Suspicious Traffic?
-
@johnpoz said in Suspicious Traffic?:
@deanfourie the 162.159 address? That you see the mac of?
Correct, the MAC is the correct MAC address of the 4G router.
-
@deanfourie said in Suspicious Traffic?:
the MAC is the correct MAC address of the 4G router.
Its not a registered mac - I can find no listing for 82:49:99?
If if that is mac of your device - I am not clear to what the issue is? You shouldn't be seeing it on the L2 if its actually the upstream, but I see mac address of my cable modem, for the public IP of the gateway, etc.
-
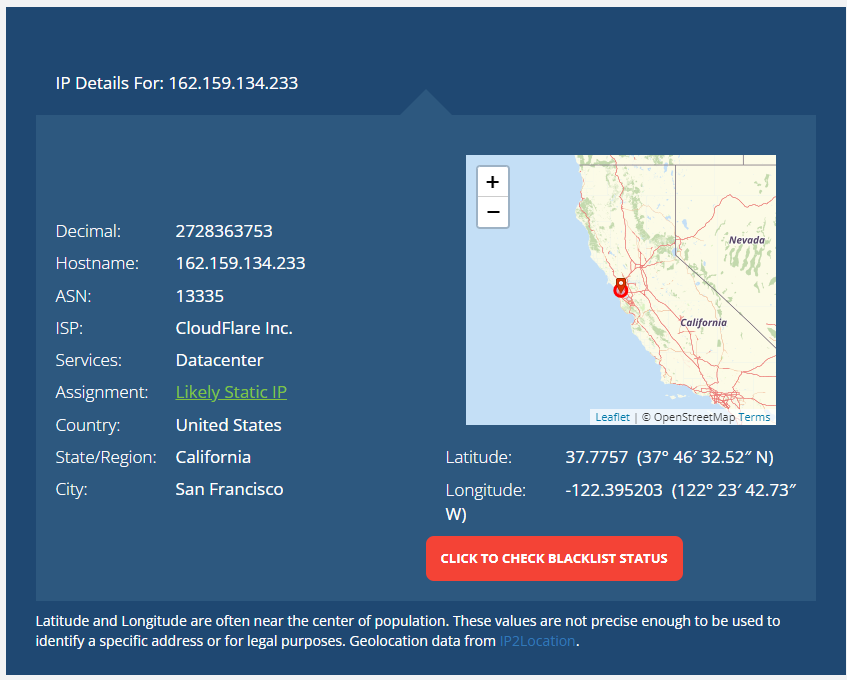
Ok, let me map it out for you too. Also, this public IP is NOT my public IP.
ISP >>>> 4G Wireless (through the air) >>>>>> 4G Router (Huawei 192.168.8.1 incoming internet) >>>>> pfSense WAN Interface (192.168.8.2) >>>>>>>> pfSense LAN (172.16.101.0/27) >>>>>>> LAN
Upon a scan on the WAN interafce I would expect to see 2 hosts, 192.168.8.1 and 192.168.8.2.
Instead of seeing a private IP on my upstream gateway, I am seeing a public IP that shows as being a datacenter in California somehwere.
Cheers
-
The router is not in bridge mode, so I would not expect to be seeing a public IP, and if I were, I would expect to be seeing my own public IP
-
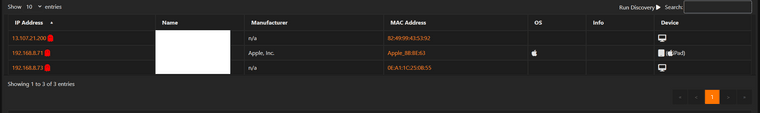
Its just gone ahead and changed again.
-
@deanfourie I wouldn't trust locations of IPs like that.
Many IP can be just registered to the owning company HQ, etc.
Its quite possible for you to learn the mac address of not connected device when using stuff like 4G or cable modems, etc..
There could be lots of ways on how that mac was learned.. I see arps from all over my ISP network on my wan.. With even different L3 address space, etc.
Maybe your device switches mode from nating to bridge when it looses a connection or when it boots up, etc. If it was actually isolated L2, then no you should see the mac for an address outside that L2.. But with such devices do you really know what its doing and how its doing it?
My cable modem bridges - but I still can access it via 192.168.100.1 address, etc.
If that is IP of your gateway on the wan side of your own device, still not understanding your concern?
-
@deanfourie said in Suspicious Traffic?:
Its just gone ahead and changed again.
Yeah 4G stuff prob going to change all the time... Connection moved to a new tower, different actual connection, etc. etc..
-
@johnpoz nah im really not comfortable with this.
When its at 192.168.8.1, I still have internet. I never see a public IP on its as its double NATting.
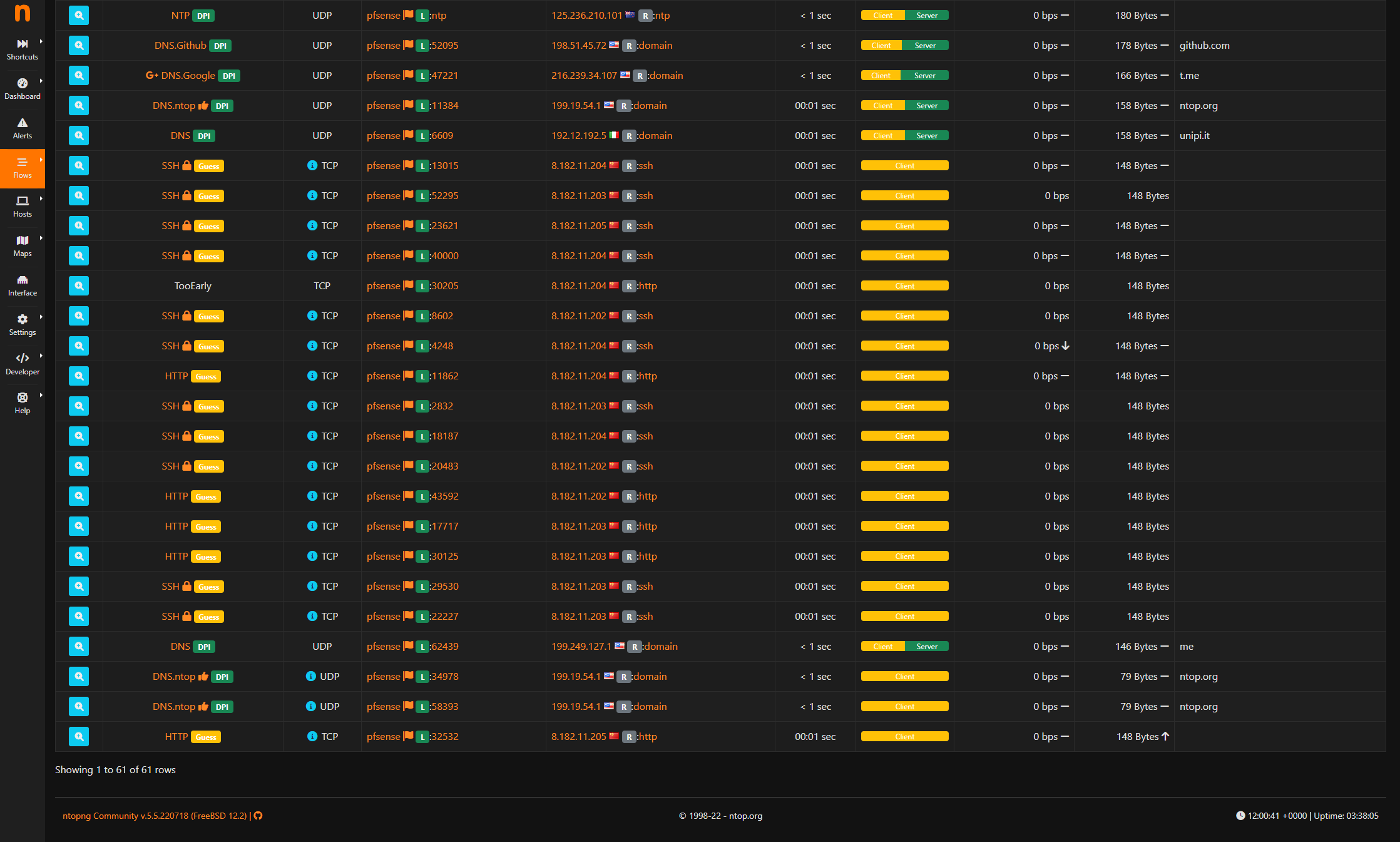
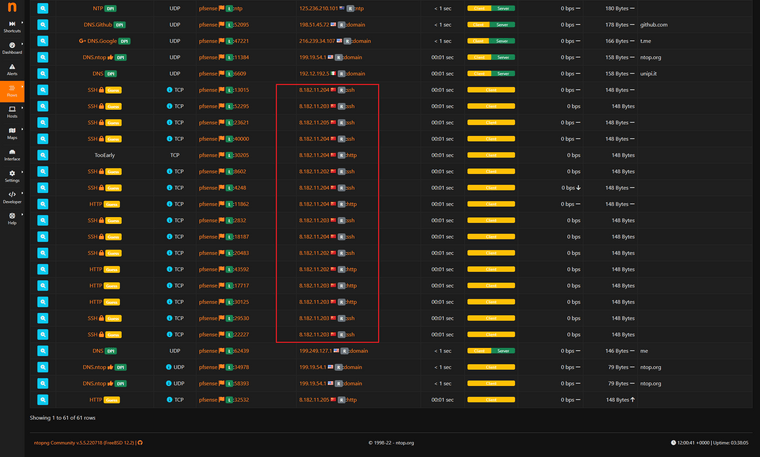
Im Natting at pfsense then again at the upstream gateway.What bout these shinnanigans? Some strange SSH and HTTP traffic to a very strange and foreign country?
-
@deanfourie pfsense itself should not be sshing to random IPs.. Or even 80..
What does pfsense show for its state table for those IPs.. If pfsense or a client generated traffic then it would be in the state table.
You sure that is just not traffic inbound from that source port as a SA? That is method of scanning..
Sniff on your wan for those IPs - lets see the pcap file.
-
-
@deanfourie sure you can..
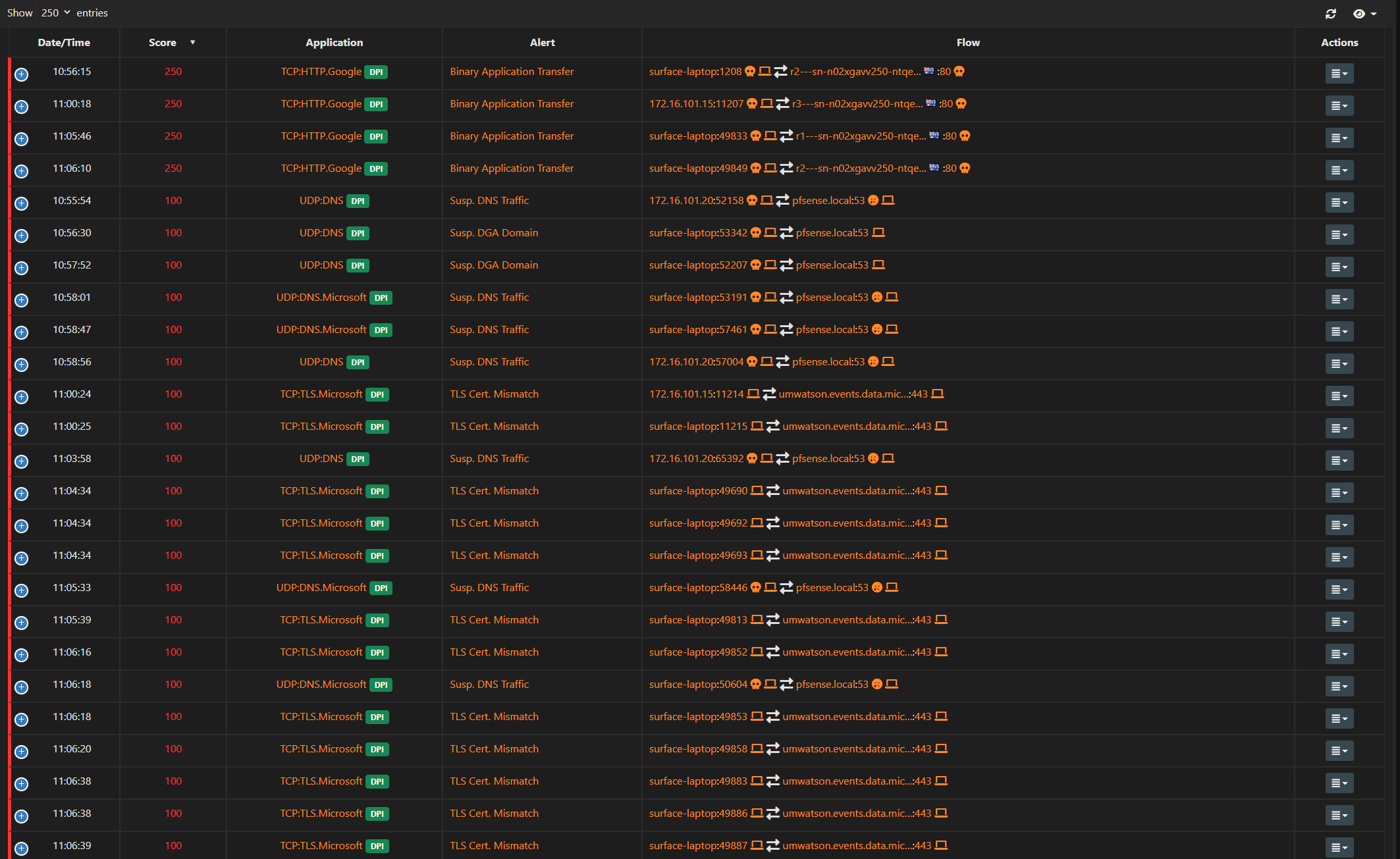
BTW those IPs are owned by Alibaba.com - well known website..
Again did you look in your state table?
-
@johnpoz could it be getting the port mappings all messed up because im double natting?
will check state table now.
-
WAN tcp 192.168.8.2:12812 (172.16.101.17:50569) -> 20.198.119.84:443 ESTABLISHED:ESTABLISHED 270 / 150 25 KiB / 34 KiB WAN tcp 192.168.8.2:18400 (172.16.101.17:50585) -> 74.125.68.188:5228 ESTABLISHED:ESTABLISHED 163 / 166 7 KiB / 18 KiB WAN tcp 192.168.8.2:46821 (172.16.101.7:40860) -> 34.120.177.193:443 ESTABLISHED:ESTABLISHED 19 / 18 2 KiB / 5 KiB WAN tcp 192.168.8.2:2211 (172.16.101.7:52014) -> 185.199.108.133:443 ESTABLISHED:ESTABLISHED 11 / 11 1 KiB / 5 KiB WAN tcp 192.168.8.2:47425 (172.16.101.15:49690) -> 76.223.31.44:443 ESTABLISHED:ESTABLISHED 40 / 42 2 KiB / 17 KiB WAN tcp 192.168.8.2:20743 (172.16.101.15:49408) -> 20.198.119.143:443 ESTABLISHED:ESTABLISHED 49 / 33 6 KiB / 9 KiB WAN tcp 192.168.8.2:7210 (172.16.101.15:49738) -> 185.159.80.151:8886 ESTABLISHED:ESTABLISHED 317 / 449 13 KiB / 18 KiB WAN tcp 192.168.8.2:11825 (172.16.101.15:49775) -> 74.125.200.188:5228 ESTABLISHED:ESTABLISHED 102 / 102 5 KiB / 12 KiB WAN tcp 192.168.8.2:50350 (172.16.101.15:1025) -> 162.159.130.234:443 ESTABLISHED:ESTABLISHED 2.854 K / 3.08 K 128 KiB / 685 KiB WAN udp 192.168.8.2:5477 -> 173.234.106.107:1194 MULTIPLE:MULTIPLE 4.046 K / 4.045 K 333 KiB / 327 KiB WAN icmp 192.168.8.2:53676 -> 1.1.1.1:53676 0:0 4.023 K / 4.022 K 114 KiB / 114 KiB WAN tcp 192.168.8.2:39097 (172.16.101.15:1503) -> 208.123.73.199:443 ESTABLISHED:ESTABLISHED 1.788 K / 1.927 K 479 KiB / 429 KiB WAN tcp 192.168.8.2:57584 (172.16.101.15:12915) -> 151.101.165.2:443 ESTABLISHED:ESTABLISHED 1.074 K / 1.735 K 168 KiB / 1.86 MiB WAN tcp 192.168.8.2:29269 (172.16.101.15:12923) -> 54.235.148.246:443 ESTABLISHED:ESTABLISHED 59 / 58 4 KiB / 14 KiB WAN tcp 192.168.8.2:43248 (172.16.101.7:52032) -> 185.199.108.133:443 ESTABLISHED:ESTABLISHED 14 / 13 1 KiB / 5 KiB WAN tcp 192.168.8.2:29264 (172.16.101.7:40878) -> 34.120.177.193:443 ESTABLISHED:ESTABLISHED 20 / 18 2 KiB / 5 KiB WAN tcp 192.168.8.2:63243 (172.16.101.17:50822) -> 35.82.210.186:443 ESTABLISHED:FIN_WAIT_2 11 / 14 1 KiB / 8 KiB WAN tcp 192.168.8.2:42063 (172.16.101.15:1083) -> 151.101.194.137:443 FIN_WAIT_2:FIN_WAIT_2 257 / 449 41 KiB / 533 KiB WAN tcp 192.168.8.2:21220 (172.16.101.15:1087) -> 199.232.214.133:443 FIN_WAIT_2:FIN_WAIT_2 2.131 K / 3.173 K 146 KiB / 3.03 MiB WAN tcp 192.168.8.2:25604 (172.16.101.15:1091) -> 151.101.130.137:443 FIN_WAIT_2:FIN_WAIT_2 309 / 499 31 KiB / 418 KiB WAN tcp 192.168.8.2:7591 (172.16.101.7:40880) -> 34.120.177.193:443 ESTABLISHED:CLOSING 19 / 29 2 KiB / 7 KiB WAN tcp 192.168.8.2:24193 (172.16.101.7:38508) -> 185.199.110.133:443 ESTABLISHED:ESTABLISHED 12 / 12 1 KiB / 5 KiB WAN tcp 192.168.8.2:41881 (172.16.101.15:1318) -> 142.250.71.78:443 ESTABLISHED:ESTABLISHED 33 / 40 10 KiB / 10 KiB WAN tcp 192.168.8.2:55573 (172.16.101.15:1352) -> 3.24.51.182:21 ESTABLISHED:ESTABLISHED 50 / 51 4 KiB / 6 KiB WAN tcp 192.168.8.2:25728 (172.16.101.15:1378) -> 162.159.135.232:443 FIN_WAIT_2:FIN_WAIT_2 14 / 13 1 KiB / 6 KiB WAN tcp 192.168.8.2:8063 (172.16.101.15:1410) -> 44.226.92.23:443 TIME_WAIT:TIME_WAIT 12 / 12 2 KiB / 8 KiB WAN udp 192.168.8.2:9834 (172.16.101.15:65210) -> 142.250.67.10:443 MULTIPLE:MULTIPLE 21 / 24 5 KiB / 7 KiB WAN tcp 192.168.8.2:55434 (172.16.101.17:50851) -> 52.41.50.6:443 FIN_WAIT_2:FIN_WAIT_2 11 / 12 2 KiB / 6 KiB WAN tcp 192.168.8.2:57382 (172.16.101.15:1418) -> 35.82.210.186:443 TIME_WAIT:TIME_WAIT 12 / 11 2 KiB / 6 KiB WAN tcp 192.168.8.2:54394 (172.16.101.15:1419) -> 202.124.124.90:80 FIN_WAIT_2:FIN_WAIT_2 6 / 5 346 B / 391 B WAN tcp 192.168.8.2:22280 (172.16.101.15:1420) -> 44.226.92.23:443 FIN_WAIT_2:FIN_WAIT_2 14 / 11 3 KiB / 6 KiB WAN tcp 192.168.8.2:44695 (172.16.101.15:1421) -> 35.82.210.186:443 TIME_WAIT:TIME_WAIT 12 / 12 2 KiB / 8 KiB WAN tcp 192.168.8.2:1247 (172.16.101.15:1422) -> 35.82.210.186:443 FIN_WAIT_2:FIN_WAIT_2 12 / 12 2 KiB / 6 KiB WAN tcp 192.168.8.2:17221 (172.16.101.15:1423) -> 202.124.124.91:80 FIN_WAIT_2:FIN_WAIT_2 6 / 5 346 B / 391 B WAN udp 192.168.8.2:19584 (172.16.101.15:53957) -> 142.250.204.4:443 MULTIPLE:MULTIPLE 175 / 396 26 KiB / 376 KiB WAN tcp 192.168.8.2:47504 (172.16.101.17:50852) -> 44.226.92.23:443 FIN_WAIT_2:FIN_WAIT_2 11 / 12 2 KiB / 6 KiB WAN tcp 192.168.8.2:48004 (172.16.101.15:1426) -> 202.124.124.91:80 FIN_WAIT_2:FIN_WAIT_2 4 / 5 266 B / 391 B WAN udp 192.168.8.2:23977 (172.16.101.15:62766) -> 142.250.67.14:443 MULTIPLE:MULTIPLE 40 / 55 6 KiB / 44 KiB WAN udp 192.168.8.2:29747 (172.16.101.15:52600) -> 172.217.24.42:443 MULTIPLE:MULTIPLE 12 / 11 4 KiB / 7 KiB WAN tcp 192.168.8.2:12425 (172.16.101.15:1427) -> 172.217.24.42:443 FIN_WAIT_2:FIN_WAIT_2 10 / 10 1 KiB / 6 KiB WAN udp 192.168.8.2:35646 (172.16.101.15:64854) -> 172.217.167.110:443 MULTIPLE:MULTIPLE 18 / 21 6 KiB / 6 KiB WAN udp 192.168.8.2:17732 (172.16.101.15:52777) -> 142.251.12.100:443 MULTIPLE:MULTIPLE 8 / 7 2 KiB / 3 KiB WAN udp 192.168.8.2:25021 (172.16.101.17:61533) -> 172.217.167.110:443 MULTIPLE:MULTIPLE 10 / 11 3 KiB / 5 KiB WAN udp 192.168.8.2:42623 (172.16.101.15:64825) -> 142.250.71.74:443 MULTIPLE:MULTIPLE 9 / 9 3 KiB / 4 KiB WAN udp 192.168.8.2:14418 (172.16.101.15:58123) -> 142.250.66.238:443 MULTIPLE:MULTIPLE 9 / 10 4 KiB / 5 KiB WAN udp 192.168.8.2:45098 (172.16.101.15:62002) -> 151.101.165.229:443 MULTIPLE:MULTIPLE 7 / 5 2 KiB / 4 KiB WAN tcp 192.168.8.2:18827 (172.16.101.15:1430) -> 68.67.73.20:443 TIME_WAIT:TIME_WAIT 9 / 10 1015 B / 6 KiB WAN tcp 192.168.8.2:11080 (172.16.101.15:1431) -> 68.67.73.20:443 TIME_WAIT:TIME_WAIT 23 / 27 6 KiB / 27 KiB WAN tcp 192.168.8.2:5459 (172.16.101.15:1432) -> 68.67.73.20:443 TIME_WAIT:TIME_WAIT 10 / 10 1 KiB / 6 KiB WAN tcp 192.168.8.2:2903 -> 204.61.216.50:53 FIN_WAIT_2:FIN_WAIT_2 6 / 5 366 B / 2 KiB WAN tcp 192.168.8.2:28352 (172.16.101.15:1437) -> 44.226.92.23:443 TIME_WAIT:TIME_WAIT 11 / 11 2 KiB / 6 KiB WAN tcp 192.168.8.2:4299 (172.16.101.15:1438) -> 202.124.124.90:80 FIN_WAIT_2:FIN_WAIT_2 5 / 5 306 B / 391 B WAN tcp 192.168.8.2:43484 (172.16.101.15:1439) -> 208.123.73.73:443 TIME_WAIT:TIME_WAIT 21 / 35 5 KiB / 40 KiB WAN tcp 192.168.8.2:51773 (172.16.101.15:1440) -> 208.123.73.73:443 TIME_WAIT:TIME_WAIT 14 / 15 4 KiB / 12 KiB WAN tcp 192.168.8.2:1628 (172.16.101.15:1441) -> 208.123.73.73:443 ESTABLISHED:ESTABLISHED 5 / 4 809 B / 511 B WAN tcp 192.168.8.2:38092 (172.16.101.15:1442) -> 208.123.73.73:443 ESTABLISHED:ESTABLISHED 9 / 9 993 B / 7 KiB WAN tcp 192.168.8.2:24666 (172.16.101.15:1443) -> 208.123.73.73:443 ESTABLISHED:ESTABLISHED 5 / 4 809 B / 511 B WAN tcp 192.168.8.2:8877 (172.16.101.15:1444) -> 208.123.73.73:443 ESTABLISHED:ESTABLISHED 9 / 9 993 B / 7 KiB WAN tcp 192.168.8.2:49217 (172.16.101.15:1445) -> 208.123.73.73:443 ESTABLISHED:ESTABLISHED 8 / 9 941 B / 7 KiB WAN tcp 192.168.8.2:20808 (172.16.101.15:1446) -> 35.82.210.186:443 FIN_WAIT_2:FIN_WAIT_2 12 / 11 3 KiB / 6 KiB WAN tcp 192.168.8.2:10716 -> 199.180.180.63:53 TIME_WAIT:TIME_WAIT 5 / 5 327 B / 2 KiB WAN tcp 192.168.8.2:27420 (172.16.101.15:1447) -> 44.226.92.23:443 ESTABLISHED:ESTABLISHED 12 / 12 2 KiB / 8 KiB WAN tcp 192.168.8.2:31279 (172.16.101.15:1448) -> 44.226.92.23:443 FIN_WAIT_2:FIN_WAIT_2 12 / 12 2 KiB / 6 KiB WAN tcp 192.168.8.2:65211 (172.16.101.17:50853) -> 35.82.210.186:443 FIN_WAIT_2:FIN_WAIT_2 11 / 12 2 KiB / 6 KiB WAN udp 192.168.8.2:60136 -> 150.171.16.34:53 MULTIPLE:SINGLE 1 / 1 73 B / 89 B WAN udp 192.168.8.2:34690 -> 202.124.124.84:53 MULTIPLE:SINGLE 1 / 1 76 B / 108 B WAN tcp 192.168.8.2:62217 (172.16.101.15:1449) -> 202.124.124.91:80 FIN_WAIT_2:FIN_WAIT_2 5 / 5 306 B / 391 B WAN tcp 192.168.8.2:43879 (172.16.101.15:1450) -> 202.124.124.91:80 FIN_WAIT_2:FIN_WAIT_2 6 / 5 346 B / 391 B WAN udp 192.168.8.2:23297 (172.16.101.15:50903) -> 142.250.204.4:443 MULTIPLE:MULTIPLE 5 / 5 3 KiB / 3 KiB WAN udp 192.168.8.2:5215 (172.16.101.5:123) -> 103.242.68.69:123 MULTIPLE:SINGLE 1 / 1 76 B / 76 B WAN udp 192.168.8.2:7924 (172.16.101.5:123) -> 162.159.200.1:123 MULTIPLE:SINGLE 1 / 1 76 B / 76 B WAN udp 192.168.8.2:20410 (172.16.101.5:123) -> 163.47.220.60:123 MULTIPLE:SINGLE 1 / 1 76 B / 76 B WAN tcp 192.168.8.2:19162 (172.16.101.15:1451) -> 52.41.50.6:443 ESTABLISHED:ESTABLISHED 11 / 11 2 KiB / 6 KiB WAN tcp 192.168.8.2:48761 (172.16.101.17:50854) -> 44.226.92.23:443 ESTABLISHED:ESTABLISHED 10 / 11 2 KiB / 6 KiB -
@deanfourie I don't see any states to that 8. address.
So pfsense didn't create, nor did a client create a connection to there.. Do a simple filter on your state table for the IPs in question.
If you do not see any states then pfsense did not create the connection, nor did a client behind pfsense.
And what you could be seeing could be SA scan, that is being interpreted wrong???
But if your concerned that pfsense, or something behind pfsense is creating connections to somewhere it shouldn't be - look in the state table.. If a connection attempt was made from or through pfsense then a state would exist. Even if the connection was not established.
Here - trying to ping one of those IPs.. Even though not getting an answer, you can see the state in the state table from pfsense
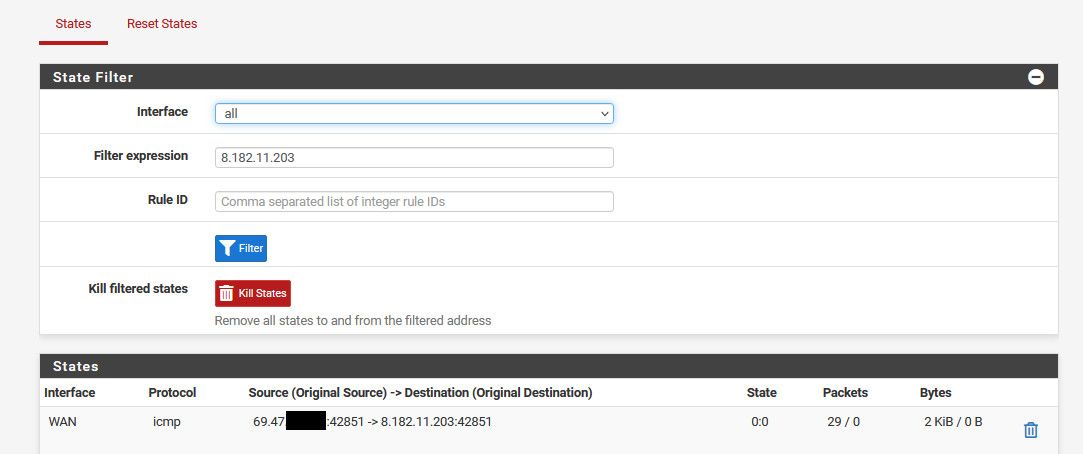
-
@johnpoz Ok great ill do this.
I hate working with upstream gateways and double natting, would much rather put the router in bridged mode and get WAN IP from DHCP and boom! Last time I did this I was on the naughty list with the ISP. They warned me
I will do more careful watching of the state table. My concern is actually with the 4G router still though,
If its doing some sort of dodgy proxying at the 4G router, I'm not going to be able to see that from pfSense WAN side as its before the WAN interface.
I mean at the end of the day, it is a Huawei router...
I cant even disable TR-069 on it, nor can I change the LAN subnet mask.
-
If you're concerned about it the only thing you can really do is tunnel all your traffic through it so the router never sees inside it. There is obviously overhead to doing that though.
Steve
-
@stephenw10 I originally was routing all traffic through a VPN, however I got so many more weird connections as a result.
One question I do have is, would doubling NATting effect the results of the flows in ntopng.
Like matching ports and applications etc?
Thanks
-
No I wouldn't expect it to. The source/destination ports/IPs that ntop can see are still the same.
-
@stephenw10 said in Suspicious Traffic?:
No I wouldn't expect it to. The source/destination ports/IPs that ntop can see are still the same.
Thank you
-
Maybe someone could take a look at this capture. Lots of SSH from 192.168.8.2 which is my pfSense firewall.
Also a lot of TCP retransmissions. I'm not sure how my pfSense could be sending out SSH traffic?