pfSense with OpenWRT Guest logon with VLAN
-
No there's no switch in the AP300, it's an access point.
What's the hardware layout in the WRT3200ACM? Is this correct for your version?
https://openwrt.org/toh/linksys/wrt3200acm#switch_ports_for_vlansIf so and you are using the eth1 (WAN) port as the uplink you should be able to create the VLAN there and then add that to the new bridge device. I've used eth0 because that's the only port on the AP300.
You could create it on eth0 (the internal switch port) on your router but then you need to configure the switch to trunk that VLAN. Or use port based VLANs to just pass it.
It looks like OpenWRT will also allow you to create a VLAN on the bridge interface which is what you have done. For me that's less logical. YMMV!
There's probably several ways to do this. It's definitely possible.
Steve
-
Oh, wait think I read that switch diagram wrong. So the hardware actually has 5 physical ports? LAN 1-4 and WAN?
In fact both actual NICs (eth0 and eth1) are connected to the switch on internal ports 5 and 6?If you're using port VLAN mode (not 802.1q) then all VLAN traffic is passed. So create a VLAN interface on eth0. Create a bridge device with that in it. Create an interface with the new bridge. Assign the guest wifi to that.
There are in fact numerous ways you could do this depending what you want.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
No there's no switch in the AP300, it's an access point.
Steve, I wasn't talking about the AP300 hardware, but in the OpenWRT LuCI, under the Network tab, does it show "Switch"?
Yes, the WRT3200ACM has 4 ports plus the WAN port.
-
No I don't see a switch menu in LuCI because there's no switch to configure.
What is your switch config currently?
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
What is your switch config currently?
I'm not really sure, there is no "Switch" function on a full DSA... that's where I think I was getting hung up on your suggestion. Ver 21 has moved to DSA... but only for some devices and the tell is whether you have the "Switch" function or not. But I digress. I follow your suggestion starting at "Create a bridge" device...". I'm not following you on "create a VLAN interface on eth0". Please elaborate.
Thanks,
Rick -
Hmm, well there must still be a way of configuring the switch IC. Look at the full
uci showoutput. What's in there that relates to the switch ports?But since you already created VLAN device and then when you added it as an interface it correctly pulled a dhcp lease from that VLAN implies however you have switch configured it must be passing the traffic.
However you created it on the existing bridge device which is not logical to me. Maybe it could work.I suggest you remove the VLAN device you created and instead create on eth0. Then create the bridge on that. Then the interface as the new bridge device.
Now when you are adding the VAP to the new interface you are adding it to a bridge and not to a VLAN. And underneath the OpenWRT config Linux still needs to bridge the traffic between those interfaces which is I think what was failing for you.Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
I suggest you remove the VLAN device you created and instead create on eth0. Then create the bridge on that. Then the interface as the new bridge device.
Now when you are adding the VAP to the new interface you are adding it to a bridge and not to a VLAN. And underneath the OpenWRT config Linux still needs to bridge the traffic between those interfaces which is I think what was failing for you.I know YOU know what you are talking about and trust you are right. I'm starting to feel like an idiot. I can't even get to the VAP point of this as I can't make what you have lined out work (again, starting with the interface as a DHCP client to verify connectivity with the pfSense supplied VLAN and DHCP server).
Am I reading/following your suggestion wrong?
Create the VLAN 10 device 802.1q with eth0 as the base device = eth0.10
Create a bridge for software VLAN eth0.10 and Switch port WAN = br.eth0.10
Create the Interface for my Guest function as a DHCP client and the device is br.eth0.10The Interface never gets an address. Lots of outbound packets, nothing inbound.
I'm sure I'm doing something wrong... just not sure what?
-
Ok, having read this and this, specifically this: https://openwrt.org/docs/guide-user/network/dsa/converting-to-dsa#wireless
I can absolutely see why you have it configured as you do and might expect it to work like that.
I also find myself beginning to hate the DSA with a fiery passion!

It seems like it hides half the ports presenting them to you as though they are interfaces and 'helpfully' adding all the VLANs and switch settings for you. Which I hate. But even more so when it doesn't do it correctly!
No idea how you know which eth ports the switch is using internally or how they are configured if you want change that....So, according to that doc, you should be able create the VLAN device on the bridge as you showed. And you should be able to add the wifi network to it directly. But you will have to enable bridge VLAN filtering in order to have the VAP added to the bridge with the correct tags by whatever dark magic powers DSA.
Or just pretend the switch doesn't exist since we know without VLAN filtering enabled it just passes all VLAN (port based vlan mode) and do what I outlined above which still works fine in 21.X.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Ok, having read this and this, specifically this: https://openwrt.org/docs/guide-user/network/dsa/converting-to-dsa#wireless
I can absolutely see why you have it configured as you do and might expect it to work like that.
I also find myself beginning to hate the DSA with a fiery passion!

It seems like it hides half the ports presenting them to you as though they are interfaces and 'helpfully' adding all the VLANs and switch settings for you. Which I hate. But even more so when it doesn't do it correctly!
No idea how you know which eth ports the switch is using internally or how they are configured if you want change that....OK, I had to chuckle at "fiery passion"... but then the reality of "This is MY problem and I still haven't resolved it" set in.
The best clue I have as tho which eth port is in play comes from the Network/Devices.
It only shows "eth0". And, that does correlate with the information as you too found on the OpenWRT site regarding the WRT3200ACM.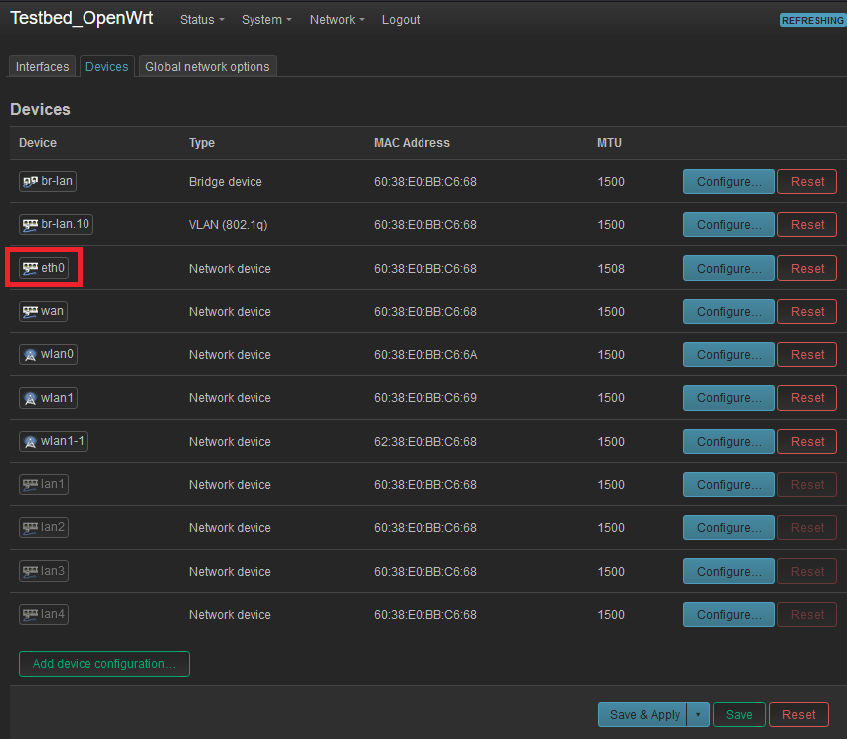
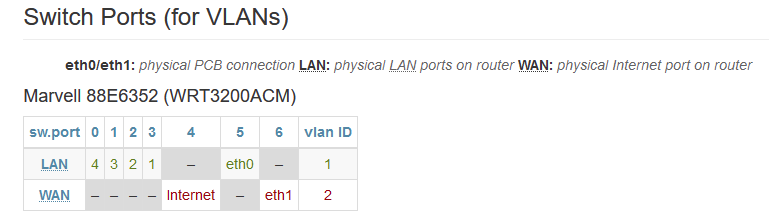
-
Mmm, it does look like it's only using eth0 and eth1 is simply ignored. That's fine for you in an access point config since you're never routing traffic between Ethernet interfaces. Any traffic there should just be switched. Though we just have to hope that's happening since we can't see how the switch is configured. And the gui makes it look like they're bridged which would be a very bad setup! </rant>
Anyway it looks like you can do this two ways:
Enable bridge VLAN filtering and add the correct VLAN tags so DSA knows how to configure the switch for 802.1Q mode when you add the VAP to it.
Or leave bridge VLAN filtering disabled and treat it like a dumb switch. In which case setup the VLAN device and additional bridge as I outlined.
One interesting thing here is the screenshot in the doc here.
Wireless interfaces will automatically be included in the bridge and belong in the correct VLAN.You can see that command they use shows exactly that. The VAP device, wlan1-1, is added to the bridge on a VLAN. I suspect that is what's not happening in your current setup. However I have no idea what command was used to check that. It's not anything default in OpenWRT. The closest I got to it was installing the bridge package and then running
brctl show. That doesn't show VLAN info me though. [Edit: I see it's a standard Linux command to show the vlans in a bridge, just not included in openwrt]Steve
-
Oh here we go you can install the ip-bridge package and then:
root@AP300:~# bridge vlan show port vlan-id eth0 1 PVID Egress Untagged br-lan 1 PVID Egress Untagged br-guest 1 PVID Egress Untagged eth0.1001 1 PVID Egress Untagged wlan1 1 PVID Egress Untagged wlan0 1 PVID Egress Untagged wlan0-1 1 PVID Egress Untagged root@AP300:~# bridge link show 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master br-lan state forwarding priority 32 cost 4 10: eth0.1001@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master br-guest state forwarding priority 32 cost 4 13: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master br-lan state forwarding priority 32 cost 100 15: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master br-lan state forwarding priority 32 cost 100 16: wlan0-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master br-guest state forwarding priority 32 cost 100So you can see the two bridges I have and the members in them. And since I do not have vlan filtering enabled on either they are all set as VLAN 1 and passing all traffic. Which includes vlan1001 tagged packets here.
Steve
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
Mmm, it does look like it's only using eth0 and eth1 is simply ignored. That's fine for you in an access point config since you're never routing traffic between Ethernet interfaces. Any traffic there should just be switched. Though we just have to hope that's happening since we can't see how the switch is configured. And the gui makes it look like they're bridged which would be a very bad setup! </rant>
Anyway it looks like you can do this two ways:
Enable bridge VLAN filtering and add the correct VLAN tags so DSA knows how to configure the switch for 802.1Q mode when you add the VAP to it.
Or leave bridge VLAN filtering disabled and treat it like a dumb switch. In which case setup the VLAN device and additional bridge as I outlined.
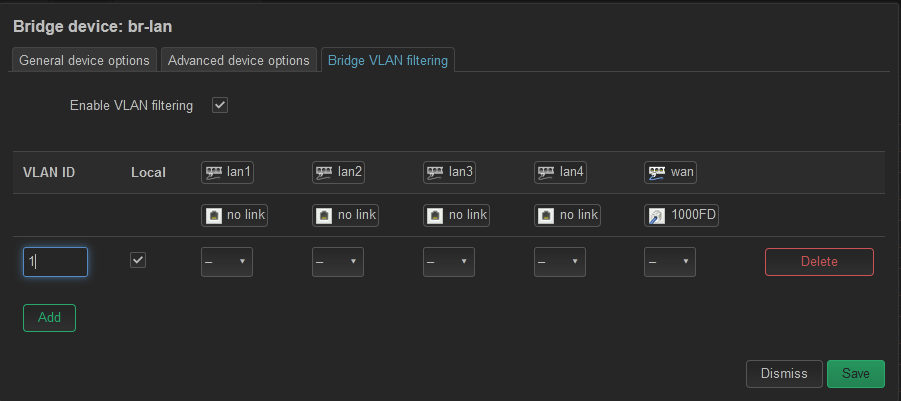
SteveIf I go back to the configuration I started with, the ONLY device that offers "Bridge VLAN Filtering" is the br-lan.
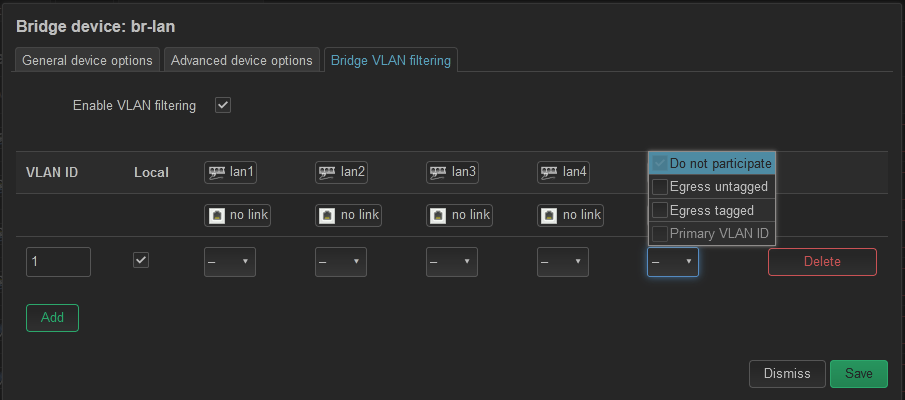
Once I enable this option, the only thing I see are the LAN ports and the WAN port which is now a lan port and being used for the back-haul. No eth0, eth1 or radios.
If I create the VLAN 10, what do you suggest the tagging be, I have no ingress option.Note: Although I have the VLAN seeming to work from pfSense through my managed switch, to my interface running DHCP client, I am no expert in tag/untag or PVID. Every time I have attempted to configure a VLAN 10, I get locked out on the save and have to wait the 90sec to revert to get back in. So what would be your best thoughts on what needs to be filitered?
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
So what would be your best thoughts
If me - I would just get a unifi wifi 6 pro for $149 and call it a day.. I show those WRT3200ACM for $249 on amazon. I sure hope you didn't pay that much..
Click click and you can run whatever vlans you want on any ssid, like a 2 minute setup ;) How many hours you got playing with this currently ;)
-
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
So what would be your best thoughts on what needs to be filitered?
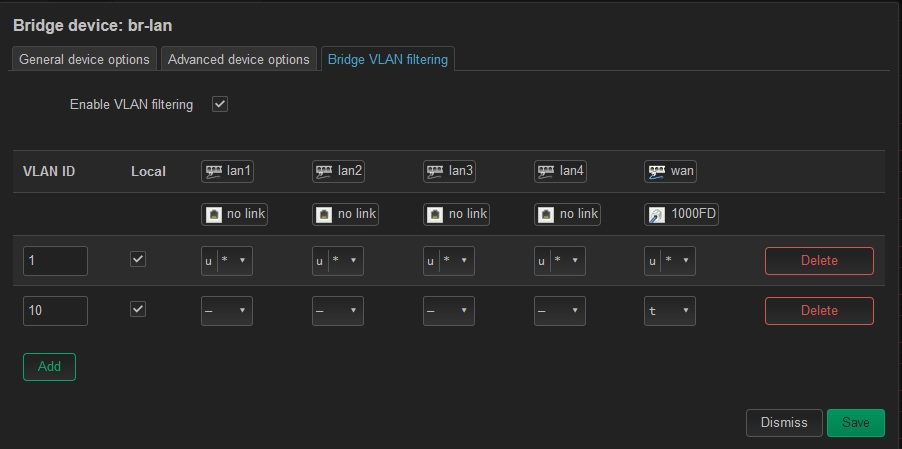
To use DSA as expected you should have VLAN 1 untagged on all ports and also the PVID on all ports. Local should be checked so the router itself can use it
VLAN 10 should be tagged on the WAN port only.
Local can be set there too so you get an IP in the vlan 10 range but it doesn't have to be. You will probably want to change that later so guest wifi clients can't connect to OpenWRT (and OpenWRT cannot route between the subnets).Steve
-
@johnpoz If I were smart... I'd have gone that way too.
All joking aside, I have always been partial to Linksys in the plastic box world. Been running them since the WRT54G v2. (and for 20 years on DD-WRT). I'm retired and one of the kids who used to work for me, who I picked to fill my position has a buddy who works for a company that buys equipment coming off lease. He saw pallets of these WRT3200ACMs at his buddy's warehouse and called me. I picked up half a dozen for (a little) less than your Amazon price. Other than this @$?#&(#/!! VLAN issue, they really are working well for their intended purpose.That said, if you'd still like to help, I have one built out to my current config I can still send your way. Either DM me or use my email (on my profile) to get me Mailing address and I'll pop it in the mail to you today when I venture down off the mountain to go to town.
Rick
-
@stephenw10 said in pfSense with OpenWRT Guest logon with VLAN:
@ramosel said in pfSense with OpenWRT Guest logon with VLAN:
So what would be your best thoughts on what needs to be filitered?
To use DSA as expected you should have VLAN 1 untagged on all ports and also the PVID on all ports. Local should be checked so the router itself can use it
VLAN 10 should be tagged on the WAN port only.First of, Thank You and John for all your help. It really is appreciated and I know you guys are busy.
Well, we made two steps forward, one backward. That is the first VLAN filtering config that hasn't locked me out and caused a revert.
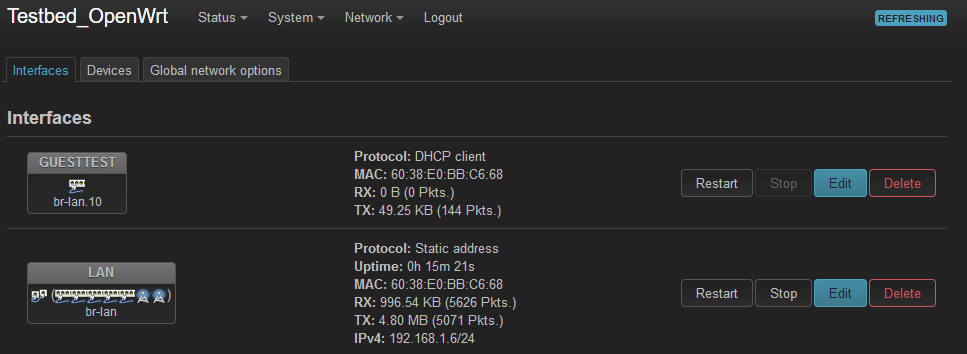
DSA did successfully create the br-lan.1 device
But now... the DHCP client on the GuestTest Interface is no longer getting an address.
-
@ramosel While I do really appreciate the offer and would be happy to play with it to help you figure out if you didn't have much better help in such matters already helping you @stephenw10 - if you were going to ship one for someone to help you - he would be the guy for sure..
If you have a bunch of them to spare, and were not expecting it back I would say send to Steve for his collection of hardware - he seems to collect all kinds of stuff, he always seems to have something in his lab to fiddle with when helping users..
Back in the day I use to love to fiddle with getting the most out of soho stuff, I had a few of those original wrt54g - I believe first router I had was their BEFSR41..
But now getting older and more money to play with - I like my shit to just do what I tell it to, without having to "fiddle" with it ;)
But Steve would be a good choice for sending one out to - it will prob be able to help many more fellow pfsense users in the future that is for sure, when the next guy comes along trying to do something with their WRT3200ACM, or something very sim..
-
@johnpoz said in pfSense with OpenWRT Guest logon with VLAN:
But Steve would be a good choice for sending one out to - it will prob be able to help many more fellow pfsense users in the future that is for sure, when the next guy comes along trying to do something with their WRT3200ACM, or something very sim..
Thanks for the response and I will certainly make that offer in that direction.
Steve, I do have a WRT3200ACM built up to my configuration. I'll certainly donate it to the cause to help get this fixed. If you can get an address to me, I'll get it on it's way.
I'm in the pfSense database somewhere. I have one of your SG-4860s that you have warranteed once. Send me an email, call me... what ever is easiest for you and I'll get this moving.
Rick Moseley
-
I'm in the UK which makes shipping something like that... more of an issue!
I may be able to get one locally. I think there is only one hardware version?What I don't see in your screenshot there is a wireless device on the GUESTTEST interface.
Try editing the wireless network and moving it to LAN and then back to GUESTTEST. It's possible it never got added to the bridge as the correct VLAN because VLAN filtering wasn't enabled at that point.I would have expected the GUESTTEST interface to pull an IP itself though since it's enabled as local.
Otherwise try installing ip-bridge and running
bridge vlanas I showed above to see how it's currently configured.Steve
-
@stephenw10 Cost is not an issue... one of my best friends runs Cosworth (from Texas). I can get it to you one way or another.