pfsense, web server and VLAN's
-
@stephenw10 Hi Stephen, Ok here are the VLAN's configured
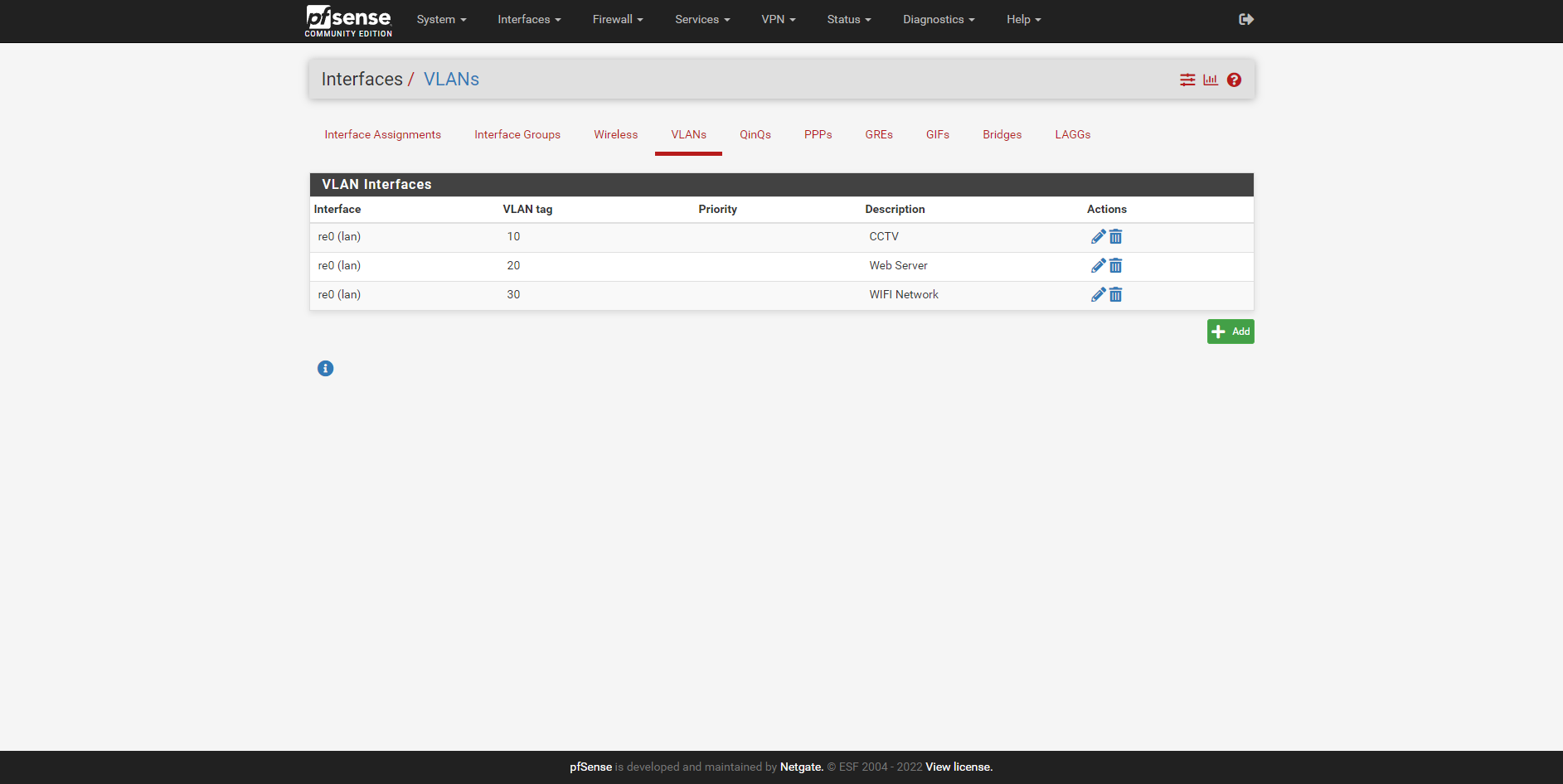
DHCP for one of the VLAN's
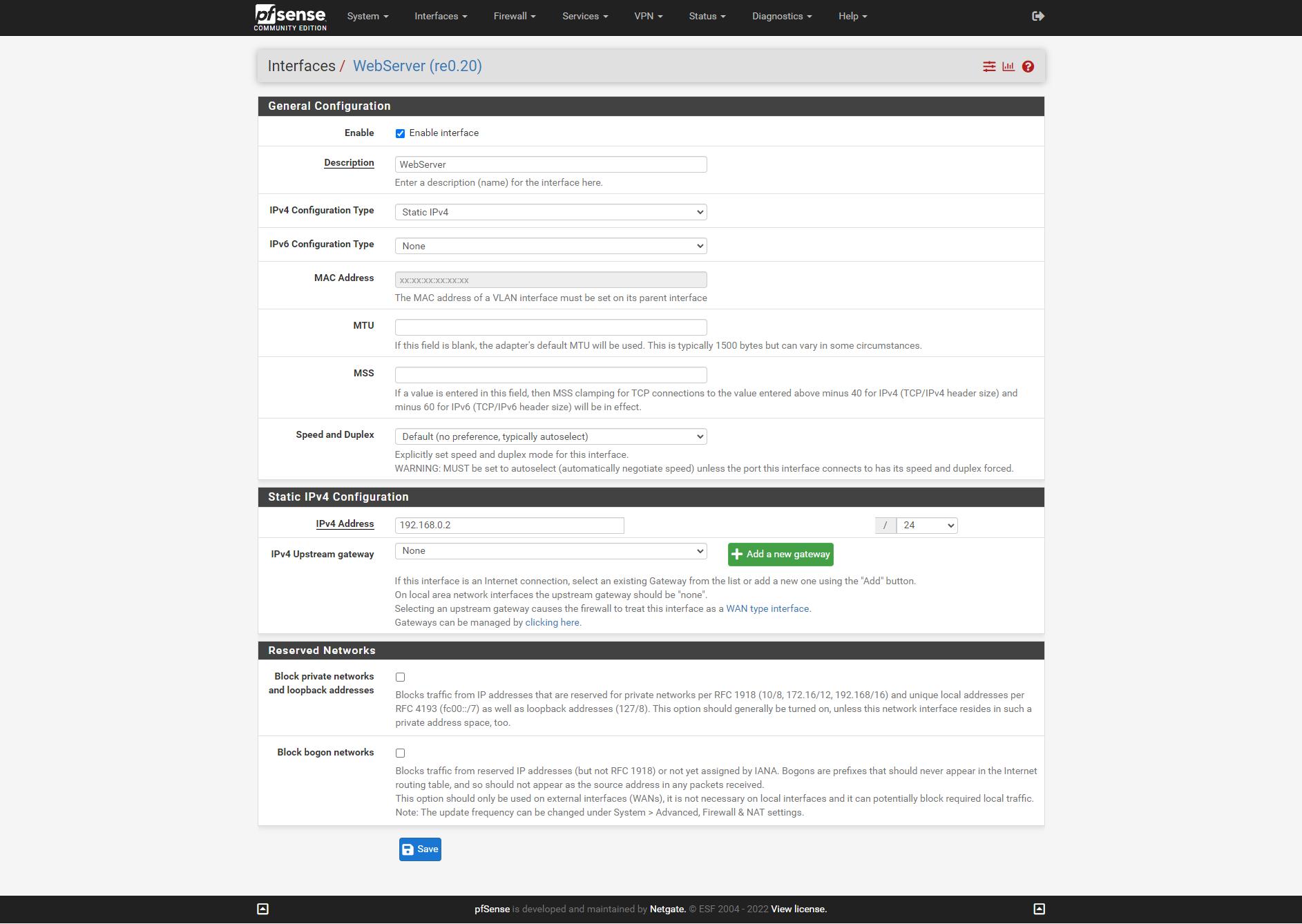
Dashboard
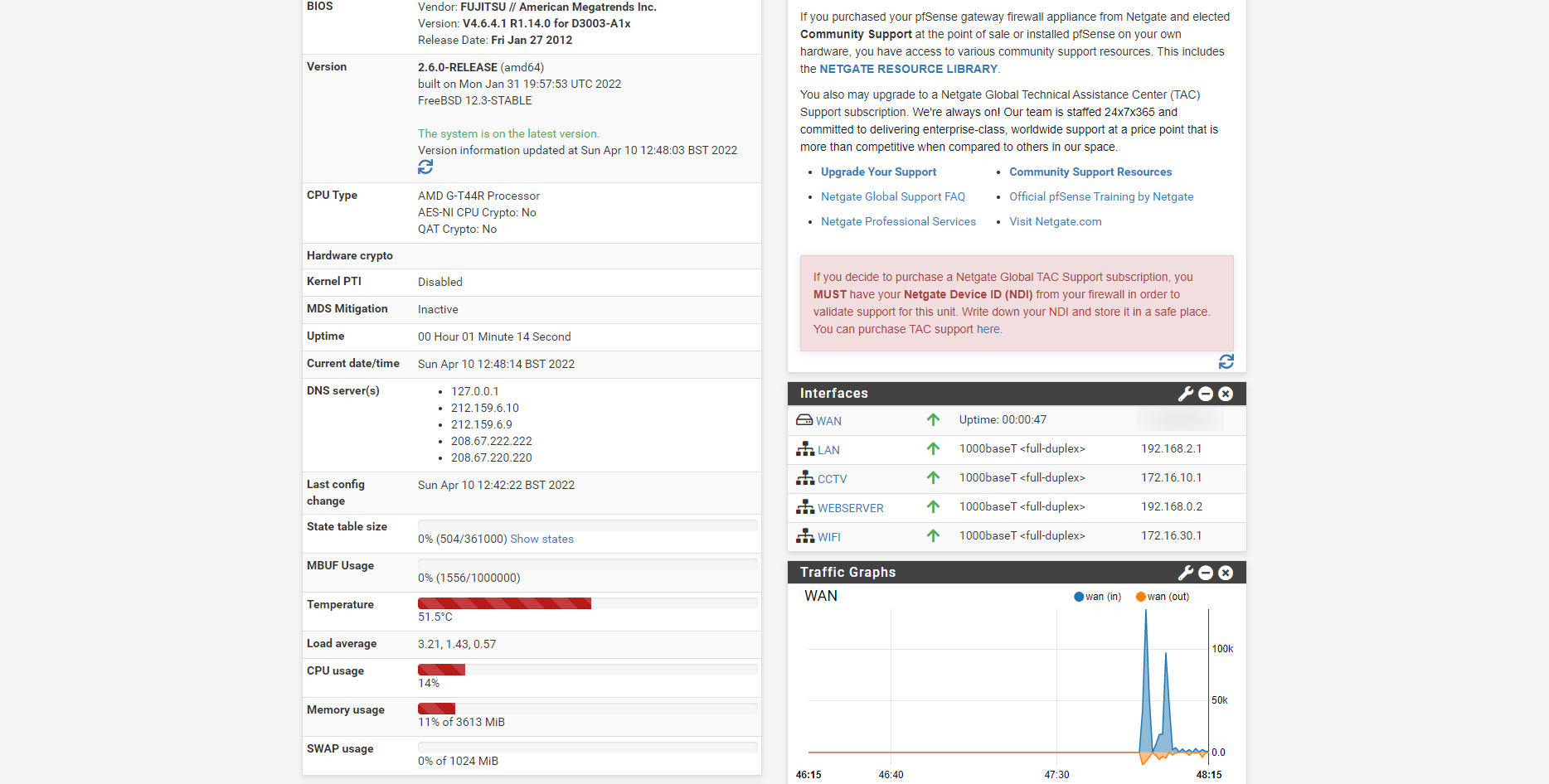
Switch
I am now getting the correct DHCP served on each port but no internet connection now?
Thanks
Rockyuk
-
You probably need to add firewall rules to the 'webserver' interface. Only LAN is given a pass rule by default. Any additional interfaces need rules to be added to pass traffic.
Steve
-
@stephenw10 Could you provide an example please?
-
Something like:
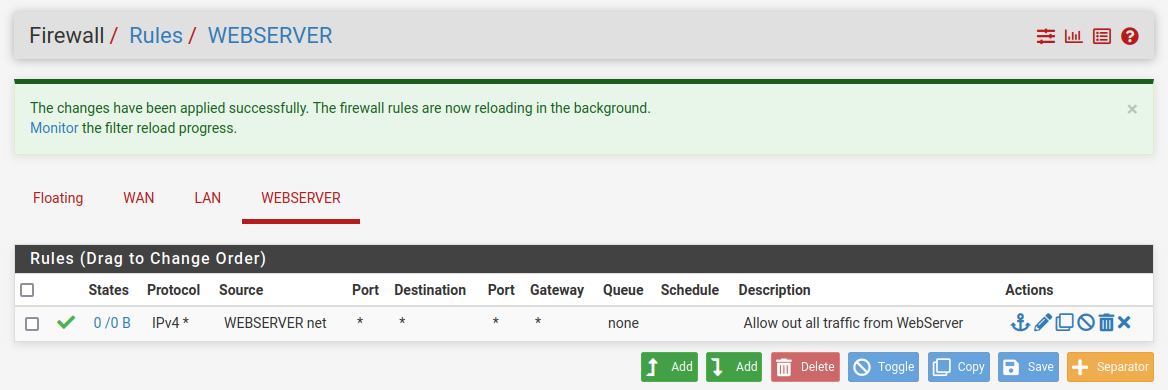
Though you may want to get more refined. It depends what subnets need access to one another.
Steve
-
@stephenw10 Thank you, I will give it a go and let you know.
-
@stephenw10 Hi Stephen, I tried that and it worked briefly then stopped and started to stop resolving websites. Tried to bring up google and duckduckgo and nothing it did work for a few seconds then stopped.
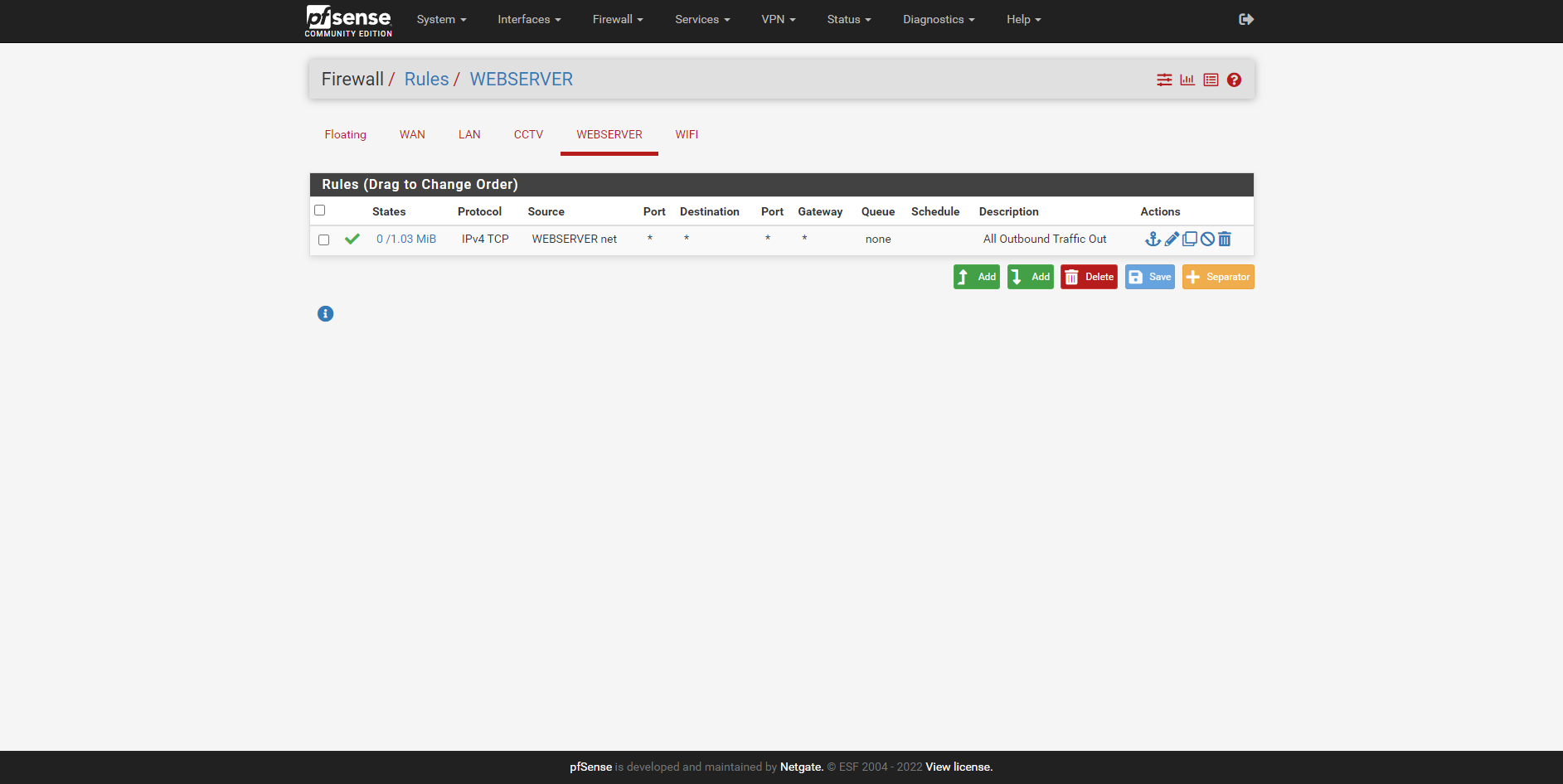
-
That rule is passing TCP only, so DNS is not passed because it mainly uses DNS.
Set the protocol to 'any' as my example rule shows.
Steve
-
@stephenw10 You are a star that worked thank you, last thing. With regards to the web server for incoming firewall rules for HTTPS, HTTP and DNS etc, as my websites SSL does not seem to be loading. Is the below rules correct for incoming on the web server?
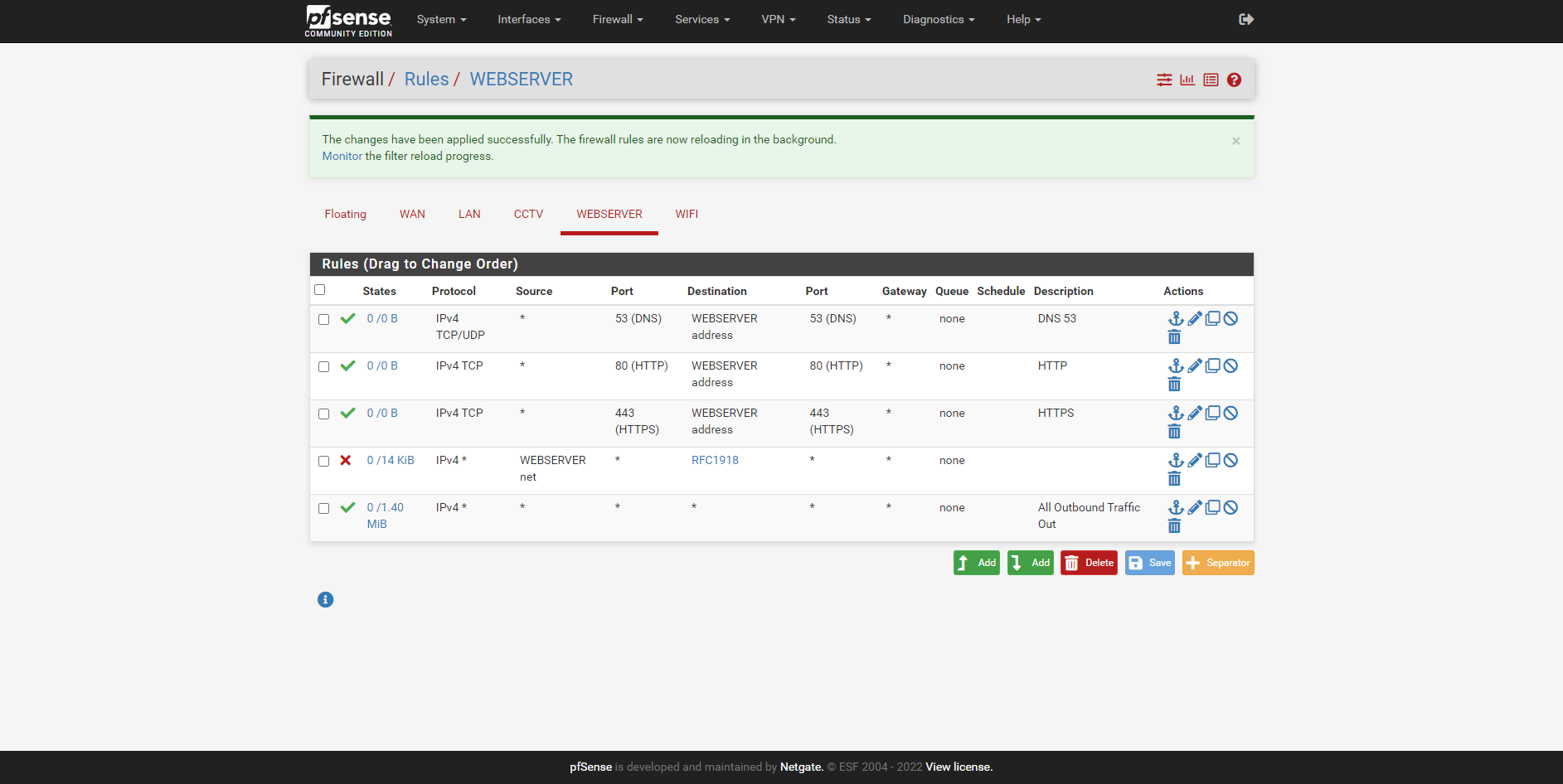
-
@rockyuk said in pfsense, web server and VLAN's:
Is the below rules correct for incoming on the web server?
Huh? Those are not "incoming" to your webserver - those are incoming to the pfsense interface your calling webserver.
They would not have anything to do with something talking to some webserver on this network, from some other network.
-
Indeed for incoming traffic to the webserver from some external address the rules would need to be on the WAN interface.
If the WEBSERVER subnet is private you would also need port forward rules to allow that. By default the port forwards will add appropriate firewall rules when you add them anyway.
The source port on rules like that should almost always be 'any'. Only the destination port is the known value for the traffic you are passing.In pfSense firewall rules apply to traffic coming into an interface. So for internal subnets that means traffic coming into the interface is from the hosts on that subnet to some other location outside the subnet.
Steve
-
@stephenw10 Apologies, I am new to all of this and probably not the easiest firewall for me to setup. So, I apologise if what I am doing does not make sense as I am learning as I go along. I have followed a lot of YouTube videos to get this far but I need a little more guidance on the Incoming Firewall rules for the web server.
Could you post an example for a rule for either incoming DNS (53) or HTTPS please. As I am clearly stuck on this part. Thank you
-
Add a port forward like this:
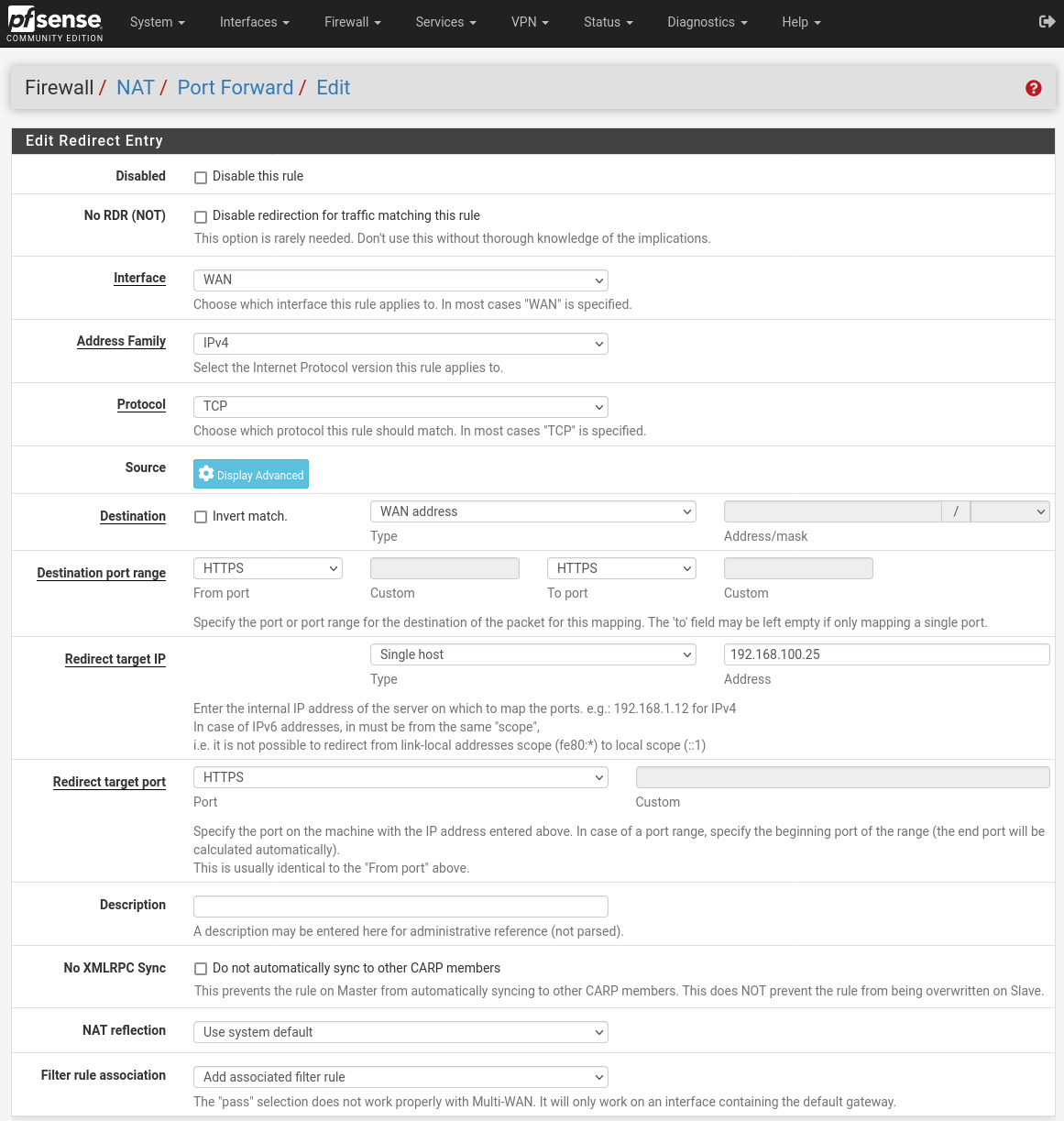
Obviously change the 'Redirect target IP' to the internal address of your webserver.
The 'Filter Rule Association' value there will create a matching firewall rule on WAN you will be able to see.
Are you sure you want to allow external access to DNS on that machine? That's almost always a bad idea!
Steve
-
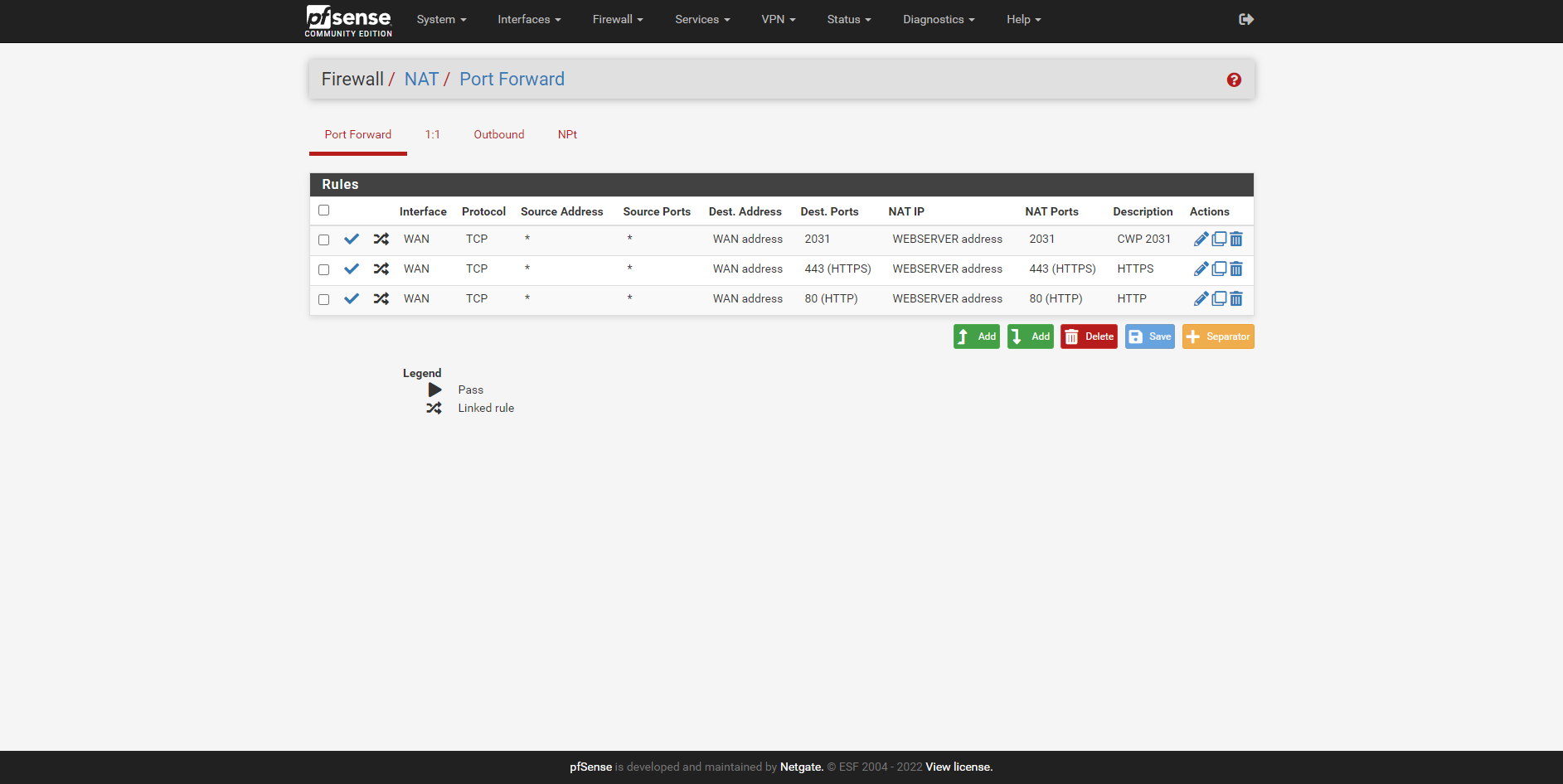
@stephenw10 I think I have done it correctly thank you.
Firewall Rules
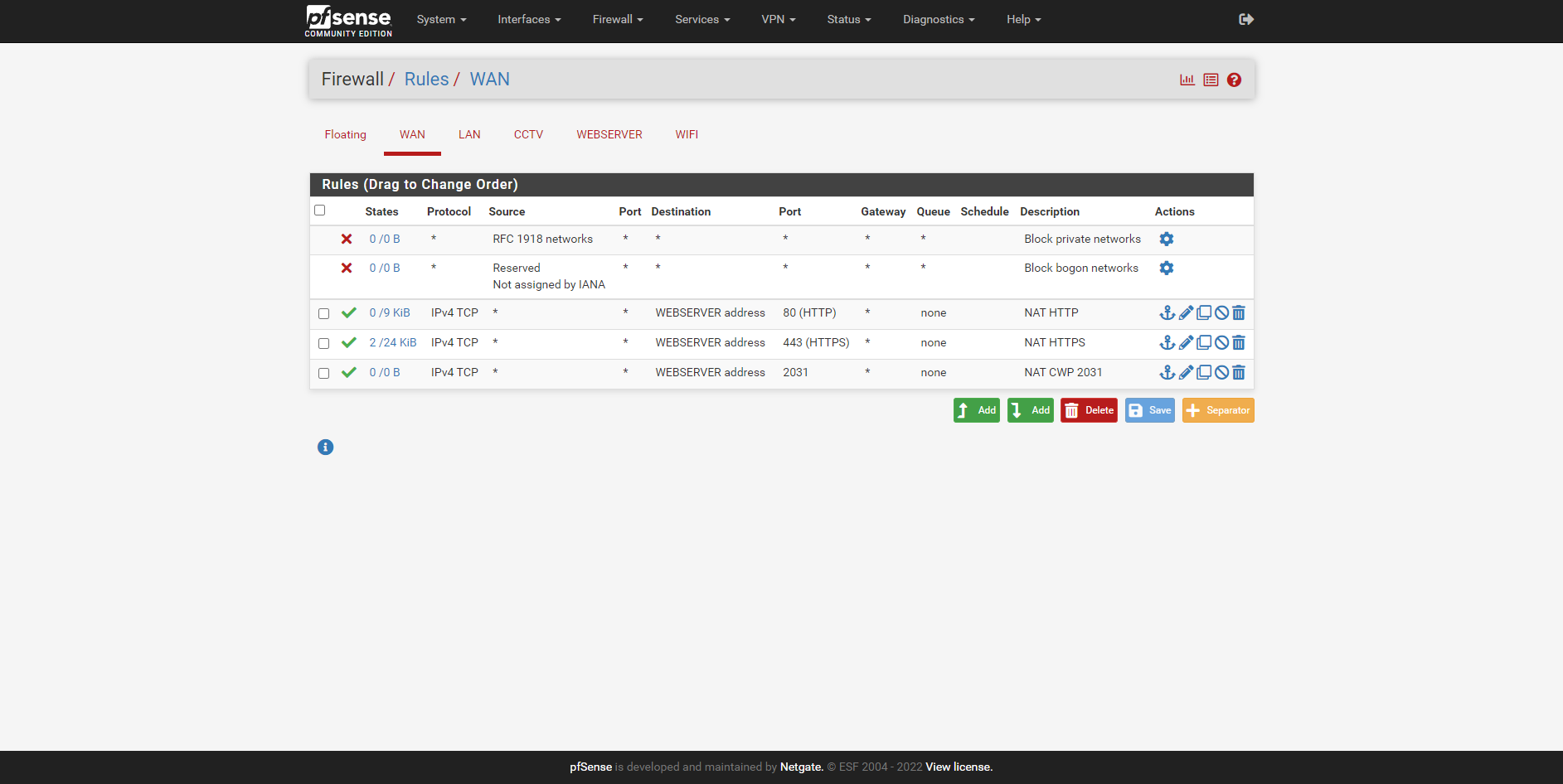
NAT
When I goto my website I it is not showing the SSL Certificate anymore and i get the following error
Potential DNS Rebind attack detected, see http://en.wikipedia.org/wiki/DNS_rebinding
Try accessing the router by IP address instead of by hostname. -
'WEBSERVER address' in that context refers to the address of the WEBSERVER interface which is wrong. The target IP needs to be the internal address of the actual web server in that subnet.
Steve
-
NAT
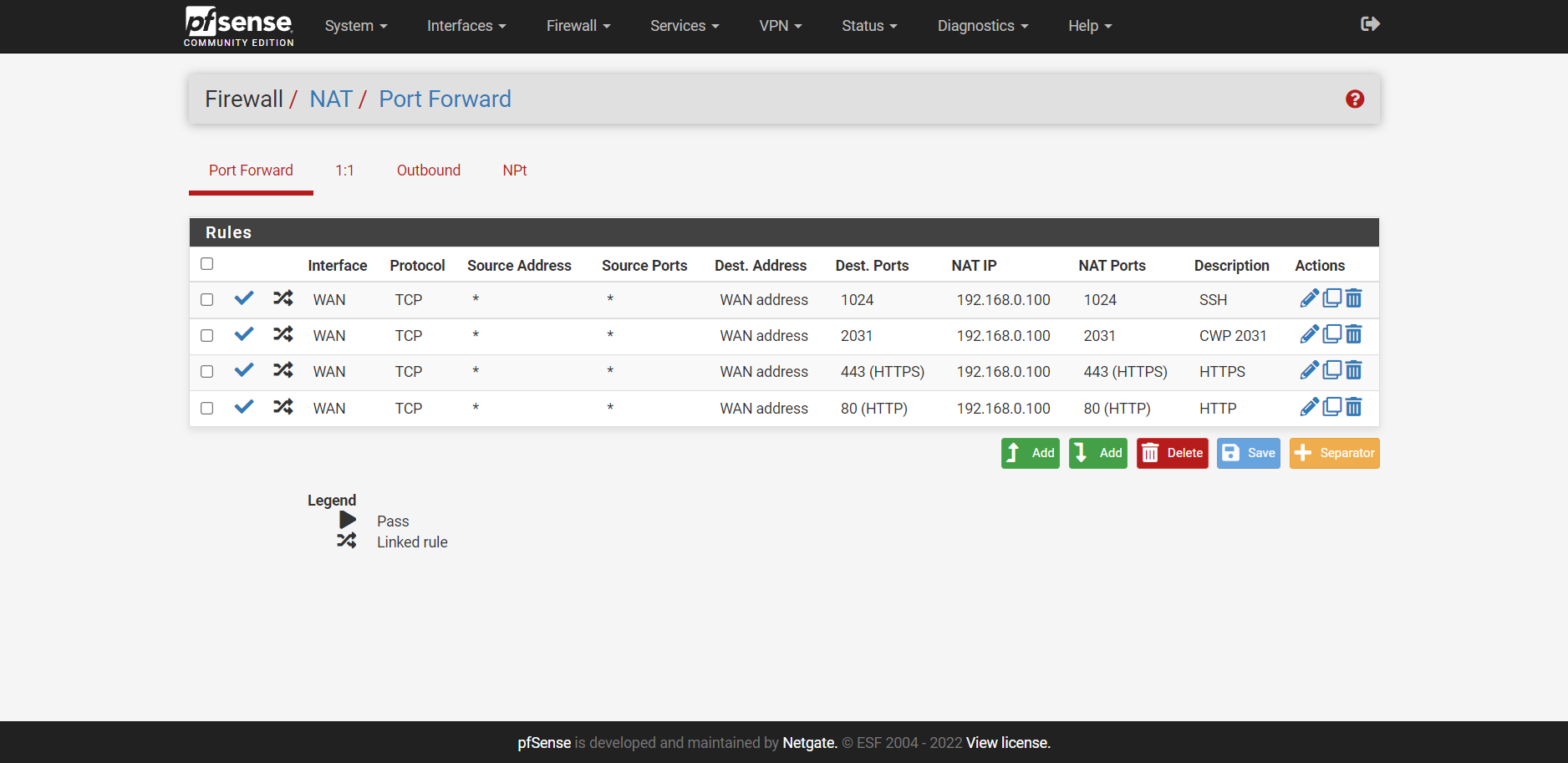
Firewall Rules
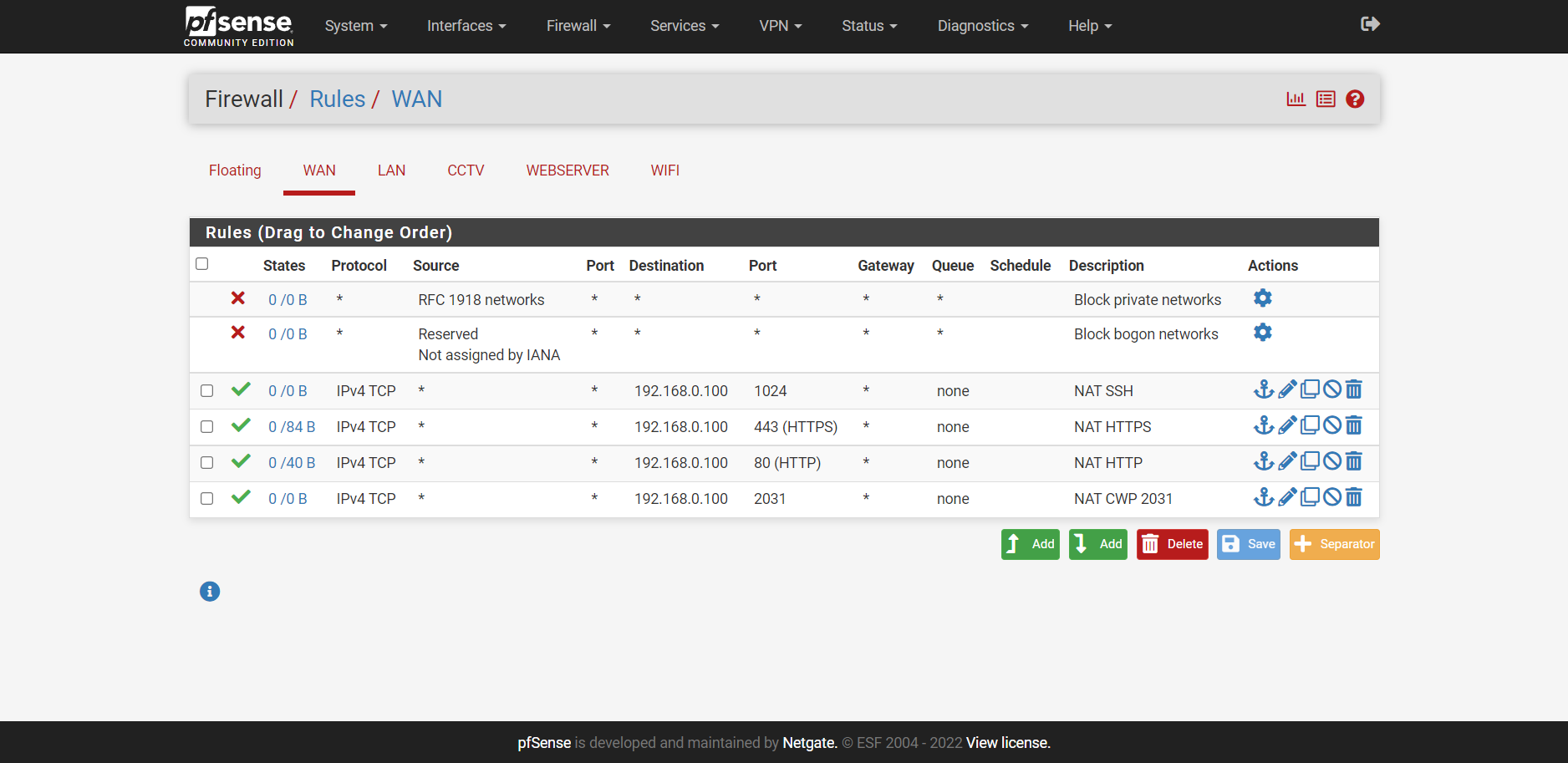
I am still unable to access my website as it is still bringing up the following
Potential DNS Rebind attack detected, see http://en.wikipedia.org/wiki/DNS_rebinding
Try accessing the router by IP address instead of by hostname. -
Ah, that's because you are testing from inside the firewall so it's hitting the pfSense GUI.
You need split DNS or NAT reflection if you want that to work:
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.htmlBut you should test from an external connection to be sure the port forward is working. So on your phone over LTE for example.
Steve
-
@stephenw10 That worked thank you, still not able to bring up website keeps timing out
-
Check the state table in Diag > States whilst you're testing.
If you see the states open on WAN and WEBSERVER for the IP you're testing from then pfSense is forwarding it correctly. It could be the server is rejecting the external traffic.
Steve
-
Looks good now whatever you did.

-
@stephenw10 Ok, I am getting offline and 100% packet loss on my Gateway.
No traffic is getting through to Web Server either, I thought it might have been my software firewall on web server CSF. I disabled it and still nothing!