Routing a specific IP through Wan instead of VPN
-
@ace-1 said in Routing a specific IP through Wan instead of VPN:
Should my rule be at the top of the LAN rule order or am I not even close.
Exactly. But there is something to consider.
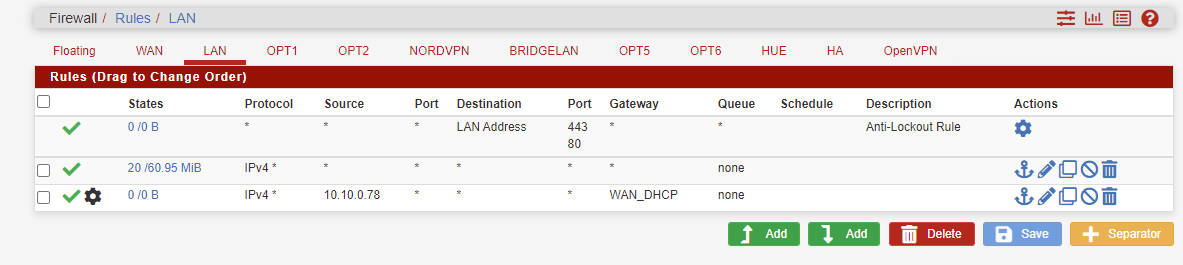
By stating a gateway, the rule directs the whole traffic for the source device to the WAN gateway. Hence the device is no more able to access any other local subnets, which I assume, is desired.
So you have to care that the policy routing rule is only applied to upstream traffic to the internet, but not for internal destinations.
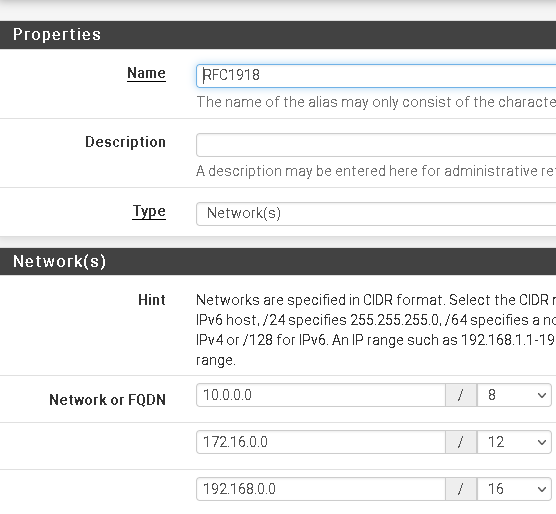
A good way to achieve this by setting the destination to invert and use an RFC 1918 alias.
To do so, you have first to add an alias of type networks, call it RFC1918, and add all private network to it.
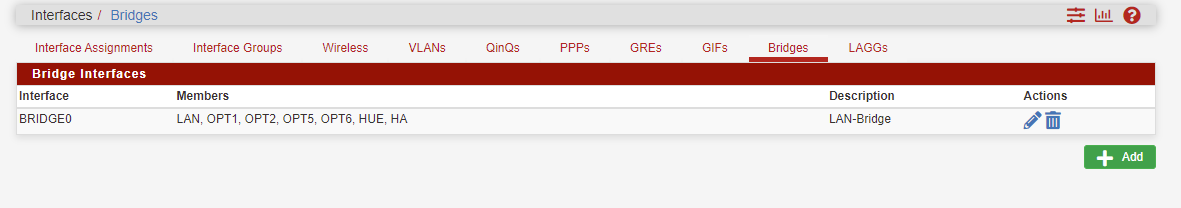
Looks like this on my pfSense:
The edit the rule, check invert at destination, select "single host or alias" and enter RFC1918 in the next field.
So this means, the rule matches to any traffic, but the private networks. Hence it is only applied to public destinations.BTW: Really wondering, why you need all your internal networks bridged.
-
You made a great point, this host is in my home theater so I actually need it to talk with 2 different windows computers that have all my media. So I want this host to be able to go through the WAN without running into problems and still be able to talk with different sources under the BridgeLAN plus protect my network.
I moved the rule up and I still see the VPN IP, does the Lan interface have to taken out of the Bridge0 interface.
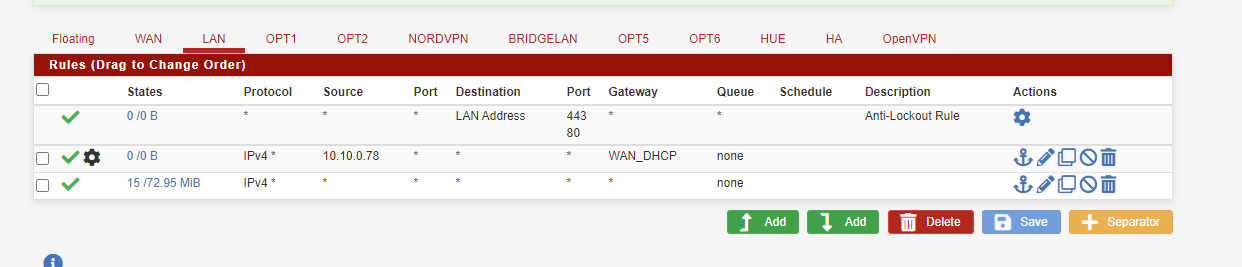
-
@ace-1
Consider to delete existing states. Changing rules does not affect existing connection.Also consider that floating rules with Quick have priority over interface rules.
-
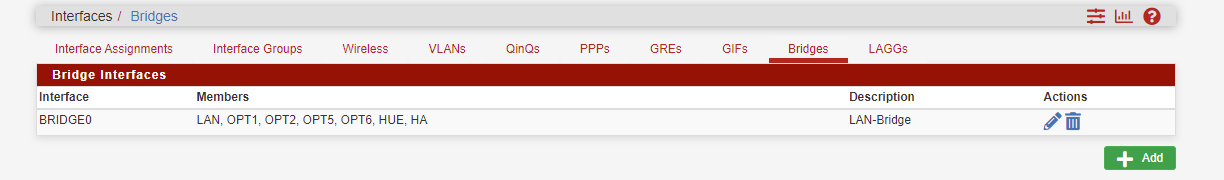
I was just bridging everything because I have very little knowledge with pfsense and this type of firewall. I wanted everything to be able to talk with each other before I started to play with all the settings.
I have 2 routers, and 2 unfi AP's behind the firewall plus many raspberry4 pi's, computers, IOT's devices used for Home Assistant. I really don't know how to split everything up so I just put them on one big network until I have a grip on how the rules and services work.
My end goal is to split everything on different networks as per each interfaces and still be able to talk with each other and only give certain devices WAN access.
Any suggestions or plans of attack are greatly accepted.
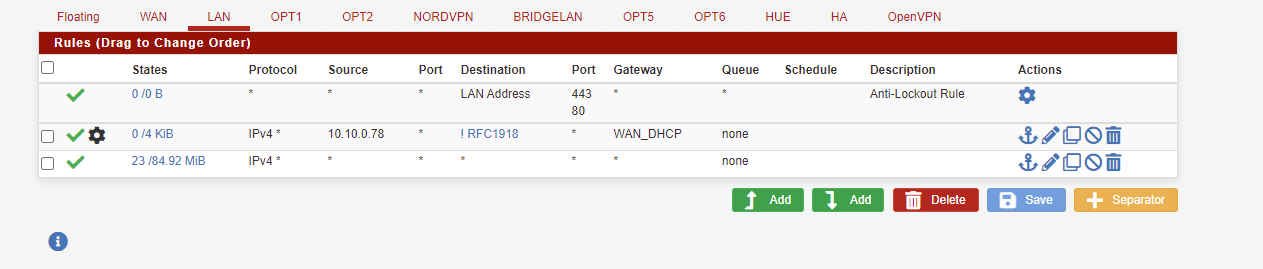
? Once I create the Alias you told me to create do I change the destination and invert under my original rule I created for the host?
Like below
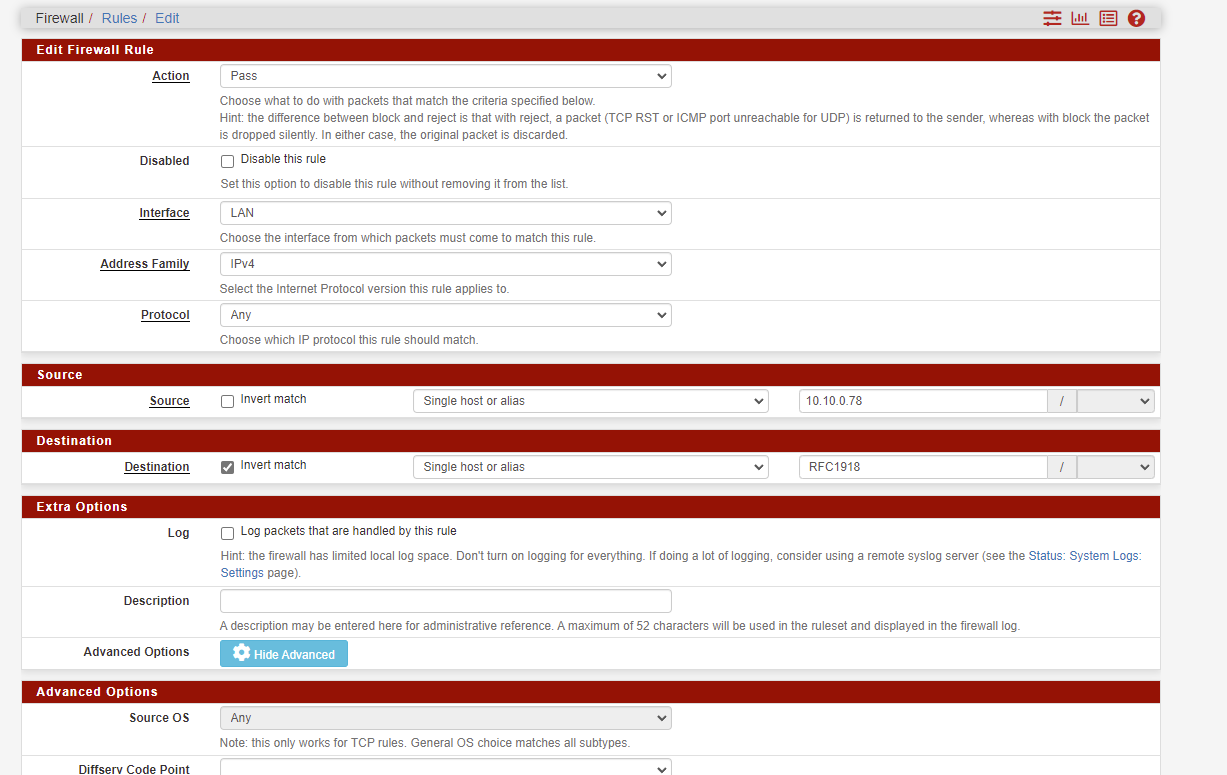
-
@ace-1 said in Routing a specific IP through Wan instead of VPN:
? Once I create the Alias you told me to create do I change the destination and invert under my original rule I created for the host?
Yes.
Bridging interfaces only makes sense to me if you need broadcasts between the devices and for some of your use purposes this might be necessary in fact.
But consider, having all interfaces bridged with a lot of devices included may also produce much brodcast noise. -
Are you saying to delete the anti lockout rule and the talk with any rule for the LAN?
-
@ace-1 said in Routing a specific IP through Wan instead of VPN:
Are you saying to delete the anti lockout rule and the talk with any rule for the LAN?
No, you simply add this rule to the top of the rule set, so that it is applied before the pass any rule.
You cannot go above the anti-lockout rule. This one stays on the top position. -
-
@ace-1
Yes, looks well. -
I am still seeing my VPN IP and I am not sure why. My LAN interface still is in the BridgeLAN interface which directs traffic through the VPN.
But what i understand is that the rule created for the host to go out the WAN should take care of that particular host.
Does that make sense.
-
@ace-1
Yes, with that rule the source IP is directed to WAN gateway for all destinations not included in the alias.Did you delete the respective states of the source device?
Do you have floating rules?
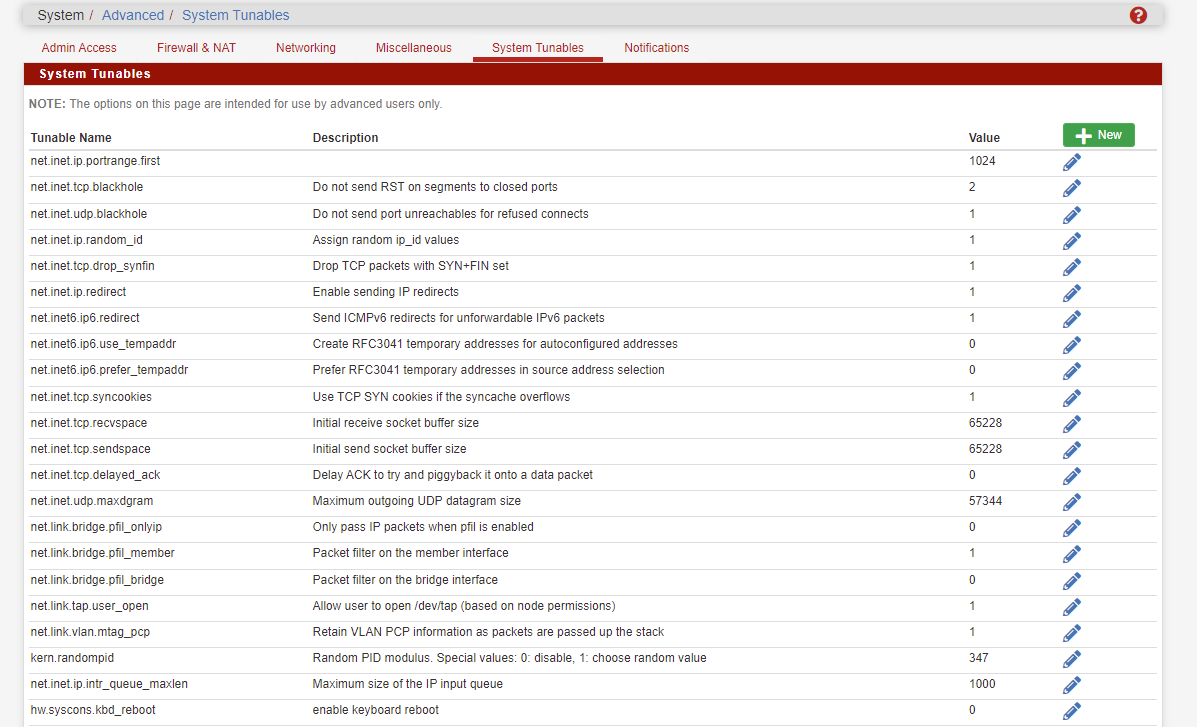
Do you have added an interface group?In System > Advanced > System Tunables check the value of "net.link.bridge.pfil_member". It should be 1.
"net.link.bridge.pfil_bridge" should be 0, or at least ensure that a rule on the bridge is not applied to the traffic from the source device. -
Can I just Reset all states? or will this miss things up?
-
@ace-1
This is my floating rukles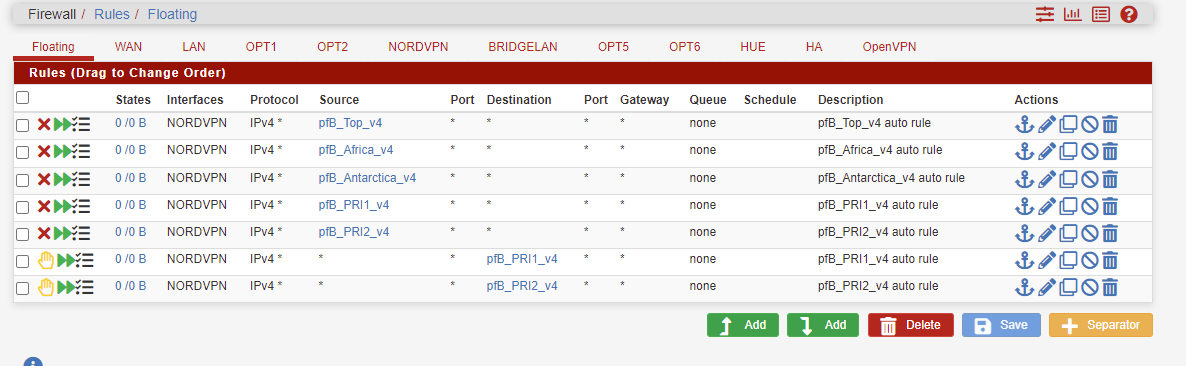
-
Before I forget.....Thank you so much for all the help
Answers to your questions
Did you delete the respective states of the source device? YES
Do you have floating rules?YES Look below
Do you have added an interface group? What should I be adding to the interface group?
In System > Advanced > System Tunables check the value of "net.link.bridge.pfil_member". It should be 1.
"net.link.bridge.pfil_bridge" should be 0, or at least ensure that a rule on the bridge is not applied to the traffic from the source device.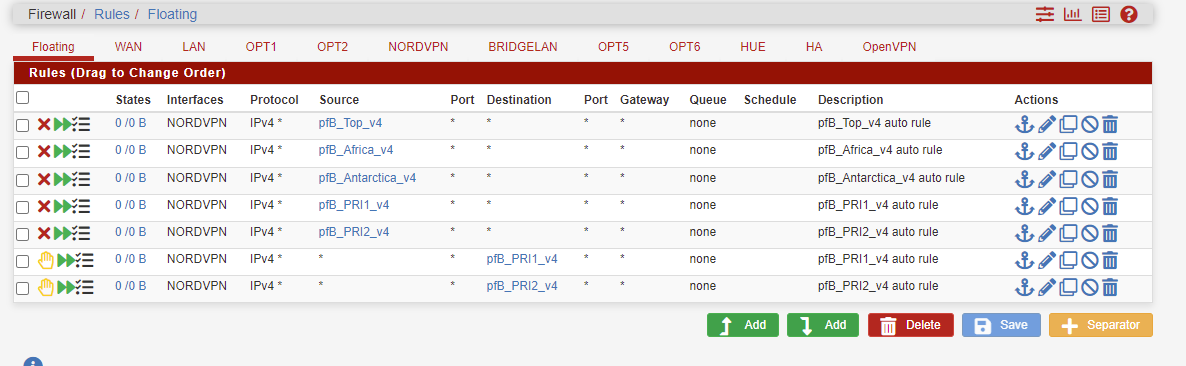
-
@ace-1
If the device still go out to the VPN the policy routing rule is obviously not applied.Are you sure the packets from the stated device come in on LAN?
You can sniff the traffic on LAN with Diagnostic > Packet Capture to check.For further investigation you should enable logging in all your firewall rules. However, it is required that you set a description for the rule to get a useful feedback in the log.
Then initiate an upstream traffic on the device and check the firewall log after to see which rule passed it. -
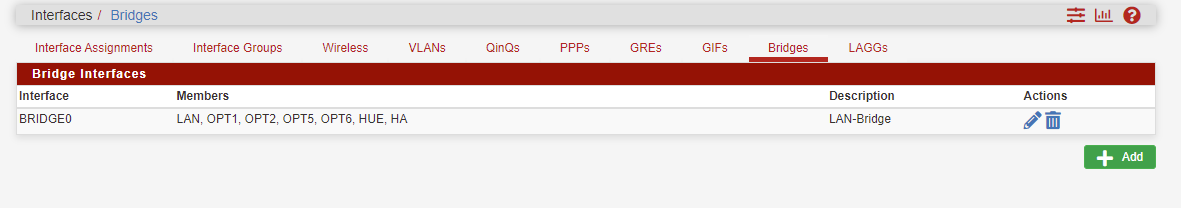
Ok, I have taken the LAN interface out of the BridgeLAN interface.
Before
After
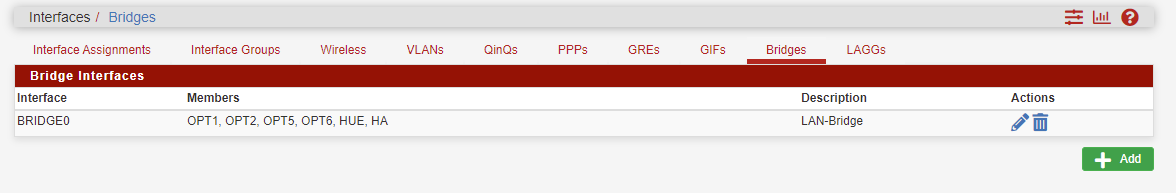
I lost connection because my computer was attached to the LAN...lol
Checked the host that we orginally were trying to get to the WAN and now I see my ISP IP like I wanted but now doesn't that mean that every other host on the land is now exposed to the WAN instead of going through the VPN?
-
@ace-1
No, routing should have nothing to do with bridging.
When you're talking about the VPN, I assume, it's the VPN provider who pushes the default route to you. This is applied to any upstream traffic, as long as it isn't permitted by a policy routing rule which state another gateway. -
So what finally worked.
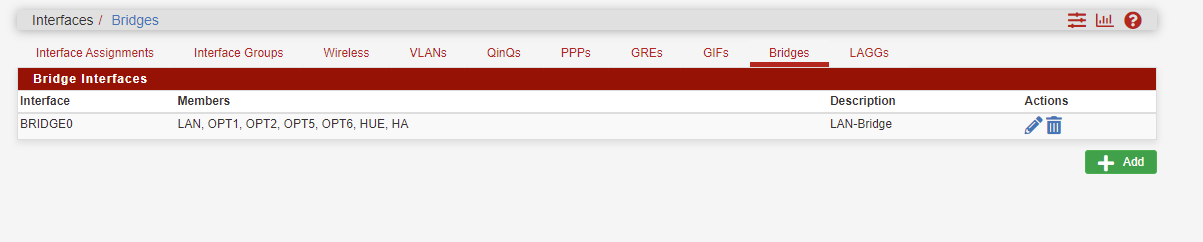
The Pfsense firewall has 7 interfaces, all bridged under 1 interface called BridgeLAN with BridgeLAN running the DHCP server. I wanted to let only 1 host out the internet without VPN because of GEOIP apps that requiring my country location.
viragomann gave me great direction any I tried his rule direction on every interfaces, what I found out that the BridgeLAN VPN rules superseded all other rule entrys because all the other interfaces are bridged inside the BridgeLAN Interfaces .
Like this
So I created the same rule to open that host above the VPN rule in the BridgeLAN rule and it worked as I wanted.
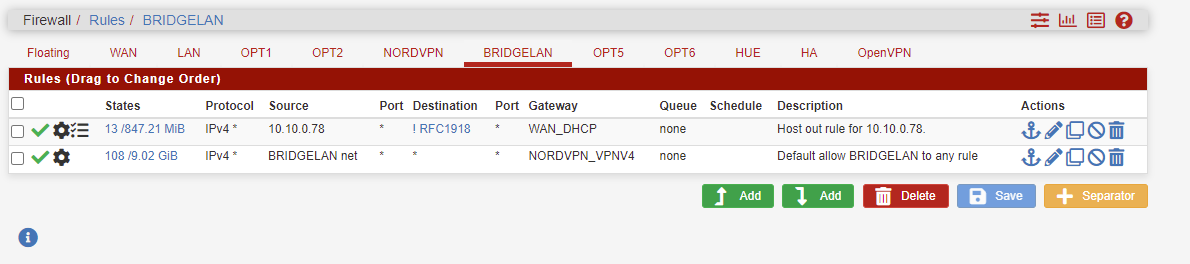
I know there is better ways to do this, and I will take any advice.
Thanks Again viragomann