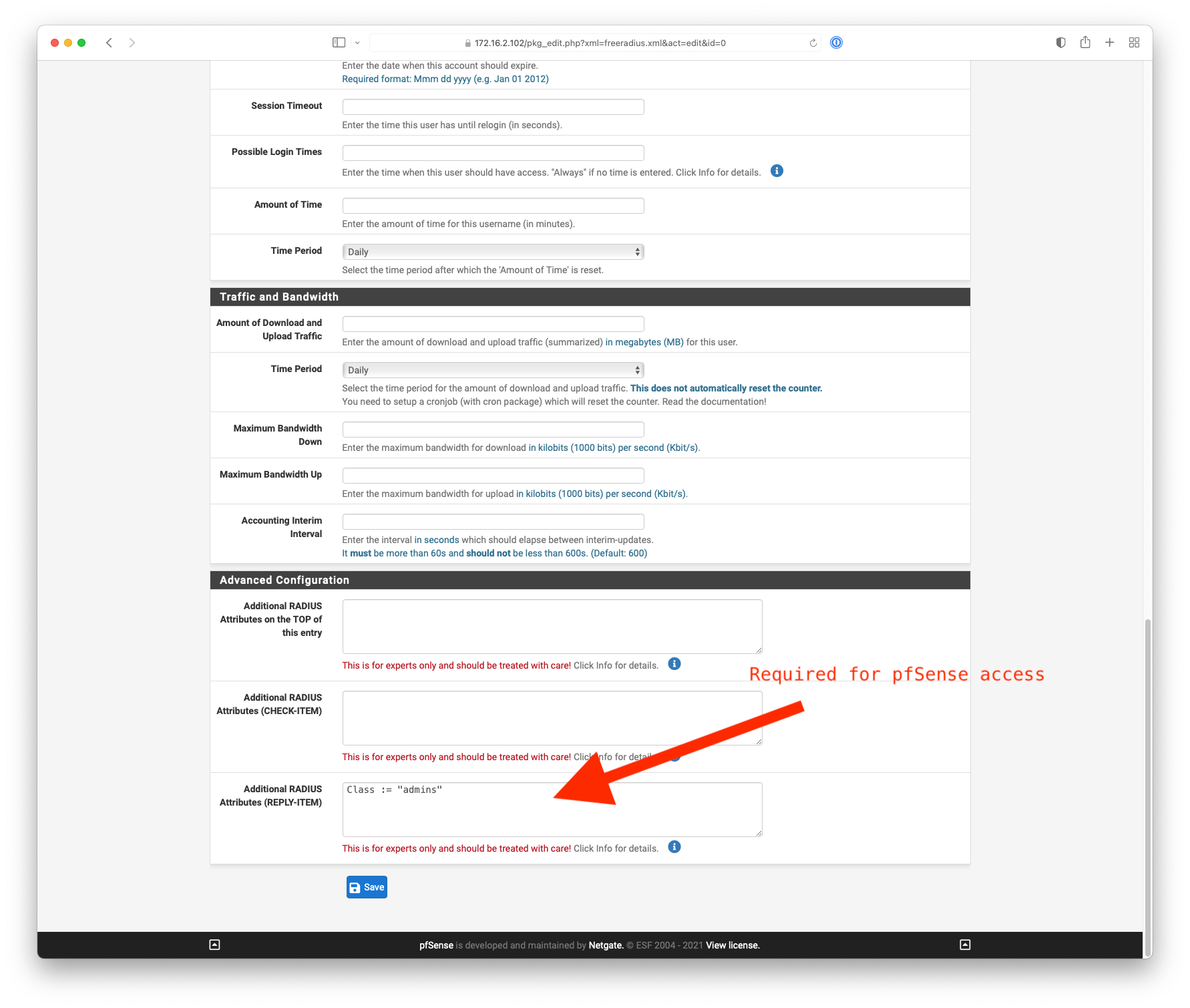
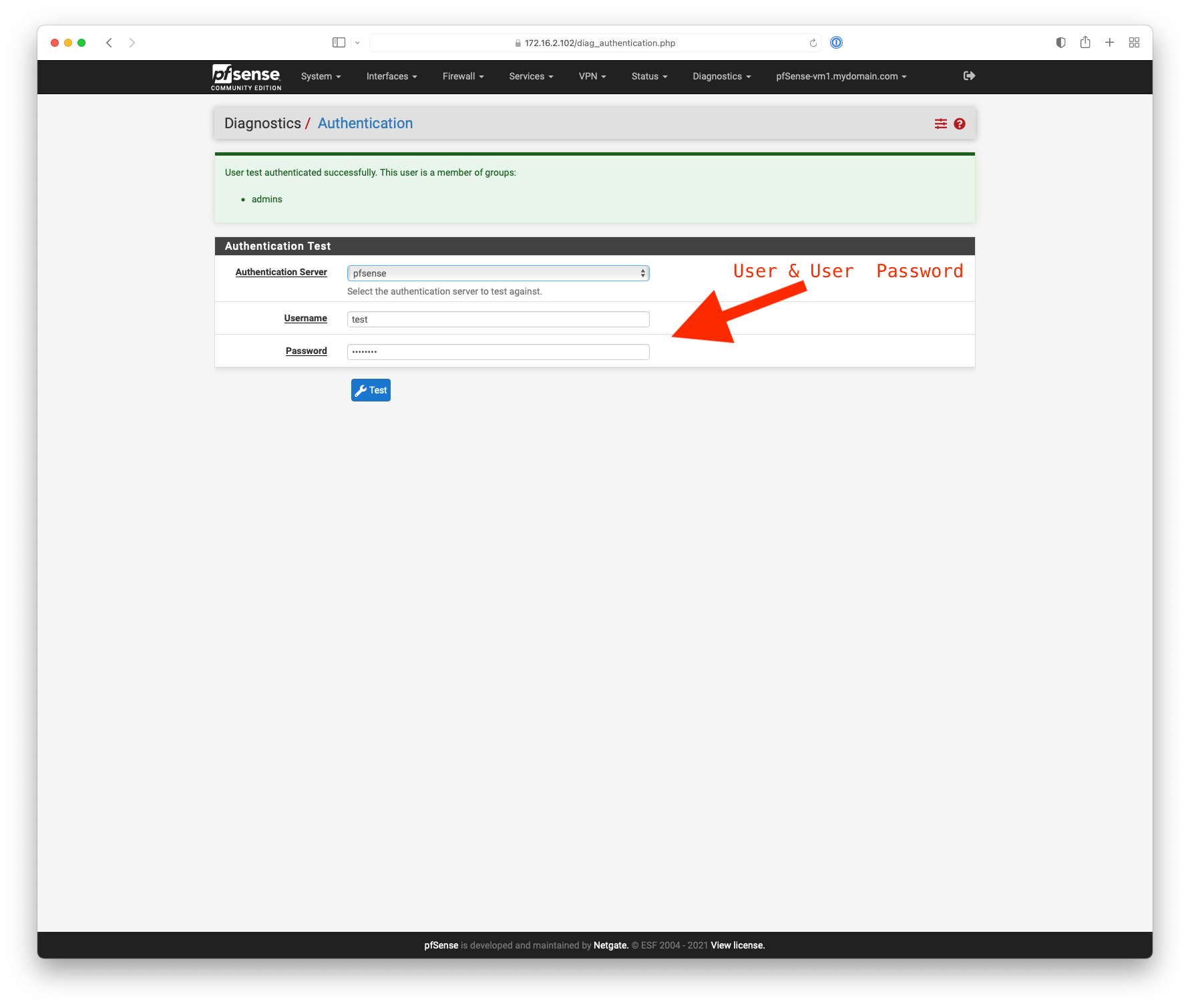
Setting up FreeRadius/OTP
-
I am following this tutorial: https://www.pfsensefirewall.com/2020/12/multi-factor-authentication-for-pfsense.html. Upon running the test (step 27), I am greeted with the following error message: The following input errors were detected:
Authentication failed.
It seems to time out after the defined 5 seconds. I noticed that if I use the 192. address instead of 127., it returns almost instantly. Should I be using 127.0.0.1? What could I have missed? Is there anything missing in the instructions so far? -
127.0.0.1 is whats known as a loopback address, if you ping any device 127.0.0.1 is its self.
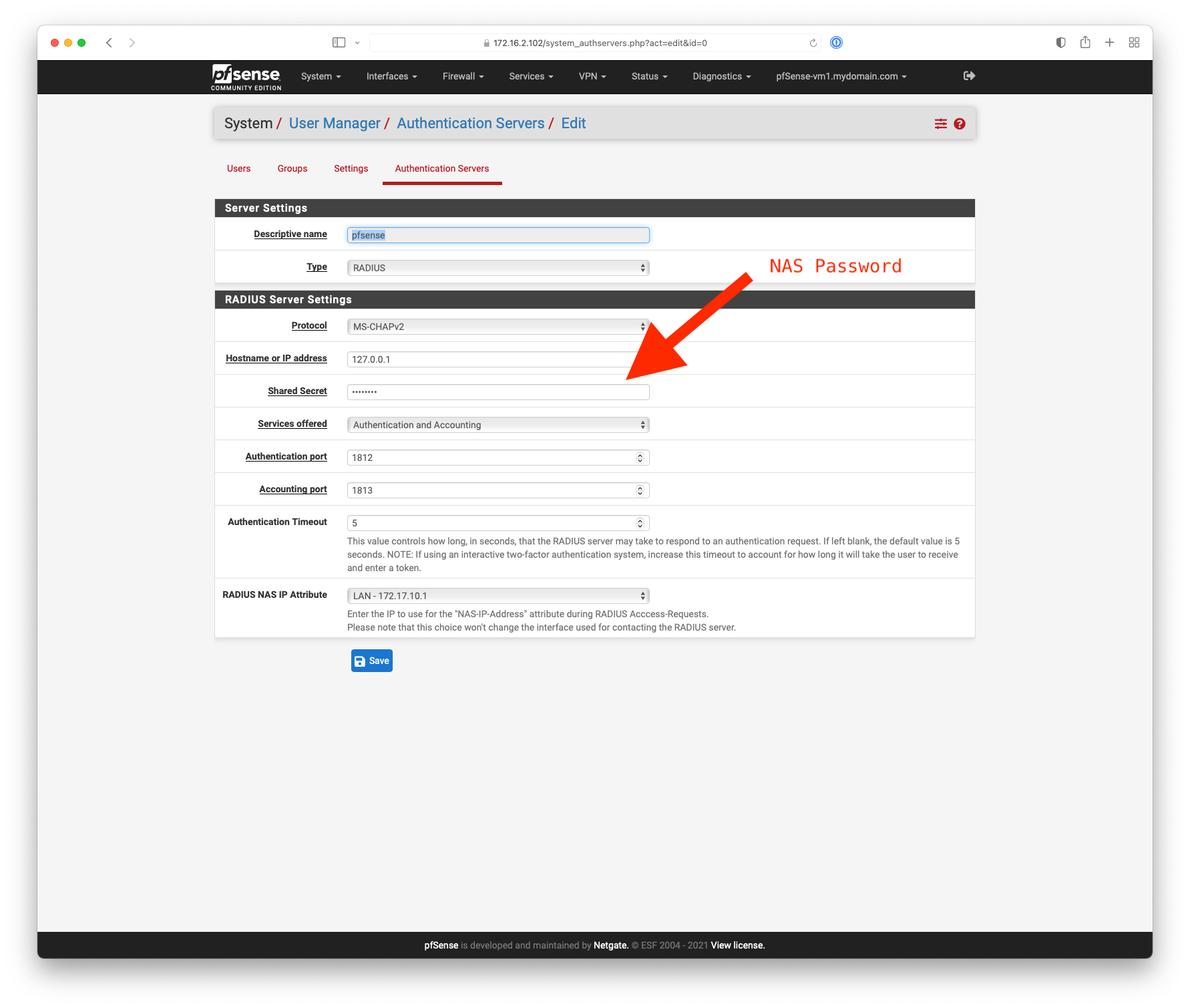
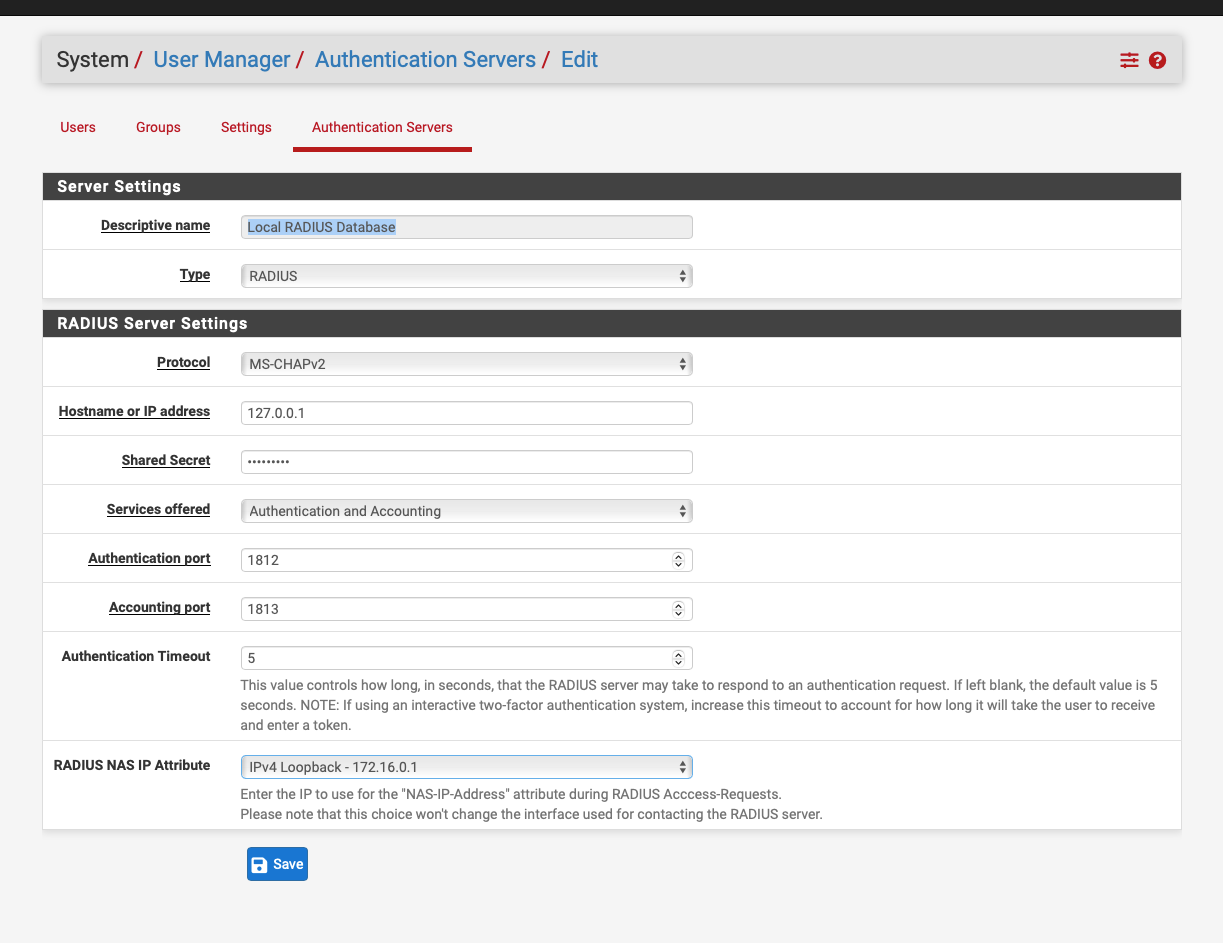
18. Under RADIUS Server Settings put "127.0.0.1" as the "Hostname or IP address"
Is that set to 127.0.0.1 ?
You could try running radfsniff -x from the cli and then try to auth.
21.05.1-RELEASE][admin@pfsense.xxxxxxxxxx.net]/root: radsniff -x Logging all events Defaulting to capture on all interfaces Sniffing on (igb0 pppoe0 igb1 ovpnc1 igb0.2 ovpnc2 igb0.3 ovpnc3 igb0.4 igb0.5 igb0.6 igb0.7 igb0.9 igb0.11 lo0 pflog0 igb5 igb2 igb3 igb4) 2021-09-24 20:27:25.919210 (1) Access-Request Id 23 lo0:127.0.0.1:23916 -> 127.0.0.1:1812 +0.000 User-Name = "xxxxx" NAS-IP-Address = 172.16.0.1 Service-Type = Login-User NAS-Identifier = "pfsense.xxxxxxxxxx.net" MS-CHAP-Challenge = 0x0d9e374a9694ce3167c781fcc44eb99f MS-CHAP2-Response = 0x0101ac14013da5fa87e576035cac1eb639b100000000000000002503f15d283d8658506e13b7e6e911da050a2bd8be0c2863 Authenticator-Field = 0x705ca7e21ff4a5039dd09123ecf7f285 2021-09-24 20:27:25.926250 (2) Access-Accept Id 23 lo0:127.0.0.1:23916 <- 127.0.0.1:1812 +0.000 +0.000 Service-Type = Administrative-User Class = 0x61646d696e73 MS-MPPE-Encryption-Policy = Encryption-Allowed MS-MPPE-Encryption-Types = RC4-40or128-bit-Allowed MS-CHAP2-Success = 0x01533d39304442443332394143364534354541453335353741313445383432443545463443343835454633 Attr-26.311.17 = 0xe6b1b1de6f7faafc05b7c8815cdf331177e6d3be0d3ee59799c16ddfd3e9d6b421d6 Attr-26.311.16 = 0xeb2f5b422272c5c1be8751c7afd11fc19803061fb08d1a9d7110097c84cc1ba72c24 Authenticator-Field = 0x2661524ab412cd871ad5a41c50991dab 2021-09-24 20:27:30.292625 (1) Cleaning up request packet ID 23 ^CDone sniffing [21.05.1-RELEASE][admin@pfsense.xxxxxxxxxx.net]/root: -
@nogbadthebad Yes, it is set to that 127 address.
EDIT: Should my RADIUS NAS IP Attribute be a 192 address? -
@nogbadthebad said in Setting up FreeRadius/OTP:
radsniff -x
Also, tried that, and got this:
radsniff -x
Logging all events
Defaulting to capture on all interfaces
radsniff: No PCAP sources available -
@droidus Are you connecting to the CLI via SSH ?
It should work.
-
@nogbadthebad Yes.
-
-
@nogbadthebad
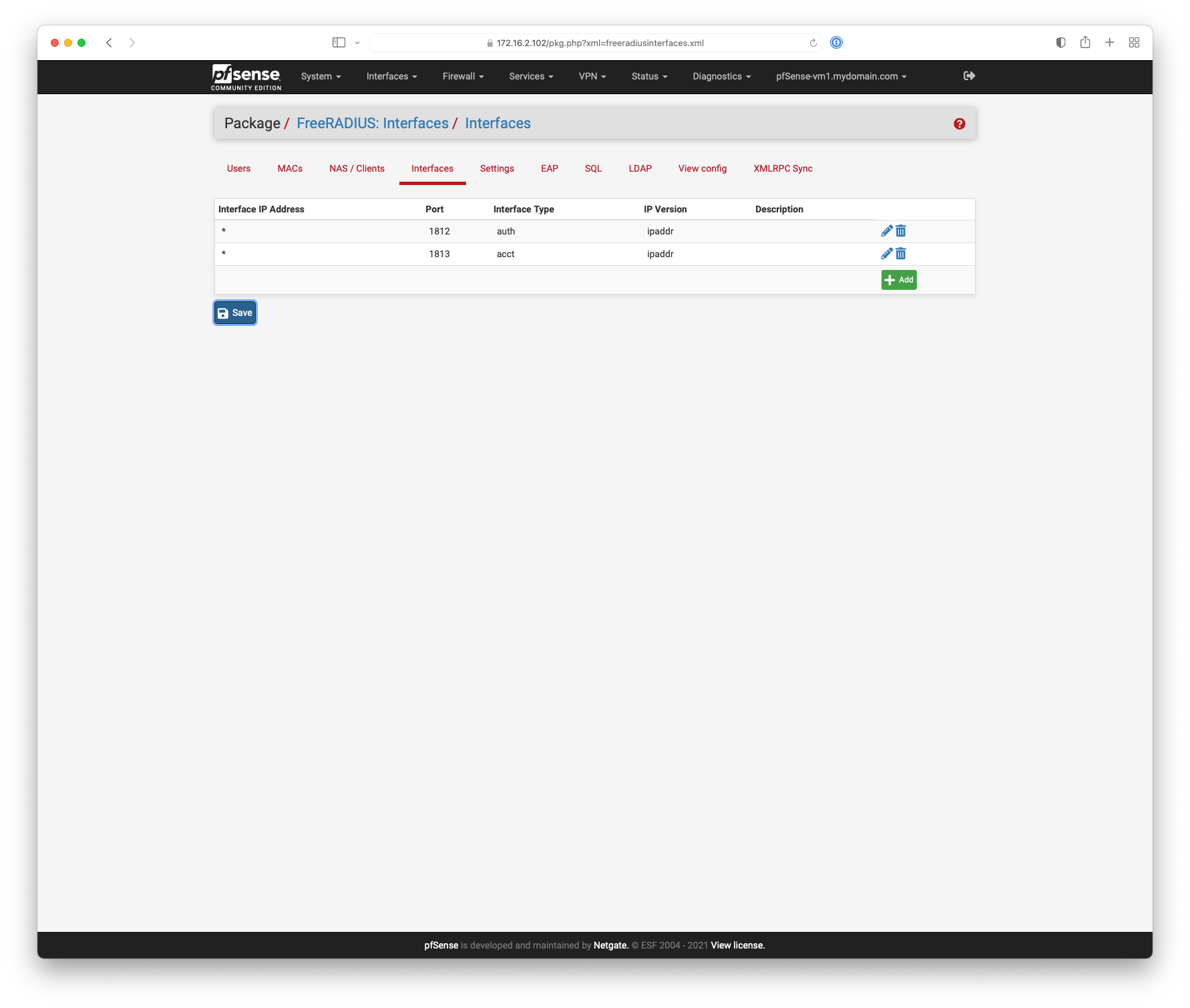
My only differences: For the first image. I am listening on 127.0.0.1 instead of *.
image 5 - I did not have that.
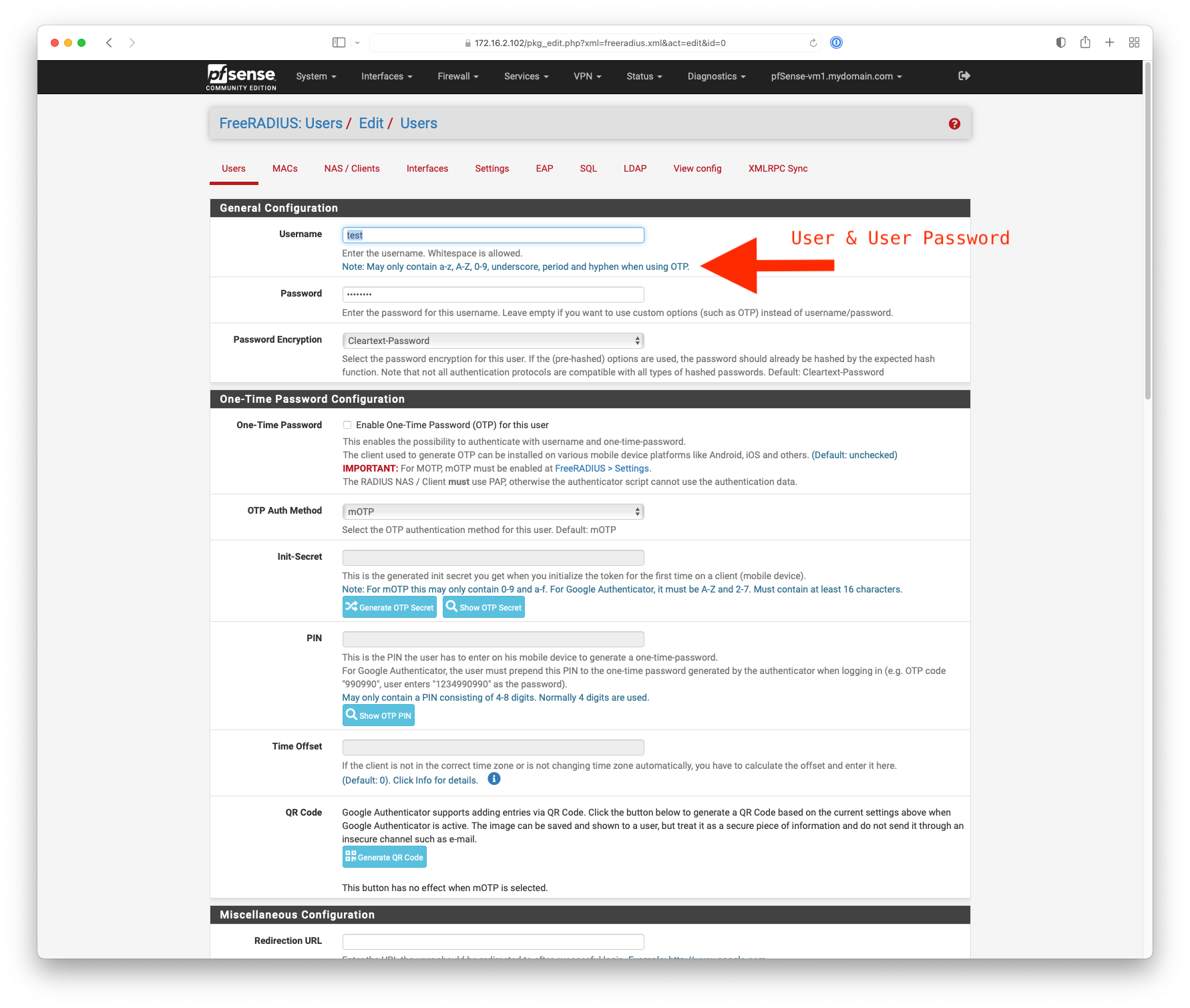
Freeradius users - Password Encryption set to MD5-Password for me. -
F furom referenced this topic on