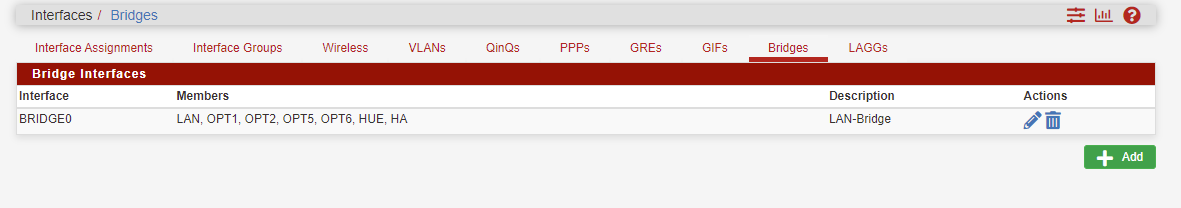
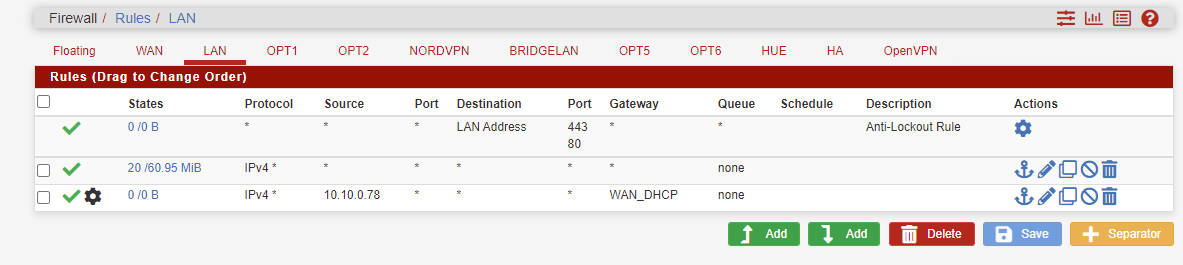
Routing a specific IP through Wan instead of VPN
-
@ace-1
Yes, looks well. -
I am still seeing my VPN IP and I am not sure why. My LAN interface still is in the BridgeLAN interface which directs traffic through the VPN.
But what i understand is that the rule created for the host to go out the WAN should take care of that particular host.
Does that make sense.
-
@ace-1
Yes, with that rule the source IP is directed to WAN gateway for all destinations not included in the alias.Did you delete the respective states of the source device?
Do you have floating rules?
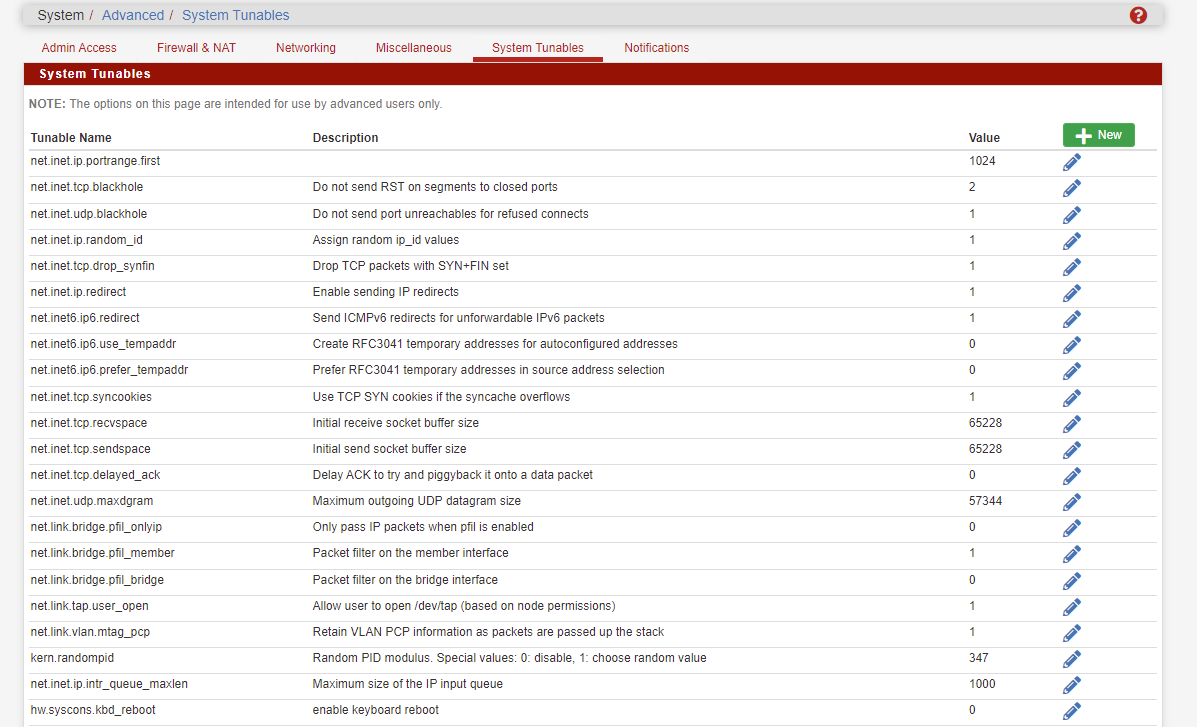
Do you have added an interface group?In System > Advanced > System Tunables check the value of "net.link.bridge.pfil_member". It should be 1.
"net.link.bridge.pfil_bridge" should be 0, or at least ensure that a rule on the bridge is not applied to the traffic from the source device. -
Can I just Reset all states? or will this miss things up?
-
@ace-1
This is my floating rukles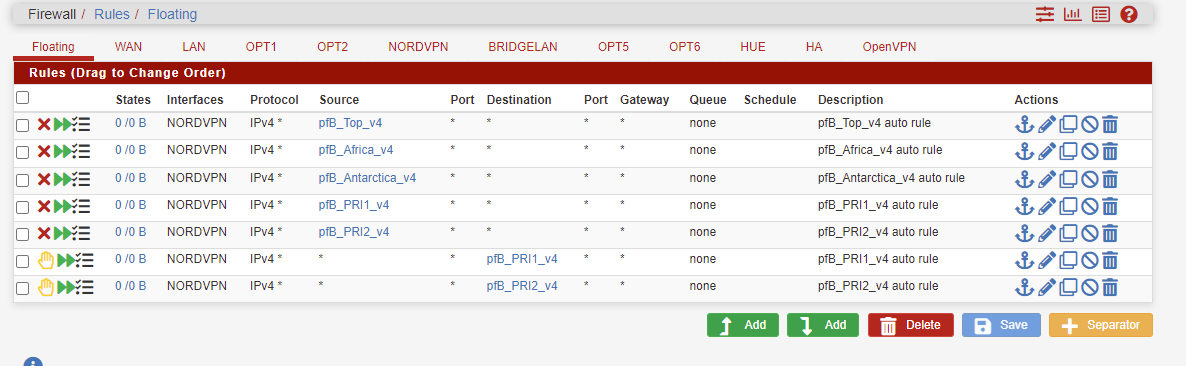
-
Before I forget.....Thank you so much for all the help
Answers to your questions
Did you delete the respective states of the source device? YES
Do you have floating rules?YES Look below
Do you have added an interface group? What should I be adding to the interface group?
In System > Advanced > System Tunables check the value of "net.link.bridge.pfil_member". It should be 1.
"net.link.bridge.pfil_bridge" should be 0, or at least ensure that a rule on the bridge is not applied to the traffic from the source device.
-
@ace-1
If the device still go out to the VPN the policy routing rule is obviously not applied.Are you sure the packets from the stated device come in on LAN?
You can sniff the traffic on LAN with Diagnostic > Packet Capture to check.For further investigation you should enable logging in all your firewall rules. However, it is required that you set a description for the rule to get a useful feedback in the log.
Then initiate an upstream traffic on the device and check the firewall log after to see which rule passed it. -
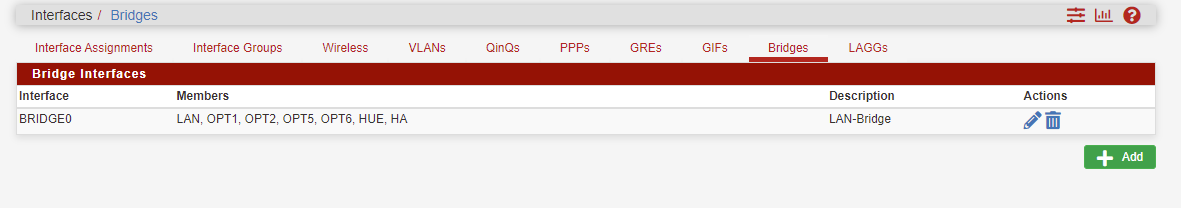
Ok, I have taken the LAN interface out of the BridgeLAN interface.
Before
After
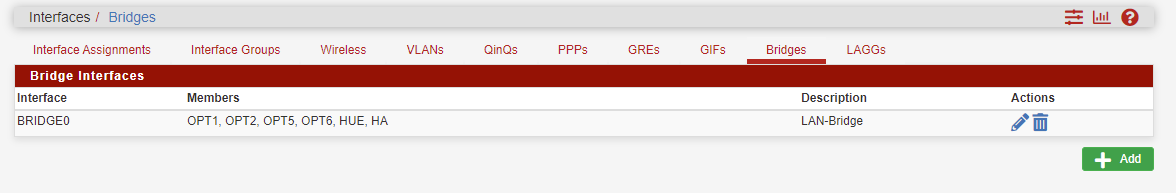
I lost connection because my computer was attached to the LAN...lol
Checked the host that we orginally were trying to get to the WAN and now I see my ISP IP like I wanted but now doesn't that mean that every other host on the land is now exposed to the WAN instead of going through the VPN?
-
@ace-1
No, routing should have nothing to do with bridging.
When you're talking about the VPN, I assume, it's the VPN provider who pushes the default route to you. This is applied to any upstream traffic, as long as it isn't permitted by a policy routing rule which state another gateway. -
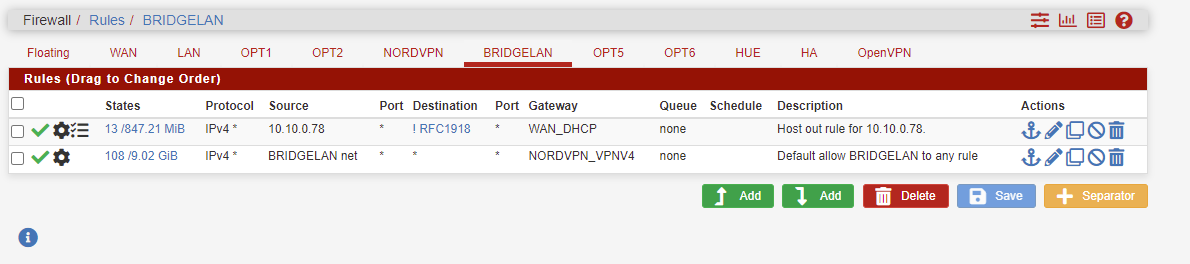
So what finally worked.
The Pfsense firewall has 7 interfaces, all bridged under 1 interface called BridgeLAN with BridgeLAN running the DHCP server. I wanted to let only 1 host out the internet without VPN because of GEOIP apps that requiring my country location.
viragomann gave me great direction any I tried his rule direction on every interfaces, what I found out that the BridgeLAN VPN rules superseded all other rule entrys because all the other interfaces are bridged inside the BridgeLAN Interfaces .
Like this
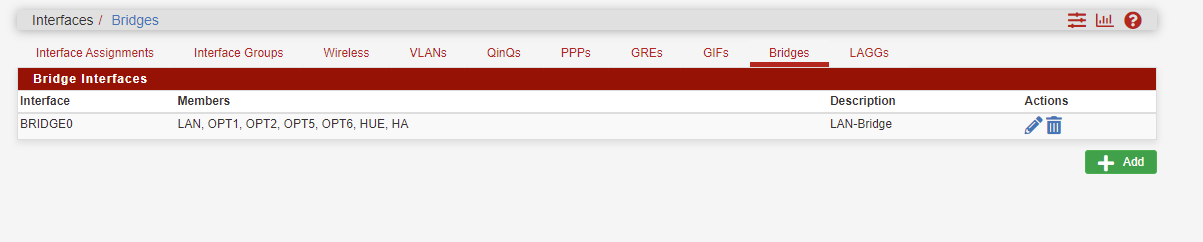
So I created the same rule to open that host above the VPN rule in the BridgeLAN rule and it worked as I wanted.
I know there is better ways to do this, and I will take any advice.
Thanks Again viragomann