Chrony, PTP, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd)
-
@daddygo said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
10G is coming (in SOHO) and I am already compatible with it,
Its already here to be honest.. Just need a few more years for the price to come down before more adoption if you ask me..
I have a few more years left on my main switch for support.. But as that nears and look for replacement, I would love a reasonable priced.. Say $200ish replacement for my sg300-28 that had atleast a few multigig ports 10ge, but also support 2.5/5ge. And hey poe would also be nice.. Or something that had sfp+ support where the modules are not all that expensive where I could add multigig..
I have 2.5ge running between my nas and pc, and yeah no way in hell I would ever go back to just gig for that connection.. But it was a bolt on sort of way of getting it with usb dongles.. It works, but much rather have that connection running through the switch vs just san type of connection between pc and nas on different network.
And my internet is only 500/50 - it works and its fine and ok with the price. I don't really see need for gig to internet for my use.. But would really love to see that at 500/500. 1/1 gig would be fantastic.. But current isps in the area have no sort of symmetrical offerings and the bump to 1000 would still only be 50 up, so its pretty pointless for my use.
-
@johnpoz said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
if you ask me..
yes I think you are a special guy :)
don't worry your opinion really matters, I see the energy you add to the forum, respect (!!!)I love Cisco at home SMB (SG series). and everywhere else, serious and considered philosophy...
+++edit:
I won't forget your SMB3 writeup on the more serious file transfer to Syno
+++edit2:
if I remember correctly is it a Realtek 2.5G USB NIC? -
@daddygo yeah the nic is club3d model, and it realtek chip..
Using this driver
https://github.com/bb-qq/r8152Overall it has been fine - but it has cut out a few times.. Where I had to unplug it and plug it back in..
SMB3 multichannel, yeah that is another option to break the 1g barrier for sure - would go back to that if had to go back to gig that is for sure.. Ran that for a couple years, never any issues with it.. But going to 2.5 did get me overall boost in top end speed..
But yeah multigig or better yet full 10ge is yeah a viable option for the soho, and prices are doable.. Its not like thousands or anything - so it can be done in the home if you want too.. But the price of doing it, is quite a bit more than just gig.. I would of hoped that 2.5/5 would become more mainstream - there are some 2.5 gig switches in the 100$ range out that is making that way more viable and pc makers are starting to include nics that can do 2.5
-
AFAIK this is the cheapest 10Gb decent "Home switch"
MikroTik Cloud Router Switch CRS309-1G-8S+IN
One on offer here , else around $280
https://www.ebay.com/itm/363622236174I have heard several reports about "fs.com" switches being nice, haven't tried them my self.
"Home"
https://www.fs.com/de-en/products/122281.htmlA bit more DC like (40G uplinks)
https://www.fs.com/de-en/products/108710.htmlTheir optics should be quite cheap too.
But not a "score" like DG's Ciscos
/Bingo
-
@bingo600 said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
I have heard several reports about "fs.com" switches being nice, haven't tried them my self.
do not do this, pls.

I've had a good relationship with FS:COM for a long time, they have super SFP/SFP+ modules, check it out:

but don't buy switches from them(!!!), BROADCOM chips are in many units and they are fast, but for example, if you want to set the current time it's simple, but strange....
by giving them DNS, they are immediately connected to a Chinese server (?)
if you are interested I will show you this tomorrow, I have Wireshark files about this and a switch like this in the next room in my flat

-
@bingo600 said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
MikroTik Cloud Router Switch CRS309-1G-8S+IN
One on offer here , else around $280
https://www.ebay.com/itm/363622236174Hmmmm,

Don't think that MikroTik is stable, look at this conversation, you wonder who I am???? :-)
(in this conversation)https://forum.mikrotik.com/viewtopic.php?t=167891
CSS610-8G-2S yes that's right it's the same in terms of the fraudulent switch, hhihihi :) - MikroTik Cloud Router Switch CRS309-1G-8S+IN
-
@daddygo said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
by giving them DNS, they are immediately connected to a Chinese server (?)
Could they be checkking for new firmware ??
-
@daddygo said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
MikroTik Cloud Router Switch CRS309-1G-8S+IN
:Don't think that MikroTik is stable, look at this conversation, you wonder who I am???? :-)
Ok ... I was sure i read that the CRS309 (and it had to the that one) , was ok.
But then i have seen lots of bugs related to RouterOS ....Thanx for the tip
-
@bingo600 said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Could they be checkking for new firmware ??
Nope, unfortunately FW can only be installed manually...
As I followed along with Wireshark, the time is synchronized from a Chinese source via some cPanel route, that in itself is very strange, because it puts you through a lot of redirection.
by default you can't even specify it, NTP servers only have their own Chinese source hard coded into them...
Neither from GUI nor from CLI you can specify a time server path, say 216.239.35.0 or 162.159.200.123 or etc.
I don't like this kind of solution, I want to be in control

-
@bingo600 said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
i have seen lots of bugs related to RouterOS ....
Yes I also have some 10G capable MikroTik on the shelf waiting to finally get a stable FW for it, because otherwise they are not bad...
Good prices among the 10G things on the market, but then if have say VLAN and say QoS problems not to mention 10G speed negotiation errors (on SFP+ ports) you can't use it well.
They'll fix it hope, - they continue to gather dust on the shelf :) -
@daddygo said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@bingo600 said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Could they be checkking for new firmware ??
Nope, unfortunately FW can only be installed manually...
As I followed along with Wireshark, the time is synchronized from a Chinese source via some cPanel route, that in itself is very strange, because it puts you through a lot of redirection.
by default you can't even specify it, NTP servers only have their own Chinese source hard coded into them...
Neither from GUI nor from CLI you can specify a time server path, say 216.239.35.0 or 162.159.200.123 or etc.
I don't like this kind of solution, I want to be in control

We goes a little bit off topic, but I also need a drop a few lines:
Two years ago, before pandemic started, before attacks on oil/gas lines happened, before issue with SolarWind, I wrote on this forum about our obligation as Security Admins / SysAdmins to stay away from any products from russia/china. Because this authority regimes using ANY TECHNOLOGY and ANY ABILITY as a weapon in a war against US and other democratic countries.
Many users reply something like “my friend, take a foil hat and no worry about!”.But let me to point on again and again: from 2018 russia and China would be more and more aggressive in their attacks, using multivectors attacks, complex hardware&software based attacks.
And popularity of very cheap/budget price of many network appliances & devices made in China - only one channel of many other to put their weapon in Your business infrastructure and in Your home.
P.S. from Jan 2024
Two Years ago I wrote this. No any reaction here on forum, even no one set “likel. But now You see russians attack to Colonel Pipeline, Pentagon internal lans, Chinas drones over the US military bases, russians drones over Bundeswer army’s buildings in Europe and oil/gas terminals in Norvay, lots of attacks on US government lans, russia help Iran and Hamas to attack Israel….
Ordinary US SysAdmins not bother too much about all of this (“so far away”, etc…), but here in EU we clearly see how 3-rd Wirld War happened RIGHT NOW and only matter of time when US receive power hit from russia and China…
Because may be too late. -
Opened #10404 a year or so ago for this topic - migration from ntpd to chronyd.
In an uninspired moment I set it to "Private" and can't change it to "Public", maybe @Netgate can help. -
Ha, I wondered why that was set private. Fixed.
-
@q54e3w said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
I'd rather have PTP personally.
How You to comment this sentence from official Chrony Docs:
2.12. Does chrony support PTP?
No, the Precision Time Protocol (PTP) is not supported as a protocol for synchronisation of clocks and there are no plans to support it.
It is a complex protocol, which shares some issues with the NTP broadcast mode.
One of the main differences between NTP and PTP is that PTP was designed to be easily supported in hardware (e.g. network switches and routers) in order to make more stable and accurate measurements. PTP relies on the hardware support. NTP does not rely on any support in the hardware, but if it had the same support as PTP, it could perform equally well.On Linux, chrony supports hardware clocks that some NICs have for PTP. They are called PTP hardware clocks (PHC). They can be used as reference clocks (specified by the refclock directive) and for hardware timestamping of NTP packets (enabled by the hwtimestamp directive) if the NIC can timestamp other packets than PTP, which is usually the case at least for transmitted packets. The ethtool -T command can be used to verify the timestamping support.
-
@sergei_shablovsky said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Sentence from official Chrony Docs:
On Linux, chrony supports hardware clocks that some NICs have for PTP. They are called PTP hardware clocks (PHC). They can be used as reference clocks (specified by the refclock directive) and for hardware timestamping of NTP packets (enabled by the hwtimestamp directive) if the NIC can timestamp other packets than PTP, which is usually the case at least for transmitted packets. The ethtool -T command can be used to verify the timestamping support.
I need to add some note about hardware timestamping: no possible to detect correct time correction delta in constantly asymmetrical link.
(For better understanding I will doing that on an example)Server A make a timestamp (t) and sending packet to Server B
Packet on the road within 30ms
Server B receive packet at time (t+30), make a timestamp and sending reply to Server A
Packet on the road within 70ms (because another route)
Server A receive reply packet with a totally delay (t+30ms+70ms = t+100ms) and Server A make decision that his time need to be corrected on 20ms (100ms / 2 ways - 30ms)But this is wrong decision (because as You see above one route are 30ms, other route are 70ms).
And no possible at all detecting this by statistics. So, in constantly asymmetrical link, the hardware NIC timestamp also not help to make great correction.
I am not sure is PTP v2 (IEEE-1588-2008) solving this problem?
-
 S Sergei_Shablovsky referenced this topic on
S Sergei_Shablovsky referenced this topic on
-
 S Sergei_Shablovsky referenced this topic on
S Sergei_Shablovsky referenced this topic on
-
@johnpoz said in Chrony, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
@sergei_shablovsky said in Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
**really outdated and vulnerable NTP”” need to be replaced.
What specific vulnerability are you talking about.. Just because NTP has been around long time - does not mean its not been kept up to date for security issues.
One of technics of NTP hacking is described here https://habr.com/ru/companies/ruvds/articles/505938/
(Please use translate.Google.com for reading.)
Only 25mins on Intel Core i5 ;) -
@sergei_shablovsky
Quite a thread resurrection you have there. Regrettably I have become unwilling to click on Russian links.That said, NTP is easily overlooked as it is a dull topic despite everyone relying on encryption these days.
In my view they called it Network Time Protocol for a reason - primarily it should be on your network, with only redundancy and sanity checks provided by the wider internet.
For years I have had one of these on my LAN:

Dedicated NTP time sources don't have to be expensive or be a hacky DIY job on a RPi.
 ️
️ -
@robbiett said in Chrony, PTP, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
Dedicated NTP time sources don't have to be expensive or be a hacky DIY job on a RPi.
And they're only $639.95!
I'll rely on NTP over the Internet.
-
@robbiett said in Chrony, PTP, Network Time Security (NTS, NTPsec) to replace unsecure/old NTP (ntpd):
hacky DIY job on a RPi.
But that's the fun part!

-
@jknott said
And they're only $639.95!
I'll rely on NTP over the Internet.
Ouch! Mine was 'only' £109 on eBay. When did they become so expensive??
Edit: The last one I purchased was 'just' £100 including expedited delivery, back in 2021:
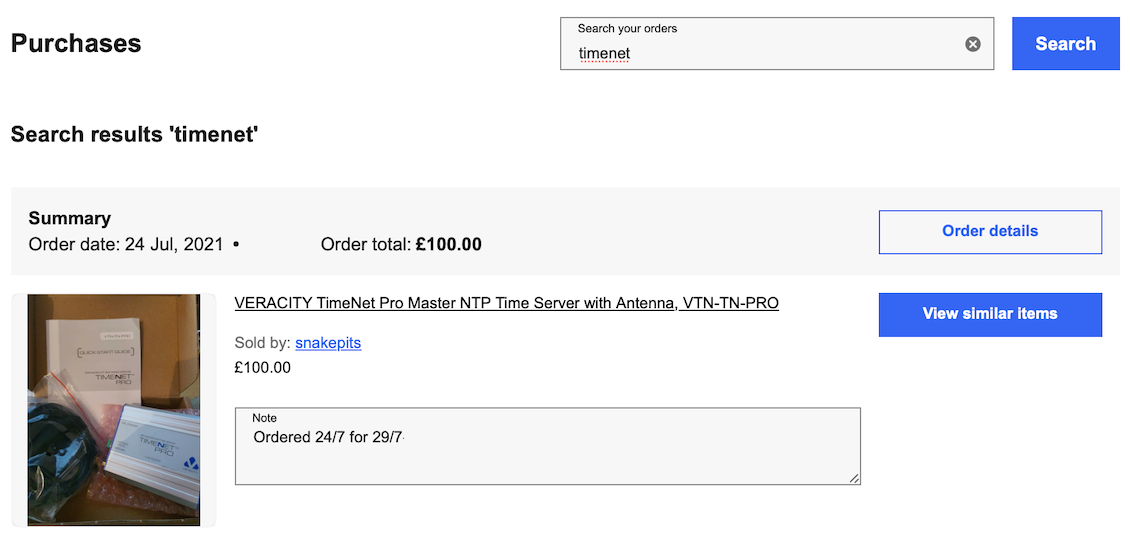
I guess I should have purchased a boatload of them.

 ️
️