How do you direct all traffic from a remote Wireguard peer through my pfsense SG5100
-
How do you direct all traffic from a remote Wireguard peer through my pFsense SG5100. With OpenVPN I set my remote clients to direct ALL traffic through my pFsense router, including those to external sites. Now that I have set up Wireguard, all traffic to the pFsense router goes via Wireguard. However traffic to external sites does not. I have added 0.0.0.0 as an allowed IP, still no luck. Any suggestions?
-
@munson You mean 0.0.0.0/0 as THE allowed IP, right? Should be the only one.
-
@jarhead Thanks for your reply. On th remote device I have set the allowed IPs to 0.0.0.0/0. while on the SG5100 the allowed IPs are 172.x.y.z (Wireguard interface),192.168.y.z and 192.168.y.z . Should I change the SG55100 allowed IPs to 0.0.0.0 instead?
Thanks
-
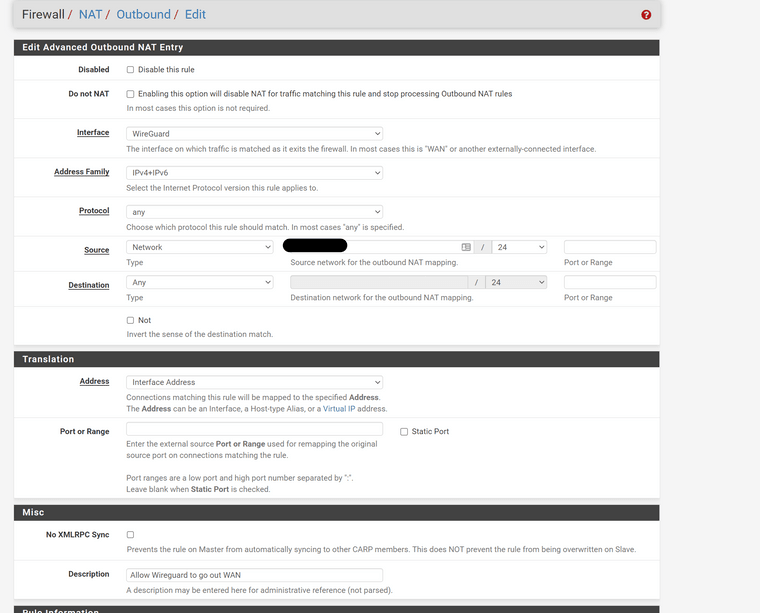
@munson you need to make sure you have an outbound NAT rule for the WireGuard subnet to exit via WAN interface.
-
@jarhead Yes for clarification the remote device allowed IP is 0.0.0.0/0, while on the SG5100 I have listed the three networks. I must be doing something wrong.
-
the allowed IPs is not the same thing as outbound NAT. If the remote device is an router, then 0.0.0.0/0 will enable you to send traffic for any IP address over the wireguard link. Assume you are using policy based rules to do that. On the 5100 end, you need to have allowed IPs set to the remote subnets. Also, you need to make sure you have the IP address of the remote wireguard interface as well. So it would be for example like 10.10.10.2/32. BUT on the the 5100, if the goal is to allow remote devices to access the internet, you need to have an outbound NAT rule allowing the remote subnets to exit via WAN.
so if my remote subs were 192.168.10.0/24, 192.168.20.0/24, and 192.168.30.0/24, I would need an outbound NAT rule for each one of those subnets as the source with the WAN interface selected as the outbound one
-
Also, you need to make sure you set static routes on the 5100 so that the router knows where to send traffic to your remote subnets. You'd make a route destined for each subnet, with the wireguard interface as the gateway. If you have not already done so, you should read the Pfsense documentation on Wireguard. It is very clear and they even provide example configs.
-
Thanks . Can you please provide an example, and what page in pFsense is this added.
-
@munson NAT is on the Firewall tab -> NAT -> Outbound. Then set your NAT to hybrid or manual (which I prefer personally) and add the rules I described.
For static routes, you need to go to System -> Routing -> Static Routes and then create the routes as I described them.
-
Thanks for your patience and expert advice. I just got back to this project. I still can not send all traffic from a peer through my SG51000
Here are some screenshots of my rules and configurations, any suggestions would be appreciated:
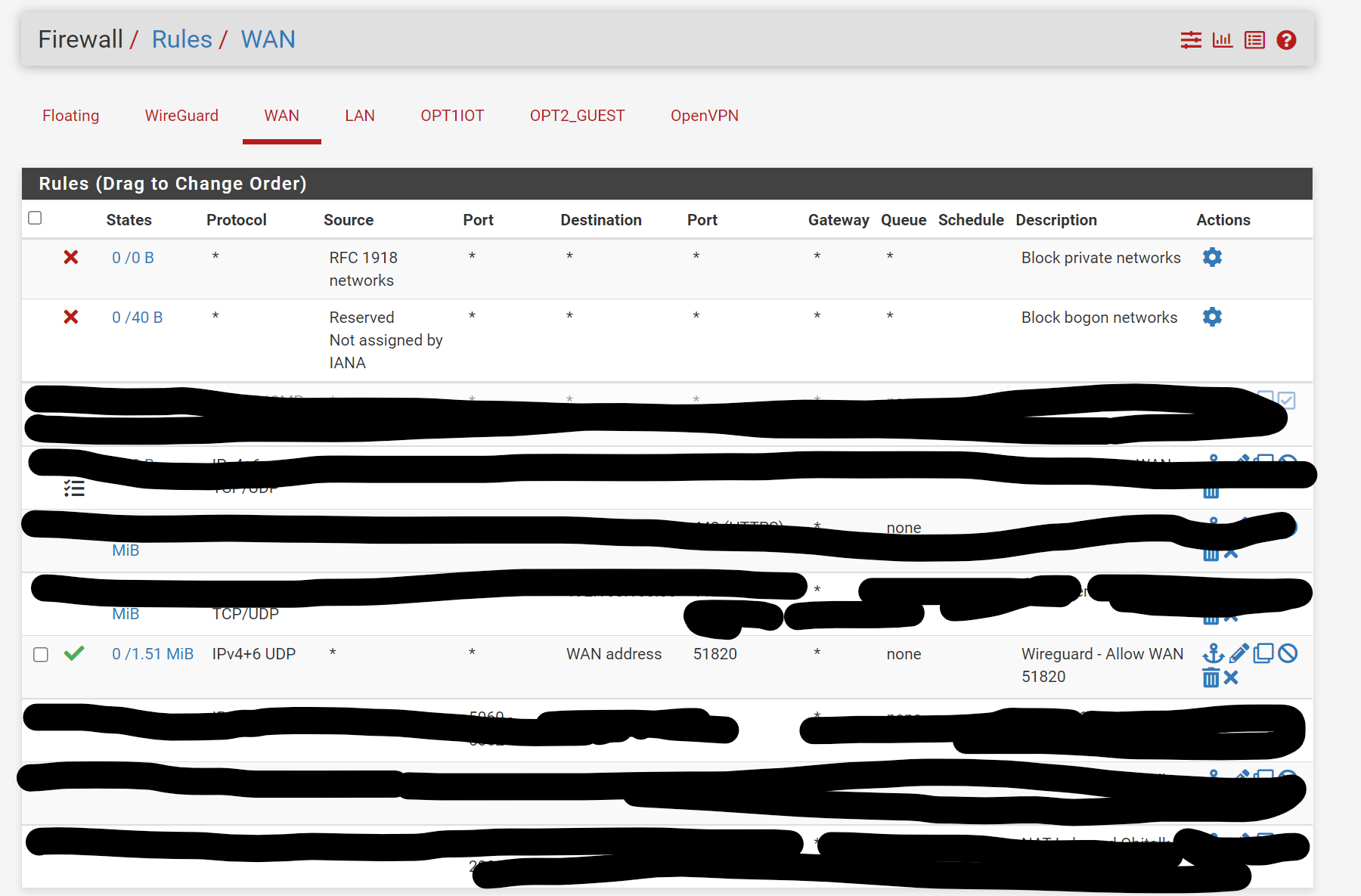
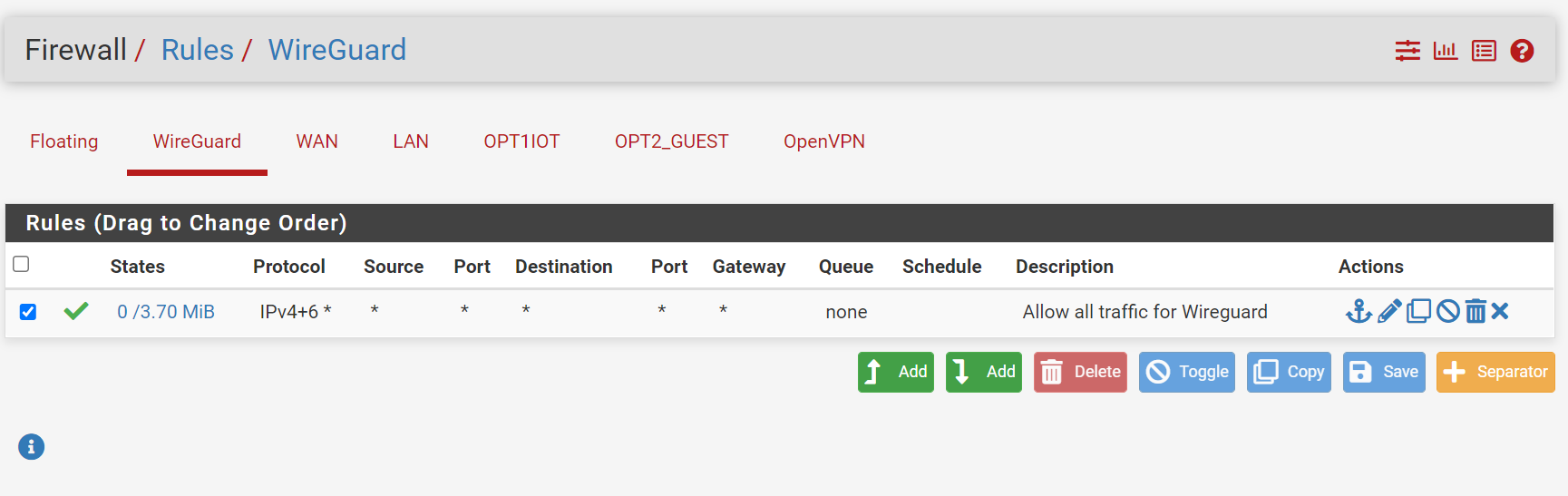
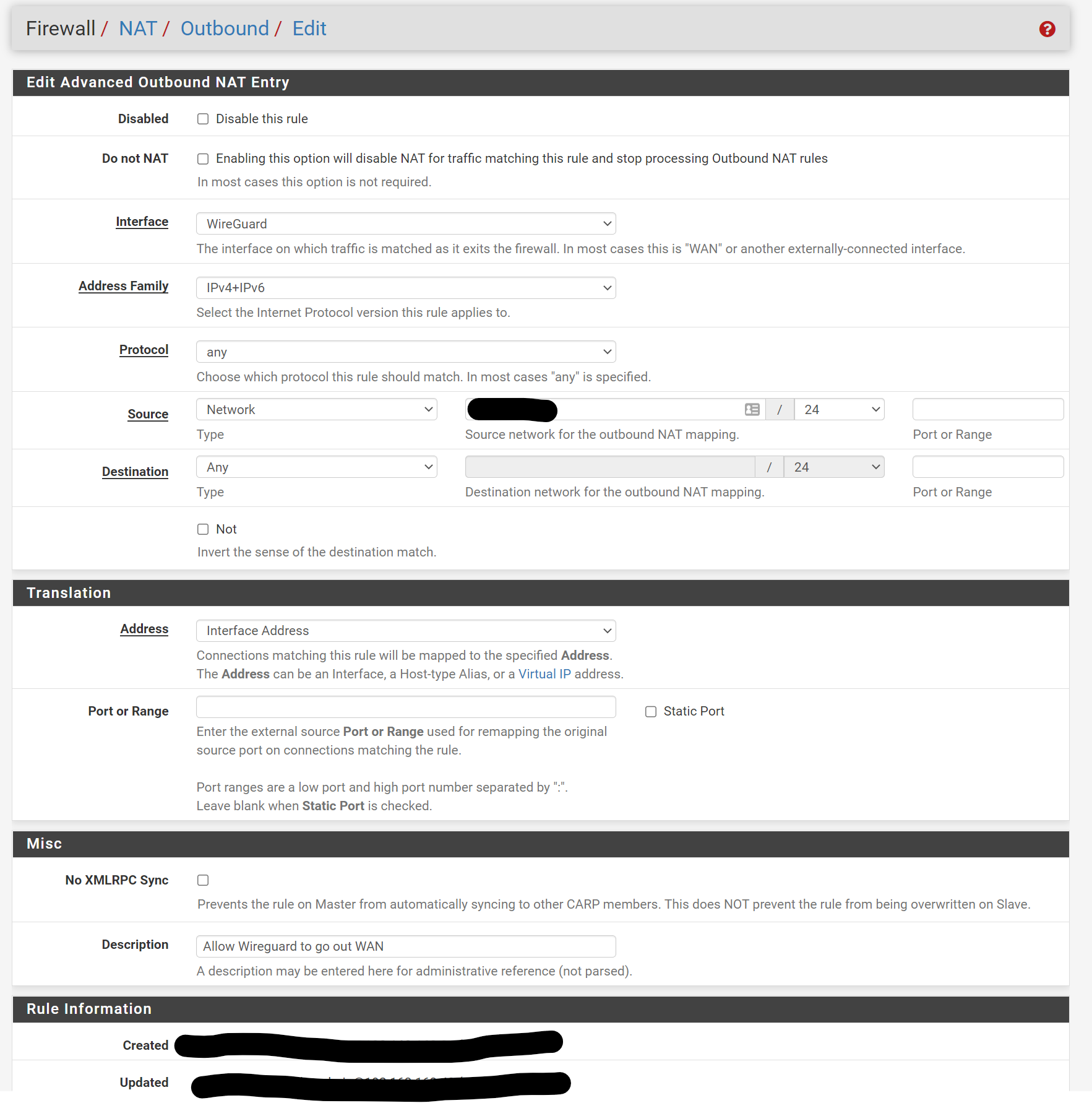
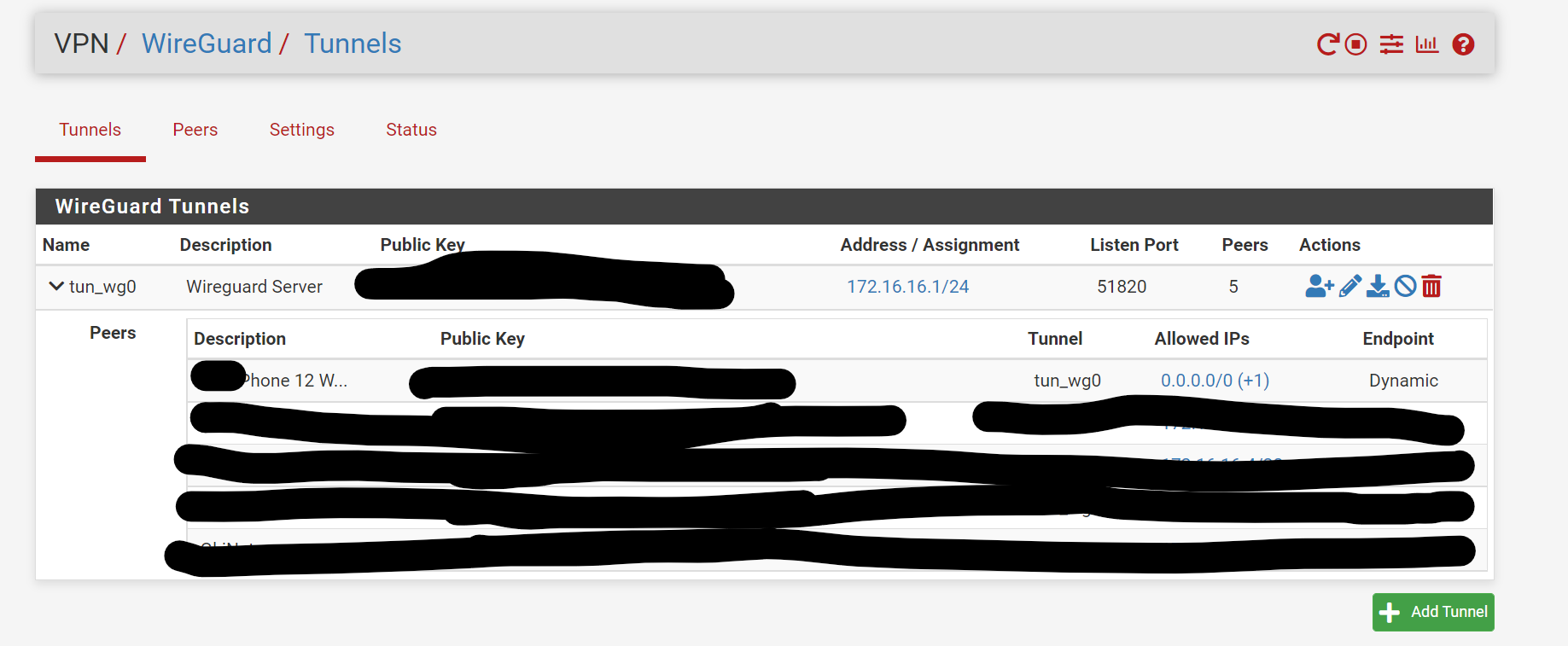
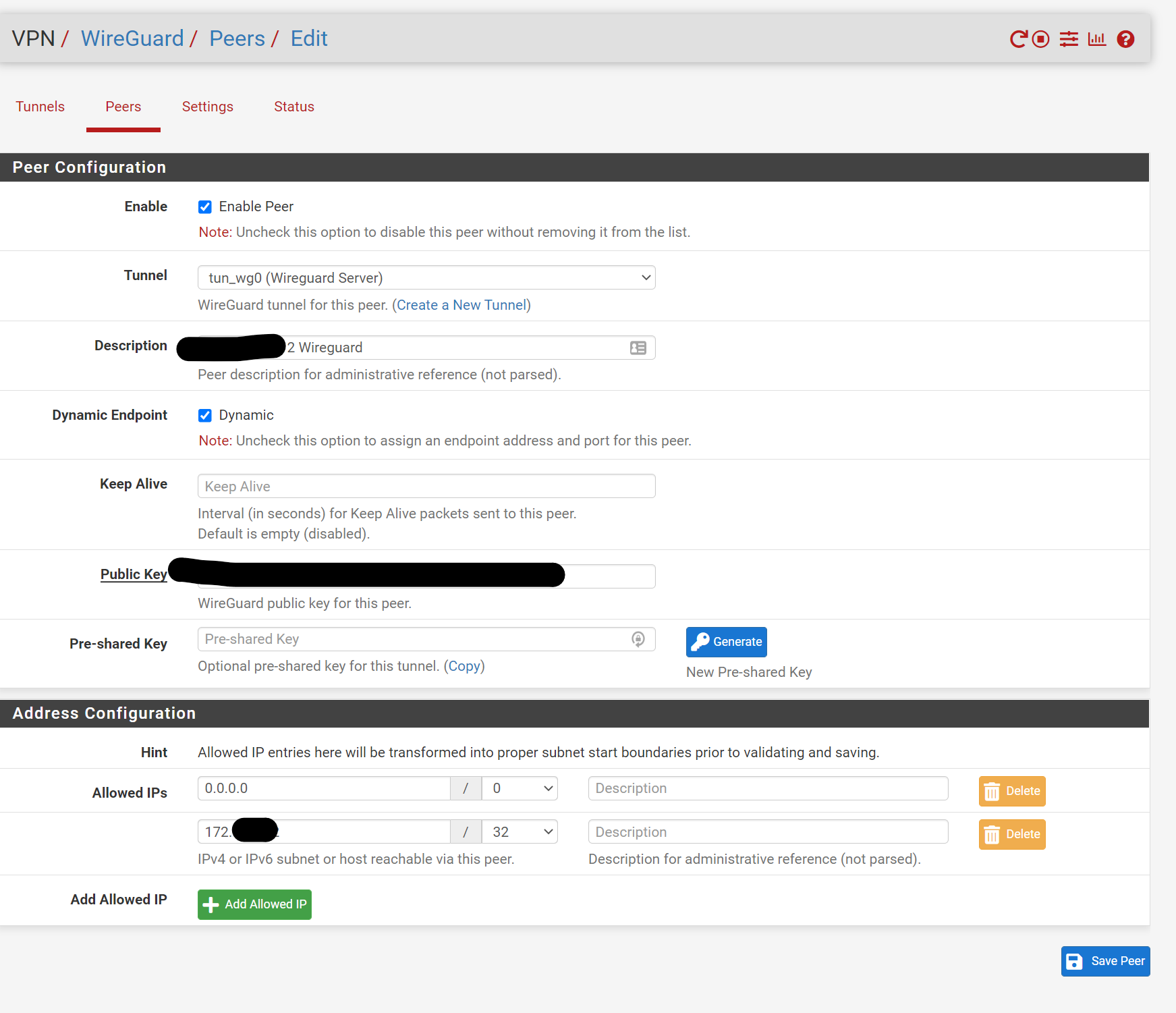
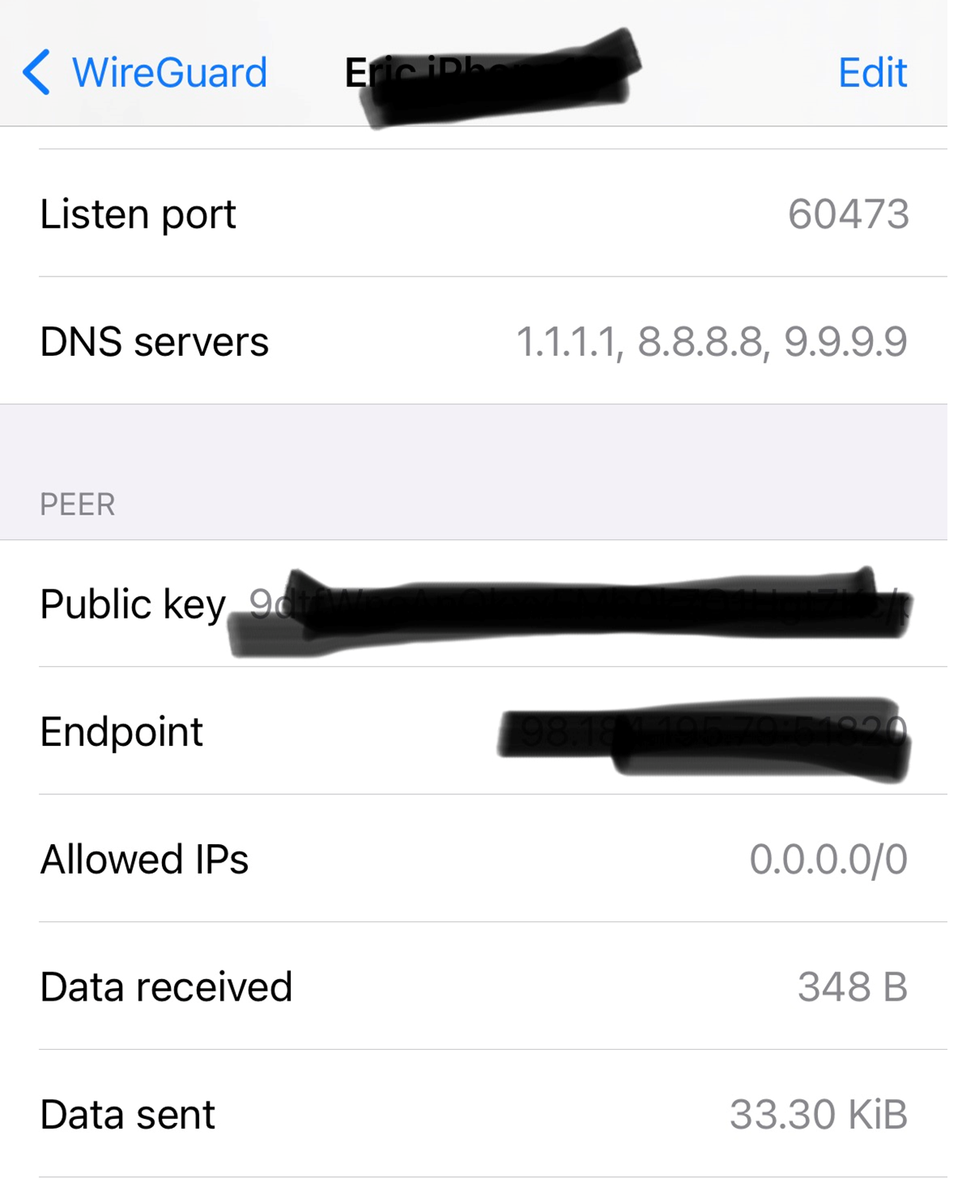
Here is the iphone configuration
Any assistance would be appreciated. -
@munson Your NAT rule is wrong. It's not the wireguard interface you are sending the traffic out to the world but WAN. Your network address (not sure why you blacked that out since they are private IPs and not public ones) should be the subnet that your client phone uses. So if the client IP is 192.168.100.2/32 then the network subject on your NAT outbound should be 192.168.100.0/24. I guess you could make it for just one IP but that seems unnecessary.
-
@munson Also, on the peers setting on the 5100, remove the 0.0.0.0/0 and just put the ip address of your phone. Looks like you're using a 172.16.x.x/24 structure so it should be 172.16.x.x/32 (whatever the specific IP for the phone is).
EDIT: sorry that wasn't very clear. On the 5100, the allowed IP address(es) is just the client IP. remove the 0.0.0.0/0.
-
@munson any update?
-
@gabacho4 Did you ever figure it out?
-
K kevdog referenced this topic on