Difficulty access the internet using my VLAN as an Guest Access Point
-
@jknott Oh...and I forgot...
If an attacker fails to break into your super hardened switch all they need to do is literally cut the physical cable that is the trunk cable, crimp it with a new RJ45 plug, and plug it into their own switch and feed it back. Unless you have the proper monitoring software on your trunk line you wouldn't know.
-
if all you're doing is setting up a VLAN for friends and family I don't see where your concerns are. VLAN's are fine your purpose.
VLAN's are adequate for creating private networks
VLAN's should not be relied upon for security if that's what you're looking for. -
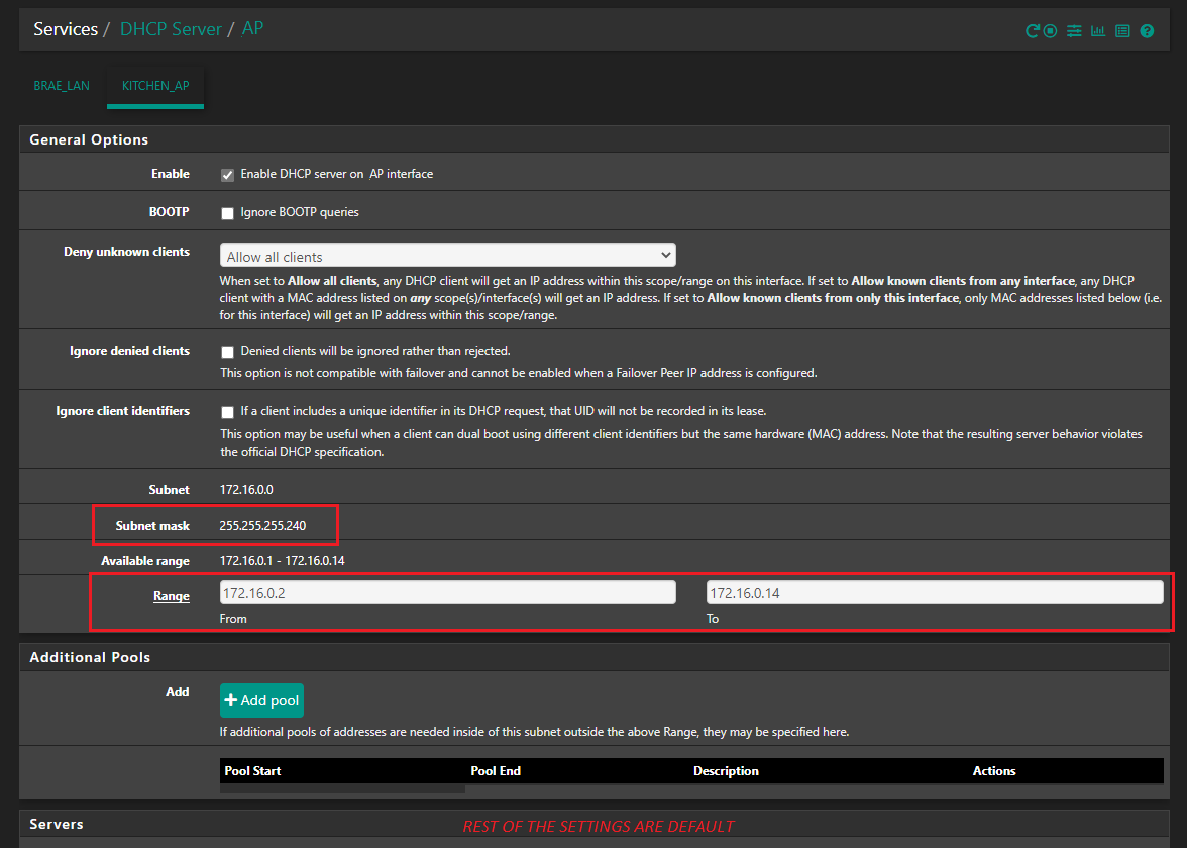
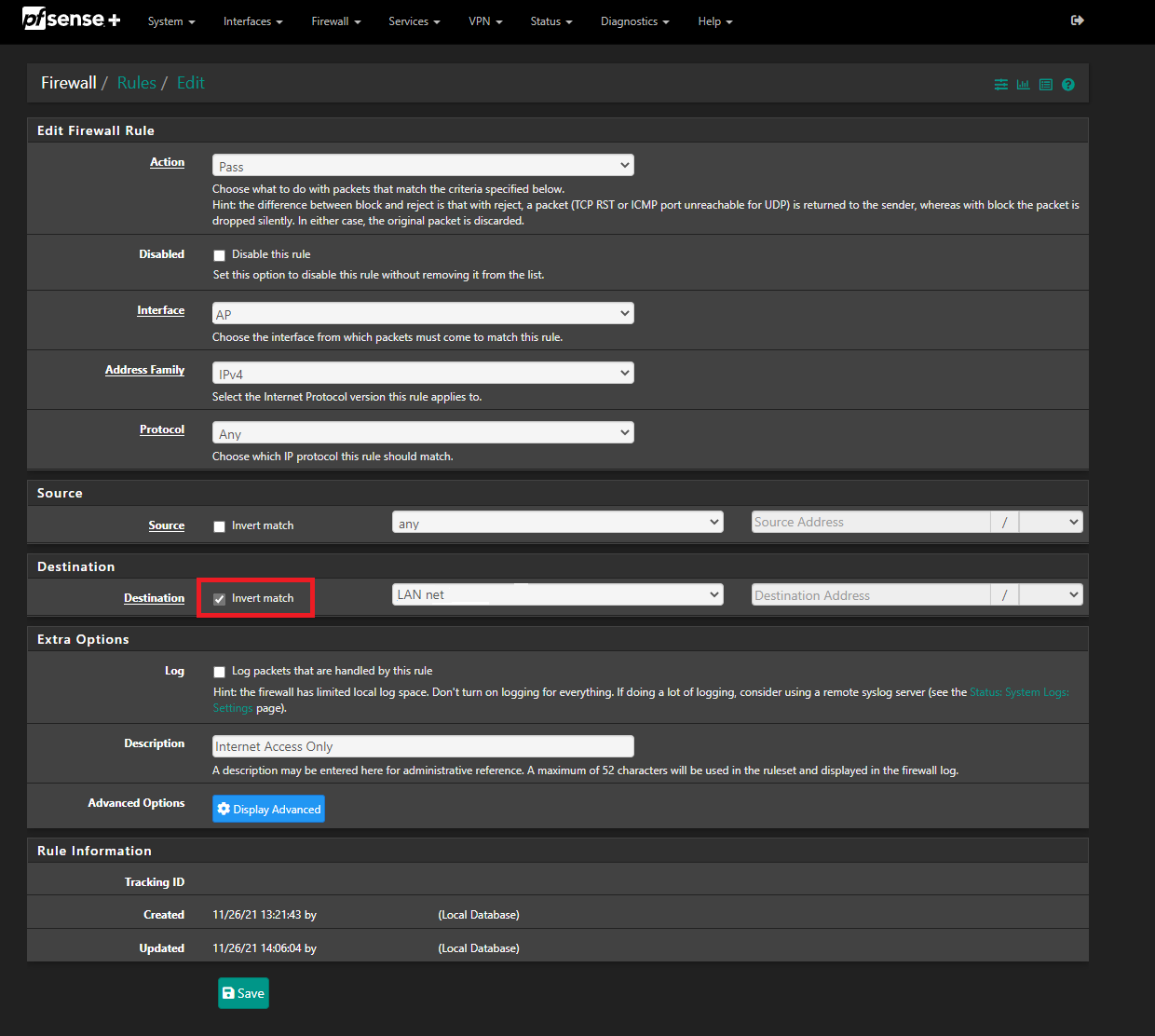
@cxcmax To me, your setup seems awkward...why not put an guest AP device that does its own DHCP and let your pfSense do DNS? Seems simpler than to have a static IP for your AP then trying to use the vlan as DHCP server.
-
@stephenw10 alternatively why don't you point me to a reliable source that states VLANs are a viable security solution.
-
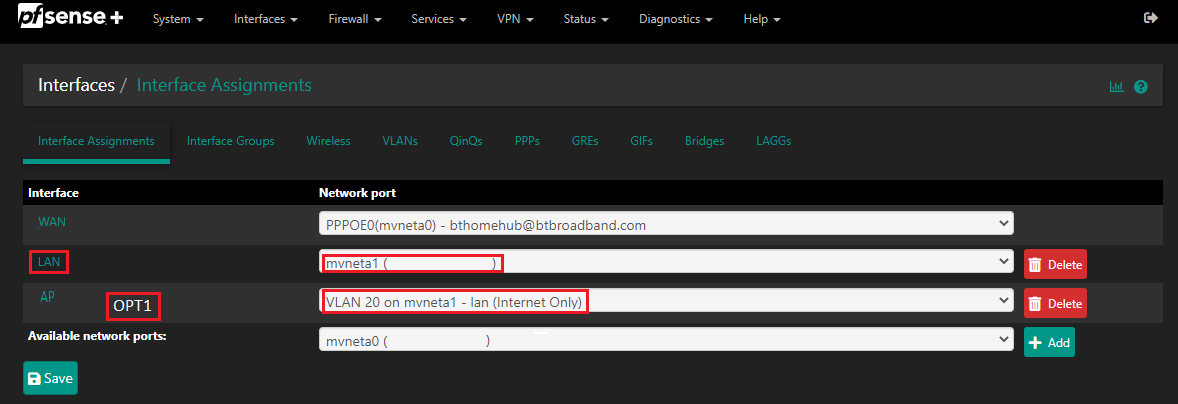
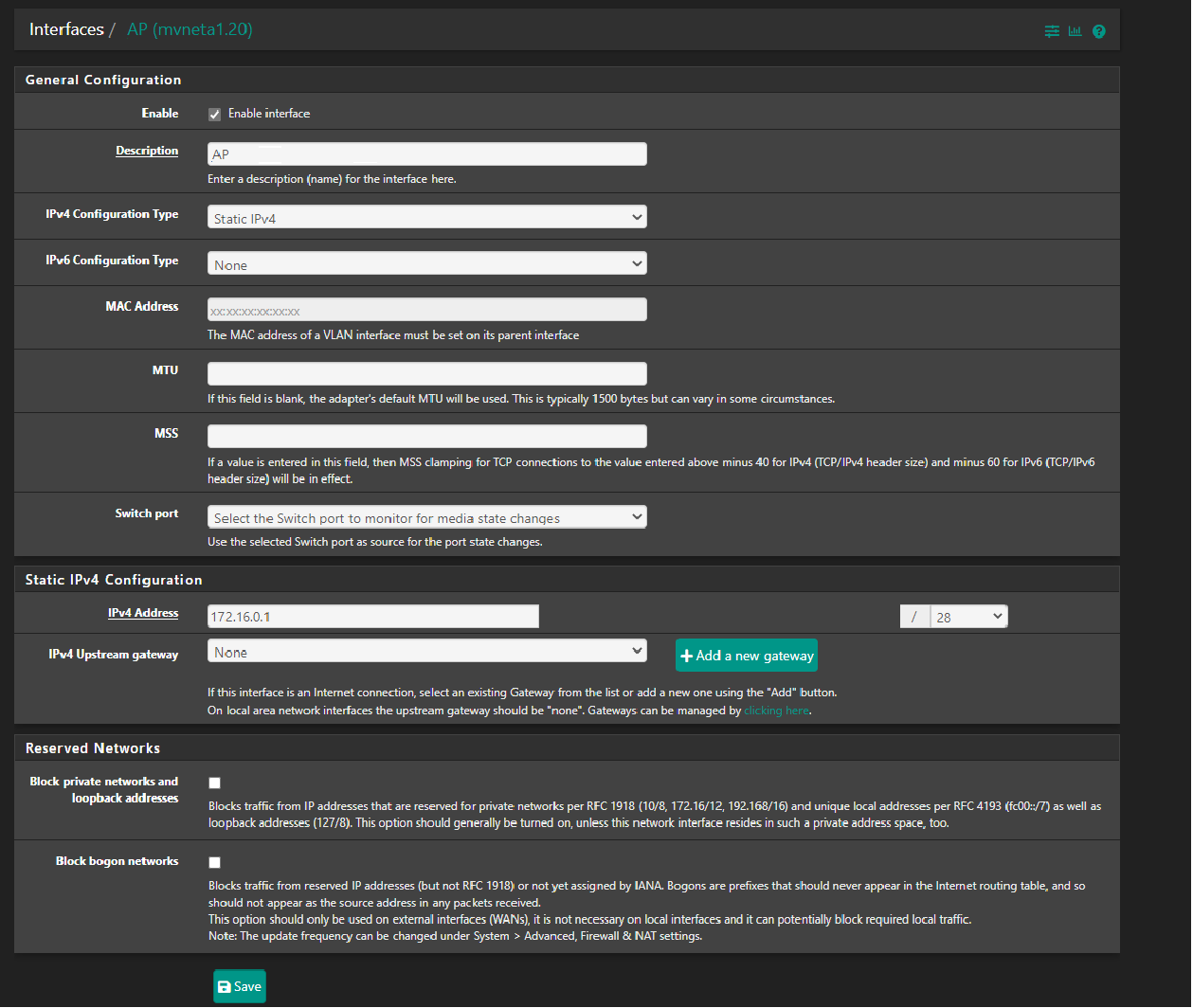
@nollipfsense all APs should use static IP. This will allow you to configure the firewall to block access to the management interface. It will also allow you to manage APs with management software.
-
@jknott said in Difficulty access the internet using my VLAN as an Guest Access Point:
For an unmanaged switch to not pass a VLAN frame, it would have to check the Ethertype and then specifically drop VLAN frames. It seems to me that's a lot to ask of a dumb switch. And to what end?
Indeed it would have to do exactly that. When I have seen this it's because what appears to be a 'dumb' switch is in fact a managed switch IC that is simply configured as a single VLAN. As I understand it (and I won't pretend to have done an exhaustive study here!) most small unmanaged switches are built like that because those are the available switch ICs. But when configured as port based VLAN they will pass all tagged traffic.
I have most commonly hit this as a problem when people try to re-use some combo device as a switch. So a router/AP/switch style device. Typically those are configured in 802.1q mode to segregate ports but there's no way to know until you test it since that is not exposed to the user interface.
Anyway having wasted hours or my life trying to solve a problem only to discover there was an additional 'dumb' switch in the connection I hadn't been told about I can only advise; do not assume tagged traffic will pass.
Steve
-
@papdee said in Difficulty access the internet using my VLAN as an Guest Access Point:
@stephenw10 alternatively why don't you point me to a reliable source that states VLANs are a viable security solution.
I think you will need to define 'security solution' in that context.
Typically VLANs are used to segregate traffic that is using the same physical connection. If that's for security reasons then it could be considered a security solution IMO.
You have suggested it's possible, trivial even, to 'hop' VLANs which I understand to mean a host on one VLAN is able to access a resource on a different VLAN. Maybe I've misunderstood what you're saying. I'm not aware of any way to do that without re-configuring a switch in between but I'd love to learn if it is.Steve
-
????
What do your posts have to do with mine?
I'm well aware of how VLANs work. I use one here for my guest WiFi, have set some up for business customers and am a Cisco CCNA. -
@jknott sorry fat fingers. should have been the one above you
-
@papdee said in Difficulty access the internet using my VLAN as an Guest Access Point:
- At the cable level VLAN hopping is straightforward. There is nothing to mitigate this.
As with any computer system, if the attacker has physical access to the relevant trusted hardware, it's game over for security. There is nothing VLAN-specific about this issue.
- At the switch level there are various ways to hop a VLAN. Most switches fresh out of their packing box will allow you to hop the VLAN. You must to take the effort to harden the switch. Even though you have spent days maybe weeks hardening your switch any security bugs in the software makes your hardening completely useless. For e.g. Some Cisco switches have a security bug in the HTTP server that is suscetiple to an OB attack giving the attacker executive privileges. This attack is easy to execute using simple telnet and a python script.
As with any computer system, misconfiguration or security bugs will hose you. There is nothing VLAN-specific about this issue.
- Finally there is the human error aspect. You can spend forever hardening your switch but at some point you are going to need to take that little paperclip bend it straight and do a full blown reset on the switch. At which point you forget you have just unhardened your switch.
As with any computer system, human error will hose you. There is nothing VLAN-specific about this issue.
-
These are worthy topics for discussion but we are derailing @cxcmax's thread

I suggest moving to a new thread in off-topic to discuss VLANs in general. Thanks.
Steve