VLAN won't communicate with LAN
-
@bingo600 Hmmm so.. I think i celebrated to fast, now - my WIFI don't work unless i disable the block rule "WIFI NET - LOKALA"...
I don't really know if there is something i am missing here but, on all the other interfaces - it looks the same, and they work just fine, can you see if i am missing something ovious?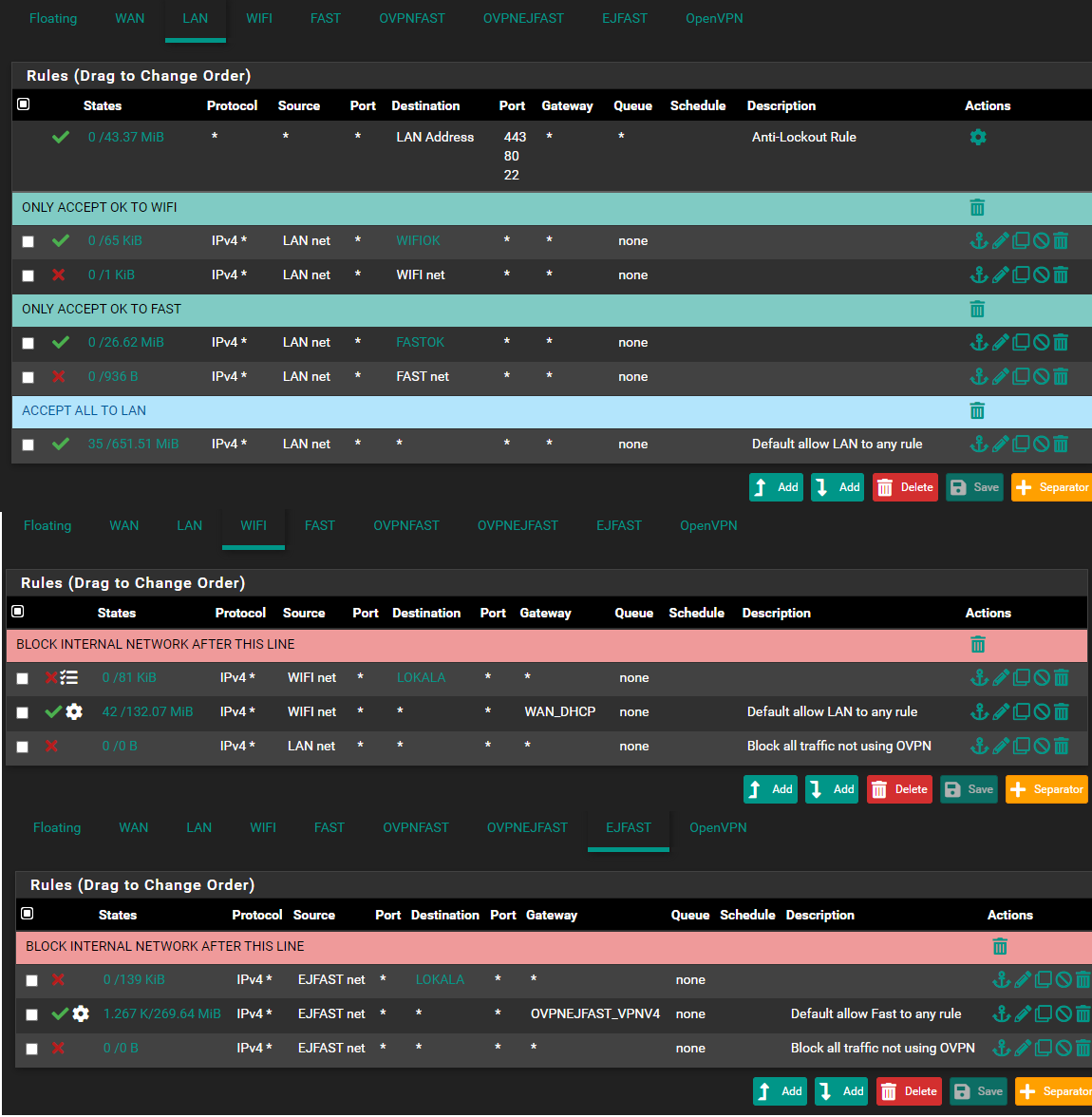
-
With those settings above on wifi & ejfast.
You have forbidden ANY communication from those net's to ANY other networks in LOKALA.So you would only be allowed to go to the internet.
But ... If you are using the pfSense as DHCP server , you will usually also (via DHCP) get settings to use pfSense as DNS server. And since the pfSense interface (used for DNS) is member of LOKALA , it will reject the DNS queries.
Try to ping 8.8.8.8 from WiFi , if that works you have access to the internet.
Try to ping www.google.com , if that doesn't work , and the above 8.8.8.8 did work. Your DNS is prob. not resolving.Er det P...Bay du gömmer ifran FRA

You need to add , above the Deny "net" LOKALA.
permit TCP/UDP Source WiFi net * Dest WiFi address Dest port range DNS (53)But you already saw those tdp/udp 53 blocks .... didn't you ......
Since you did enable logging on all the DENY lines , as we spoke about.
Or ...
If you tell the firewall to block EVERYTHING to LOKALA it will block EVERYTHING , including DNS requests and NTP and ....
Technically you should have "Lost" your DHCP too.
But the pfSense guyzz were nice, and AFAIK. Have permitted DHCP packages in a hidden rule. If you enable the DHCP server on that lan.On the pfSense firewall , rules are matched from top and going down until "first match".
TIP:
If you use the pfSense as DNS server , you might have a DNS Leak.
You could use 1.1.1.1 or 8.8.8.8 instead (on the Vlans where you use VPN as exit).
And then you do not need the : Allow DNS to pfSense interface rule, on that interface./Bingo
-
@bingo600 Yeah, that's what i wan't. I don't want the networks to communicate except some of the IP's (hence why i have "Only accept if OK" on LAN)
That made alot of sence when you said it like that.. bc my DNS servers on pfsense are as below; (From the vpn provider) And just like you say, they get blocked by that rule..
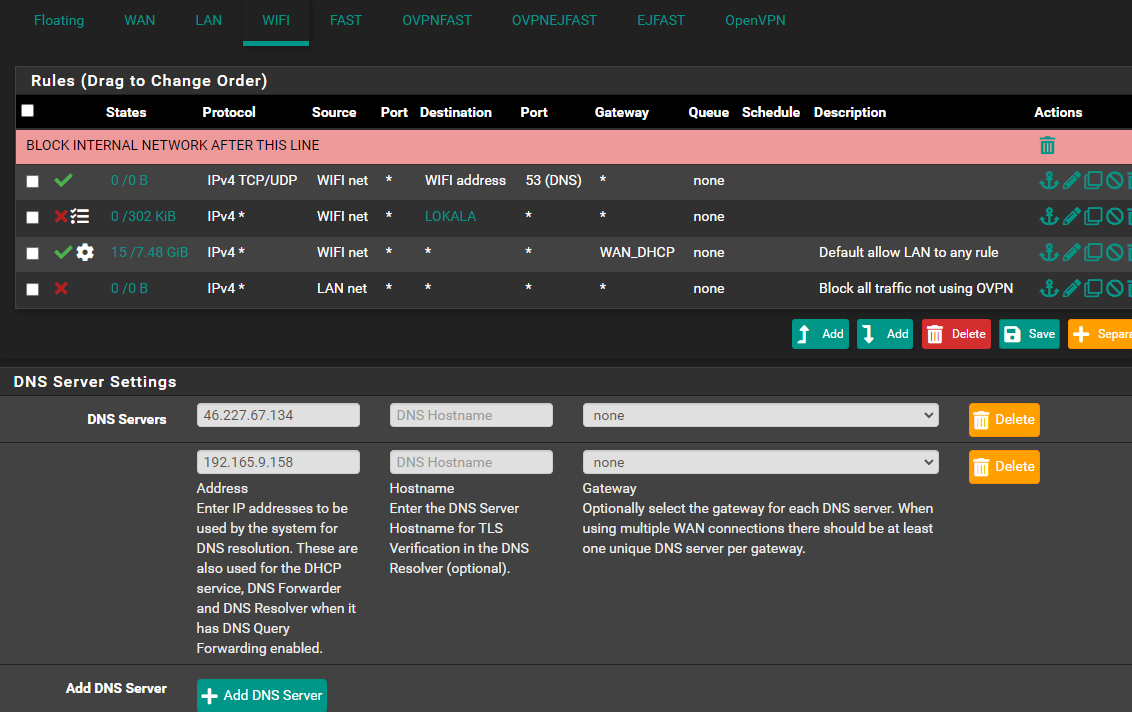
Haha nej, inget p...bay.. bara väldigt försiktig av mig

You are awesome man! Now it works, when i added it like you said.. Everything seems so easy for you haha, and when you expain it - it make alot of sense.. I am learning every day that passes!
Well, as you can see in that image, i did enable the log option, however.. i could't find where it was saving that logs.. under "Firewall" in System logs, i could't find it anywhere.. But i am surly blind..

Yeah, that makes alot of sense.. Surly, on the pic above - the settings are correct this time?
About you'r tip, i don't wan't any DNS leaks.. So, should i use those DNS servers instead, of the ones i am using now?
Thank you once again..
-
@djjoakim That lan net as source on your wifi net is pointless.. In what possible scenario would some lan net address be the source of traffic into your wifi net interface?
And lets say it was, how would it be sending traffic to wifi address to be routed anywhere, and even if it could - it wouldn't be allowed because the source is not wifi net for your allow rules - and if not explicitly allowed - then default is deny. So there is NO possible case were such a rule would be needed.
-
@johnpoz oops… Thanks for that, i simply copied that from the LAN net and apparently forgot to change source from LAN to WIFI…. Thanks for the imput! As you say, it dosen’t make any sense as it is now.
Thanks
-
@djjoakim if you change that rule to wifi net still doesn't make any sense - because it would never be evaluated since there is a rule above it that would be and send all traffic out your wan dhcp gateway. Just delete that rule, or change it in such a way that it would be evaluated how you want it to be. With what you posted just changing it to wifi net a source - pointless.
-
@johnpoz
AFAIK he has set "disable rule when gateway is down" , and the next is to blackhole if the above rule is disabled. -
@johnpoz But haven't i done like it says in here, or am i missunderstanding something?
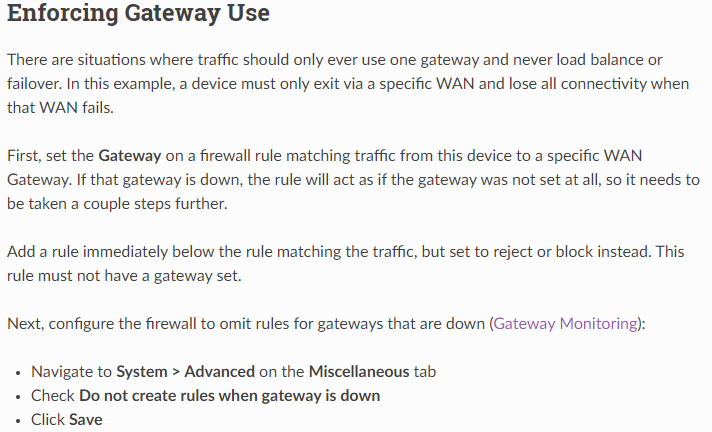
-
If he set gateway down disable rule - still no traffic allowed because there is no allow rule. What is the point of that block rule? Unless specific do not want to log traffic?
Only when that gateway is down?
-
@johnpoz I honestly have no idea - i just followed what's said on the Netgate site.
@bingo600
Sorry for waking this thread up again, but i can't understand what's wrong here.. I have 8 devices under "EJFAST" that works just fine, but one device can't access internet.. Only when i disable my block rule from talking to other networks "LOKALA", internet works for that device (?) So, now when i check the logs i can see it's trying to connect on my LAN with port :53, so just like "WIFI" interface, i added the DNS rule on "EJFAST" interface aswell, but - i still get the same deny in logs, and the device can't access internet.. Any ideas?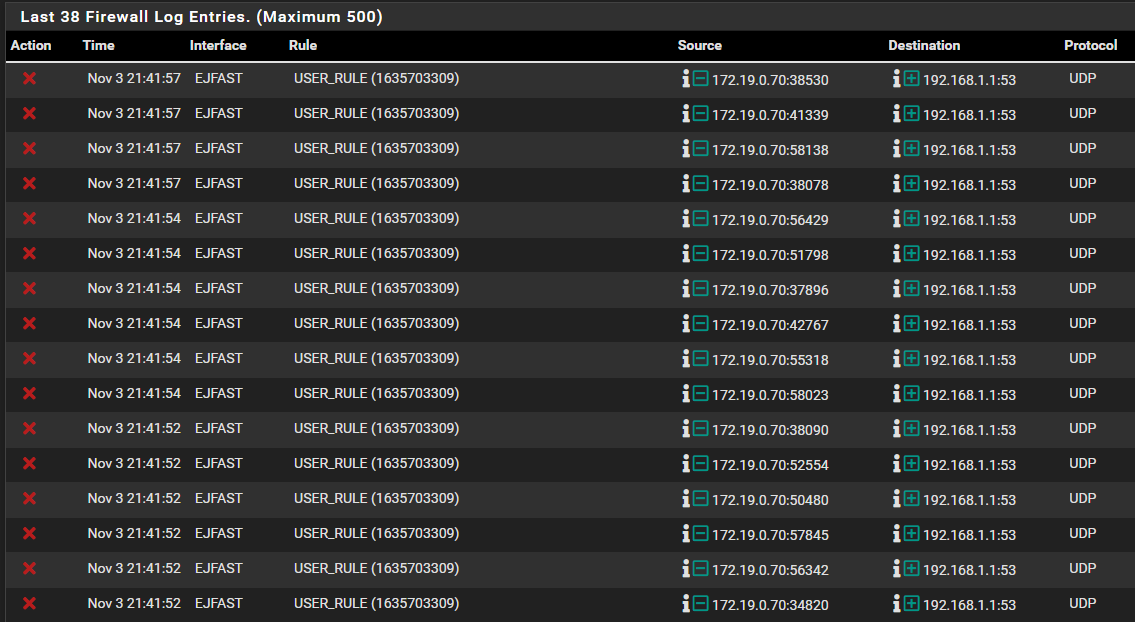
Thanks!
-
@djjoakim well where is your rule that would allow that traffic before you block it.
if something is trying to use 192.168.1.1 for dns - and your not allowing it - then no internet not going to work without dns..
i just followed what's said on the Netgate site.
Where - there is no where on site that says to make pointless rules..
Trying to apply a guide without understanding what is actually going on and what the rules actually do is going to lead to nonsense rules that make no sense in whatever setup your trying to do..
-
@johnpoz Yes i understand that... but the part i don't understand is that on the interface "WIFI" i added DNS rule, as shown below - and then it worked. But even with this rule added to "EJFAST" it won't work..
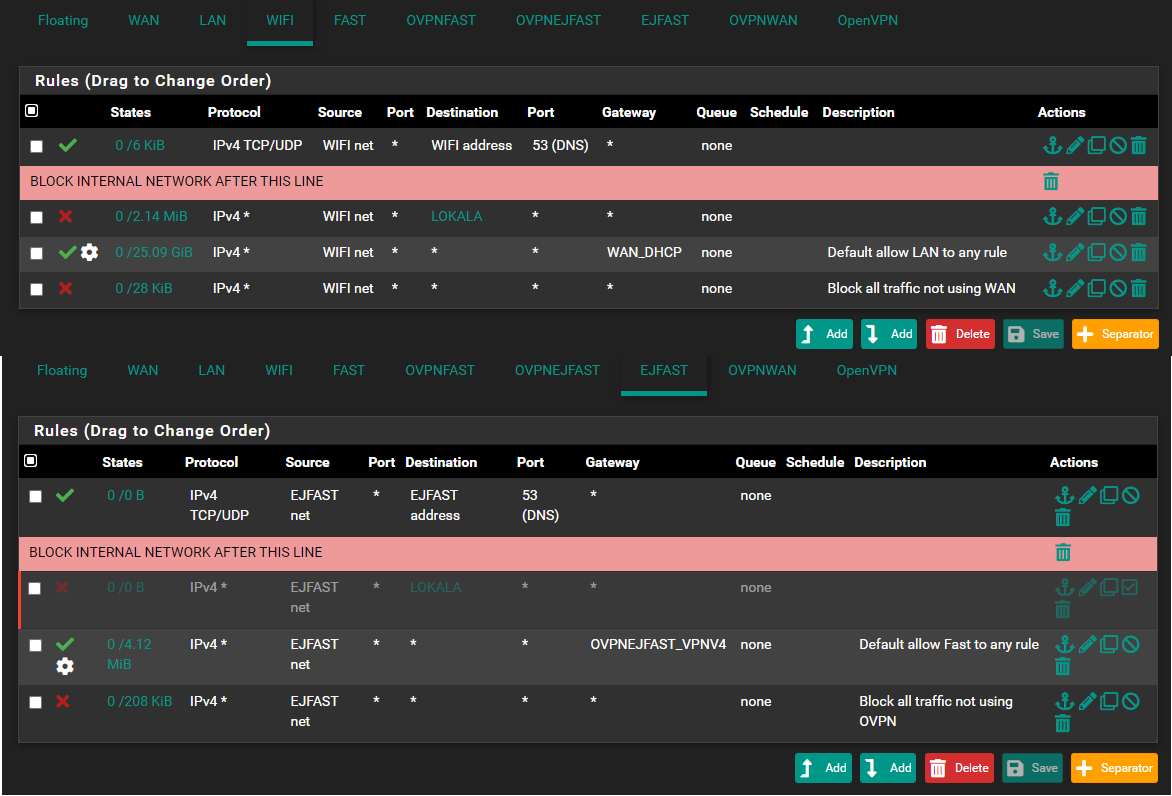
Well like i said, i am new to this and trying to learn, so i follow the guides that are available, please correct me if there is something i have misunderstand with this guide.
It's impossible to know everything with 1 week of knowledge.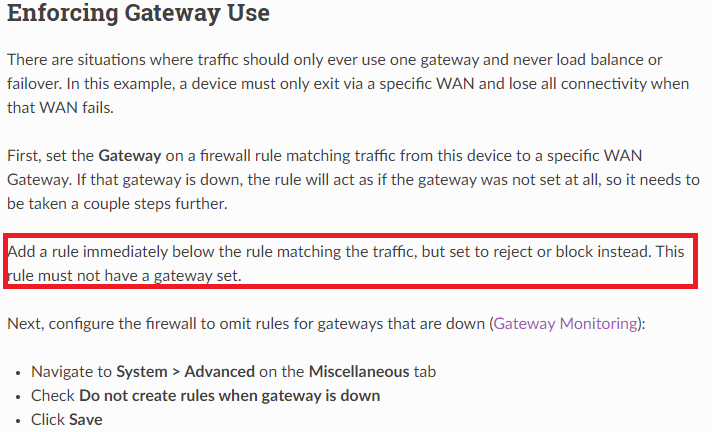
-
-
That would be a kill switch for a vpn connection. Which your using wan dhcp gateway. So makes no sense in this context.
Blindly following some guide that makes no sense for what your doing - leads to nonsense rules..
You would only need such a rule if you have an allow rule below your policy route rule, if you didn't want that allow rule to be used - then you would need a block rule above the allow rule.
You have no ALLOW rule.. So like I said your traffic would be denied by default...
-
@johnpoz
yeah, you are right, I was shooing in the blind. Long time since I used OpenVPN. I use WG, and have no problem too accessing different networks locally. -
Your "deny" log showed that pfSense blocked EJFAST clients , sending DNS packets to 192.168.1.1 (Lan interface)
My guess is that you have set that DNS (LAN) IP in the EJFAST DHCP definitions.So you either have to remove the entry from the DHCP (then it will default to the connected interface , here EJFAST). .... Preferred.
Or allow DNS from EJFAST net to LAN address
/Bingo
-
@bingo600 Yep... got it working. Thank you so much again.. :)