Security of Vlan on WAN with Send options
-
An ISP login like that is not really expected to be super secure anyway. Most ISPs don'y require a login there at all and some only have that because the protocol requires it.
If someone else has those credentials what can they do with it?Steve
-
@stephenw10 said in Security of Vlan on WAN with Send options:
If someone else has those credentials what can they do with it?
Exactly - not like its your bank account info, or your gmail login, etc.
-
-> Yeah if it is snooped and someone signs in at the same time as me, they may be able to see my traffic.
-
on my wan locally ? Huh? Wht do you mean?
-> On ISP's L2, you mean employees or just other people who are subscribers ?
This sounds both concerning and irrelevant; mainly because I just do not understand enough about networking. Appreciate help!
-
-
Why would someone be able to see your traffic by signing in as you? To the ISP I assume you mean?
Waaay back in the day some cable providers would allow subscribers to talk to each other on the same layer 2 but I'm pretty sure that hasn't been the case for years. It isn't for DSL anyway.
So people who might potentially be able to see this would be, your ISP or technicians operating anything in the path between you and the ISPs DHCP server.Steve
-
@stephenw10 said in Security of Vlan on WAN with Send options:
talk to each other on the same layer 2 but I'm pretty sure that hasn't been the case for years.
I would think the same - but on my own cable connection, I am able to see arps from other subscribers. Now I would have to sniff for dhcp traffic, since this is broadcast as well. Its running now - but could take a bit of time to see if see anything since lease is decent length and its not like their are 1000's and thousands of users on the same L2, etc..
And its quite possible they restrict dhcp but allow arp, because for one dhcp would be either to filter on.
Will let it run for say an hour or so and report back if seeing any dhcp traffic on wan other than possible my own.. Few times I have checked while writing this - haven't seen any.
If your so concerned - use their device ;) But I just don't understand your concern to be honest, if it was me I would not have any issues with what they are asking.
-
Their router will be doing exactly the same thing though.
If you don't want to do that change ISP.
-
@stephenw10 said in Security of Vlan on WAN with Send options:
Their router will be doing exactly the same thing though.
That was my point ;) hehehe - maybe I wasn't as clear as I wanted to be with my attempt at sarcasm ;) heheh should of added the /s tag I guess.
I concur the device is possible doing the exact same thing, or maybe it has some generic auth they use for their devices.. Either way the only reason the user has any clue to this is asked the isp use their own device.
Why don't you bring up your concerns of doing that with the ISP - and see what they say about it. BTW - not seeing any dhcp on my wan as of yet.
-
@johnpoz Where I am located there are no ISPs that make it easy to connect your own router. They all have some workaround needed.
Thanks for settling my mind on this and sharing some info, again this is all a learning process for me I am less experienced than you.
In the forum post there is one point where I am stuck. They say to send the options with priority 6, when I swapped the prority on the Vlan to 6 my speed dropped a lot. Is there a way to only send that traffic with priority 6 and all other WAN traffic with priority 0 ?
-
@srytryagn said in Security of Vlan on WAN with Send options:
Is there a way to only send that traffic with priority 6 and all other WAN traffic with priority 0 ?
No, not via any easy method. You might be able to do something with netgraph scripting but it would take some development effort.
If it's working fine for you using prio 0 I would stick with that.
Steve
-
@srytryagn so that capture has been running for a while this is all I saw
No discover, not requests, acks just these naks
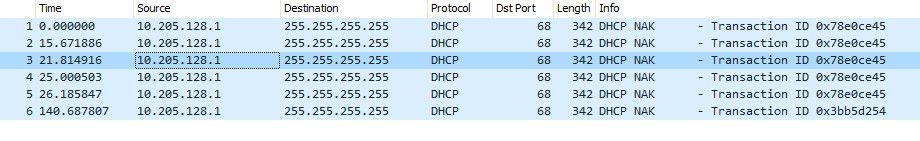
One I can tell from the mac address is a netgear, and that last one is some belkin device.
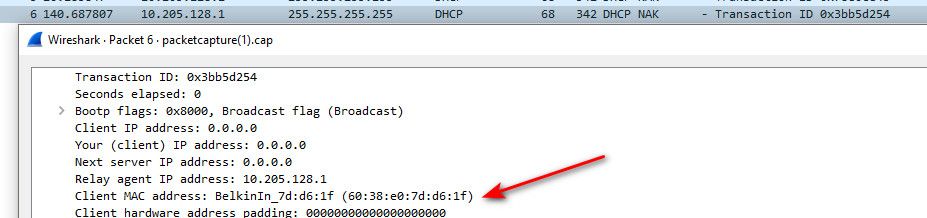
But clearly they are doing some filtering, or I would of seen the requests or discovers those devices were sening - but all I saw was naks.
-
@stephenw10 Thanks for taking a look and sharing this. How did you do it ? I am curious on my end to check as well.
-
What about if visiting websites or other internet connections, would they be able to see my login information?
-
@srytryagn no.. That login info is sent only via dhcp to your isp, to allow your router to get an IP.
-
@srytryagn Awesome. Thx.
-
And logins to other more remote sites will be encrypted with https or similar.