manage AP on another subnet [Solved]
-
@lolcakes69 You need to set the default gateway on the device being managed. That is assuming it will allow itself to be managed from something off its local subnet in the first place.
-
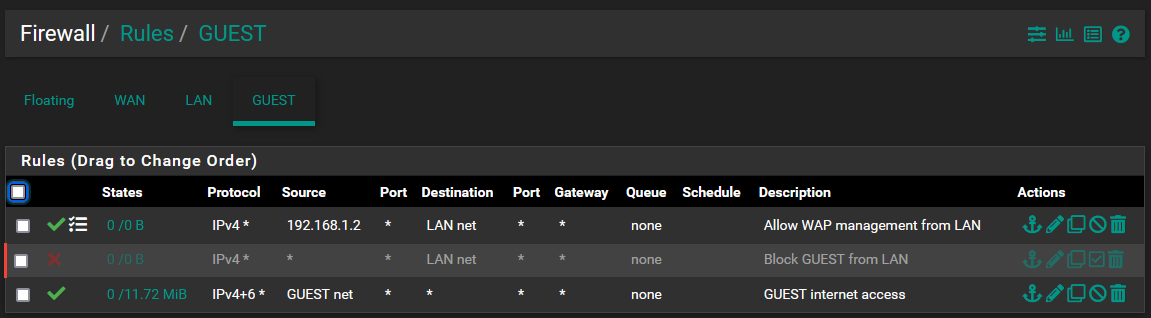
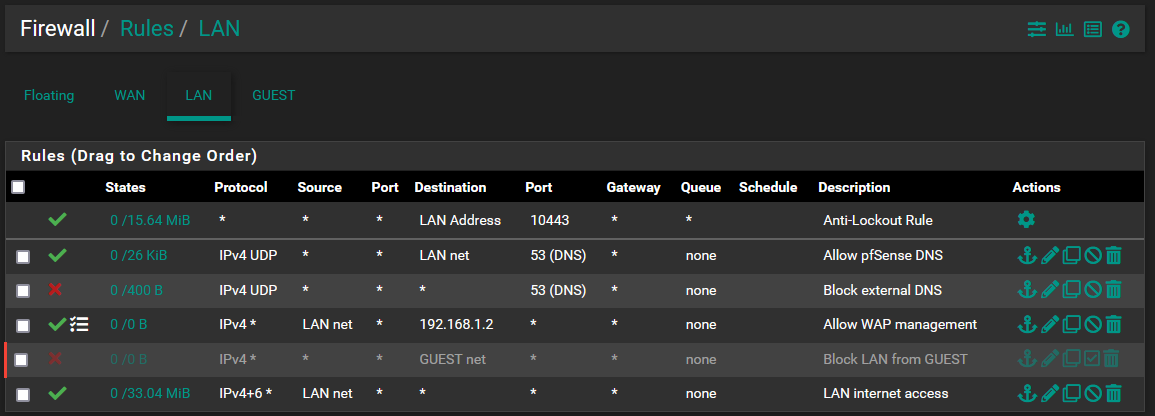
@derelict The only rule you need is the last rule on LAN. you have made a more-specific rule two rules up but it is competely unnecessary. The rule on GUEST would allow connections from the AP to LAN Net, not the other way around.
-
@lolcakes69 I would also point out your dns rules should be adjusted.
The use of lan net is odd, this should be lan address - its clearer in understanding of the rule. Pfsense has no control of stuff talking to each other on the lan net. So unless you have a vip or something on pfsense that is also in the lan net.. The rule would be better if explicitly stated lan address vs net.
Also dns can use tcp as well in some cases, so when doing dns rules it normally better to allow both udp and tcp on 53.
Same goes for your block rule. While you blocking clients from using say an external dns on udp, they could fall back to using tcp which your not blocking.
-
@derelict the AP has an option to set a failover IP which is how I was able to give it the 192.168.1.2 with subnet 255.255.255.0 and gateway 192.168.1.1 which is the GUEST address.
just to make sure you're saying the "allow WAP management" rule on LAN can be deleted because the rule on GUEST is sufficient?
@johnpoz I have adjusted the DNS rule, thank you. that was something new i literally just got off a youtube video, they might have set it to address instead of net and I just missed it.
-
@lolcakes69 said in manage AP on another subnet:
"allow WAP management" rule on LAN can be deleted because the rule on GUEST is sufficient?
There are no rules need on guest network to allow access from lan.
Rules are evaluated on the interface traffic enters pfsense, from the network attached. Return traffic is allowed via the state that creates when traffic is allowed.
The lan rule you created it is redundant to the rule on the bottom that is an any any rule.. The only reason to create a more specific rule would be if you say wanted to log that traffic, or not log it, etc.
edit: if your AP has a gateway and web gui access is not working. As mentioned it could be that that the AP doesn't like access from a non local IP. If this is the case you could "trick" it into allowing access from your lan by doing a source nat so that traffic from lan looks like it coming from your pfsense IP in the guest network. This is done via an outbound nat on the guest interface.
-
@lolcakes69 said in manage AP on another subnet:
i'm also still kinda new to this.
That is for sure given that none of your shown rules is making sense.

-
@johnpoz i'm a little confused here unfortunately, I have a rule that stops GUEST and LAN from speaking so I thought it'd be necessary to create a rule to only allow speaking to AP IP for management purposes no?
@Bob-Dig yes, ty for the input, much helpful, very wow... everyone starts somewhere, would you like to explain what doesn't make sense? some of the rules I got from lawrence systems on youtube, which was the whole reason i jumped into this in the first place. I'm willing to learn, otherwise I wouldn't have jumped in but idk what you want me to with your response:
"i'm a noob"
"lol yeah you are"Rules to block communication between my LAN and GUEST which is wifi only. This makes sense to me since the two shouldn't have any need to communicate.
Like I said above, the DNS rules are brand new that I got from another lawrence video that I was still messing with and I've adjusted those according to johnpoz's recommendations.
-
@lolcakes69 said in manage AP on another subnet:
I have a rule that stops GUEST and LAN from speaking
You do - but that rule shows as disabled.. But sure if your going to stop lan from talking to all of guest, then you would need a rule above it to allow access to the AP.. But you for sure do not need a return rule on the guest interface.
Even if you have a specific rule on guest that blocks access to lan, the state created when you allow from lan to guest, would allow the return traffic from guest to lan.
-
@johnpoz I guess that is my bad, I disabled it for a quick test but it's enabled otherwise.
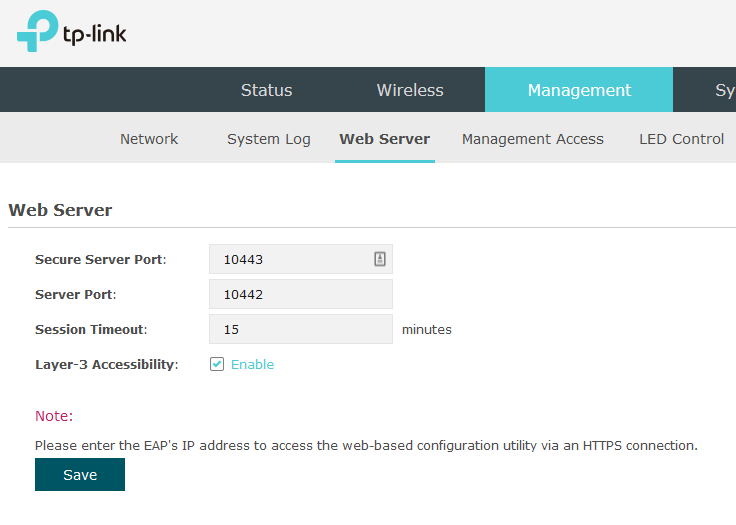
I also did check my AP settings, there's a "layer 3 accessibility" but my switch is only layer 2, so I guess even enabling that, it wouldn't help. I will have to figure out how to get those source and outbound NAT rules setup.
-
@lolcakes69 said in manage AP on another subnet:
there's a "layer 3 accessibility"
Not sure what that is - but pfsense is routing at layer 3. This might have to do with allowing access from other networks other than the AP local network - what is the specific make and model of this AP. I should be able to take a look at the manual and see what exactly they mean by that statement.
If I had to "guess" you would have to provide the IP(s) that can access it, or the cidr block that can, etc. like 192.168.1.0/24
-
@johnpoz it is a TP-Link EAP225. oh yeah that's right, that went straight over my head - my AP isn't even connected to my switch lol idk why I said that. I have the AP set to 192.168.1.2
-
@lolcakes69 those are meant to be managed by a controller, do you not run the controller? If your trying to manage it via the web gui and not a controller.. I believe that has limited functionality..
I looked for emulator of that model but could only find like the 610.. Could you post up a screen shot of where your seeing that.
-
@johnpoz it's in this menu here
-
i can all of a sudden access it now? I've had that setting enabled since I found it but wasn't able to access it until now. I don't even know if I did anything different. But it works now? So I guess that's good?
-
@lolcakes69 well per this thread - sure seems like that is what allows access from other network
https://community.tp-link.com/en/business/forum/topic/229318
So your trying to access from lan with say https://192.168.1.2:10443
What I would do if not working with your wide open lan rule.. Is sniff on the guest interface on pfsense (packet capture under diagnostics) on that IP and port.. While you try and access from your lan. If you see the traffic go out, and no response then the problem is with the AP.
edit:
Oh so its working now - great!! Maybe that setting didn't take effect, did you maybe reboot the ap? Or maybe you didn't use the :port on the end of your url? -
@johnpoz AP wasn't rebooted. Actually I think what it was is I wasn't putting in https:// and had just assumed it would connect via that. All I had in the address bar before was 192.168.1.2:10443
-
@lolcakes69 yeah you really need to make sure you call out http or https - browser can quite often default to http and that port isn't the http port, etc.
-
@johnpoz ty for your help. Now how do I close this thread or mark it as resolved? lol
-
@lolcakes69 you should be able to edit the subject - but I will mark it for you.