k Views
-
0 Votes17 Posts1k Views
-
0 Votes5 Posts462 Views
-
0 Votes3 Posts290 Views
-
Bridging WAN + OPT1 for second WAN IP through ISP’s DHCP.
0 Votes2 Posts619 Views -
0 Votes8 Posts2k Views
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.