Problem with snapshot 3/31 16:19:49
-
-
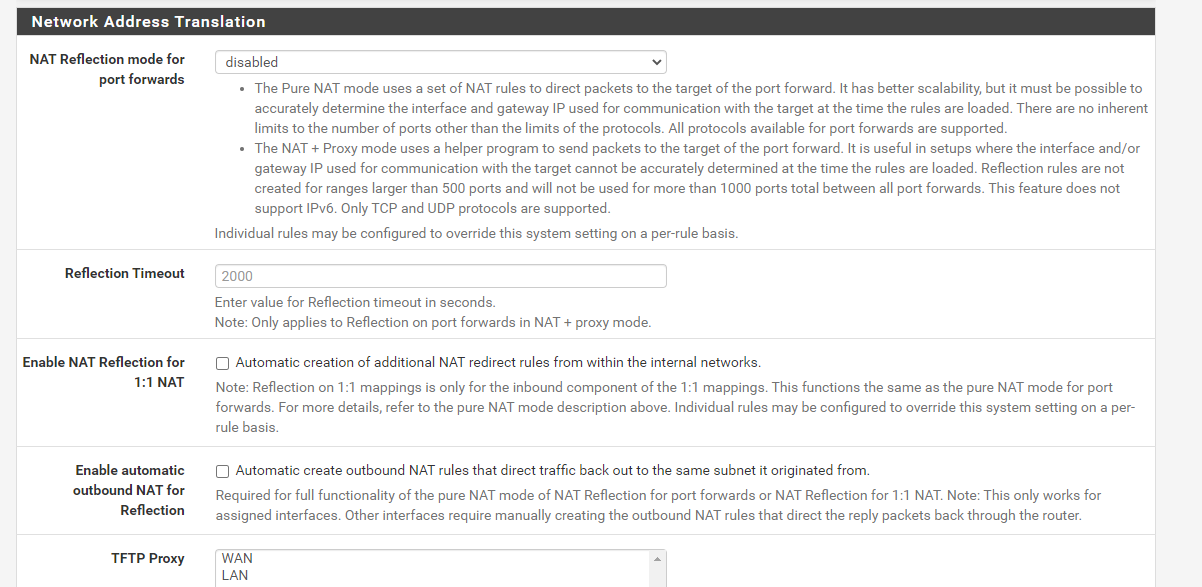
There is also a per-rule option on the individual port forwards. Is it enabled there?
-
Also your port forward target should really be
127.0.0.1and not192.168.1.1, assuming192.168.1.1is the LAN address of the firewall. -
Firewall rules
-
@jimp said in Problem with snapshot 3/31 16:19:49:
127.0.0.1
correct to loopback address
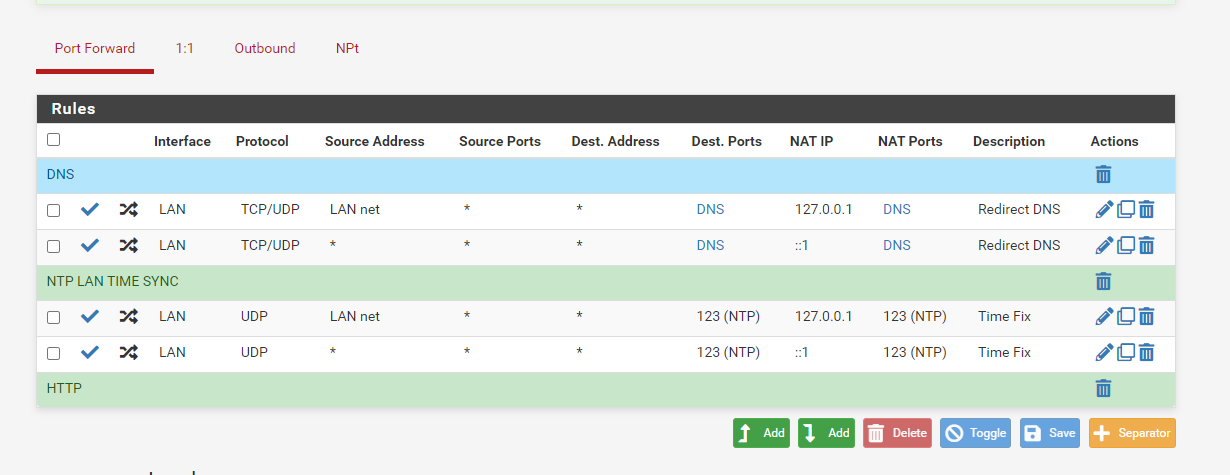
filter reload failed at same point as before with loopback address
-
Did you reboot after making that change? Once you get the error you have to reboot to know if it's fixed. Also check and see if those
no nat onrules are still present. -
I have to wait for 2 hours to do a reboot I am at work and the firewall must be up for 2 hours. I have changed the NTP and DNS to use the loopback 127, the no nat rules still show in debug if you delete them they return. Thanks I will reboot at 11:10am
-
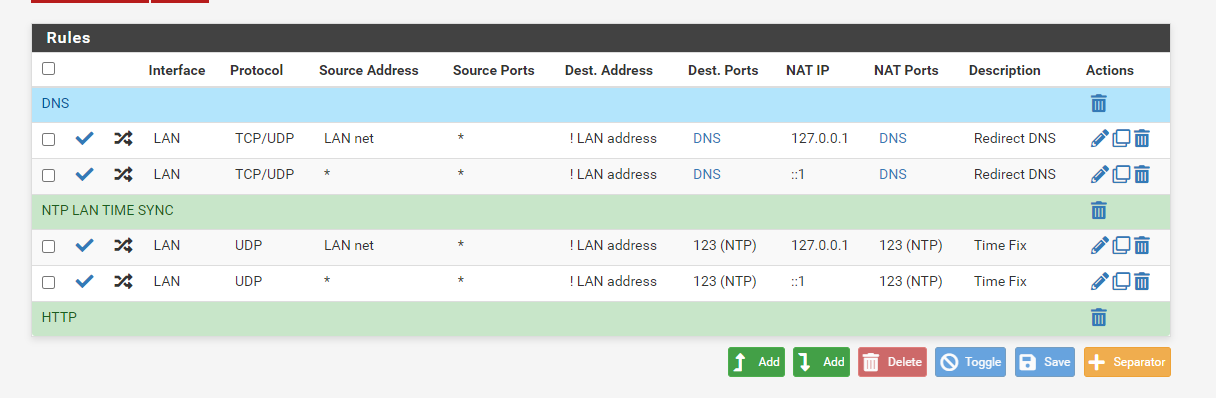
OK, I see the real source of your duplicate rules now and I can replicate it here. Your destination on those port forwards is Any and it should not be set to that. You should set that to ! LAN address (so check the Invert Match box for the destination and then set the destination to LAN Address)
As described in the docs:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html -
-
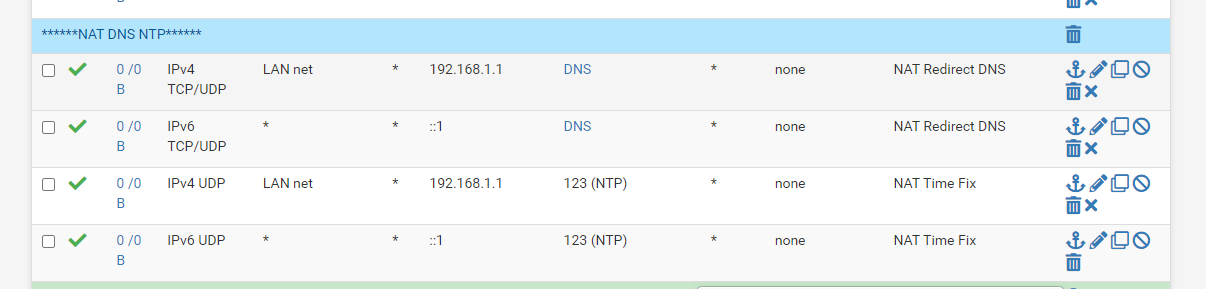
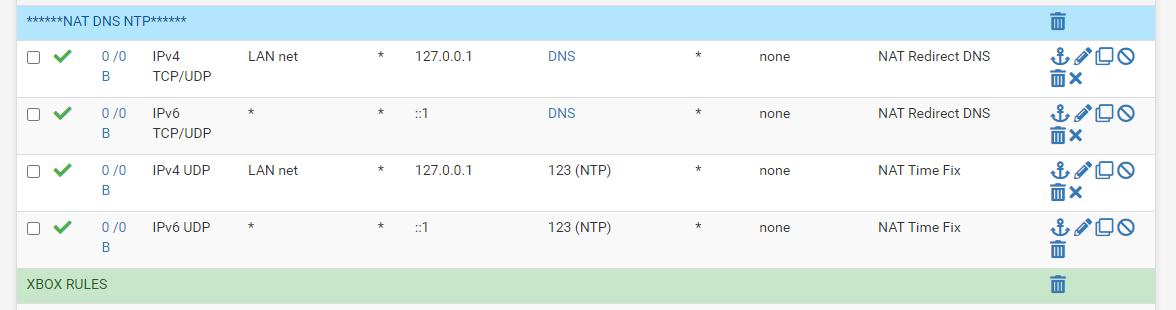
That looks good, if you look in
/tmp/rules.debugnow you shouldn't see thoseno nat onrules under therdrrules for those port fowards. If that is the case, you should be in good shape after a reboot. -
They are gone now, I wonder why that worked for so long before this update.
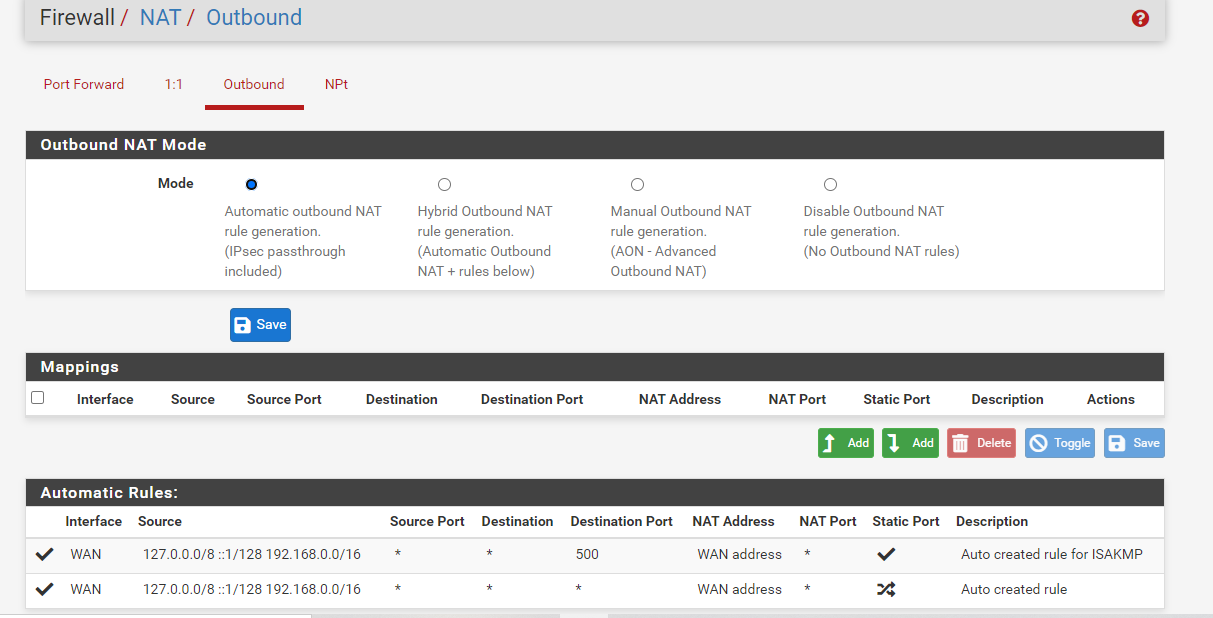
Outbound NAT rules (automatic)
Subnets to NAT
tonatsubnets = "{ 127.0.0.0/8 ::1/128 192.168.0.0/16 }"
nat on $WAN inet from $tonatsubnets to any port 500 -> 64.113.111.129/32 static-port
nat on $WAN inet6 from $tonatsubnets to any port 500 -> (mvneta0) static-port
nat on $WAN inet from $tonatsubnets to any -> 64.113.111.129/32 port 1024:65535
nat on $WAN inet6 from $tonatsubnets to any -> (mvneta0) port 1024:65535TFTP proxy
rdr-anchor "tftp-proxy/*"
NAT Inbound Redirects
rdr on mvneta1 inet proto { tcp udp } from 192.168.0.0/16 to !192.168.1.1 port $DNS -> 127.0.0.1
rdr on mvneta1 inet proto udp from 192.168.0.0/16 to !192.168.1.1 port 123 -> 127.0.0.1Setup Squid proxy redirect
rdr pass on mvneta1 inet proto tcp from any to !(mvneta1) port 80 -> 127.0.0.1 port 3128
rdr pass on mvneta1 inet proto tcp from any to !(mvneta1) port 443 -> 127.0.0.1 port 3129UPnPd rdr anchor
rdr-anchor "miniupnpd"
-
Thank you for your help with this and all you do.
-
The update has a problem with duplicate rules. We're still working on a fix, but in the meantime you can work around it by eliminating the duplicate rules. Most people get them from reflection + VIPs, but in your case it was port forwards with a destination of Any.
I'm surprised those port forwards worked well at all, they would have been looping traffic around a bit since even a query sent to the firewall would be caught and then redirected to ... the firewall. Unnecessarily. Port forwards for a destination of Any have a long history of problems.
See also:
-
The update forced me to use a more efficient configuration, Amazing, glad I waited it out. On a side note we are talking about efficiency in algorithm complexity in Java class this week. Again, I never thought about having to program dynamic conditional expressions for user configuration errors until today. Example if users programs routers ip in nat default to loopback, and or throw exception. Easier said then done I am sure. The routers Ip can be different, and each Nat rule can be different because of the packages in use.
-
This fixed it however i-cap will not start or clamAV any longer all errors for filter issues are gone and filter shows states logs now again.
-
@jonathanlee yes I have many packages that dont start now
avahi
lldpd
ntopng
ssftlowd
vnstatd/etc/rc.packages: The command '/usr/local/etc/rc.d/avahi-daemon.sh stop' returned exit code '2', the output was '/usr/local/etc/rc.d/avahi-daemon.sh: 17: Syntax error: "}" unexpected'
/rc.start_packages: The command '/usr/local/etc/rc.d/ntopng.sh stop' returned exit code '2', the output was '/usr/local/etc/rc.d/ntopng.sh: 29: Syntax error: "}" unexpected' -
Apr 1 11:21:13 (squid-1) 86303 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:24 (squid-1) 26626 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:36 (squid-1) 50467 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:47 (squid-1) 53928 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:21:59 (squid-1) 56555 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:10 (squid-1) 59214 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:22 (squid-1) 63577 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:34 (squid-1) 78058 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:45 (squid-1) 91402 FATAL: UFSSwapDir::openLog: Failed to open swap log.
Apr 1 11:22:47 php-fpm 402 /pkg_edit.php: Configuration Change:This is my only issue now
-
Everything corrected however I can no longer start ClamAv or I-CAP or LightSquid
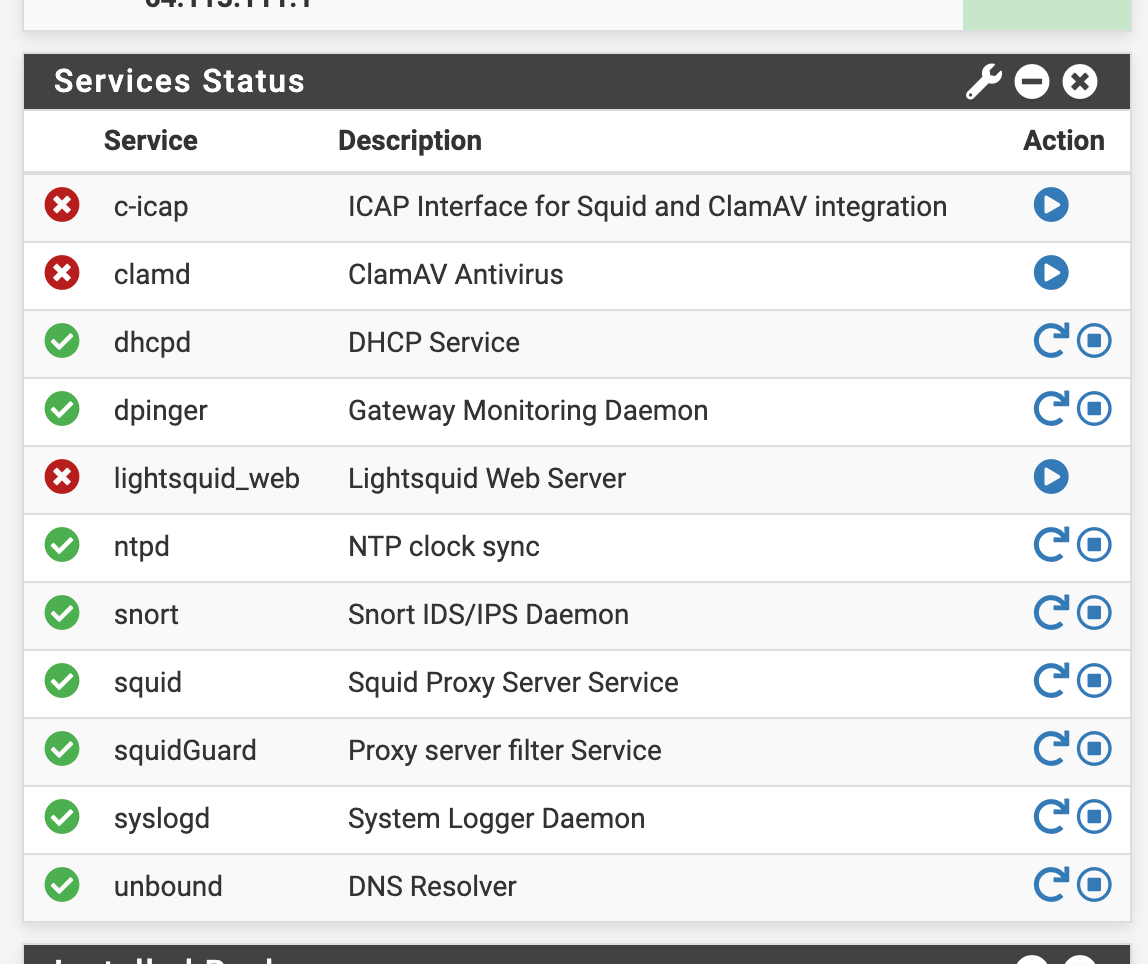
Is there something else that I am missing for the port 1344 and 7445 that worked before and no longer work today?
-
Shell Output - squid -k
2022/04/01 15:14:18| Startup: Initializing Authentication Schemes ...
2022/04/01 15:14:18| Startup: Initialized Authentication Scheme 'basic'
2022/04/01 15:14:18| Startup: Initialized Authentication Scheme 'digest'
2022/04/01 15:14:18| Startup: Initialized Authentication Scheme 'negotiate'
2022/04/01 15:14:18| Startup: Initialized Authentication Scheme 'ntlm'
2022/04/01 15:14:18| Startup: Initialized Authentication.
2022/04/01 15:14:18| Processing Configuration File: /usr/local/etc/squid/squid.conf (depth 0)
2022/04/01 15:14:18| Processing: http_port 192.168.1.1:3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=10MB cert=/usr/local/etc/squid/serverkey.pem cafile=/usr/local/share/certs/ca-root-nss.crt capath=/usr/local/share/certs/ cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:HIGH:!RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS tls-dh=prime256v1:/etc/dh-parameters.2048 options=NO_SSLv3,SINGLE_DH_USE,SINGLE_ECDH_USE
2022/04/01 15:14:18| UPGRADE WARNING: 'cafile=/usr/local/share/certs/ca-root-nss.crt' is deprecated in http_port. Use 'tls-cafile=' instead.
2022/04/01 15:14:22| ERROR: Unknown TLS option SINGLE_DH_USE
2022/04/01 15:14:22| ERROR: Unknown TLS option SINGLE_ECDH_USE
2022/04/01 15:14:22| Processing: http_port 127.0.0.1:3128 intercept ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=10MB cert=/usr/local/etc/squid/serverkey.pem cafile=/usr/local/share/certs/ca-root-nss.crt capath=/usr/local/share/certs/ cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:HIGH:!RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS tls-dh=prime256v1:/etc/dh-parameters.2048 options=NO_SSLv3,SINGLE_DH_USE,SINGLE_ECDH_USE
2022/04/01 15:14:22| Starting Authentication on port 127.0.0.1:3128
2022/04/01 15:14:22| Disabling Authentication on port 127.0.0.1:3128 (interception enabled)
2022/04/01 15:14:22| UPGRADE WARNING: 'cafile=/usr/local/share/certs/ca-root-nss.crt' is deprecated in http_port. Use 'tls-cafile=' instead.
2022/04/01 15:14:25| ERROR: Unknown TLS option SINGLE_DH_USE
2022/04/01 15:14:25| ERROR: Unknown TLS option SINGLE_ECDH_USE
2022/04/01 15:14:25| Processing: https_port 127.0.0.1:3129 intercept ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=10MB cert=/usr/local/etc/squid/serverkey.pem cafile=/usr/local/share/certs/ca-root-nss.crt capath=/usr/local/share/certs/ cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:HIGH:!RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS tls-dh=prime256v1:/etc/dh-parameters.2048 options=NO_SSLv3,SINGLE_DH_USE,SINGLE_ECDH_USE
2022/04/01 15:14:25| Starting Authentication on port 127.0.0.1:3129
2022/04/01 15:14:25| Disabling Authentication on port 127.0.0.1:3129 (interception enabled)
2022/04/01 15:14:25| UPGRADE WARNING: 'cafile=/usr/local/share/certs/ca-root-nss.crt' is deprecated in https_port. Use 'tls-cafile=' instead.
2022/04/01 15:14:29| ERROR: Unknown TLS option SINGLE_DH_USE
2022/04/01 15:14:29| ERROR: Unknown TLS option SINGLE_ECDH_USE
2022/04/01 15:14:29| Processing: icp_port 3130
2022/04/01 15:14:29| Processing: digest_generation off
2022/04/01 15:14:29| Processing: dns_v4_first on
2022/04/01 15:14:29| ERROR: Directive 'dns_v4_first' is obsolete.
2022/04/01 15:14:29| dns_v4_first : Remove this line. Squid no longer supports preferential treatment of DNS A records.
2022/04/01 15:14:29| Processing: pid_filename /var/run/squid/squid.pid
2022/04/01 15:14:29| Processing: cache_effective_user squid
2022/04/01 15:14:29| Processing: cache_effective_group proxy
2022/04/01 15:14:29| Processing: error_default_language en
2022/04/01 15:14:29| Processing: icon_directory /usr/local/etc/squid/icons
2022/04/01 15:14:29| Processing: visible_hostname proxy.pfsense.secure
2022/04/01 15:14:29| Processing: cache_mgr jonathanlee571@gmail.com
2022/04/01 15:14:29| Processing: access_log /var/squid/logs/access.log
2022/04/01 15:14:29| Processing: cache_log /var/squid/logs/cache.log
2022/04/01 15:14:29| Processing: cache_store_log none
2022/04/01 15:14:29| Processing: netdb_filename /var/squid/logs/netdb.state
2022/04/01 15:14:29| Processing: pinger_enable on
2022/04/01 15:14:29| Processing: pinger_program /usr/local/libexec/squid/pinger
2022/04/01 15:14:29| Processing: sslcrtd_program /usr/local/libexec/squid/security_file_certgen -s /var/squid/lib/ssl_db -M 4MB -b 2048
2022/04/01 15:14:29| Processing: tls_outgoing_options cafile=/usr/local/share/certs/ca-root-nss.crt
2022/04/01 15:14:29| Processing: tls_outgoing_options capath=/usr/local/share/certs/
2022/04/01 15:14:29| Processing: tls_outgoing_options options=NO_SSLv3,SINGLE_DH_USE,SINGLE_ECDH_USE
2022/04/01 15:14:29| ERROR: Unknown TLS option SINGLE_DH_USE
2022/04/01 15:14:29| ERROR: Unknown TLS option SINGLE_ECDH_USE
2022/04/01 15:14:29| Processing: tls_outgoing_options cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:HIGH:!RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS
2022/04/01 15:14:29| Processing: tls_outgoing_options flags=DONT_VERIFY_PEER
2022/04/01 15:14:29| Processing: sslcrtd_children 5
2022/04/01 15:14:29| Processing: sslproxy_cert_adapt setValidAfter all
2022/04/01 15:14:29| Processing: logfile_rotate 7
2022/04/01 15:14:29| Processing: debug_options rotate=7
2022/04/01 15:14:29| Processing: shutdown_lifetime 3 seconds
2022/04/01 15:14:29| Processing: acl localnet src 192.168.0.0/16
2022/04/01 15:14:29| Processing: forwarded_for transparent
2022/04/01 15:14:29| Processing: via off
2022/04/01 15:14:29| Processing: httpd_suppress_version_string on
2022/04/01 15:14:29| Processing: uri_whitespace strip
2022/04/01 15:14:29| Processing: dns_nameservers 127.0.0.1
2022/04/01 15:14:29| Processing: refresh_pattern -i windowsupdate.com/..(cab|exe|dll|ms[i|u|f|p]|[ap]sf|wm[v|a]|dat|zip|psf) 43200 80% 129600 reload-into-ims
2022/04/01 15:14:29| Processing: refresh_pattern -i microsoft.com/..(cab|exe|dll|ms[i|u|f|p]|[ap]sf|wm[v|a]|dat|zip|psf) 43200 80% 129600 reload-into-ims
2022/04/01 15:14:29| Processing: refresh_pattern -i windows.com/..(cab|exe|dll|ms[i|u|f|p]|[ap]sf|wm[v|a]|dat|zip|psf) 43200 80% 129600 reload-into-ims
2022/04/01 15:14:29| Processing: refresh_pattern -i microsoft.com.akadns.net/..(cab|exe|dll|ms[i|u|f|p]|[ap]sf|wm[v|a]|dat|zip|psf) 43200 80% 129600 reload-into-ims
2022/04/01 15:14:29| Processing: refresh_pattern -i deploy.akamaitechnologies.com/..(cab|exe|dll|ms[i|u|f|p]|[ap]sf|wm[v|a]|dat|zip|psf) 43200 80% 129600 reload-into-ims
2022/04/01 15:14:29| Processing: refresh_pattern -i msedge.b.tlu.dl.delivery.mp.microsoft.com/..(cab|exe|dll|ms[i|u|f|p]|[ap]sf|wm[v|a]|dat|zip|psf) 43200 80% 129600 reload-into-ims
2022/04/01 15:14:29| Processing: refresh_pattern ^http.facebook.com. 720 100% 4320
2022/04/01 15:14:29| Processing: refresh_pattern -i pixel.facebook.com..(jpg|png|gif|ico|css|js) 241920 80% 241920
2022/04/01 15:14:29| Processing: refresh_pattern -i .akamaihd.net..(jpg|png|gif|ico|css|js) 241920 80% 241920
2022/04/01 15:14:29| Processing: refresh_pattern -i ((facebook.com)|(85.131.151.39)).(jpg|png|gif) 241920 99% 241920 store-stale
2022/04/01 15:14:29| Processing: refresh_pattern static.(xx|ak).fbcdn.net.(jpg|gif|png) 241920 99% 241920
2022/04/01 15:14:29| Processing: refresh_pattern ^http.profile.ak.fbcdn.net.(jpg|gif|png) 241920 99% 241920
2022/04/01 15:14:29| Processing: refresh_pattern -i .video.ak.fbcdn.net..(mp4|flv|mp3|amf) 10080 80% 43200
2022/04/01 15:14:29| Processing: refresh_pattern (audio|video)/(webm|mp4) 129600 99% 129600 store-stale
2022/04/01 15:14:29| Processing: refresh_pattern -i ^http.squid.internal. 241920 100% 241920 store-stale
2022/04/01 15:14:29| Processing: refresh_pattern ^http.mail.yahoo.com. 720 100% 4320 # YAHOO MAIL
2022/04/01 15:14:29| Processing: refresh_pattern ^http.yahoo. 720 100% 4320 # YAHOO ITSELF
2022/04/01 15:14:29| Processing: refresh_pattern ^http.yimg. 720 100% 4320 # YAHOO IMAGES
2022/04/01 15:14:29| Processing: refresh_pattern ([^.]+.|)(download|adcdownload).(apple.|)com/..(pkg|dmg) 4320 100% 43200 reload-into-ims
2022/04/01 15:14:29| /usr/local/etc/squid/squid.conf line 76: refresh_pattern ([^.]+.|)(download|adcdownload).(apple.|)com/..(pkg|dmg) 4320 100% 43200 reload-into-ims
2022/04/01 15:14:29| refreshAddToList: Invalid regular expression '([^.]+.|)(download|adcdownload).(apple.|)com/..(pkg|dmg)': empty (sub)expression
2022/04/01 15:14:29| Processing: refresh_pattern -i appldnld.apple.com 129600 100% 129600
2022/04/01 15:14:29| Processing: refresh_pattern -i phobos.apple.com 129600 100% 129600
2022/04/01 15:14:29| Processing: refresh_pattern -i iosapps.itunes.apple.com 129600 100% 129600
2022/04/01 15:14:29| Processing: refresh_pattern ^http.gmail. 720 100% 4320 # GMAIL
2022/04/01 15:14:29| Processing: refresh_pattern ^http.google. 720 100% 4320 # GOOGLE
2022/04/01 15:14:29| Processing: refresh_pattern ^http.kaspersky. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.geo.kaspersky.com. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.officecdn.microsoft.com. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.officecdn.microsoft.com.edgesuite.net. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.delivery.mp.microsoft.com/filestreamingservice/files. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.download.windowsupdate.com. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.download.windowsupdate.com/. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.au.download.windowsupdate.com/. 43200 100% 43200
2022/04/01 15:14:29| Processing: refresh_pattern ^http.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files. 43200 100% 43200
2022/04/01 15:14:29| Processing: range_offset_limit 0
2022/04/01 15:14:29| Processing: cache_mem 1000 MB
2022/04/01 15:14:29| Processing: maximum_object_size_in_memory 512 KB
2022/04/01 15:14:29| Processing: memory_replacement_policy heap GDSF
2022/04/01 15:14:29| Processing: cache_replacement_policy heap LFUDA
2022/04/01 15:14:29| Processing: minimum_object_size 0 KB
2022/04/01 15:14:29| Processing: maximum_object_size 5000 MB
2022/04/01 15:14:29| Processing: cache_dir ufs /var/squid/cache 15000 256 256
2022/04/01 15:14:29| Processing: offline_mode off
2022/04/01 15:14:29| Processing: cache_swap_low 90
2022/04/01 15:14:29| Processing: cache_swap_high 95
2022/04/01 15:14:29| Processing: acl donotcache dstdomain "/var/squid/acl/donotcache.acl"
2022/04/01 15:14:29| Processing: cache deny donotcache
2022/04/01 15:14:29| Processing: cache allow all
2022/04/01 15:14:29| Processing: refresh_pattern ^ftp: 1440 20% 10080
2022/04/01 15:14:29| Processing: refresh_pattern ^gopher: 1440 0% 1440
2022/04/01 15:14:29| Processing: refresh_pattern -i (/cgi-bin/|?) 0 0% 0
2022/04/01 15:14:29| Processing: refresh_pattern . 0 20% 4320
2022/04/01 15:14:29| Processing: acl allsrc src all
2022/04/01 15:14:29| Processing: acl safeports port 21 70 80 210 280 443 488 563 591 631 777 901 8080 3128 3129 1025-65535 3128 3129 1344 3130
2022/04/01 15:14:29| Processing: acl sslports port 443 563 8080 8854 8810 8806 1344 3128 3129 3130
2022/04/01 15:14:29| Processing: acl purge method PURGE
2022/04/01 15:14:29| Processing: acl connect method CONNECT
2022/04/01 15:14:29| Processing: acl HTTP proto HTTP
2022/04/01 15:14:29| Processing: acl HTTPS proto HTTPS
2022/04/01 15:14:29| Processing: acl step1 at_step SslBump1
2022/04/01 15:14:29| Processing: acl step2 at_step SslBump2
2022/04/01 15:14:29| Processing: acl step3 at_step SslBump3
2022/04/01 15:14:29| Processing: acl allowed_subnets src 192.168.0.0/16 127.0.0.1/32
2022/04/01 15:14:29| Processing: acl whitelist dstdom_regex -i "/var/squid/acl/whitelist.acl"
2022/04/01 15:14:29| /usr/local/etc/squid/squid.conf line 154: acl whitelist dstdom_regex -i "/var/squid/acl/whitelist.acl"
2022/04/01 15:14:29| WARNING: regular expression '.' has only wildcards and matches all strings. Using '.' instead.
2022/04/01 15:14:29| Processing: http_access allow manager localhost
2022/04/01 15:14:29| Processing: http_access deny manager
2022/04/01 15:14:29| Processing: http_access allow purge localhost
2022/04/01 15:14:29| Processing: http_access deny purge
2022/04/01 15:14:29| Processing: http_access deny !safeports
2022/04/01 15:14:29| Processing: http_access deny CONNECT !sslports
2022/04/01 15:14:29| Processing: http_access allow localhost
2022/04/01 15:14:29| Processing: quick_abort_min 512 KB
2022/04/01 15:14:29| Processing: quick_abort_max 512 KB
2022/04/01 15:14:29| Processing: quick_abort_pct 90
2022/04/01 15:14:29| Processing: request_body_max_size 0 KB
2022/04/01 15:14:29| Processing: delay_pools 1
2022/04/01 15:14:29| Processing: delay_class 1 2
2022/04/01 15:14:29| Processing: delay_parameters 1 -1/-1 -1/-1
2022/04/01 15:14:29| Processing: delay_initial_bucket_level 100
2022/04/01 15:14:29| Processing: delay_access 1 allow allsrc
2022/04/01 15:14:29| Processing: url_rewrite_program /usr/local/bin/squidGuard -c /usr/local/etc/squidGuard/squidGuard.conf
2022/04/01 15:14:29| Processing: url_rewrite_bypass off
2022/04/01 15:14:29| Processing: url_rewrite_children 16 startup=8 idle=4 concurrency=0
2022/04/01 15:14:29| Processing: http_access allow whitelist
2022/04/01 15:14:29| Processing: acl youtubedst dstdomain -n www.youtube.com m.youtube.com youtubei.googleapis.com youtube.googleapis.com www.youtube-nocookie.com
2022/04/01 15:14:29| Processing: request_header_access YouTube-Restrict deny all
2022/04/01 15:14:29| Processing: request_header_add YouTube-Restrict moderate youtubedst
2022/04/01 15:14:29| Processing: acl sglog url_regex -i sgr=ACCESSDENIED
2022/04/01 15:14:29| Processing: http_access deny sglog
2022/04/01 15:14:29| Processing: ssl_bump peek step1
2022/04/01 15:14:29| Processing: ssl_bump splice all
2022/04/01 15:14:29| Processing: http_access allow allowed_subnets
2022/04/01 15:14:29| Processing: http_access allow localnet
2022/04/01 15:14:29| Processing: http_access deny allsrc
2022/04/01 15:14:29| WARNING: use of 'reload-into-ims' in 'refresh_pattern' violates HTTP
2022/04/01 15:14:29| WARNING: HTTP requires the use of Via
2022/04/01 15:14:29| Initializing https:// proxy context
2022/04/01 15:14:29| SECURITY WARNING: Peer certificates are not verified for validity!
2022/04/01 15:14:29| UPGRADE NOTICE: The DONT_VERIFY_PEER flag is deprecated. Remove the clientca= option to disable client certificates.
2022/04/01 15:14:29| Initializing http_port 192.168.1.1:3128 TLS contexts
2022/04/01 15:14:29| Using certificate in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Using certificate chain in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Adding issuer CA: /CN=internal-ca/C=US/ST=California/L=Roseville/O=Homeuse
2022/04/01 15:14:29| Using key in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Not requiring any client certificates
2022/04/01 15:14:29| Initializing http_port 127.0.0.1:3128 TLS contexts
2022/04/01 15:14:29| Using certificate in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Using certificate chain in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Adding issuer CA: /CN=internal-ca/C=US/ST=California/L=Roseville/O=Homeuse
2022/04/01 15:14:29| Using key in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Not requiring any client certificates
2022/04/01 15:14:29| Initializing https_port 127.0.0.1:3129 TLS contexts
2022/04/01 15:14:29| Using certificate in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Using certificate chain in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Adding issuer CA: /CN=internal-ca/C=US/ST=California/L=Roseville/O=Homeuse
2022/04/01 15:14:29| Using key in /usr/local/etc/squid/serverkey.pem
2022/04/01 15:14:29| Not requiring any client certificates -
@jonathanlee Netgate TAC has directed me to go back to 21.0 and use the firmware that was provided with their equipment when I purchased it and everything is working again.
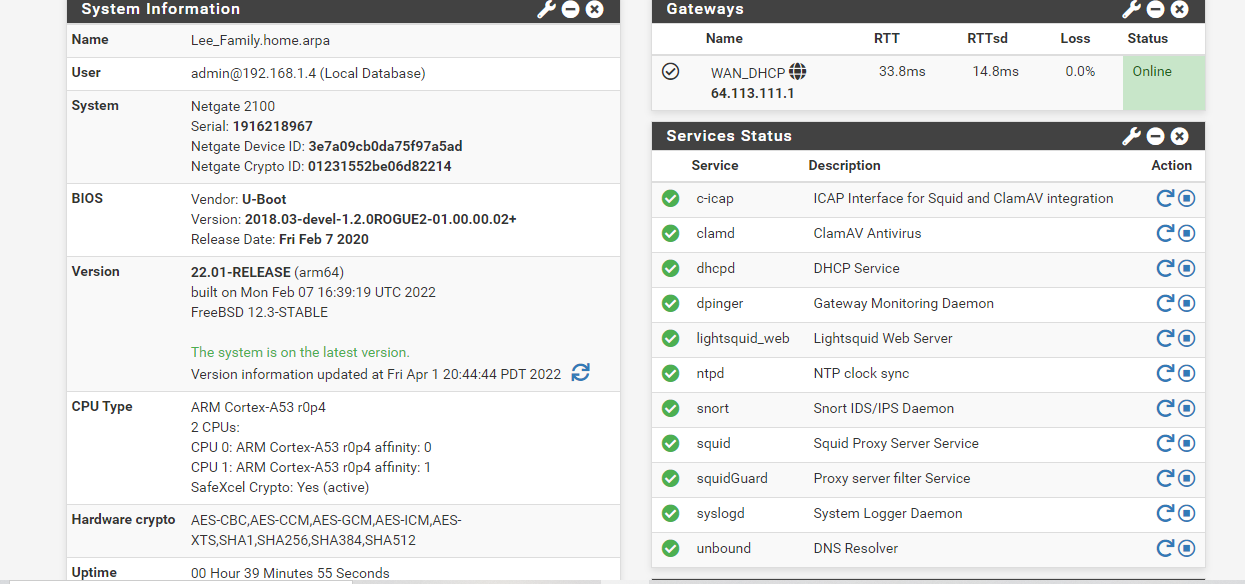
I had to restore my old Nat rules to make it work again perfectly also. I do not know why. Maybe that is something to look into on the development side.