[Solved] Firewall Log entries flooded for IPv6/:5353
-
@kiokoman Floating rule so that I only have to create one rule for all interfaces instead of defining Pass rule for :5353 on each of the interfaces. As you can see from the previous snapshot, the firewall is logging traffic destined for ff02::fb:5353 across several interfaces (LAN,IOT,KIDS, etc.)
-
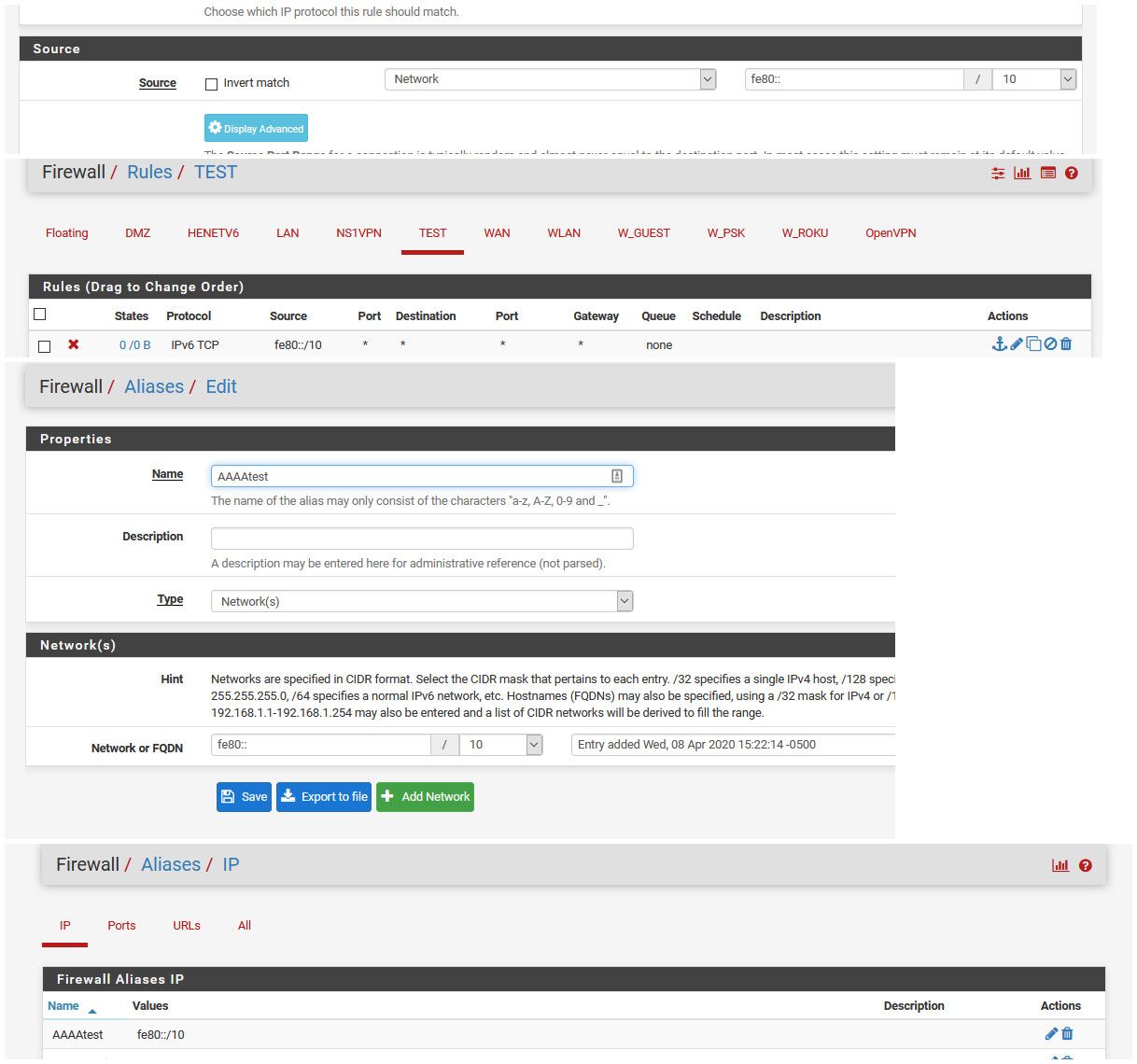
@stephenw10 When I try to create a Network alias as "fe80 /10" and save it, the alias reverts back to "fe80/32"

I would like to create one floating rule for all interfaces that allows for all link-local fe80::* instead of defining link-local pass rule per interface.
-
its fe80::/10
And why do you need an alias you can just put that directly in the rule..
-
@johnpoz Initially, I had wanted to create an alias to put in all link-local addresses and then use that alias when defining the fw rules. Now with fe80/10 there's no need for an alias.
What I was missing was the :: when I was creating the alias or when I was trying to directly put fe80::/10 in the fw rule. Unfortunately, in this instance I cannot blame the keyboard


-
@rsaanon btw, how do I mark this thread as resolved?
-
There's no formal way of doing it. You can edit the title and prefix it [solved]. Or I can.
-
@stephenw10 @johnpoz Thank you for helping me in getting this issue resolved. Am I able to donate something-something or at the very least buy you guys some beer :-)
-
Best thing to do is just pay it forward, see if there is someone you can help on the forums.. If you feel you must donate - then you can donate to freebsd.
https://www.freebsd.org/donations/
Or pick a worthy charity - anything related to helping with covid-19 would prob be a good choice with the current situation..
-
@jknott said in [Solved] Firewall Log entries flooded for IPv6/:5353:
Perhaps I'm missing something, but why would you have rules for something that's not supposed to leave the local link?
@johnpoz said in [Solved] Firewall Log entries flooded for IPv6/:5353:
Only reason to create such rules would be to no log the traffic jknott..
That makes sense but why create pass rules. To prevent the default block rule logging, should not we be creating an equivalent block rule but without logging enabled?
However I'm rather new to this and not sure if that would break some function I'm not aware of. Hence my question, where should the block ff02::fb 5353 go to just block the logging but not change the default pfsense filtering
- WAN outgoing or
- floating rule on all or perhaps all LAN interfaces
-
@patch You can create whatever rule you want be it allow or block or reject - and set it not to log.. But unless you were using something like avahi to pass on the mdns query - pfsense really has no use for such traffic, and wouldn't be doing anything with it. If you allowed it.
Pfsense is clearly blocking it already, what interface your seeing the traffic on would be the interface you create the rule on to block it and "not" log it.
-
A anthonys referenced this topic on
-
S SteveITS referenced this topic