I don't know were to begin... Cloudflare and the dreaded 522 error
-
@swemattias none of those rules show any hits on them see the 0/0 that means the rule has never even been evaluated by any matching traffic.
Not sure how anything from the web would have a destination of your lan address. The destination of any traffic coming from the internet would be your wan address.
The firewall rule would be there to allow that after the port forward that sent it there.
-
@swemattias Move the from address (cloudflare) down to the portforwards to your internal server.
Delete the top rule afterwards.
-
@johnpoz and @Cool_Corona
Yes the rules has a 0/0 hit ratio, that is not good. But all I have read about the 522 says that the incoming traffic can't reach the internal server.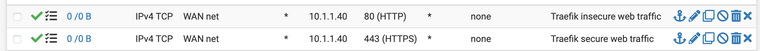
New rules. Still 0/0. I have read so much looked at so many YTs that I have gone blind it feels like.
I have setup so that pfSense sends the real ip to the service, so that is correct.I now also added a rule to LAN to accept traffic from WAN, just because.
-
@swemattias said in I don't know were to begin... Cloudflare and the dreaded 522 error:
Yes the rules has a 0/0 hit ratio, that is not good. But all I have read about the 522 says that the incoming traffic can't reach the internal server.
Possibly it can neither reach pfSense.
Sniff the traffic on the WAN to check it out.
-
@swemattias that rule is wan net, the source is not your wan net - its going to be anything on the internet, wan net is just that the network your wan is attached too.
-
-
@viragomann Any tips how to best do that? Something lurking inside pfSense?
-
@swemattias
Diagnostic > Packet CaptureSelect WAN at interface. At port enter "80|443". Hit Start.
Trigger some packets by trying to access your web server from the internet. Stop the capture and check the result if you see any packet. -
@swemattias are you actually creating a port forward, creating wan rules with destination of your lan side IP is not going to work without a port forward.
Again that rule is not have any evaluations 0/0
To sniff on your wan, under diagnostics packet capture.. Should be simple enough to just go to can you see me .org and try port 443 for example while you do the packet capture.
Do you have floating rules? Lets see your port forwards..
-
@johnpoz I has only opened the port like I have done so many times before. But I did create an Port Forward under NAT now.
It is a, a translated Swedish saying, fall forward. I don't get an 522 but still an time out....In the packet sniffing I do see this from time to time:
20:34:15.581150 IP my.external.ip.12483 > 108.157.214.15.443: tcp 0 20:34:15.581483 IP my.external.ip.12483 > 108.157.214.15.443: tcp 517Here are the whole packet sniff result.
Sniffing resultI am not used or have any valuable knowledge looking at packet sniffing results...
-
@swemattias said in I don't know were to begin... Cloudflare and the dreaded 522 error:
In the packet sniffing I do see this from time to time:
20:34:15.581150 IP my.external.ip.12483 > 108.157.214.15.443: tcp 0
20:34:15.581483 IP my.external.ip.12483 > 108.157.214.15.443: tcp 517This might be outbound connections.
But obviously nothing hits my.external.ip.443. So you should look in front of your pfSense for the failure.
Maybe there is something wrong on Cloudflare. -
I did redid my Port forwards under NAT, to divide them into 80 and 443 so they are more clear.
And suddenly it all started to work.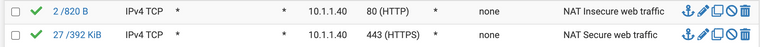
Thank you for helping me, means more to me than you will ever know.
So thank you @johnpoz @Cool_Corona and @viragomann

-
@swemattias said in I don't know were to begin... Cloudflare and the dreaded 522 error:
only opened the port like I have done so many times before
I don't know what you were doing before - maybe you had haproxy listening on your wan before, then no you wouldn't need a port forward.
If you want traffic to hit your public IP on wan, and get sent to some rfc1918 address behind you have to do a port forward. Unless your using haproxy as a reverse proxy to have that do that for you.
-
@johnpoz I ditched HAProxy and went to Traefik and all is working now. :)
-
This post is deleted!

