VLAN won't communicate with LAN
-
@djjoakim
Ah ... That alias is a pfSense internal , no worries.
But the home made RFC1918 Alias , not being the full range ....I'd try to reboot the firewall first , before ripping the PC apart.
Real reboot , not just clear states. -
A Tip of Experience....
Move your lan away from 192.168.1.0/24
Move your WiFi away from 10.0.0.0/24They are always used , and might "Bite your ..." if/when you have to run a VPN to a buddy , that also uses those two
And why have you used a network from each of the 3 RFC1918 ranges ??
Why haven't you used all your internal nets in the same range ...Ie.
10.42.0.0/16 = Home Lan
10.42.1.0/24 = Lan
10.42.64.0/24 = WiFi
10.42.128.0/24 = Fast
10.42.129.0/24 = EJFastetc ......
Er du norsk ?
-
@bingo600 Alright, thanks.
Yeah well since i am very new to this, i have watched alot of youtube guides, and a friend of mine who is somehow better at this then me, has helped alot aswell.
But yeah, i understand how you mean - that do sound better.. I will figure out why my PC won't communicate with the other subnets and then i will re-do my ip adresses in my firewall.
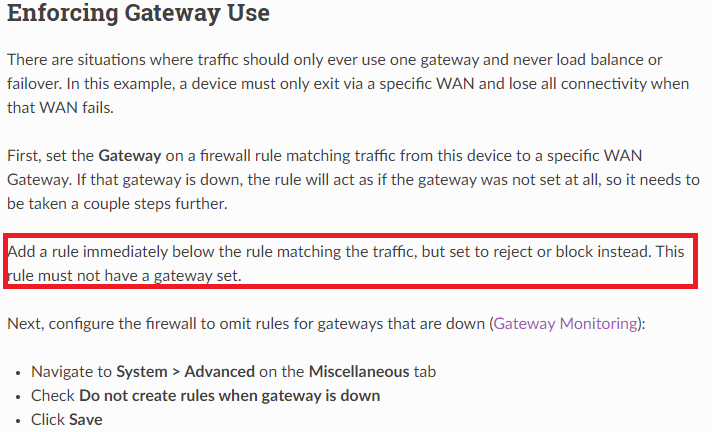
I think the problem maybe something wrong in my switch..Since you seem to be alot better at this then me, can you just confirm this settings(?) I think i have done it like netgate site says it should be done, i have set Do not create rules when gateway is down in the settings. My goal here is that if my vpn client goes down, the devices connected to it can't leak into my regular WAN.
Inte norsk, men väldigt nära granne... ;)
-
@djjoakim said in VLAN won't communicate with LAN:
@bingo600 Alright, thanks.
But yeah, i understand how you mean - that do sound better.. I will figure out why my PC won't communicate with the other subnets and then i will re-do my ip adresses in my firewall.
You will be happier later on.
And now is the time to do it , before you have to move tonzz of devices.I think the problem maybe something wrong in my switch..
Your switch is a L2 (Layer 2) device, i would expect.
Brand/Model ?If it works one way and not the other , it's usually not on L2.
Unless you have short circuited some vlans.Since you seem to be alot better at this then me, can you just confirm this settings(?) I think i have done it like netgate site says it should be done, i have set Do not create rules when gateway is down in the settings. My goal here is that if my vpn client goes down, the devices connected to it can't leak into my regular WAN.
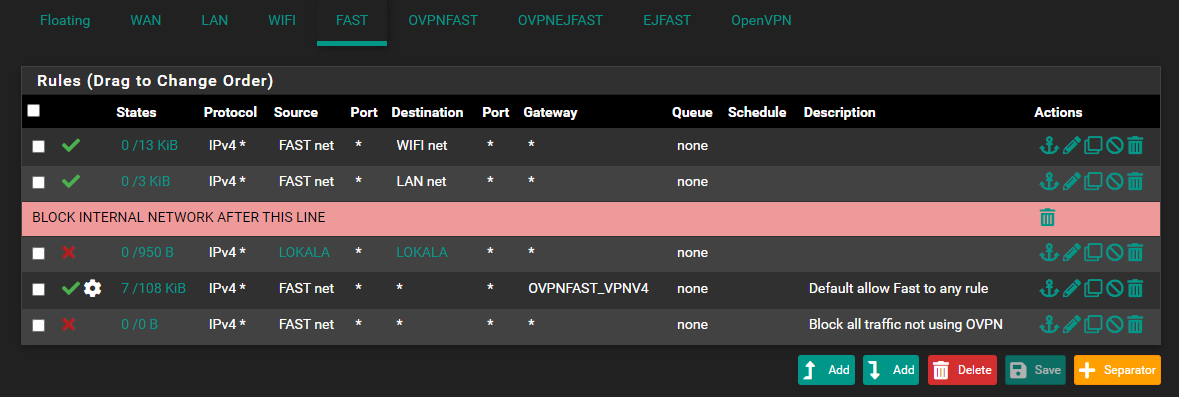
I would change the first LOKALA til FAST net.
That line would cause anything having a FAST net IP , to be "dropped/denyed" if destination is one of the ip's matching the nets in LOKALA.
Now get the logging enabled on those DENY lines ...
You will make your life so much easier.If they log kazillions of lines , you can consider removing them , but else you will be happy to see what is being blocked.
Inte norsk, men väldigt nära granne... ;)
Heh ... Har et Torp näre Laholm.
Vet du der er et Svensk forum her

-
@bingo600 Yeah, i just wan't the LAN to communicate with VLAN first.. then i will swap ip's ;) one problem at a time...
I have a TP-Link TL-SG105E Switch, but i tried to change my LAN in a different port (witch i thought was the problem) but the problem is still there, i also disabled my windows firewall.. And yep, still not working.
Alright, now i have done that (Changed lokala to FAST net) Yes, i will turn on logging for that - there is no so many devices so it's true, it would be really nice to see the log what's blocking and what's not.. You are right about that.
Ah! En kompis har en stuga i Gördalen, precis bredvid norska gränsen. Brukar vara där på vintrarna.. :)
Hade faktiskt ingen aning de fanns ett svensk forum, ska kolla in det :) Tack! -
@djjoakim said in VLAN won't communicate with LAN:
@bingo600 Yeah, i just wan't the LAN to communicate with VLAN first.. then i will swap ip's ;) one problem at a time...
Good strategy
I have a TP-Link TL-SG105E Switch,
That's probably the worst switch to own. 105/108
It is known for leaking VLAN1 on every port ..
See
https://forum.netgate.com/topic/68488/tp-link-smart-switches-anyoneWhat hardware version do you have , do you have the latest firmware ?
https://www.tp-link.com/us/support/download/tl-sg105e/#FirmwareI think they might have fixed something in HW version 3 or higher.
But i don't trust them. I have a 108E that i don't use because of those issues.
TP-Link switches are "Cheap & Bad"Suggest a Dlink DGS-1100-08v2
https://www.pricerunner.se/pl/167-3200059049/Switchar/D-Link-DGS-1100-08-v2-priserbut i tried to change my LAN in a different port (witch i thought was the problem) but the problem is still there, i also disabled my windows firewall.. And yep, still not working.
Lousy switch
But there is no 100% guarantee that a DGS-1100-08 would solve your issue.
But it will solve the VLAN Leaking security issue.Alright, now i have done that (Changed lokala to FAST net) Yes, i will turn on logging for that - there is no so many devices so it's true, it would be really nice to see the log what's blocking and what's not.. You are right about that.

Ah! En kompis har en stuga i Gördalen, precis bredvid norska gränsen. Brukar vara där på vintrarna.. :)
Er dansk , så Halland (Laholm) er jo näre (og gammelt dansk)
Hade faktiskt ingen aning de fanns ett svensk forum, ska kolla in det :) Tack!
-
@bingo600 Yeah i heard some people was having problem with the switch, but people was also complaing on D-link.. I was getting another switch first, but that was sold out and was expected in november, so then i bought this model..
Oh, that dosen't sound good.. Well, i have VLAN1 deactivated in the switch, so hopfully it will work.. but it dosen't feel so good, since it's only my PC that can't reach the other subnets, but all the other devices can..
Yep, the switch is only 1 month old, so it's the latest.
If i can't get the problem solved, i will defently check other switches.. but i hope the problem isn't in the switches, since i just paid 1000SEK for them..
Ah såklart! Jag förknippade Danmark med Norge... ber om ursäkt för det :) Men då är vi grannar trots allt.. Jag är ju dock bosatt på andra sidan Sverige.. "baksidan" som dom flesta kallar det..
-
Well il be damn.... I feel so stupid now, but yeah! The problem is now solved.
I could't get it off my mind why it was working on all other devices in the subned EXEPT my LAN Windows PC... I could't access any other devices from my PC, so i disabled my firewall, antivirus and so on, but no - still nothing... Then i realised that i use a VPN device on my PC, and ofc it was connected to a VPN service. So when i shut it off, i can access all my other subnets...
I feel so dumb right now! Somehow my VPN Client is blocking me from accessing other subnets, when it's connected...Well, it's sunday here so i will blame it on that...
Anyways, thanks alot for the response i got on this forum - you guys are amazing at what you do, and i will be forever thankful for the time you spend on helping dumb people like me.
Thanks @johnpoz for you'r quick response and especially thanks to you @bingo600 for taking you'r time trying to explain simple stuff for me, i really appreciate you taking you'r time.

-
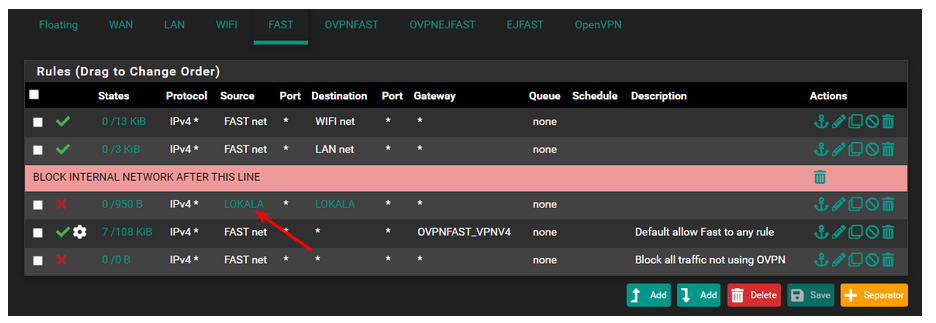
@bingo600 Hmmm so.. I think i celebrated to fast, now - my WIFI don't work unless i disable the block rule "WIFI NET - LOKALA"...
I don't really know if there is something i am missing here but, on all the other interfaces - it looks the same, and they work just fine, can you see if i am missing something ovious?
-
With those settings above on wifi & ejfast.
You have forbidden ANY communication from those net's to ANY other networks in LOKALA.So you would only be allowed to go to the internet.
But ... If you are using the pfSense as DHCP server , you will usually also (via DHCP) get settings to use pfSense as DNS server. And since the pfSense interface (used for DNS) is member of LOKALA , it will reject the DNS queries.
Try to ping 8.8.8.8 from WiFi , if that works you have access to the internet.
Try to ping www.google.com , if that doesn't work , and the above 8.8.8.8 did work. Your DNS is prob. not resolving.Er det P...Bay du gömmer ifran FRA

You need to add , above the Deny "net" LOKALA.
permit TCP/UDP Source WiFi net * Dest WiFi address Dest port range DNS (53)But you already saw those tdp/udp 53 blocks .... didn't you ......
Since you did enable logging on all the DENY lines , as we spoke about.
Or ...
If you tell the firewall to block EVERYTHING to LOKALA it will block EVERYTHING , including DNS requests and NTP and ....
Technically you should have "Lost" your DHCP too.
But the pfSense guyzz were nice, and AFAIK. Have permitted DHCP packages in a hidden rule. If you enable the DHCP server on that lan.On the pfSense firewall , rules are matched from top and going down until "first match".
TIP:
If you use the pfSense as DNS server , you might have a DNS Leak.
You could use 1.1.1.1 or 8.8.8.8 instead (on the Vlans where you use VPN as exit).
And then you do not need the : Allow DNS to pfSense interface rule, on that interface./Bingo
-
@bingo600 Yeah, that's what i wan't. I don't want the networks to communicate except some of the IP's (hence why i have "Only accept if OK" on LAN)
That made alot of sence when you said it like that.. bc my DNS servers on pfsense are as below; (From the vpn provider) And just like you say, they get blocked by that rule..
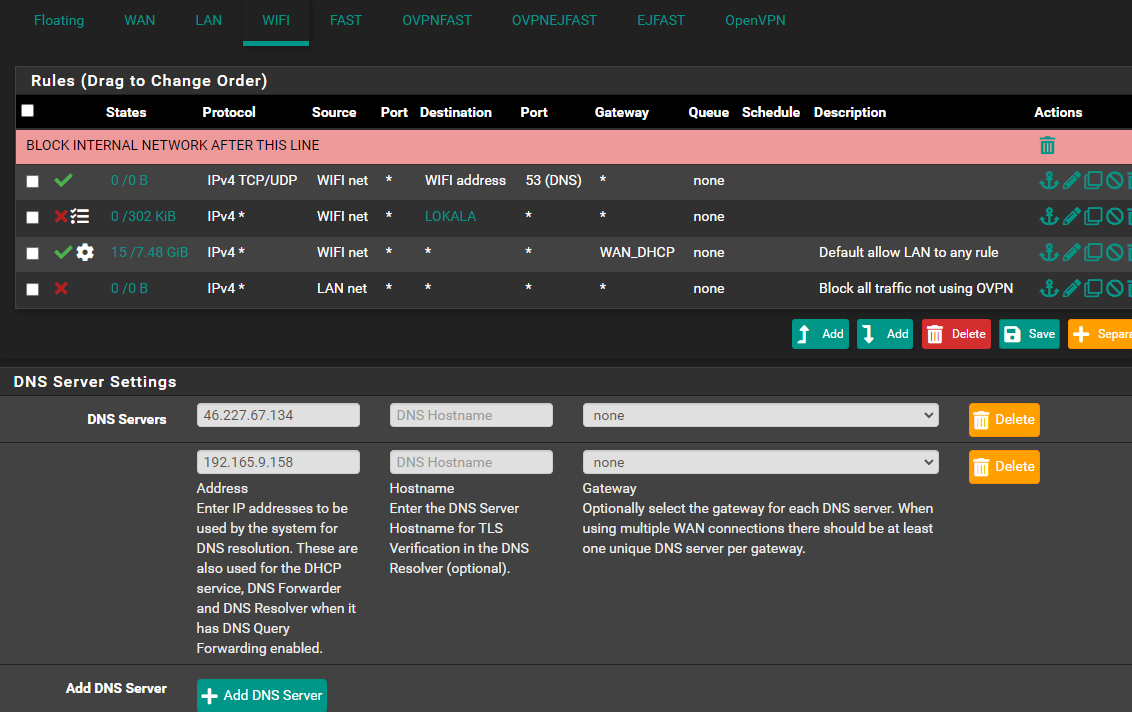
Haha nej, inget p...bay.. bara väldigt försiktig av mig

You are awesome man! Now it works, when i added it like you said.. Everything seems so easy for you haha, and when you expain it - it make alot of sense.. I am learning every day that passes!
Well, as you can see in that image, i did enable the log option, however.. i could't find where it was saving that logs.. under "Firewall" in System logs, i could't find it anywhere.. But i am surly blind..

Yeah, that makes alot of sense.. Surly, on the pic above - the settings are correct this time?
About you'r tip, i don't wan't any DNS leaks.. So, should i use those DNS servers instead, of the ones i am using now?
Thank you once again..
-
@djjoakim That lan net as source on your wifi net is pointless.. In what possible scenario would some lan net address be the source of traffic into your wifi net interface?
And lets say it was, how would it be sending traffic to wifi address to be routed anywhere, and even if it could - it wouldn't be allowed because the source is not wifi net for your allow rules - and if not explicitly allowed - then default is deny. So there is NO possible case were such a rule would be needed.
-
@johnpoz oops… Thanks for that, i simply copied that from the LAN net and apparently forgot to change source from LAN to WIFI…. Thanks for the imput! As you say, it dosen’t make any sense as it is now.
Thanks
-
@djjoakim if you change that rule to wifi net still doesn't make any sense - because it would never be evaluated since there is a rule above it that would be and send all traffic out your wan dhcp gateway. Just delete that rule, or change it in such a way that it would be evaluated how you want it to be. With what you posted just changing it to wifi net a source - pointless.
-
@johnpoz
AFAIK he has set "disable rule when gateway is down" , and the next is to blackhole if the above rule is disabled. -
@johnpoz But haven't i done like it says in here, or am i missunderstanding something?
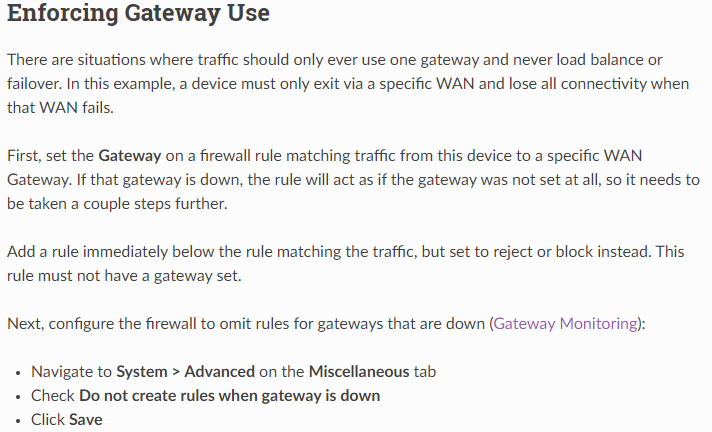
-
If he set gateway down disable rule - still no traffic allowed because there is no allow rule. What is the point of that block rule? Unless specific do not want to log traffic?
Only when that gateway is down?
-
@johnpoz I honestly have no idea - i just followed what's said on the Netgate site.
@bingo600
Sorry for waking this thread up again, but i can't understand what's wrong here.. I have 8 devices under "EJFAST" that works just fine, but one device can't access internet.. Only when i disable my block rule from talking to other networks "LOKALA", internet works for that device (?) So, now when i check the logs i can see it's trying to connect on my LAN with port :53, so just like "WIFI" interface, i added the DNS rule on "EJFAST" interface aswell, but - i still get the same deny in logs, and the device can't access internet.. Any ideas?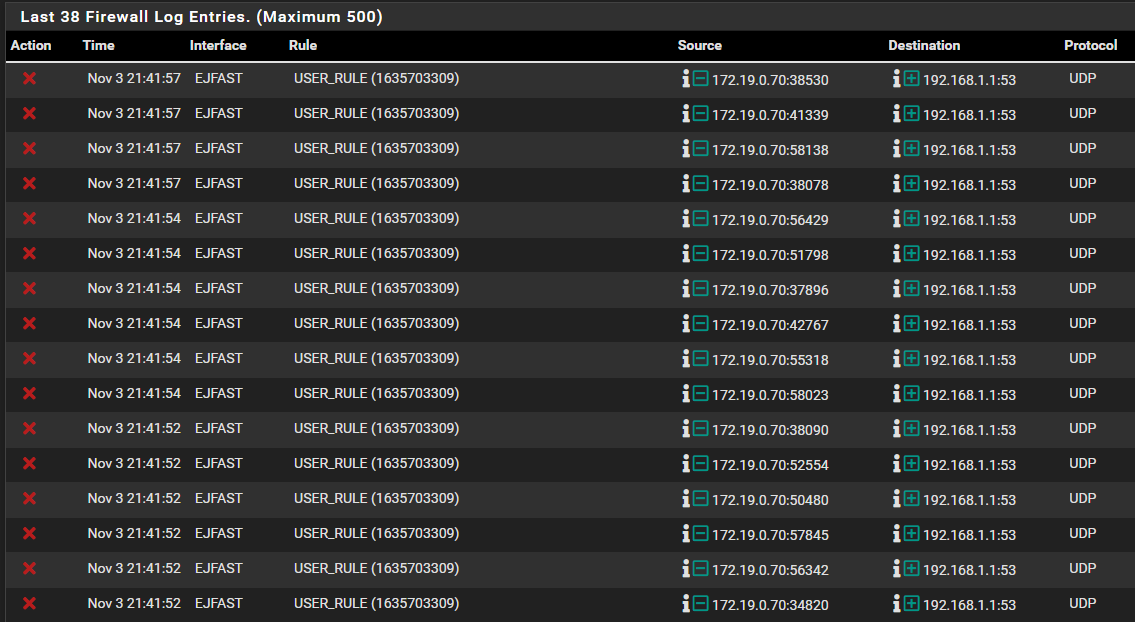
Thanks!
-
@djjoakim well where is your rule that would allow that traffic before you block it.
if something is trying to use 192.168.1.1 for dns - and your not allowing it - then no internet not going to work without dns..
i just followed what's said on the Netgate site.
Where - there is no where on site that says to make pointless rules..
Trying to apply a guide without understanding what is actually going on and what the rules actually do is going to lead to nonsense rules that make no sense in whatever setup your trying to do..
-
@johnpoz Yes i understand that... but the part i don't understand is that on the interface "WIFI" i added DNS rule, as shown below - and then it worked. But even with this rule added to "EJFAST" it won't work..
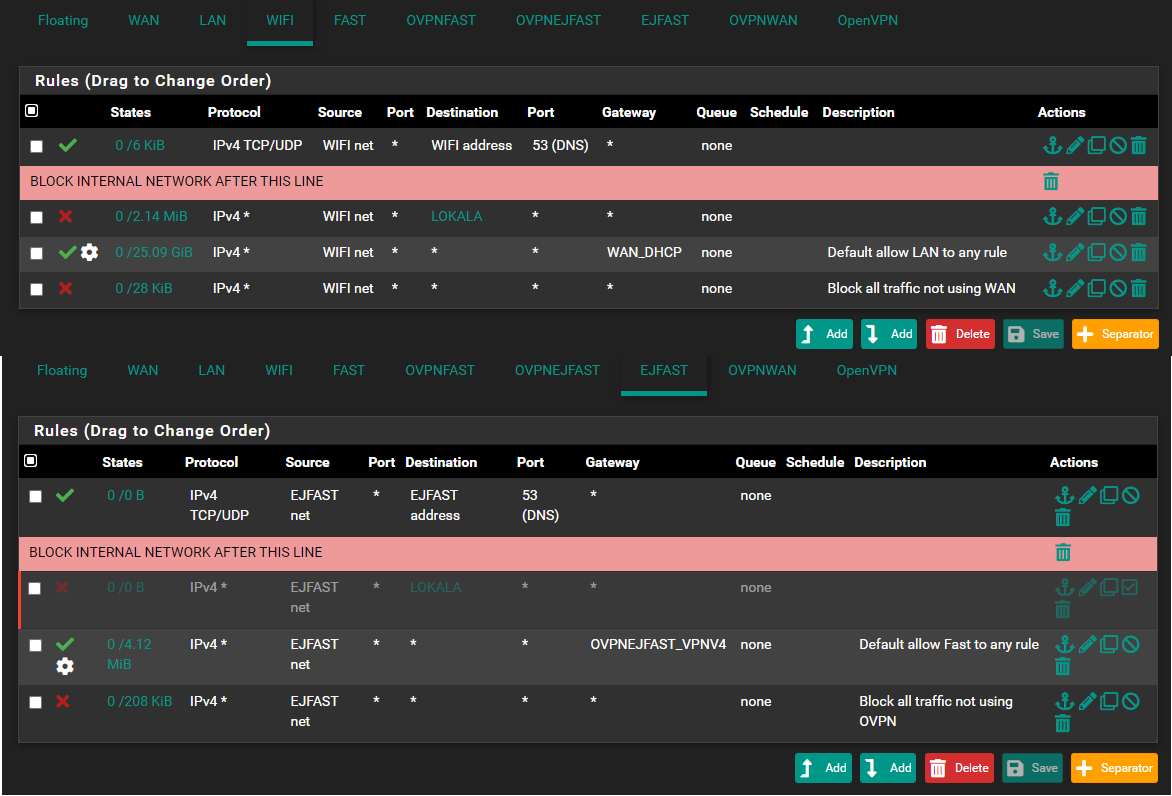
Well like i said, i am new to this and trying to learn, so i follow the guides that are available, please correct me if there is something i have misunderstand with this guide.
It's impossible to know everything with 1 week of knowledge.