Problem with snapshot 3/31 16:19:49
-
@jimp You got it thanks for the help
here is your request this was the original settings, I have tried to delete the one line however it re adds
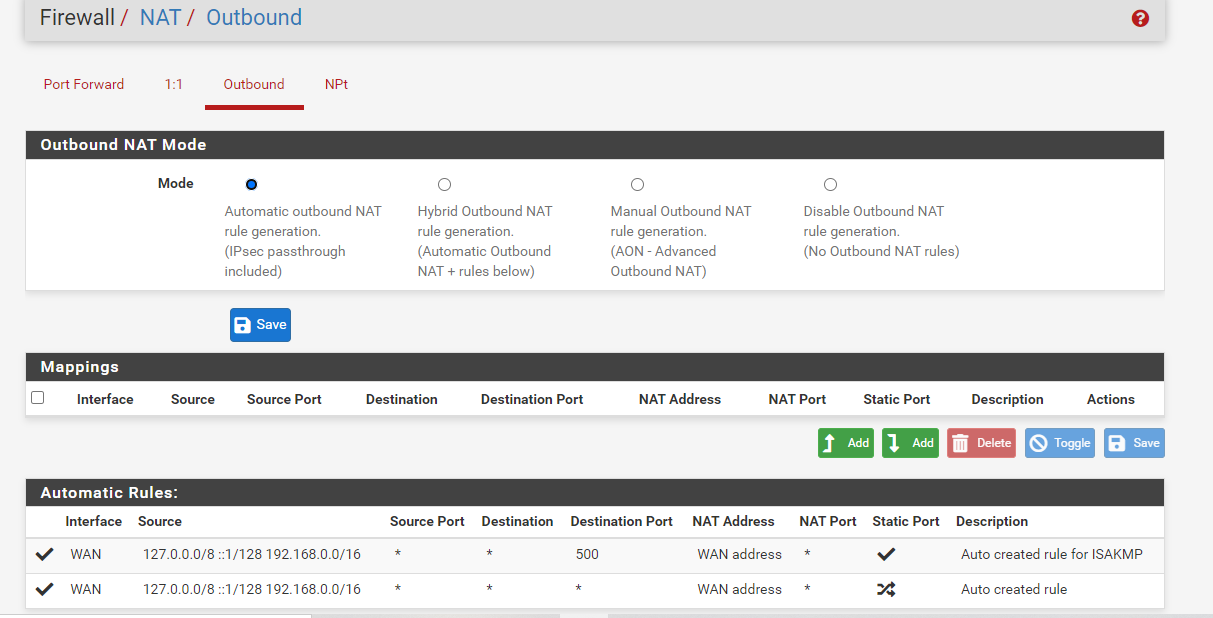
Outbound NAT rules (automatic)
Subnets to NAT
tonatsubnets = "{ 127.0.0.0/8 ::1/128 192.168.0.0/16 }"
nat on $WAN inet from $tonatsubnets to any port 500 -> 64.113.111.129/32 static-port
nat on $WAN inet6 from $tonatsubnets to any port 500 -> (mvneta0) static-port
nat on $WAN inet from $tonatsubnets to any -> 64.113.111.129/32 port 1024:65535
nat on $WAN inet6 from $tonatsubnets to any -> (mvneta0) port 1024:65535TFTP proxy
rdr-anchor "tftp-proxy/*"
NAT Inbound Redirects
rdr on mvneta1 inet proto { tcp udp } from 192.168.0.0/16 to any port $DNS -> 192.168.1.1
no nat on mvneta1 inet proto tcp from (mvneta1) to 192.168.0.0/16
nat on mvneta1 inet proto tcp from 192.168.0.0/16 to 192.168.1.1 port $DNS -> (mvneta1)rdr on mvneta1 inet6 proto { tcp udp } from any to any port $DNS -> ::1
rdr on mvneta1 inet proto udp from 192.168.0.0/16 to any port 123 -> 192.168.1.1
no nat on mvneta1 inet proto tcp from (mvneta1) to 192.168.0.0/16
nat on mvneta1 inet proto tcp from 192.168.0.0/16 to 192.168.1.1 port 123 -> (mvneta1)rdr on mvneta1 inet6 proto udp from any to any port 123 -> ::1
Setup Squid proxy redirect
rdr pass on mvneta1 inet proto tcp from any to !(mvneta1) port 80 -> 127.0.0.1 port 3128
rdr pass on mvneta1 inet proto tcp from any to !(mvneta1) port 443 -> 127.0.0.1 port 3129 -
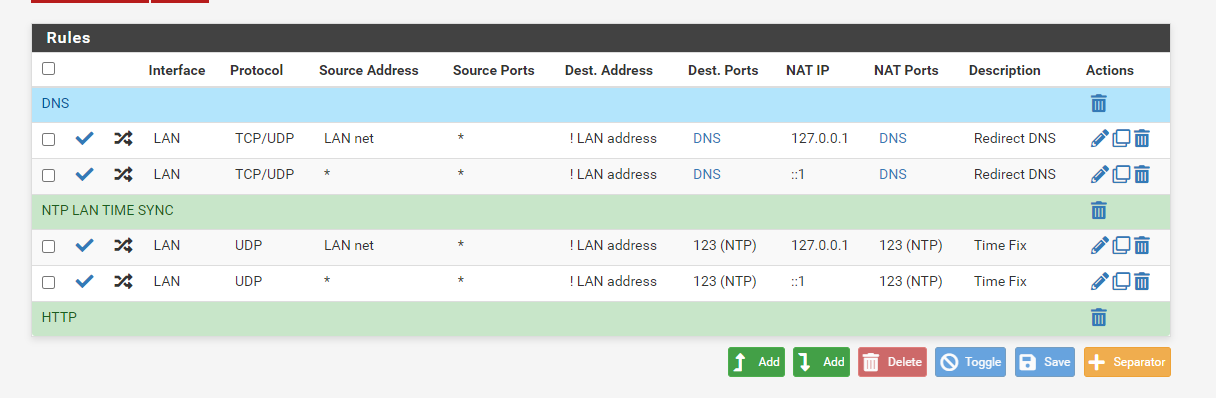
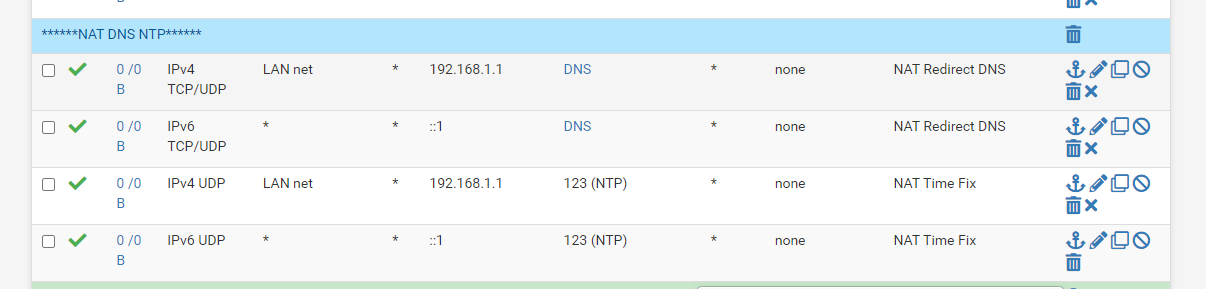
This is my NAT for DNS and NTP
I force them to use the firewall
This setting has worked for some time now I get time from the firewall no matter what wan ip address a device requests for NTP. I had issues with time being jumped 15-20 mins without this nat setting for NTP, no clue why so I added a rule that let the firewall handle all NTP requests, after that no issues with time jumps
-
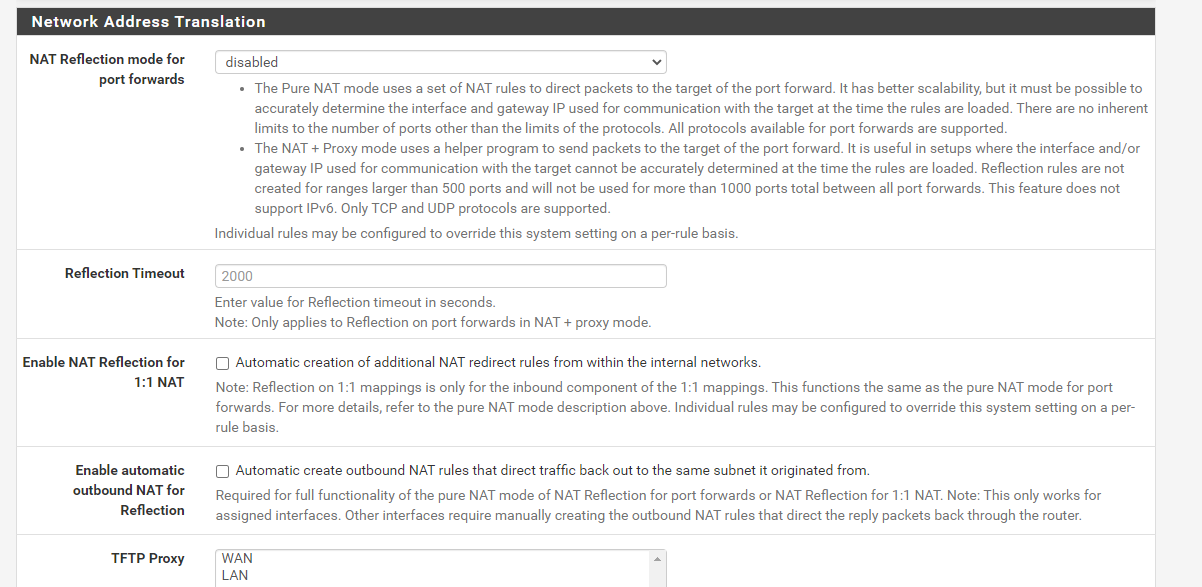
Do you have NAT reflection enabled globablly or on those rules? If so, disable it.
-
-
There is also a per-rule option on the individual port forwards. Is it enabled there?
-
Also your port forward target should really be
127.0.0.1and not192.168.1.1, assuming192.168.1.1is the LAN address of the firewall. -
Firewall rules
-
@jimp said in Problem with snapshot 3/31 16:19:49:
127.0.0.1
correct to loopback address
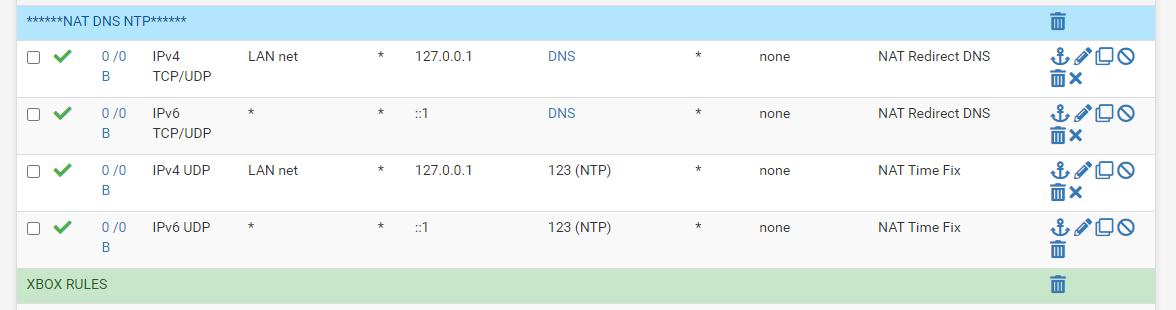
filter reload failed at same point as before with loopback address
-
Did you reboot after making that change? Once you get the error you have to reboot to know if it's fixed. Also check and see if those
no nat onrules are still present. -
I have to wait for 2 hours to do a reboot I am at work and the firewall must be up for 2 hours. I have changed the NTP and DNS to use the loopback 127, the no nat rules still show in debug if you delete them they return. Thanks I will reboot at 11:10am
-
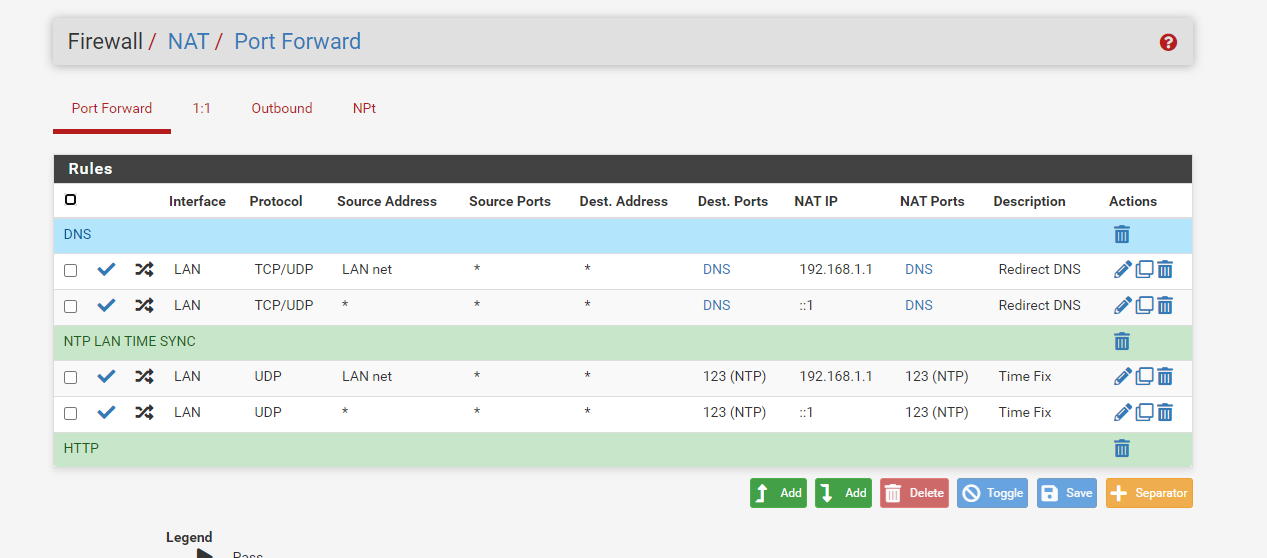
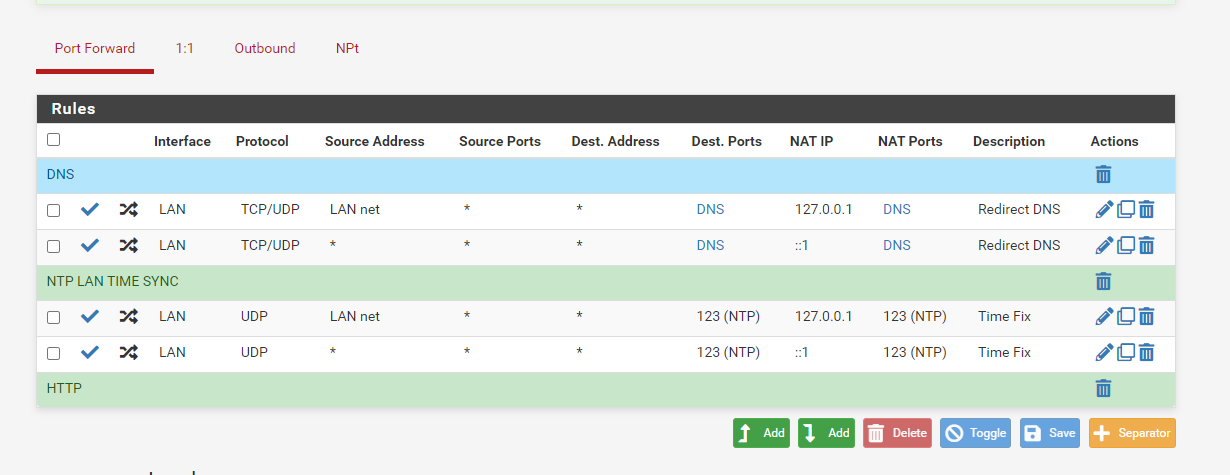
OK, I see the real source of your duplicate rules now and I can replicate it here. Your destination on those port forwards is Any and it should not be set to that. You should set that to ! LAN address (so check the Invert Match box for the destination and then set the destination to LAN Address)
As described in the docs:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html -
-
That looks good, if you look in
/tmp/rules.debugnow you shouldn't see thoseno nat onrules under therdrrules for those port fowards. If that is the case, you should be in good shape after a reboot. -
They are gone now, I wonder why that worked for so long before this update.
Outbound NAT rules (automatic)
Subnets to NAT
tonatsubnets = "{ 127.0.0.0/8 ::1/128 192.168.0.0/16 }"
nat on $WAN inet from $tonatsubnets to any port 500 -> 64.113.111.129/32 static-port
nat on $WAN inet6 from $tonatsubnets to any port 500 -> (mvneta0) static-port
nat on $WAN inet from $tonatsubnets to any -> 64.113.111.129/32 port 1024:65535
nat on $WAN inet6 from $tonatsubnets to any -> (mvneta0) port 1024:65535TFTP proxy
rdr-anchor "tftp-proxy/*"
NAT Inbound Redirects
rdr on mvneta1 inet proto { tcp udp } from 192.168.0.0/16 to !192.168.1.1 port $DNS -> 127.0.0.1
rdr on mvneta1 inet proto udp from 192.168.0.0/16 to !192.168.1.1 port 123 -> 127.0.0.1Setup Squid proxy redirect
rdr pass on mvneta1 inet proto tcp from any to !(mvneta1) port 80 -> 127.0.0.1 port 3128
rdr pass on mvneta1 inet proto tcp from any to !(mvneta1) port 443 -> 127.0.0.1 port 3129UPnPd rdr anchor
rdr-anchor "miniupnpd"
-
Thank you for your help with this and all you do.
-
The update has a problem with duplicate rules. We're still working on a fix, but in the meantime you can work around it by eliminating the duplicate rules. Most people get them from reflection + VIPs, but in your case it was port forwards with a destination of Any.
I'm surprised those port forwards worked well at all, they would have been looping traffic around a bit since even a query sent to the firewall would be caught and then redirected to ... the firewall. Unnecessarily. Port forwards for a destination of Any have a long history of problems.
See also:
-
The update forced me to use a more efficient configuration, Amazing, glad I waited it out. On a side note we are talking about efficiency in algorithm complexity in Java class this week. Again, I never thought about having to program dynamic conditional expressions for user configuration errors until today. Example if users programs routers ip in nat default to loopback, and or throw exception. Easier said then done I am sure. The routers Ip can be different, and each Nat rule can be different because of the packages in use.
-
This fixed it however i-cap will not start or clamAV any longer all errors for filter issues are gone and filter shows states logs now again.
-
@jonathanlee yes I have many packages that dont start now
avahi
lldpd
ntopng
ssftlowd
vnstatd/etc/rc.packages: The command '/usr/local/etc/rc.d/avahi-daemon.sh stop' returned exit code '2', the output was '/usr/local/etc/rc.d/avahi-daemon.sh: 17: Syntax error: "}" unexpected'
/rc.start_packages: The command '/usr/local/etc/rc.d/ntopng.sh stop' returned exit code '2', the output was '/usr/local/etc/rc.d/ntopng.sh: 29: Syntax error: "}" unexpected' -
Apr 1 11:21:13 (squid-1) 86303 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:24 (squid-1) 26626 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:36 (squid-1) 50467 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:47 (squid-1) 53928 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:59 (squid-1) 56555 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:10 (squid-1) 59214 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:22 (squid-1) 63577 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:34 (squid-1) 78058 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:45 (squid-1) 91402 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:47 php-fpm 402 /pkg_edit.php: Configuration Change:This is my only issue now